
XiaoBa ransomware is a new type of computer virus. It is a highly domestically produced ransomware virus. It is mainly spread through emails, program Trojans, and web page hanging horses. . This virus uses various encryption algorithms to encrypt files, making it difficult for the infected to decrypt them. Only by obtaining the decrypted private key can the virus be successfully cracked. If the ransom is not paid within 200 seconds, all encrypted files will be destroyed.
The above description is taken from Baidu Encyclopedia, but the XiaoBa variant I analyzed does not have the above behavioral characteristics, but it has strong concealment and infectivity, and has file encryption, file deletion and mining. Three main functions.
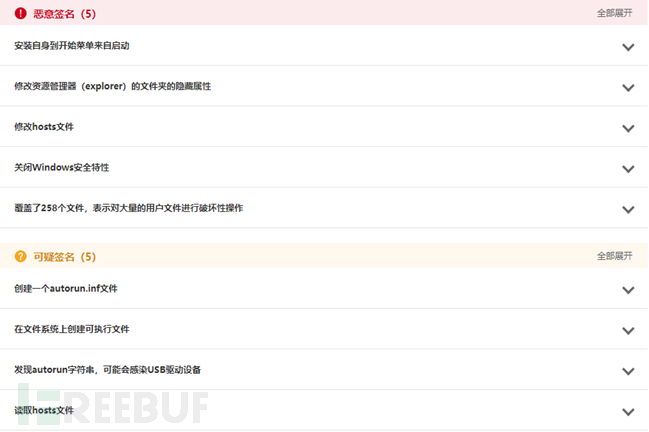
This sample has been analyzed by Weibu Cloud Sandbox (see "Reference Links" for related links) and confirmed to be a malicious sample
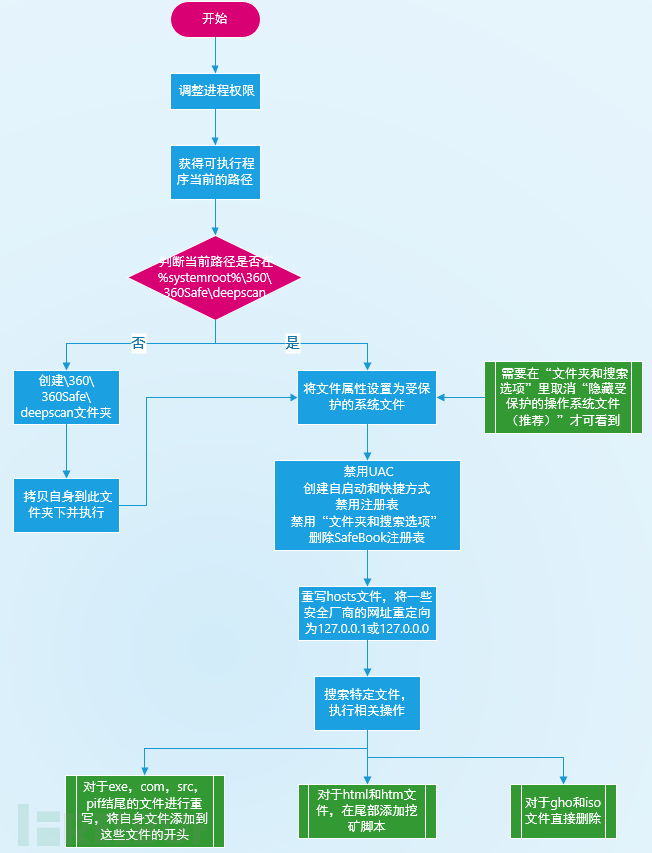
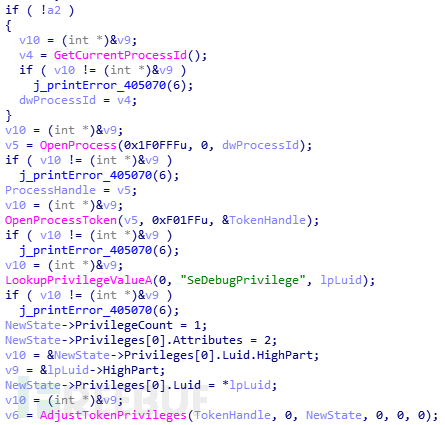
After running the sample, first adjust the process permissions to ensure that you have sufficient permissions for subsequent operations Operation
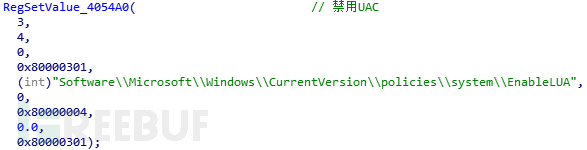
This path Judgment: The sample will determine whether the current execution path is%systemroot%\ 360 \ 360safe \ deepscan directory. directory and execute. If you are in this path, you will first perform some operations related to modifying system settings:
