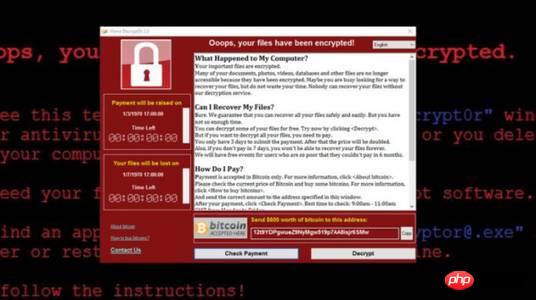
看到这个画面,恭喜你!你中奖了!说明你中了比特币勒索病毒,所有的服务器web文件都被加密,一般要求你支付3个比特币才能解密,一比特币大概等于10000人民币,3个比特币也是30000多元。如下图
国家网络与信息安全信息通报中心最新通报:
监测发现,在全球范围内爆发的WannaCry 勒索病毒出现了变种:WannaCry 2.0。
与之前版本的不同是,这个变种取消了Kill Switch,不能通过注册某个域名来关闭变种勒索病毒的传播,该变种传播速度可能会更快。
请广大网民尽快升级安装Windows操作系统相关补丁,已感染病毒机器请立即断网,避免进一步传播感染。
此前通报:
国家网络与信息安全信息通报中心更早之前紧急通报称:2017年5月12日20时左右,新型“蠕虫”式勒索病毒爆发,目前已有100多个国家和地区的数万台电脑遭该勒索病毒感染,我国部分Windows系列操作系统用户已经遭到感染。
请广大计算机用户尽快升级安装补丁,地址为:https://technet.microsoft.com/zh-cn/library/security/MS17-010.aspx。
Windows 2003和XP没有官方补丁,相关用户可打开并启用Windows防火墙,进入"高级设置",禁用"文件和打印机共享"设置;或启用个人防火墙关闭445以及135、137、138、139等高风险端口。
已感染病毒机器请立即断网,避免进一步传播感染。

