
Add security group rules
You can allow or prohibit security groups by adding security group rules ECS instances within the system access the public network or private network.
Prerequisites
Before adding security group rules, please confirm the following information:
1. You have created a security group. For specific operations, see Creating a Security Group.
2. You already know which public or intranet access to the ECS instance needs to be allowed or prohibited. For more application cases on security group rule settings, see Security Group Application Cases.
Background Information
The security group is responsible for managing whether to allow access requests from the public network or the intranet. For security reasons, most security group inbound directions adopt a deny access policy. If you are using the default security group, or you selected the Web Server Linux template or Web Server Windows template when creating the security group, the system will automatically add security group rules to some communication ports. For more details, see Security Group Overview. The contents of this article apply to the following scenarios:
1. When your application needs to communicate with a network outside the security group where the ECS instance is located, but the request enters a long waiting state after being initiated, you need to set the security group rules first. .
2. When you find that some request sources have malicious attacks during the operation of your application, you can add security group rules that deny access to implement isolation policies.
Before adding security group rules, please understand the following:
1. Security group rules will differ in network card settings.
#Classic network type security group rules distinguish between internal network cards and public network cards.
# Private network VPC type security group rules do not distinguish between intranet network cards and public network cards.
Public network access to private network VPC type ECS instances is forwarded through intranet network card mapping. Therefore, you cannot see the public network card inside the ECS instance, and you can only set intranet security group rules. However, the security group rules take effect on both the intranet and the public network.
2. Before adding any security group rules to the security group you created, all access is allowed in the outbound direction and all access is denied in the inbound direction.
3. Security group rules support IPv4 security group rules and IPv6 security group rules.
4. The total number of inbound and outbound rules for each security group cannot exceed 200.
5. Enterprise security groups do not support setting priorities, authorization to security groups, and setting security group rules that deny access. For more details, see Enterprise Security Groups Overview.
Operation steps
1. Log in to the ECS management console.
2. In the left navigation bar, select Network and Security > Security Group.
3. On the top status bar, select the region.
4. Find the security group for which you want to configure authorization rules. In the operation column, click Configure Rules.
5. On the security group rules page, you can choose any of the following methods to complete the operation.
Method 1:
Quickly create rules, suitable for no need to set ICMP and GRE protocol rules. And the operation scenario can be completed by checking multiple ports. The quick creation rule provides application port settings for SSH 22, telnet 23, HTTP 80, HTTPS 443, MS SQL 1433, Oracle 1521, MySQL 3306, RDP 3389, PostgreSQL 5432 and Redis 6379. You can check one or more ports at the same time, or customize TCP/UDP ports.
Click Quick Create Rule. For detailed guidance on setting parameters such as network card type, rule direction, and port range in the Quick Create Rule dialog box, see Method 2 to add security group rules.
Method 2:
Add security group rules, suitable for scenarios where multiple communication protocols need to be set, such as ICMP and GRE protocols.
a. Click Add Security Group Rule.
b. (Classic network type security group only) Select the network card type.
Intranet: Your ECS instance cannot access the public network/Internet, or does not need to access the public network.
Public network: Your ECS instance can access the public network and provides Internet access to applications.
c. Select the rule direction.
Outbound direction: Refers to the ECS instance accessing other ECS instances in the intranet or resources on the public network.
Inbound direction: refers to other ECS instances in the intranet or resources on the public network accessing the ECS instance.
d. Select the authorization policy.
Allow: Allow access requests corresponding to this port.
Reject: Drop the data packet directly without returning any response information. If the rules of the two security groups are the same except for the authorization policy, the denial of authorization will take effect and the allow policy will not take effect.
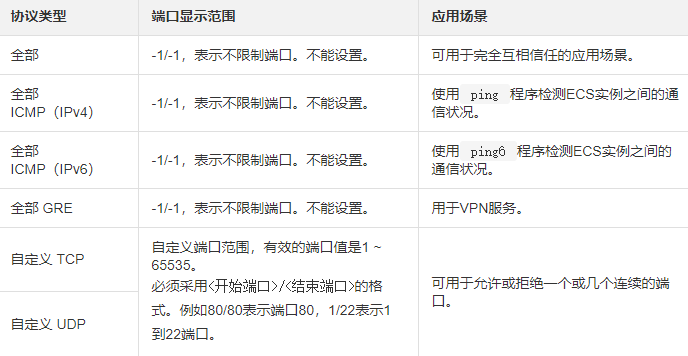
e.Select the protocol type and port range.
The setting of the port range is affected by the protocol type. The following table shows the relationship between the protocol types and port ranges involved in the creation page. For more information about commonly used ports, see Typical Applications of Common Ports.
