
Use CLI to display the current Nginx version
Nginx will display the version on error pages and in the "Server" response header field. We can verify this using the following command: Example output:
$ curl -I https://your-domain $ curl -I https://www.cyberciti.biz HTTP/2 200 server: nginx/1.17.10 (Ubuntu)date: Tue, 23 Jun 2020 09:36:49 GMTcontent-type: text/html; charset=UTF-8strict-transport-security: max-age=15768000x-whome: l-ncbz01-mg-wg
This is the output of my HTTP/502 error page showing the message:
Use the server_tokens directive to hide the Nginx version
You need to set server_tokens to off to hide the Nginx server version on Linux and Unix-like systems. Edit your nginx.conf file using a text editor such as vim/nano:
We can only set server_tokens in http, server or location context. I will add to my http section: This is what it looks like:
$ sudo vim /etc/nginx/nginx.confserver_tokens off;
http { ## Basic Settings ## charset utf-8; sendfile on; tcp_nopush on; tcp_nodelay on; log_not_found off; keepalive_timeout 65; types_hash_max_size 2048; client_max_body_size 16M; include /etc/nginx/mime.types; default_type application/octet-stream; ## Hide Nginx version ## server_tokens off; ## Security headers for Nginx ## add_header Strict-Transport-Security "max-age=15768000" always; add_header X-Content-Type-Options "nosniff" always; add_header X-Frame-Options "SAMEORIGIN" always; add_header X-Xss-Protection "1; mode=block" always; add_header Referrer-Policy strict-origin-when-cross-origin; add_header Feature-policy "accelerometer 'none'; camera 'none'; geolocation 'none'; gyroscope 'none'; magnetometer 'none'; microphone 'none'; payment 'none'; usb 'none'"; add_header Content-Security-Policy "default-src 'self' http: https: data: blob: 'unsafe-inline'" always; ## SSL Settings ## ssl_protocols TLSv1.3; access_log /var/log/nginx/access.log; error_log /var/log/nginx/error.log; ## Virtual Host Configs ## include /etc/nginx/conf.d/*.conf; include /etc/nginx/sites-enabled/*;}
Restart or reload the Nginx server normally:
sudo nginx -tsudo nginx -s reload
Verify whether the Nginx version is hidden
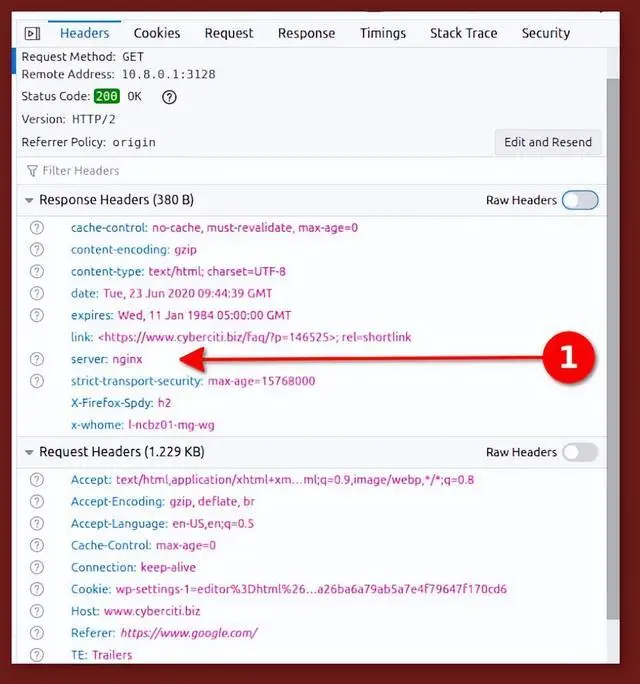
Use the curl command as follows: Looking at my Nginx server does not show any version:
$ curl -I https://your-domain-name-here $ curl -I https://www.cyberciti.biz HTTP/2 200 server: nginxdate: Tue, 23 Jun 2020 09:43:17 GMTcontent-type: text/html; charset=UTF-8strict-transport-security: max-age=15768000
Firefox also confirmed that I also successfully hidden the Nginx version:
Other possible values for hiding Nginx version
The syntax is as follows: The default settings on Linux, *BSD and Unix are as follows:
server_tokens on | off | build | string; server_tokens on;
Remove versions from server headers and error pages
We can enable or disable emitting nginx version by changing to the following value:
on: Display the version number.
off: Turn off displaying the version number.
build: Make sure we emit a build name as well as the nginx version. You must have Nginx version 1.11.10.
string: Available for commercial subscriptions only, starting in version 1.9.13, it is possible to use a string with a variable to display the signature and "server" response header field values on the settings error page. An empty string disables emitting of the "server" field.
Set a custom version number in Nginx
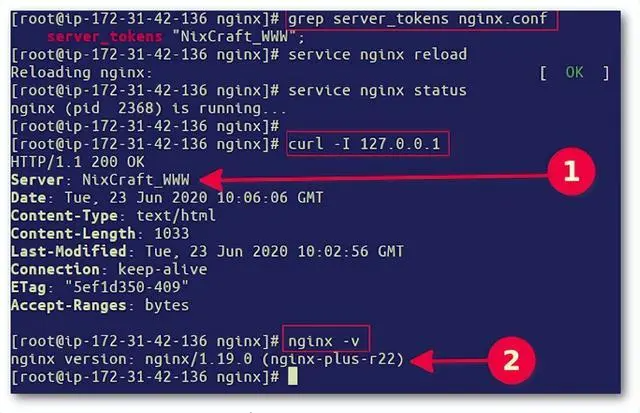
For example, commercial subscription (Nginx Plus) users can set it to a fake server version and a custom name: Reload the Nginx server using the service command or the systemctl command: Likewise, test it using the curl command as shown below :
;$ service nginx reload$ curl -I http://127.0.0.1/
Hidden versions are safe in obscurity
Yes, it is security via covert functionality. It is one of the methods of defense in depth. However, it should not be the primary form of defense. You need to write secure code. Install a firewall, especially a WAF (Web Application Firewall). There is no reason to expose the Nginx or PHP or Python version as it could be useful information to an attacker. Keep in mind that Linux/Unix operating systems, web apps/Nginx should remain secure regardless of whether the Nginx version is public or not. However, we do not provide any benefit to attackers by publishing version numbers.
The above is the detailed content of Hide Nginx version on Linux and Unix. For more information, please follow other related articles on the PHP Chinese website!




