According to how the firewall processes data, firewalls can be divided into
According to the firewall's method of processing data, firewalls can be divided into packet filtering firewalls and proxy firewalls; packet filtering products are the primary products of firewalls, and their technical basis is packet transmission technology in the network; proxy firewalls A firewall can also be called a proxy server. Its security is higher than that of packet filtering products, and it has begun to develop towards the application layer.

The operating environment of this article: Windows 7 system, DELL G3 computer
--According to the firewall's method of processing data, what can firewalls be divided into?
Although the development of firewalls has gone through several generations, according to the way firewalls process internal and external data, they can be roughly divided into two major systems: packet filtering firewalls and proxy firewalls (application layer gateway firewalls).
Packet filtering products are the primary products of firewalls, and their technical basis is packet transmission technology in the network. Data on the network is transmitted in units of "packets". The data is divided into packets of a certain size. Each packet will contain some specific information, such as the source address, destination address, and TCP/UDP source of the data. port and destination port, etc. The firewall reads the address information in the data packets to determine whether these "packets" come from a trustworthy and safe site. Once a data packet from a dangerous site is found, the firewall will reject the data. System administrators can also flexibly formulate judgment rules based on actual conditions.
The advantages of packet filtering technology are that it is simple and practical, with low implementation cost. When the application environment is relatively simple, it can ensure system security to a certain extent at a relatively low cost.
But the flaws of packet filtering technology are also obvious. Packet filtering technology is a security technology based entirely on the network layer. It can only be judged based on network information such as the source, destination, and port of the data packet. It cannot identify malicious intrusions based on the application layer, such as malicious Java applets and emails. Comes with viruses. Experienced hackers can easily forge IP addresses and deceive packet filtering firewalls.A proxy firewall can also be called a proxy server. Its security is higher than that of packet filtering products, and it has begun to develop towards the application layer. The proxy server is located between the client and the server, completely blocking data exchange between the two. From the client's point of view, the proxy server is equivalent to a real server; and from the server's point of view, the proxy server is a real client. When a client needs to use data on the server, it first sends a data request to the proxy server. The proxy server then requests data from the server based on this request, and then the proxy server transmits the data to the client. Since there is no direct data channel between the external system and the internal server, it is difficult for external malicious intrusions to harm the enterprise's internal network system.
The advantage of the proxy firewall is that it has high security, can detect and scan the application layer, and is very effective in dealing with intrusions and viruses based on the application layer. Its disadvantage is that it has a great impact on the overall performance of the system, and the proxy server must be set up one by one for all application types that may be generated by the client, which greatly increases the complexity of system management.
The former is represented by Israel's Checkpoint firewall and Cisco's PIX firewall, and the latter is represented by the American NAI Company's Auntlet firewall.
--According to the location of the firewall, the firewall can be divided into external firewall and internal firewall.
The former establishes a protective layer between the internal network and the external network to prevent the invasion of "hackers" by monitoring and restricting all incoming and outgoing communications, blocking external illegal information and controlling the leakage of sensitive information; The latter separates the internal network into multiple LANs, thereby limiting the damage caused by external attacks.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of According to how the firewall processes data, firewalls can be divided into. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
OneDrive is a popular cloud storage application provided by Microsoft. Most of us use OneDrive to store our files, folders, documents, etc. But some users complained that when they try to access shared files on OneDrive, it gives an error stating “Error: 0x80070185, Cloud operation was unsuccessful”. Therefore, they cannot perform any operations on OneDrive such as copying files, pasting, downloading shared files, etc. Nowadays, it is necessary to use these operations in our daily work. This error can be easily solved and for this we have some methods that we can apply and try to solve the problem. let's start! Method 1 – Sign out and sign back in to OneDrive app steps
 How to solve if Edge browser is blocked by firewall?
Mar 13, 2024 pm 07:10 PM
How to solve if Edge browser is blocked by firewall?
