
Microsoft posted information about a new malware on its security website on April 12, 2022. The malware, dubbed Tarrask, exploits a vulnerability in the Windows task scheduling system to evade detection.
Tarrask is used by the hacking group Hafnium, which has targeted telecommunications, internet service providers and data services sectors in the past.
The group exploits zero-day vulnerabilities to attack computer systems. Once a system is successfully compromised, a vulnerability in Windows can be exploited to hide the malware's traces and make detection more difficult. Tarrask uses this bug to create hidden scheduled tasks to avoid detection and possibly for persistence.
Systems and applications use Windows Task Scheduler to initiate tasks, such as checking for updates or running maintenance operations. Applications can add tasks to Task Scheduler, provided they execute with sufficient permissions. According to Microsoft, malware often uses tasks to "maintain persistence in Windows environments."
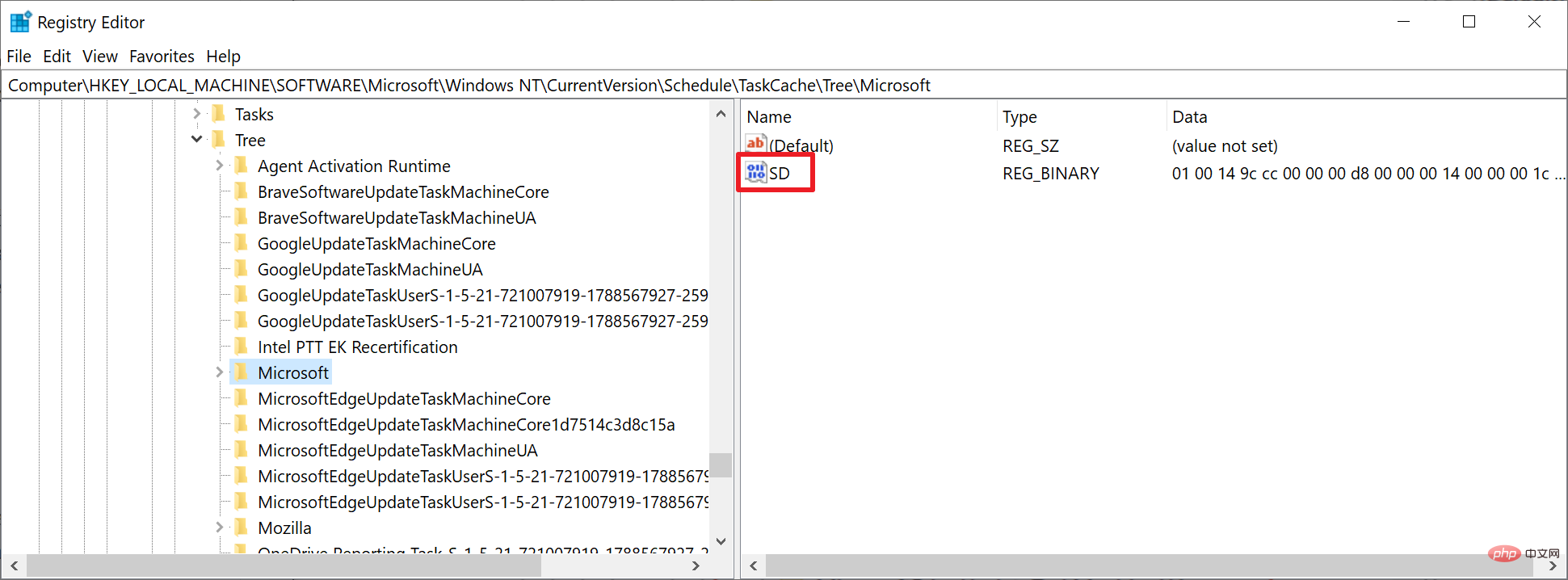
Tasks can be analyzed by launching the Task Scheduler tool on Windows. Tarrask uses an error to hide its tasks, and using the command line option "schtasks /query", it returns a list of existing scheduled tasks. To avoid detection, Tarrask deletes the task's security descriptor value in the Windows registry; this causes the task to disappear from Task Scheduler and command-line tools. In other words: A careful inspection of all tasks using either tool will not reveal a malicious task.
The malware does not completely delete task information as its traces are still recorded in the system registry. Microsoft suspects that the hacking group left data in the registry to allow the malware to persist, or that the group was unaware that the task would "keep running" after removing the SD component.
Windows administrators may analyze scheduled task information in the system registry to determine whether the system is infected with Tarrask malware:
If a task is found without an SD value, it is a hidden task and will not show up in Task Scheduler or the command line utility. The task cannot be deleted normally because it is run in the context of the SYSTEM user. Attempts to delete the task will fail with an access denied error message.
The latest version of Microsoft's Windows Defender security application has detected malware. Microsoft has added a new watch event to Windows Defender for detecting hidden tasks; these are marked as Behavior:Win32/ScheduledTaskHide.A and then used by applications.
Microsoft recommends that system administrators adopt the following recommendations and security guidelines to detect malware using attack vectors:
Enumerate your Windows environment registry hives, view HKEY_LOCAL_MACHINE\SOFTWARE \Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree registry hive and identifies any scheduled tasks that do not have an SD (security descriptor) value in the task key. Analyze these tasks as needed.
Modify your audit policy to identify scheduled task operations by enabling logging "TaskOperational" in Microsoft-Windows-TaskScheduler/Operational. Apply the recommended Microsoft audit policy settings appropriate for your environment.
Enable and centralize the following Task Scheduler logs. Even if tasks are "hidden", these logs will track key events related to them, which may lead you to discover well-hidden persistence mechanisms in the Security.evtx log Microsoft-Windows-TaskScheduler/Operational.evtx log
EventID 4698Threat actors in this campaign use hidden scheduled tasks to maintain access to critical assets exposed on the internet by regularly re-establishing outbound communications with the C&C infrastructure. Stay alert and monitor outbound communications for unusual behavior by ensuring these connections from these critical Tier 0 and Tier 1 assets are monitored and alerted.
The above is the detailed content of How to detect Windows Tarrask malware using errors to avoid detection. For more information, please follow other related articles on the PHP Chinese website!




