Found a total of 10000 related content

How to solve the Bitcoin ransomware virus
Article Introduction:How to deal with the Bitcoin ransomware virus: 1. Identify the ransom message; 2. Disconnect from the network; 3. Quarantine files; 4. Contact law enforcement; 5. Back up data; 6. Scan for viruses; 7. Consider payment (not recommended); 8 .Restore pre-infection status (only if other methods fail).
2024-08-09
comment 0
1047
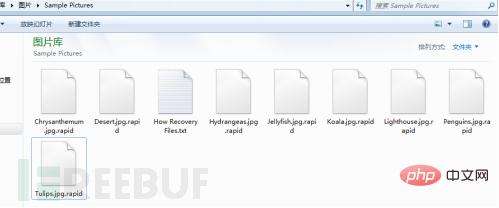
How to analyze and detect Rapid ransomware virus
Article Introduction:Ransomware has always been a hot topic in the security industry. Recently, security personnel have discovered a ransomware called rapid. This ransomware uses RSA and AES to encrypt files. It will not only infect existing files on the computer, but also Encrypt newly created files. This article conducts a detailed analysis of the rapid virus, analyzes its encryption mechanism, and parses its encrypted files. 1. Overview When the rapid virus runs, it will create multiple threads to continuously scan the file system and encrypt files. It will not only infect existing files on the computer, but also encrypt newly created files. The encrypted file has a ".rapid" extension added to its file name, and the file size is increased by 0x4D0 bytes. rapid virus
2023-05-13
comment 0
1466

How to deal with ransomware attacks?
Article Introduction:Ransomware attacks are a common cybersecurity threat that extort ransom by encrypting a user's important files or blocking access to a computer system. Ransomware attacks can cause huge losses to individuals and businesses, so we must take the right steps to prevent and respond to this threat. First, back up your data regularly. Regular backups can at least reduce the risk of losing important data. During the backup process, it is best to back up to both external devices and cloud storage to prevent the external storage device from being locked if the computer system is infected. in addition,
2023-06-11
comment 0
2585

What are the ransomware ports?
Article Introduction:The ransomware ports are 135, 139, 138, 137 and 445; they can be prevented by closing the ports. Specific method: first close the port in the firewall; then open the "Local Group Policy Editor", click "Windows Settings" - "Security Settings" - "IP Security Policy", create an IP security policy and close the relevant ports.
2021-02-02
comment 0
26162

Thoughts on data security under the threat of ransomware
Article Introduction:Introduction On May 12, the WannaCry (Wanna Cry) ransomware broke out globally. In just 24 hours, it swept through more than 150 countries around the world at lightning speed and infected more than 300,000 computers. Joint monitoring by the National Computer Virus Emergency Response Center also found that a "ransomware" similar to WannaCry has appeared abroad. It will encrypt victim users' files and rename them. The new file names will have the ".UIWIX" suffix; the center has not yet collected Reports of infections among domestic users have been reported, reminding the country to be more vigilant. The booming development of the Internet era has brought convenience and future expectations beyond imagination. At the same time, it has inevitably increased the risk of leakage of personal data and privacy. This ransomware incident also
2024-01-08
comment 0
868
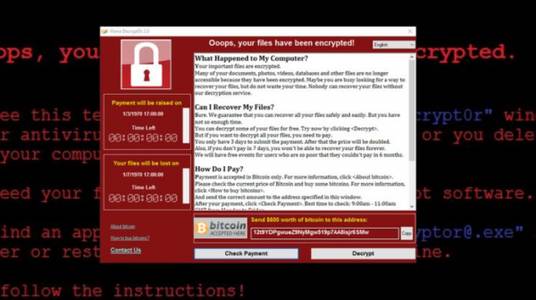
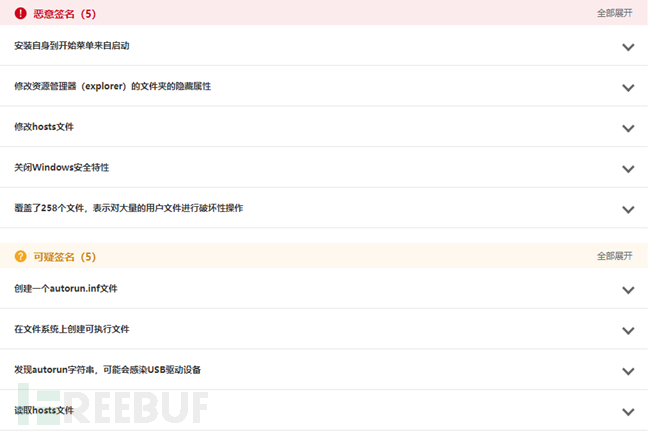
How to analyze XiaoBa ransomware variants
Article Introduction:Overview XiaoBa ransomware is a new type of computer virus. It is a highly domestically produced ransomware virus. It is mainly spread through emails, program Trojans, and web page Trojans. This virus uses various encryption algorithms to encrypt files. The infected person generally cannot decrypt the files and must obtain the decrypted private key to crack them. If the ransom is not paid within 200 seconds, all encrypted files will be destroyed. The above description is taken from Baidu Encyclopedia, but the XiaoBa variant I analyzed does not have the above behavioral characteristics. However, it has strong concealment and infectivity, and has three main functions: file encryption, file deletion and mining. Sample analysis: This sample has been analyzed by Weibu Cloud Sandbox (see "Reference Links" for related links) and confirmed to be malicious.
2023-05-26
comment 0
1570

