
Mainly due to the lack of the following configuration code: nginx version 1.8.0
server {
listen 80 default_server;
server_name _;
return 403;
}Let all unconfigured server_name return 403 error
I have never added this configuration to nginx before , but I have never encountered such a problem before, and I tested it on another server. Even without this code, it is impossible to parse and request successfully. I am very speechless.
Supplement:
After searching around, I found that nginx should use its own unique 444 status code for this kind of problem. It is best
server {
listen 80 default_server;
server_name _;
access_log off;
return 444;
}This way on the browser side When accessing, the browser will automatically prompt the user that the user cannot access
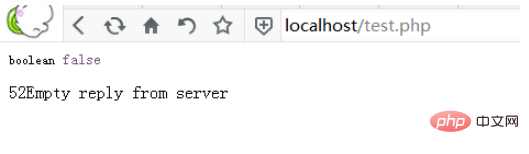
The results captured through curl (the output is http error message)
The above is the detailed content of How to prevent Nginx from being maliciously parsed by domain names. For more information, please follow other related articles on the PHP Chinese website!




