
The followingphpmyadmin tutorialcolumn will introduce you tophpmyadminpenetration tips. I hope it will be helpful to friends in need!

##Just record it for yourself, if you all Don’t dislike it when you see itSome website building software or fool-like building software phpmyadmin often uses ports 888 and 999
nikto -host http://Test domain name address: 999/
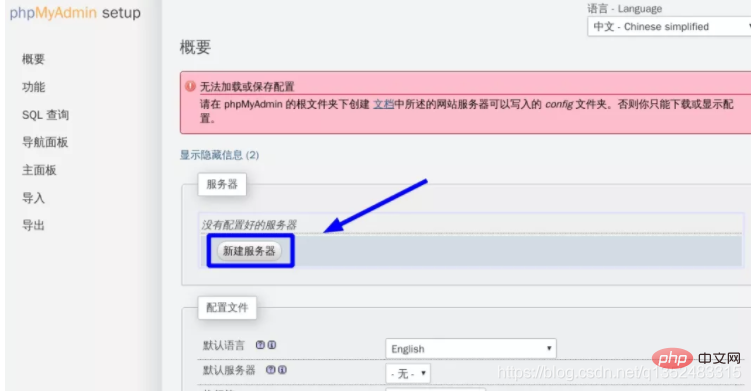

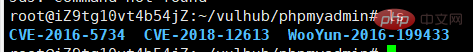
show variables like "%dir%";
The above is the detailed content of Record phpmyadmin penetration tips. For more information, please follow other related articles on the PHP Chinese website!
 Commonly used mysql management tools
Commonly used mysql management tools What to do if phpmyadmin fails to import sql file
What to do if phpmyadmin fails to import sql file How to change phpmyadmin to Chinese
How to change phpmyadmin to Chinese What's going on when phpmyadmin can't access it?
What's going on when phpmyadmin can't access it? Free erp management system software
Free erp management system software what is ed
what is ed The difference between lightweight application servers and cloud servers
The difference between lightweight application servers and cloud servers Apple store cannot connect
Apple store cannot connect