
ipp printer refers to a printer that uses the ipp protocol. IPP stands for "Internet Printing Protocol" and is a standard network protocol for printing on the Internet. The IPP protocol allows users to manage printers connected to the Internet and send printer jobs to online host printers; users can control various parameters such as paper type and resolution used for printed products through relevant interfaces.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
ipp printer refers to a printer that uses the ipp protocol.
IPP stands for "Internet Printing Protocol" and as the name suggests, this protocol allows users to manage printers connected to the Internet and send printer jobs to online host printers. The difference between IPP and many other printer management protocols is that IPP is a security protocol that supports advanced features such as access control lists, authentication, and encrypted communications, however, this does not mean that the device owner is using these features.

wireshark captures the packet analysis and parses out the print file name, file, and IP port , Username;
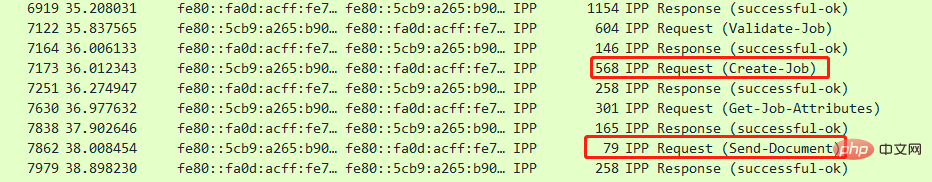
## 1. Agreement Description
Internet Printing Protocol (IPP; InternetPrintingProtocol) is a standard network protocol for printing on the Internet. It allows users to print remotely and manage print jobs through the Internet. Users can control various parameters such as paper type and resolution used for printed products through relevant interfaces;IPP uses the Hypertext Transfer Protocol HTTP POST method to conduct conversations between the client and the print server. . Described by the object model involved in the IPP protocol, there are three types of objects:Communication method
##2. TCP data flow analysis Both the client and the server rely on the HTTP protocol for transmission, and the operation layer uses the inherent format of the message body of HTTP requests and responses (see
3for details) Message structure ) Interaction; (1) Single document printing
print-job: The client wants to submit a print job that contains only a single document. Document data will be sent with the request.
(2) Multiple document printing
Create-job: The client wants to submit a print job containing multiple documents. Documents are sent using send-document and send-uri operations.
Send-document: The client wants to add a document to a print job created using the print-job operation. Document data will be sent with the request.
print-job: The client is submitting a print job that contains only a single document. Document data will be sent with the request.
3. Message structure
3.1 Operation request and response encoding
------- --------------------------------------------------
| Version number -----------------------
| Operation ID (request) or |
| Status code (response) | Request 2 bytes
---------------------------------------- --------------
| Request ID | Requires 4 bytes
-------------- ---------------------------------------
| Group
--------------------------| Attribute end tag | 1 byte
------ ------------------------------------------------| Data --------------------------The fourth field is the "Attribute Group" field, which allows 0 or more occurrences. Each "property group" field represents a single set of properties, such as an operation property group or a job property group (see document model). The IPP model file specifies the required set of attributes and their order for each operation request and response.The "End Tag" field is always present
, even when "data" does not exist.The model document specifies whether the "data" field exists for each operation request and response.
3.2 Attribute Group-------------------------- ----------------------------
| Attribute group start tag | 1 byte-------------------------------------------------- ----
|Attributes
to ---------------------------------------------"Attribute group start tag" The field marks the beginning of an attribute group, and its value identifies thetype of the attribute group
. For example, aoperation attribute group and a job attribute group . The "attribute group start tag" also marks the end of the previous attribute group unless it is the first attribute group in the request or response. The "Attribute Start Tag" field serves as the termination of an "Attribute Group" because an "Attribute Group" field cannot be nested within another "Attribute Group" field.
An attribute group field contains zero or more "attribute" fields.
Note: The "Attribute Group Start Tag" field and the "Attribute Group End Tag" field are called "delimiter tags".
3.3 Attributes
The "Attribute" field is coded as follows:
-------------- ----------------------------------------
| Single value attribute . --------------------
| r bytes (0 or more)Added value
#------------------------------------------------ -----When an attribute is single-valued (e.g. "Copy" has a value of 10) or is multi-valued but only takes one value (e.g. "Multi-party support" only takes the value 'unilateral') , then it is only encoded with the "single value attribute" field. When an attribute is multi-valued and takes n values (e.g. "multi-party support" takes the values 'unilateral' and 'two-sided long boundary'), it is encoded with an "attribute single value" field, followed by n-1 "additional values" field.
