
File mapping is a mechanism that maps files on disk to the virtual memory space of a process.
In this way, the process can read and write files directly through the memory address without having to go through regular system calls such as read and write.
In file mapping, we connect the file to the virtual memory of the process through the Linux mechanism, so that the process can directly read and write file data in the memory without directly accessing the disk. This mechanism provides a more efficient file access method and also simplifies the file operation process.
File mapping is often called memory mapping, and the two are usually the same. Memory mapping covers the operations of mapping files to memory and mapping anonymous memory to the process address space.
File mapping is a special case of memory mapping.
View the file mapping information of the corresponding process
$ pmap -X 12345#查看指定PID的文件映射信息 12345: ./example 0000555555554000100K r-x-- example 00005555556730004K r---- example 00005555556740004K rw--- example 00007ffff7de0000 1360K r-x-- libc-2.31.so ... mapped: 1448Kwriteable/private: 8Kshared: 0K
Use thecat /proc/PID/mapscommand to view the memory mapping of the process.
Each line represents a memory mapped area, the format is as follows:
address perms offsetdev inodepathname 00400000-0040b000 r-xp 00000000 08:01 1167685/usr/bin/cat 0060a000-0060b000 r--p 0000a000 08:01 1167685/usr/bin/cat 0060b000-0060c000 rw-p 0000b000 08:01 1167685/usr/bin/cat
Now we demonstrate through an example how to use file mapping to map a file into memory, then modify the contents in memory, and finally demonstrate by unmapping the memory.
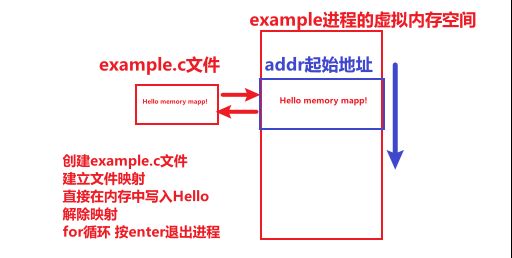
example.c file
#include#include #include #include #include #include #include #include int main() { const char *file_path = "example.txt"; const size_t file_size = 4096; int fd = open(file_path, O_RDWR | O_CREAT, S_IRUSR | S_IWUSR); if (fd == -1) { perror("open"); exit(EXIT_FAILURE); } if (ftruncate(fd, file_size) == -1) { perror("ftruncate"); close(fd); exit(EXIT_FAILURE); } // Create a memory-mapped region void *addr = mmap(NULL, file_size, PROT_READ | PROT_WRITE, MAP_SHARED, fd, 0); if (addr == MAP_FAILED) { perror("mmap"); close(fd); exit(EXIT_FAILURE); } // Now 'addr' points to the beginning of the file in memory // 现在addr表示文件在进程的内存空间代表区域的起始位置 // Write a message to the memory-mapped file // 向映射文件写入一句消息。 const char *message = "Hello, Memory Mapping!n"; strncpy(addr, message, strlen(message)); printf("Press Enter to exit...n"); getchar();// Wait for user to press Enter // Unmap the memory region解除文件和内存区域的映射关系 if (munmap(addr, file_size) == -1) { perror("munmap"); close(fd); exit(EXIT_FAILURE); } // Close the file descriptor close(fd); return 0; }
Compile and execute:
$ ls example.c $ gcc example.c -o example $ ./example Press Enter to exit...
View the file mapping information of the process:
$ ps aux|grep example codersong 15245420.00.0 27761152 pts/0S+ 19:23 0:00 ./example codersong 15245470.00.0121882432 pts/2S+ 19:23 0:00 grep --color=auto example $ pmap -X 1524542 1524542: ./example 地址 Perm 偏移量 设备 Inode SizeRss Pss Pss_Dirty Referenced Anonymous LazyFree ShmemPmdMapped FilePmdMapped Shared_Hugetlb Private_Hugetlb Swap SwapPss Locked THPeligible Mapping 557b482c3000 r--p0000000008:03 712405144 4 04 000 00 00 00 0 example 557b482c4000 r-xp0000100008:03 712405144 4 04 000 00 00 00 0 example 557b482c5000 r--p0000200008:03 712405144 4 04 000 00 00 00 0 example 557b482c6000 r--p0000200008:03 712405144 4 44 400 00 00 00 0 example 557b482c7000 rw-p0000300008:03 712405144 4 44 400 00 00 00 0 example 557b48e9e000 rw-p0000000000:00 01324 4 44 400 00 00 00 0 [heap] 7f8fe5600000 r--p0000000008:03264612160160 