This article brings you relevant knowledge about HTTPS, which mainly introduces how the browser verifies the digital certificate of HTTPS. , as well as an introduction to the concepts of HTTP protocol and related certificates. Let’s take a look at them together. I hope it will be helpful to everyone.

The problems solved in this article are as follows:
Free certificate application website:https://freessl.cn
Domain name application , and resolve to the server
The certificate is bound to the domain name
Download the certificate deployment script on the server and deploy
From the HTTP protocol stack level, we can insert a security layer between TCP and HTTP, and all data passing through the security layer will be encrypted or decrypted,
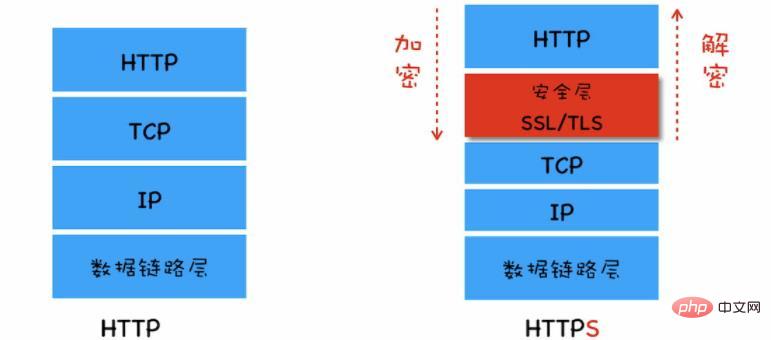
So HTTPS becomes HTTP and the security layer communicates first, and the security layer communicates with TCP. Complete the data encryption and decryption process at the security layer.
Based on the above characteristics, the data transmission process uses symmetric encryption to ensure data transmission efficiency , using asymmetric encryption to solve the problem of easy exposure of keys.
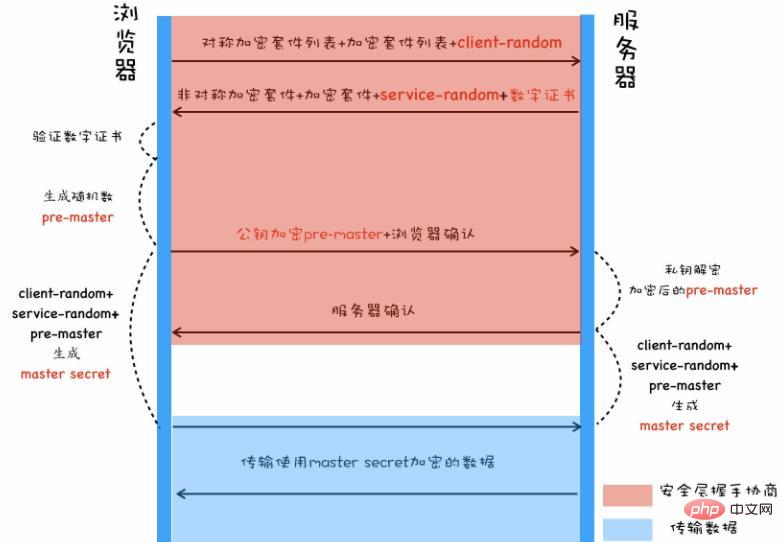
When the browser initiates an https handshake link, it informs the server of the "symmetric cipher suite list" and "asymmetric cipher suite list" it supports and a Self-generated "random number client-random".
After the server receives the request, it selects the encryption method it supports and informs the browser, and returns a "data number service-random" and "server's digital certificate" and the number issued to the server. The certificate is the "digital certificate of the CA organization itself".
The browser verifies the validity of the "server digital certificate" and "CA organization digital certificate". After successful verification, it generates a random number "pre-master" and uses the "server digital certificate" The "public key" carried in the "digital certificate" encrypts the random number "pre-master" and sends it to the service for confirmation.
The server uses the "private key" of the "server digital certificate" to decrypt, obtains the random number "pre-master", and responds that the browser has received it.
The browser combines the random numbers "client-random" and "pre-master" it generated before and the "service-random" returned by the server to generate a new key. "master secret", and then use the new key to encrypt data between the server and the server.
Where does the certificate on the server come from?
When the digital certificate applied to the CA organization is deployed on the server, generally in addition to the digital certificate issued by the CA organization to the service (commonly known as the gateway certificate), there is also the "CA organization's own digital certificate".
What is included in the digital certificate issued by the CA to the server?
At least include the "organization/personal information" when applying for a certificate from the CA organization, "certificate validity period", "certificate's public key", "digital signature of the certificate given by the CA organization", "CA organization information", etc.
Only the server's own certificate is deployed on the server, but there is no digital certificate from the CA organization. What should I do?