分析:勒索软件的威胁远未消失
网络安全专家指出,勒索软件网络攻击大规模爆发于北京时间12日晚8点左右,当时国内有大量机构和企业的网络节点已关机,因此15日开机将面临安全考验。许多重要的计算机系统处于内网环境,无法访问前述域名,并且也可能无法及时更新安全补丁,因此仍可能面临较大风险。
网络安全专家建议,用户要断网开机,即先拔掉网线再开机,这样基本可以避免被勒索软件感染。开机后应尽快想办法打上安全补丁,或安装各家网络安全公司针对此事推出的防御工具,才可以联网。
被该勒索软件入侵后,用户主机系统内的照片、图片、文档、音频、视频等几乎所有类型的文件都将被加密,加密文件的后缀名被统一修改为.WNCRY,并会在桌面弹出勒索对话框,要求受害者支付价值数百美元的比特币到攻击者的比特币钱包,且赎金金额还会随着时间的推移而增加。
国家互联网应急中心博士、工程师韩志辉表示,目前,安全业界暂未能有效破除该勒索软件的恶意加密行为。用户主机一旦被勒索软件渗透,只能通过专杀工具或重装操作系统的方式来清除勒索软件,但用户重要数据文件不能完全恢复。
服务器中了比特币勒索病毒怎么办?
建议解决方案:
除了国家网络与信息安全信息通报中心的建议外,我们帮您整理了一份临时解决方案,现在就手把手教你:如何设置电脑,防范勒索病毒。
临时解决方案:
开启系统防火墙
利用系统防火墙高级设置阻止向445端口进行连接(该操作会影响使用445端口的服务)
打开系统自动更新,并检测更新进行安装
360公司发布的“比特币勒索病毒”免疫工具下载地址:http://dl.360safe.com/nsa/nsatool.exe
恢复数据的步骤:
1:先杀干净病毒
如果用免费的杀软,建议使用360安全卫士11,目前可以查杀到加密病毒。如图
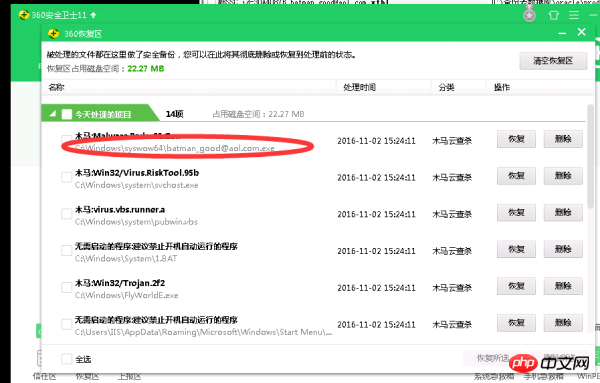
-注意-wallet病毒邮箱有2个http://india.com或者http://aol.com,那么会查杀到一个payload_xxxx.exe.
2:修改中毒前的RDP(远程桌面控制)弱口令(密码)
(有些童鞋说我的QWEasd!@#,这样的密码强不强,我只能说你老板给你开的工资太低了,用这样的口令和你开着门让黑客进来没区别)
3:恢复数据
A:XTBL请使用免费的卡巴斯基破解工具 http://media.kaspersky.com/utilities/VirusUtilities/RU/rannohdecryptor.zip?_ga=1.69588624.1814211149.1453294100(亲测有效,请在测试前备份避免损坏文件)
B:wallet作为XTBL的变种病毒,目前wallet加密数据目前没有破解工具,只能支付比特币给黑客处理(一般黑客报价是3个比特币,合计人民币30000元左右),如果你不急使用数据,请耐心等待卡巴斯基爆出,数据越急越需要注意风险,请找专业的有经验的人士处理。
恢复实例快照:这是一台70多万个文件被加密为fly_goods@aol.com.wallet后缀的服务器,通过购买私钥完成了60多万个文件的恢复,耗时4小时20分钟,估计全部恢复正常得要1-2天,恢复文件70万个大约要5个小时,重新配置服务器环境最少1天。------麻痹的黑客,exe应用你也加密。
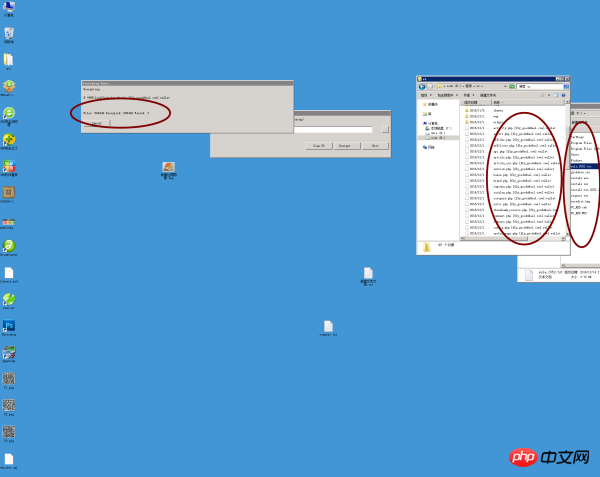
C:一般好一点的服务器都自带磁盘快照功能,你可以先将快照恢复到感染之前,最大可能的降低损失,再启用个人防火墙关闭445以及135、137、138、139等高风险端口,再安装必要的杀毒软件,打上最新的补丁。
【猜你喜欢】
1.php中文网特别推荐:php程序员工具箱下载(一键搭建php环境)

每个人都需要一台速度更快、更稳定的 PC。随着时间的推移,垃圾文件、旧注册表数据和不必要的后台进程会占用资源并降低性能。幸运的是,许多工具可以让 Windows 保持平稳运行。

Copyright 2014-2025 //m.sbmmt.com/ All Rights Reserved | php.cn | 湘ICP备2023035733号