
This article mainly introduces the group policy and user settings of the win2008 R2 WEB server Security Settings Guide, friends in need can refer to the following
Set group policies through optimization, and set system defaults Administrators and users can take measures such as renaming and creating trap accounts to improve system security.
Continuing from the previous article, we have changed the remote connection port and can reject some attacks, but these settings are not enough. When doing the following security, you must make sure that your server software has been fully configured and can be used normally. Otherwise, if you install the software after setting the security, the installation may fail or other events may occur. Error, causing environment configuration to fail.
Password Policy
The strength of the system password is directly related to the security of the system. If your password is too simple, if your remote connection port is scanned, It will only take minutes to crack your password. Therefore, our system password must set a password that meets security requirements, such as using uppercase and lowercase English, numbers, special symbols, and a length of not less than 6 characters to enhance password security. In Windows 2008 and above systems, the system provides a "Password Policy" setting. Let's set it. First enter the "Local Security Policy",
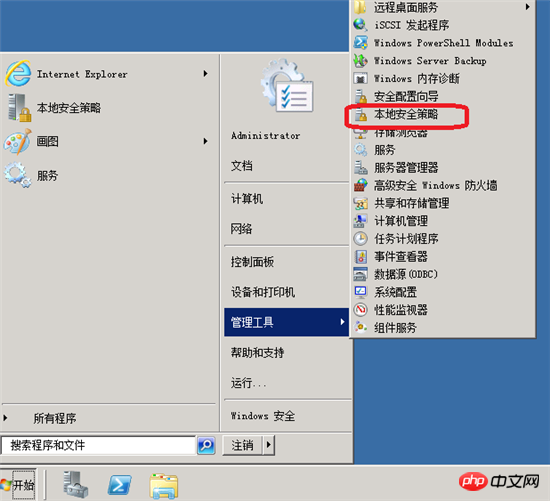
and open "Security" in sequence. Set "-----"Account Policy"-----"Password Policy"-----Password must meet complexity requirements, enable.
AuditStrategy
The role of the audit policy is that in case a malicious user cracks your password, logs into your system, or modifies your system and other events, you can Detect and deal with it early.
The default is no audit, we must modify it, the following is the audit policy I modified,
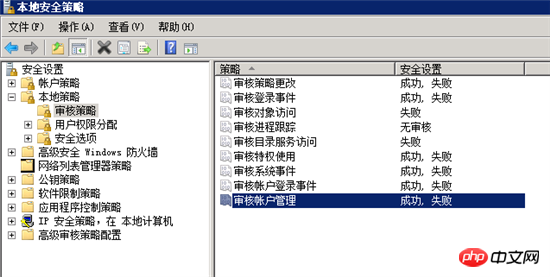
can basically capture the required information, we only need to Analyzing these generated logs can reveal the problem.
User permissions allocation
This is mainly to limit which users can use remote connections to log in to the server. The default is Administrators group and Remote Desktop Users group. These two groups All members can remotely log in to the server. As a WEB server, we generally don’t have too many users. There may be only one administrator, so there is no need to specify a group, just specify the user directly.
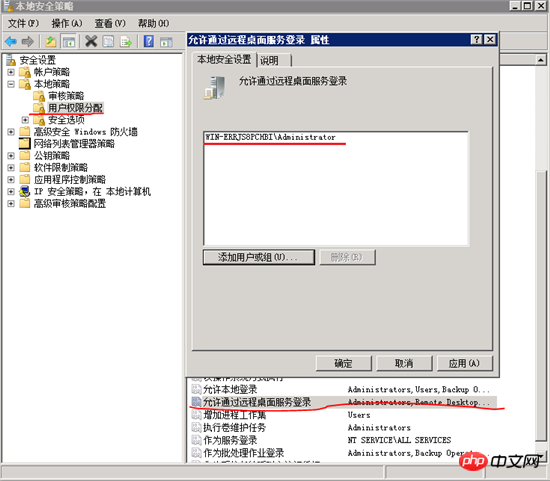
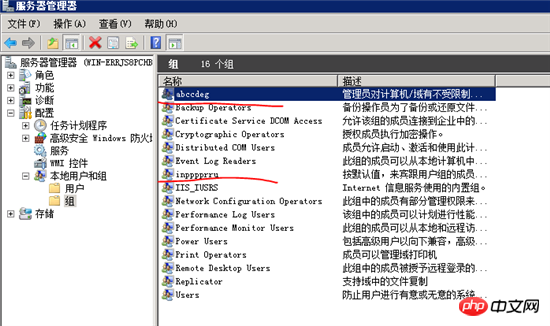
Modify system users and groups
1. Rename the system default user name and user group. This is divided into two steps.
⑴. Rename the default administrator administrator and guest account. For example, I will rename administrator to wobushiad and guest to wobushiguest,
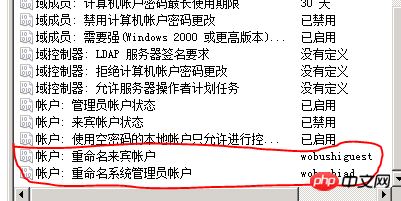
In the future, you will need to use the modified username wobushiad to log in to the server.