What is the method to deal with ransomware virus?
Article Introduction:Ransomware disposal methods are to isolate infected servers/hosts and prevent new infections. Detailed introduction: 1. Isolate the infected host. Isolation mainly includes two means: physical isolation and access control. Physical isolation mainly means disconnecting the network or power, and access control mainly refers to strict authentication and control of permissions to access network resources; 2. To prevent new infections, immediately change the login password of the infected server. Secondly, modify the security settings of databases, shared folders, user mailboxes, etc. to restrict access by illegal users.
2023-09-04
comment 0
1911

What does Bitcoin blackmail virus mean? A simple explanation of Bitcoin blackmail virus
Article Introduction:Bitcoin extortion virus is a type of ransomware that encrypts victim files and demands ransom in Bitcoins. The following steps can be taken to prevent Bitcoin extortion viruses: 1. Disconnect from the Internet; 2. Do not pay the ransom; 3. Back up files; 4. Use anti-virus software; 5. Report to law enforcement agencies; 6. Seek professional help. Preventive measures include: 1. Update software; 2. Use strong passwords; 3. Watch out for suspicious emails and websites; 4. Use antivirus software; 5. Back up files regularly.
2024-07-05
comment 0
576

Lockbit ransomware virus member pleads guilty in the United States! Most of the money that attracted more than 500 million US dollars was Bitcoin.
Article Introduction:This site (120bTC.coM): The U.S. Department of Justice announced on Thursday that 21-year-old Russian citizen Ruslan Magomedovich Astamirov and 31-year-old Mikhail Vasiliev, a dual citizen of Canada and Russia, have admitted to participating in the ransomware hacker group LockBit, which targeted victims in the United States and around the world. Launch a LockBit ransomware attack. The announcement pointed out that between January 2020 and February 2024, LockBit once became the most active and destructive ransomware group in the world, attacking more than 2,500 victims in at least 120 countries, including 1,800 in the United States. Victims, including individuals, small businesses
2024-07-22
comment 0
939

Can python write viruses?
Article Introduction:Can. The National Computer Virus Emergency Response Center discovered through monitoring the Internet that a malicious Trojan horse program written in Python language appeared. This malicious program spreads by disguising itself as a variety of commonly used application software, inducing computer users to download and install it. This new ransomware is called Dablio and can theoretically infect all commonly used files.
2019-06-20
comment 0
10826

Computer virus emergence time
Article Introduction:The first computer virus appeared in the 1970s, but as early as 1949, computer pioneer John Van Newman had already outlined the blueprint of a virus program in a paper he proposed.
2019-11-01
comment 0
5900

How to turn on ransomware protection in Windows 11 Steps to turn on ransomware protection
Article Introduction:1. First, right-click this computer on the desktop and open the Properties panel. 2. Then, click the Protectionsecurity menu to open the Windows Security Center option. 3. Then, find and click the Virus and Threat Protection button. 4. Finally, click on the Microsoft Defender Antivirus option. , turn on ransomware protection.
2024-06-02
comment 0
1144