3.4 Single value attribute (key value)
------------------------ ----------------------------------| Value tag ’ ’ s ’ s through ’ through ’s ‐ to 1-byte---- -------------------------------------------------- ----
| Key name length (unitu
) | 2 bytes------------- ---------------------------------------| #ubytes--------------------------------------------- ------------------
| Value value length (unit
v) | 2 bytes-- -------------------------------------------------- --
| ----------------------------------
"Single value attribute" is encoded by five fields:
The "value label" field specifies the syntax of the attribute, for example,
0x44represents the attribute syntax "
keyword".
The "Name Length" field specifies the length of the "Name" field in bytes. For example, u or 15 in the above figure indicates that the name is "Multi-Party Support". The "Name" field contains a text name attribute, such as "Bilateral Support". The "Value Length" field specifies the length of the "Value" field in bytes. For example, v or 9 in the above figure indicates the value "unilateral".
The "Value" field contains attributes of the value, such as the text value "One Side".
3.5 Added value
------------------------- ----------------------------------
| use using using ‐ ‐ ‐ ‐ ‐ #------------------------------------------------ -----
|
---------------------------------------- -------------| Value length (unitw) | 2 bytes------ -------------------------------------------------- | -----------------------
Added value uses 4 fields to encode:The "value label" field specifies the attribute syntax, for example, 0x44 indicates the attribute syntax "keyword".
The "name length" field can take a value of 0 to indicate that this is an "additional value".The value of the "Name Length" field is the "Additional Value" field ("Name Length" is 0
) and the "Single Value Attribute" field ("Name Length" is not
0
The "Value" field contains the value attribute, such as the text value "Both sides long boundary". 4. Structure parameters
//属性值;
struct _ipp_attr_value{
char type;//属性类型
short len;//值长度
std::string value;//值内容
};
//一个属性包括一个属性名name,零个或者多个属性值;
typedef struct _ipp_attr{
std::string name;//属性名称
std::vector<_ipp_attr_value *> values;//一个或者多个属性值
}IPP_ATTR;
//一个属性组包括一个组TAG,零个或者多个属性;
struct _ipp_attr_seq{
char seq;//属性组类型
std::vector<IPP_ATTR *> attr;//一个或者多个属性
};
typedef struct _ipp{
int data_left;//移动剩下的数据长度
short version;//版本号
union{
short int operation;//操作码
short int response;//响应码
};
int request_id;//请求ID
//零个或者多个属性组
std::vector<_ipp_attr_seq *> seqs;// 一个或者多个属性组
}IPP;
IPP *m_ipp;//IPP结构
short int m_bufptr;//记录buf移动位置For example, experts at Shadowserver say that this port can be used to gather intelligence: because a large portion of IPP-enabled printers (such as printer name, location, model, firmware version, organization name, and even WiFi network name) are returned Additional information about themselves, an attacker can collect this information and then use this information to examine the company network to facilitate future attacks. In addition, a quarter of the IPP-enabled printers (approximately 21,000 units) also revealed details of their design and manufacturing. Disclosing this information apparently makes it easier for attackers to find specific vulnerable groups of devices.
The bad thing is, IPP hacking tools are also available online. Programs such as PRET (Printer Operations Toolkit) support IPP hacking and have been used in the past to hijack and force printers to print various promotional messages, possibly even taking over a vulnerable device entirely.Shadowserver The Foundation said it plans to publish a daily IPP exposure report on its website in the future. "We hope that sharing IPP device data reporting in our new open space will reduce the number of exposed IPP-enabled printers and increase awareness of the dangers of exposing such devices to unauthenticated scanners/attackers. Awareness." Companies or national CERT teams that subscribe to organizational security alerts will receive automatic notifications when any IPP services are exposed online in the country's network and IP address space. The Shadowserver Foundation's forward-looking recommendations for dealing with devices exposed to the Internet are consistent with academic research last year, which found that DDoS takedowns are often ineffective and that law enforcement should focus on patching systems to limit attacker. It is also recommended that users read the printer's manual to configure IPP access control and IPP authentication functions to protect the printer before it is exploited. Most printers in the management panel have an IPP configuration section. From there, users can enable authentication, encryption and restrict access to the device via access lists. For more related knowledge, please visit the FAQ column!
The above is the detailed content of what is ipp printer. For more information, please follow other related articles on the PHP Chinese website!
 Why does the printer not print?
Why does the printer not print?
 Printer installation failed
Printer installation failed
 Set default printer
Set default printer
 0x00000006 What to do if the printer cannot be connected?
0x00000006 What to do if the printer cannot be connected?
 windows cannot open add printer
windows cannot open add printer
 How to restore normal printing when the printer is offline
How to restore normal printing when the printer is offline
 Why does the printer not print?
Why does the printer not print?
 Reasons why Windows printer does not print
Reasons why Windows printer does not print