Mar 13, 2024 pm 07:10 PM
How to solve the problem that the Edge browser is blocked by the firewall? Edge browser is Microsoft's own browser. Some users found that this browser was blocked by the firewall during use. So what's going on? Let this site give users a detailed introduction on how to recover the Edge browser if it is blocked by the firewall. How to restore the Edge browser if it is blocked by the firewall? 1. Check the firewall settings: - Click the "Start" button on the Windows taskbar, and then open "Settings". -In the Settings window, select Update & Security. -exist
 Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
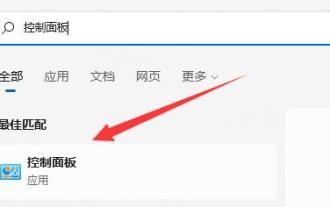
When setting up the firewall, many friends found that their win11 firewall advanced settings were grayed out and unable to be clicked. This may be caused by not adding a control unit, or by not opening the advanced settings in the correct way. Let’s take a look at how to solve it. Win11 firewall advanced settings gray method one: 1. First, click the start menu below, search and open "Control Panel" at the top 2. Then open "Windows Defender Firewall" 3. After entering, you can open "Advanced Settings" in the left column . Method 2: 1. If the above method cannot be opened, you can right-click "Start Menu" and open "Run" 2. Then enter "mmc" and press Enter to confirm opening. 3. After opening, click on the upper left
 8 Big Fixes if Grammarly Not Working on Windows 10 Browser
May 05, 2023 pm 02:16 PM
8 Big Fixes if Grammarly Not Working on Windows 10 Browser
May 05, 2023 pm 02:16 PM
If you have syntax issues on your Windows 10 or 11 PC, this article will help you solve the problem. Grammarly is one of the most popular typing assistants for fixing grammar, spelling, clarity, and more. It has become an essential part of writing professionals. However, if it doesn't work properly, it can be a very frustrating experience. Many Windows users have reported that this tool does not work well on their computers. We did an in-depth analysis and found the cause and solution of this problem. Why doesn't Grammarly work on my PC? Grammarly on PC may not work properly due to several common reasons. It includes the following
 Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
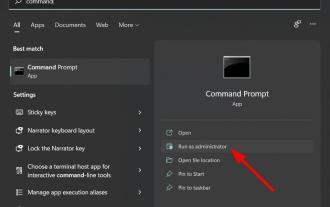
After installing the latest operating system on your PC, activating your copy of Windows 11 is the main job. Not only does it unlock the true potential of the Windows 11 operating system, but it also gets rid of the annoying "Activate your Windows 11" message. However, for some users, Windows 11 activation error 0xc004f074 hinders the smooth progress of activation. This bug apparently prevents users from activating Windows 11 and forces them to use an operating system with limited functionality. Windows 11 activation error code 0xc004f074 is related to the Key Management Service. You will encounter this problem when KMS is unavailable. Okay, that's it for this tutorial
 How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
On AlpineLinux, you can use the iptables tool to configure and manage firewall rules. Here are the basic steps to enable or disable the firewall on AlpineLinux: Check the firewall status: sudoiptables -L If the output shows rules (for example, there are some INPUT, OUTPUT, or FORWARD rules), the firewall is enabled. If the output is empty, the firewall is currently disabled. Enable firewall: sudoiptables-PINPUTACCEPTsudoiptables-POUTPUTACCEPTsudoiptables-PFORWARDAC
 How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
How to remove the firewall logo on the Win10 desktop icon?
Jan 01, 2024 pm 12:21 PM
Many friends who use win10 system find that there is a firewall logo on the icon on the computer desktop. What is going on? This makes many friends with obsessive-compulsive disorder particularly uncomfortable. In fact, we only need to open the control panel and click " It can be solved by changing "Change User Account Control Settings". Let's take a look at the specific tutorial. How to cancel the firewall logo on the desktop icon in Windows 10 1. First, right-click the Start menu button next to the computer startup screen, and then select the Control Panel function from the pop-up menu. 2. Then select the "User Account" option and select the "Change User Account Control Settings" item from the new interface that appears. 3. After adjusting the slider in the window to the bottom, click Confirm to exit.
 How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
How to fix UFW status showing as inactive in Linux
Mar 20, 2024 pm 01:50 PM
UFW, also known as Uncomplex Firewall, is adopted by many Linux distributions as their firewall system. UFW is designed to make it easy for novice users to manage firewall settings through both the command line interface and the graphical user interface. A UFW firewall is a system that monitors network traffic according to set rules to protect the network from network sniffing and other attacks. If you have UFW installed on your Linux system but its status shows as inactive, there could be several reasons. In this guide, I will share how to resolve the UFW firewall inactive issue on Linux systems. Why UFW Shows Inactive Status on Linux Why UFW Is Inactive by Default on Linux How to Inactive on Linux