When the digital certificate of the CA organization is not available on the server, the browser can automatically download it from the Internet, but this may prolong the time for the first interface/page access, and may also fail.
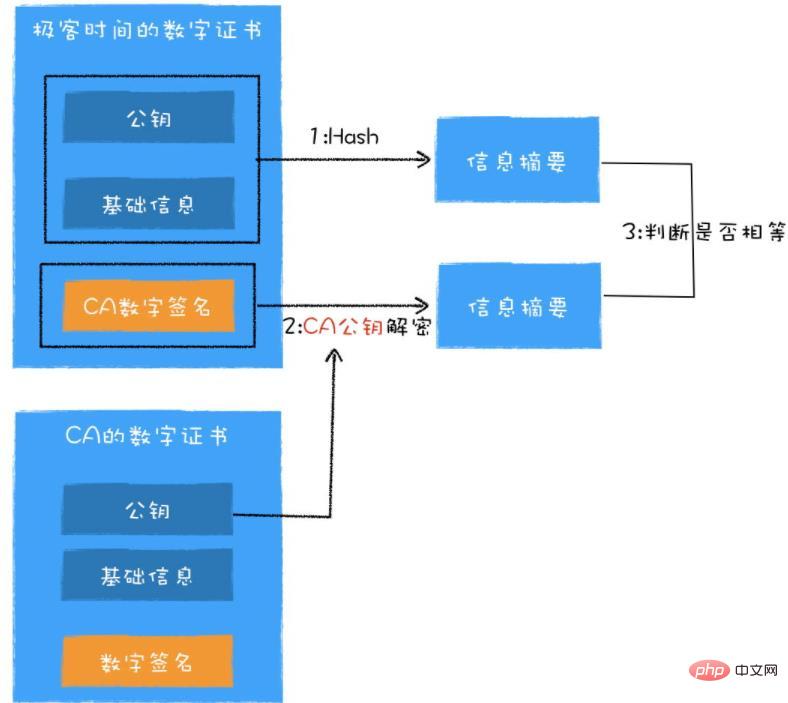
First, the browser uses the hash algorithm specified in the certificate to calculate the information digest of the "plain text information of the organization"
Then , using the public key of the CA certificate to decrypt the "digital signature" in the digital certificate, and the decrypted data is also an information digest.
Finally, just determine whether the two summary information are equal.
The simple and crude solution is: the operating system has built-in certificates of all CA organizations, and it is assumed that the operating system has not been maliciously invaded.
The compromise is to divide the CA organization into two categories, the root CA and the intermediate CA. We usually apply for certificates from the intermediate CA, and the root CA is mainly used for certification by the intermediate CA. The intermediate CA can certify other intermediate CAs, forming a tree structure, with level-by-level certification until the root certificate is found.
There is a certificate chain on the certificate. You can find out what the upper-level organization is. Use the same algorithm as the previous step to let the upper-level organization confirm the authenticity of the current certificate until it is traced back to the root certificate. , and the root certificate only needs to be found in the operating system for the task to be correct, because the root certificate is a specification for browser and operating system manufacturers in the industry.
The root certificate is built-in when installing the operating system. The built-in root certificate is an authoritative certificate certified by WebTrust international security audit.
How to verify whether the root certificate is legal? The browser checks whether the root certificate exists in the operating system. If not, it is illegal, and vice versa.
WebTrust is a security audit standard jointly developed by two well-known CPA associations, AICPA (American Institute of Certified Public Accountants) and CICA (Canadian Institute of Certified Public Accountants). It mainly reviews the systems and business operations of Internet service providers. A total of seven items including logical security and confidentiality were subjected to nearly rigorous review and authentication. Only through WebTrust international security audit certification can the root certificate be pre-installed on mainstream operating systems and become a trusted certification authority.
The self-signed CA certificate requires the user to build the certificate into the user's computer file in advance, or place it on the server.
The root certificate is a special self-signed certificate.
##Recommended study: "HTTP Video Tutorial"
The above is the detailed content of Teach you step by step how to verify HTTPS digital certificate in the browser. For more information, please follow other related articles on the PHP Chinese website!
 The computer has Internet access but the browser cannot open the web page
The computer has Internet access but the browser cannot open the web page What does browser mean
What does browser mean Browser compatibility
Browser compatibility How to solve the problem of garbled characters when opening a web page
How to solve the problem of garbled characters when opening a web page How to open csv format file
How to open csv format file Detailed explanation of sprintf function usage
Detailed explanation of sprintf function usage Three major characteristics of java
Three major characteristics of java How to use the axis function in Matlab
How to use the axis function in Matlab