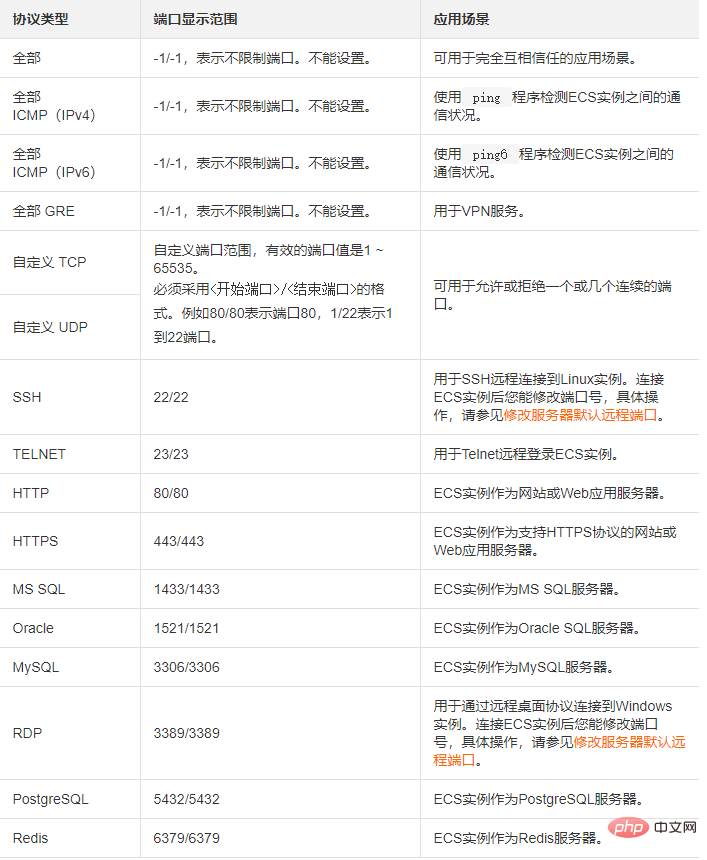
#Note: STMP port 25 in the public network outbound direction is restricted by default and cannot be opened through security group rules. If you need to use STMP port 25, please avoid security risks by yourself, and then apply to unblock port 25. For specific operations, see Applying to Unblock Port 25.
f. Select the authorization type and authorization object.
The setting of the authorization object is affected by the authorization type. The following is the relationship between the two.
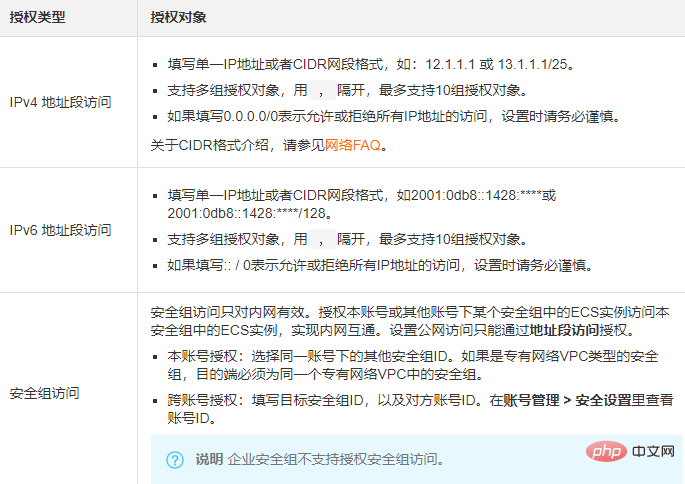
#Note: For security reasons, for the intranet inbound rules of the classic network, security group access is preferred as the authorization type. If you choose address segment access, you can only authorize a single IP address. The format of the authorization object can only be a.b.c.d/32, only IPv4 is supported, and the subnet mask must be /32.
g. Priority: The value range is 1~100.
Note: The smaller the priority value, the higher the priority. Only common security groups can set priorities. Enterprise security groups do not support setting priorities. See Rule Priority for more details.
h. Click OK
Execution Result
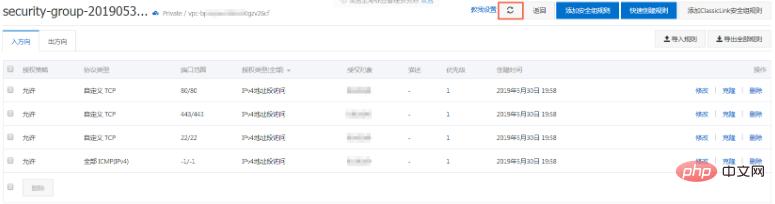
Click the refresh icon to view the added security group rules , confirm that the addition has been completed. Changes to security group rules will be automatically applied to ECS instances in the security group. It is recommended that you test whether they take effect immediately.
##Next Steps
Each ECS instance belongs to at least one security group. You can add ECS instances to one or more security groups based on business needs. For specific operations, see Adding an ECS instance to a security group.
Related Documents
# AuthorizeSecurityGroup
# AuthorizeSecurityGroupEgress
Recommended tutorial:
windows tutorialThe above is the detailed content of Add security group rules to Alibaba Cloud ECS server. For more information, please follow other related articles on the PHP Chinese website!




