What are the five basic functions of a firewall?
The five basic functions of a firewall are: 1. A network security barrier, which can greatly improve the security of an internal network and reduce risks by filtering unsafe services. 2. Strengthen network security policies; through firewall-centered security solution configuration, all security software can be configured on the firewall. 3. Monitor and audit. 4. Prevent the leakage of internal information; by using firewalls to divide the internal network, key network segments of the internal network can be isolated, thereby limiting the impact of local key or sensitive network security issues on the global network. 5. Logging and event notification.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
Firewall technology helps computer networks build a relatively isolated protective barrier between the internal and external networks by organically combining various software and hardware devices for security management and screening to protect user data and A technology for information security.
Five functions of firewalls:
1. Network security barrier
A firewall (as a blocking point, control point) can greatly improve Security of an internal network and reduce risk by filtering unsecured services. Because only carefully selected application protocols can pass through the firewall, the network environment becomes more secure.
For example, a firewall can prohibit protocols such as the well-known insecure NFS from entering and exiting the protected network, so that external attackers cannot use these vulnerable protocols to attack the internal network. Firewalls also protect the network from route-based attacks, such as source routing attacks in IP options and redirect paths in ICMP redirects. The firewall should be able to reject all the above types of attack packets and notify the firewall administrator.
2. Strengthen network security strategy
Through the firewall-centered security solution configuration, all security software (such as passwords, encryption, identity authentication, auditing, etc.) can be configured on the firewall. Centralized security management through firewalls is more economical than spreading network security issues across individual hosts. For example, when accessing the network, the one-time password system and other identity authentication systems do not need to be scattered on various hosts, but concentrated on the firewall.
3. Monitoring and auditing
If all accesses pass through the firewall, then the firewall can record these accesses and make log records, and can also provide statistics on network usage. When suspicious actions occur, the firewall can issue appropriate alarms and provide detailed information on whether the network is being monitored and attacked.
In addition, it is also very important to collect the usage and misuse of a network. The first reason is to know whether the firewall can withstand attacker detection and attacks, and whether the firewall controls are adequate. Network usage statistics are also very important for network demand analysis and threat analysis.
4. Prevent the leakage of internal information
By using firewalls to divide the internal network, key network segments of the intranet can be isolated, thereby limiting the impact of local key or sensitive network security issues. Global network impact. Furthermore, privacy is a matter of great concern in internal networks. Inconspicuous details in an internal network may contain clues about security and arouse the interest of external attackers, and even expose certain security vulnerabilities of the internal network. .
Using a firewall can hide services that reveal internal details such as Finger and DNS. Finger displays the registered names, real names, last login time and shell type of all users on the host. However, the information displayed by Finger is very easy to be learned by attackers. An attacker can know how frequently a system is used, whether users of this system are connected to the Internet, whether this system attracts attention when being attacked, etc.
The firewall can also block DNS information about the internal network, so that the domain name and IP address of a host will not be known to the outside world. In addition to the security function, the firewall also supports the virtual private network of the enterprise's internal network technology system with Internet service capabilities.
5. Log recording and event notification
All data entering and leaving the network must pass through the firewall. The firewall records it through logs and can provide detailed statistical information on network usage. When suspicious events occur, the firewall can provide alarms and notifications based on the mechanism, providing information on whether the network is under threat.
(Related recommendations: Server Security)
The above is the detailed content of What are the five basic functions of a firewall?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
OneDrive is a popular cloud storage application provided by Microsoft. Most of us use OneDrive to store our files, folders, documents, etc. But some users complained that when they try to access shared files on OneDrive, it gives an error stating “Error: 0x80070185, Cloud operation was unsuccessful”. Therefore, they cannot perform any operations on OneDrive such as copying files, pasting, downloading shared files, etc. Nowadays, it is necessary to use these operations in our daily work. This error can be easily solved and for this we have some methods that we can apply and try to solve the problem. let's start! Method 1 – Sign out and sign back in to OneDrive app steps
 How to solve if Edge browser is blocked by firewall?
Mar 13, 2024 pm 07:10 PM
How to solve if Edge browser is blocked by firewall?