⑵. Create a new user named administrator, who belongs to the Guests group, and set a super complex password (type a string of characters in Notepad including uppercase and lowercase letters, numbers, and special symbols and copy them in. You don’t need to Remember this password) and disable the account. This account is a trap account and we do not use this account ourselves.
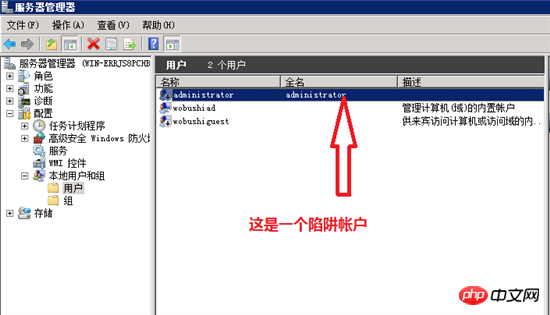
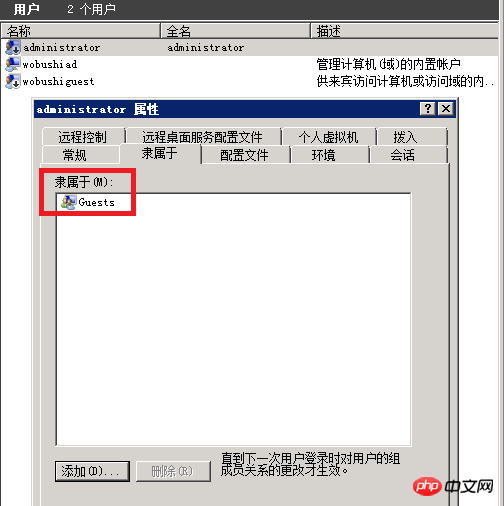
Then modify the default administrator group administrators and Guest group,
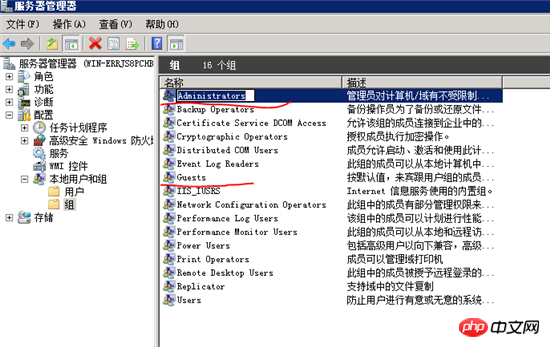
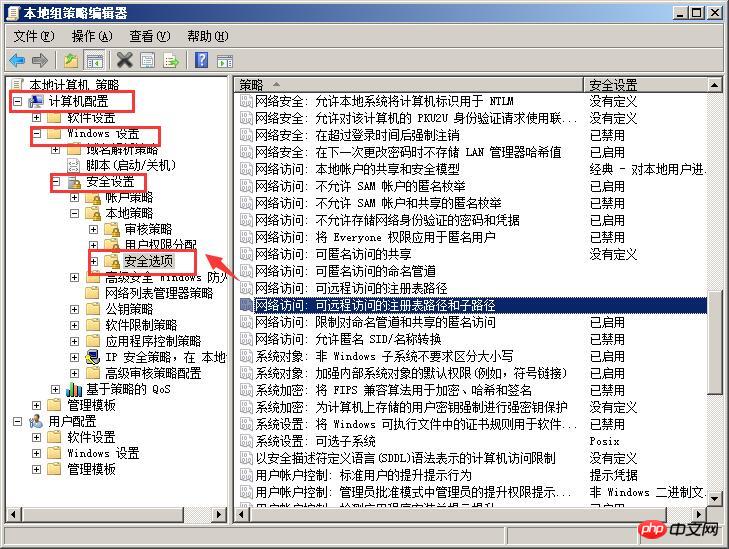
Security Options
Interactive login: Do not display last username, enable
Network access: Do not allow SAM accounts and shares Anonymous enumeration of
Network access enabled: Do not allow storage of passwords and credentials for network authentication, Enable
Network access: Remotely accessible registry path, clear
Network access: Registry paths and subpaths that can be accessed remotely, clear
The above is the detailed content of Detailed explanation of group policy and user settings in win2008 R2 WEB server security settings guide (picture). For more information, please follow other related articles on the PHP Chinese website!