To set the file attributes to protected system files, you need to enter the "folder and Uncheck the "Hide protected operating system files (recommended)" option in Search Options" to see
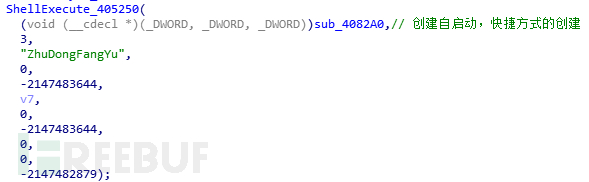
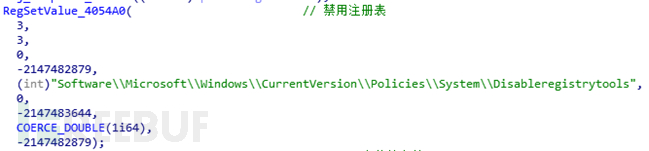
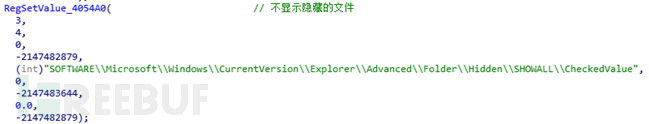
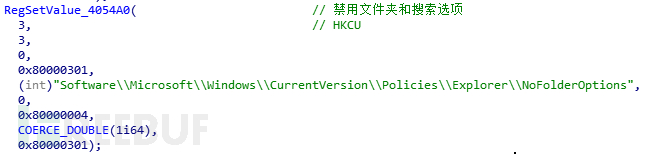
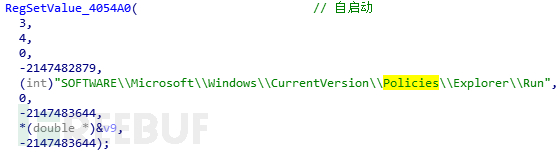

Traverse the disk, create the autorun.inf file in the root directory of the disk, write the following data, try to infect the U disk, and inevitably This file is set to be hidden
Create the folder RECYCLER\S-5-4-62-7581032776-5377505530-562822366-6588, and copy its own file in to rewrite the hosts file and redirect the security manufacturer's website
Finally create a thread. In the thread function, XiaoBa will traverse all files and look for extensions of .exe, .com, .scr, .pif, .html, .htm, .gho , .iso files, perform different operations for different extensions. .exe, .com, .scr, .pif
rewrite these files and write their own files to the beginning of these files. If you later If you run these files, ZhuDongFangYu.exe
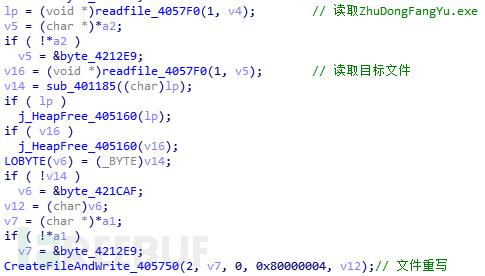
.html, .htm
will be run. Add the mining script
# at the end of these files. ##.gho, .isoFor these files, delete them directly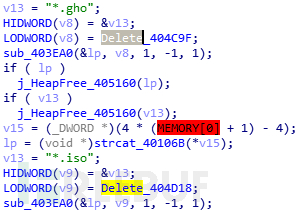
The above is the detailed content of How to analyze XiaoBa ransomware variants. For more information, please follow other related articles on the PHP Chinese website!