Mar 13, 2024 pm 07:10 PM
How to solve the problem that the Edge browser is blocked by the firewall? Edge browser is Microsoft's own browser. Some users found that this browser was blocked by the firewall during use. So what's going on? Let this site give users a detailed introduction on how to recover the Edge browser if it is blocked by the firewall. How to restore the Edge browser if it is blocked by the firewall? 1. Check the firewall settings: - Click the "Start" button on the Windows taskbar, and then open "Settings". -In the Settings window, select Update & Security. -exist
 Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
When setting up the firewall, many friends found that their win11 firewall advanced settings were grayed out and unable to be clicked. This may be caused by not adding a control unit, or by not opening the advanced settings in the correct way. Let’s take a look at how to solve it. Win11 firewall advanced settings gray method one: 1. First, click the start menu below, search and open "Control Panel" at the top 2. Then open "Windows Defender Firewall" 3. After entering, you can open "Advanced Settings" in the left column . Method 2: 1. If the above method cannot be opened, you can right-click "Start Menu" and open "Run" 2. Then enter "mmc" and press Enter to confirm opening. 3. After opening, click on the upper left
 Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
After installing the latest operating system on your PC, activating your copy of Windows 11 is the main job. Not only does it unlock the true potential of the Windows 11 operating system, but it also gets rid of the annoying "Activate your Windows 11" message. However, for some users, Windows 11 activation error 0xc004f074 hinders the smooth progress of activation. This bug apparently prevents users from activating Windows 11 and forces them to use an operating system with limited functionality. Windows 11 activation error code 0xc004f074 is related to the Key Management Service. You will encounter this problem when KMS is unavailable. Okay, that's it for this tutorial
 How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
On AlpineLinux, you can use the iptables tool to configure and manage firewall rules. Here are the basic steps to enable or disable the firewall on AlpineLinux: Check the firewall status: sudoiptables -L If the output shows rules (for example, there are some INPUT, OUTPUT, or FORWARD rules), the firewall is enabled. If the output is empty, the firewall is currently disabled. Enable firewall: sudoiptables-PINPUTACCEPTsudoiptables-POUTPUTACCEPTsudoiptables-PFORWARDAC
 How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
Many friends who use win10 system find that there is a firewall logo on the icon on the computer desktop. What is going on? This makes many friends with obsessive-compulsive disorder particularly uncomfortable. In fact, we only need to open the control panel and click " It can be solved by changing "Change User Account Control Settings". Let's take a look at the specific tutorial. How to cancel the firewall logo on the desktop icon in Windows 10 1. First, right-click the Start menu button next to the computer startup screen, and then select the Control Panel function from the pop-up menu. 2. Then select the "User Account" option and select the "Change User Account Control Settings" item from the new interface that appears. 3. After adjusting the slider in the window to the bottom, click Confirm to exit.
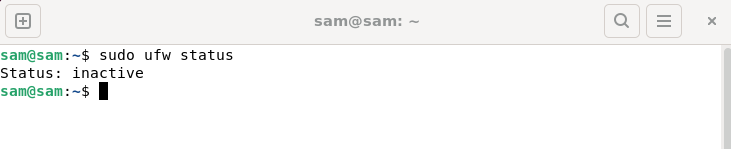 How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
UFW, also known as Uncomplex Firewall, is adopted by many Linux distributions as their firewall system. UFW is designed to make it easy for novice users to manage firewall settings through both the command line interface and the graphical user interface. A UFW firewall is a system that monitors network traffic according to set rules to protect the network from network sniffing and other attacks. If you have UFW installed on your Linux system but its status shows as inactive, there could be several reasons. In this guide, I will share how to resolve the UFW firewall inactive issue on Linux systems. Why UFW Shows Inactive Status on Linux Why UFW Is Inactive by Default on Linux How to Inactive on Linux
 How to avoid Web Shell attacks in Nginx firewall
Jun 10, 2023 pm 09:07 PM
How to avoid Web Shell attacks in Nginx firewall
Jun 10, 2023 pm 09:07 PM
With the increase of Web applications, security has become an increasingly important issue. In these applications, WebShell is a common security threat. A WebShell is an executable web script that can be uploaded and executed via HTTP or other web protocols. For attackers, WebShell is an important way to access web servers and obtain sensitive information. Nginx firewall is a popular web server software that can be used to protect web applications from attacks.