7 0160 000 00 00 00 0 libc.so.6 7f8fe5628000 r-xp0002800008:03264612 162078824 0788 000 00 00 00 0 libc.so.6 7f8fe57bd000 r--p001bd00008:03264612352 64 1 0 64 000 00 00 00 0 libc.so.6 7f8fe5815000 r--p0021400008:03264612 16 161616 161600 00 00 00 0 libc.so.6 7f8fe5819000 rw-p0021800008:0326461288 8 88 800 00 00 00 0 libc.so.6 7f8fe581b000 rw-p0000000000:00 0 52 202020 202000 00 00 00 0 7f8fe58f6000 rw-p0000000000:00 0 128 8 88 800 00 00 00 0 7f8fe5908000 rw-p0000000000:00 084 4 44 400 00 00 00 0 7f8fe590a000 r--p0000000008:0326460088 0 08 000 00 00 00 0 ld-linux-x86-64.so.2 7f8fe590c000 r-xp0000200008:03264600168168 7 0168 000 00 00 00 0 ld-linux-x86-64.so.2 7f8fe5936000 r--p0002c00008:03264600 44 40 1 0 40 000 00 00 00 0 ld-linux-x86-64.so.2 7f8fe5941000 rw-s0000000008:03 712405244 4 04 000 00 00 00 0 example.txt 7f8fe5942000 r--p0003700008:0326460088 8 88 800 00 00 00 0 ld-linux-x86-64.so.2 7f8fe5944000 rw-p0003900008:0326460088 8 88 800 00 00 00 0 ld-linux-x86-64.so.2 7ffef93f2000 rw-p0000000000:00 0132 121212 121200 00 00 00 0 [stack] 7ffef9485000 r--p0000000000:00 0 160 0 00 000 00 00 00 0 [vvar] 7ffef9489000 r-xp0000000000:00 084 0 04 000 00 00 00 0 [vdso] ffffffffff600000 --xp0000000000:00 040 0 00 000 00 00 00 0 [vsyscall] ==== ==== === ========= ========== ========= ======== ============== ============= ============== =============== ==== ======= ====== =========== 2780 1344 15296 13449600 00 00 00 0 KB $ $ $ cat /proc/1524542/maps 557b482c3000-557b482c4000 r--p 00000000 08:03 7124051/home/codersong/zhengshihong/example 557b482c4000-557b482c5000 r-xp 00001000 08:03 7124051/home/codersong/zhengshihong/example 557b482c5000-557b482c6000 r--p 00002000 08:03 7124051/home/codersong/zhengshihong/example 557b482c6000-557b482c7000 r--p 00002000 08:03 7124051/home/codersong/zhengshihong/example 557b482c7000-557b482c8000 rw-p 00003000 08:03 7124051/home/codersong/zhengshihong/example 557b48e9e000-557b48ebf000 rw-p 00000000 00:00 0[heap] 7f8fe5600000-7f8fe5628000 r--p 00000000 08:03 264612 /usr/lib/x86_64-linux-gnu/libc.so.6 7f8fe5628000-7f8fe57bd000 r-xp 00028000 08:03 264612 /usr/lib/x86_64-linux-gnu/libc.so.6 7f8fe57bd000-7f8fe5815000 r--p 001bd000 08:03 264612 /usr/lib/x86_64-linux-gnu/libc.so.6 7f8fe5815000-7f8fe5819000 r--p 00214000 08:03 264612 /usr/lib/x86_64-linux-gnu/libc.so.6 7f8fe5819000-7f8fe581b000 rw-p 00218000 08:03 264612 /usr/lib/x86_64-linux-gnu/libc.so.6 7f8fe581b000-7f8fe5828000 rw-p 00000000 00:00 0 7f8fe58f6000-7f8fe58f9000 rw-p 00000000 00:00 0 7f8fe5908000-7f8fe590a000 rw-p 00000000 00:00 0 7f8fe590a000-7f8fe590c000 r--p 00000000 08:03 264600 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2 7f8fe590c000-7f8fe5936000 r-xp 00002000 08:03 264600 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2 7f8fe5936000-7f8fe5941000 r--p 0002c000 08:03 264600 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2 7f8fe5941000-7f8fe5942000 rw-s 00000000 08:03 7124052/home/byzoro/zhengshihong/example.txt 7f8fe5942000-7f8fe5944000 r--p 00037000 08:03 264600 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2 7f8fe5944000-7f8fe5946000 rw-p 00039000 08:03 264600 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2 7ffef93f2000-7ffef9413000 rw-p 00000000 00:00 0[stack] 7ffef9485000-7ffef9489000 r--p 00000000 00:00 0[vvar] 7ffef9489000-7ffef948b000 r-xp 00000000 00:00 0[vdso] ffffffffff600000-ffffffffff601000 --xp 00000000 00:00 0[vsyscall]
Now pressctrl Cto exit the example program and view the contents of the example.txt file:
$ cat example.txt Hello, Memory Mapping!
The above is the detailed content of What are the methods to view Linux file mappings?. For more information, please follow other related articles on the PHP Chinese website!




