Found a total of 10000 related content
Do win10 vulnerabilities need to be fixed? Detailed introduction
Article Introduction:After installing the win10 system, everyone's computer will definitely have a lot of vulnerabilities. So do the win10 vulnerabilities need to be repaired? In fact, these vulnerabilities can be repaired, otherwise they will easily lead to virus invasion. Let's take a look at the detailed introduction. Do win10 vulnerabilities need to be fixed? Answer: Win10 vulnerabilities need to be fixed. After the system has been used for a long time, there will definitely be a lot of vulnerabilities, large and small. This is very normal, but repairs are also necessary. If not repaired, there will be many problems, such as blue screen crashes, and the most troublesome thing is that there are Trojans that will use it. Vulnerabilities invade computers. Easy method to fix win10 vulnerabilities: 1. First press the shortcut key "win+i" to open windows settings. 2. Then click "Update and Security" inside.
2023-12-24
comment 0
1250

PHP vulnerability scanning and remediation tips
Article Introduction:PHP vulnerability scanning and remediation includes: scanning for vulnerabilities using tools such as Acunetix, Nessus, and BurpSuite. Fix vulnerabilities, such as updating PHP version, installing patches or modifying code. Use security libraries and frameworks. Rescan periodically to confirm the fixes are effective.
2024-05-02
comment 0
1199

Log4j Vulnerability Repair Tutorial: Best Practices to Effectively Prevent and Repair Log4j Vulnerabilities
Article Introduction:Log4j vulnerability repair tutorial: Best practices to effectively prevent and repair log4j vulnerabilities, specific code examples are required. Recently, a vulnerability in an open source library called "log4j" has attracted widespread attention. The vulnerability, labeled CVE-2021-44228, affects a variety of applications and systems, triggering security alerts around the world. This article will introduce how to effectively prevent and repair log4j vulnerabilities, and provide some specific code examples. Vulnerability Overview log4j is a Java for logging
2024-02-23
comment 0
1099

log4j vulnerability repair tutorial: guide you step by step to repair log4j vulnerabilities
Article Introduction:Log4j Vulnerability Repair Tutorial: Detailed guide to repair log4j vulnerabilities step by step, specific code examples are required Introduction Recently, the "log4j vulnerability" (also known as the CVE-2021-44228 vulnerability) has caused widespread attention and concern around the world. This vulnerability poses a serious security risk to applications that use the ApacheLog4j logging library. An attacker can use this vulnerability to remotely execute malicious code, resulting in complete control of the system. This article will provide you with a detailed log4j vulnerability
2024-02-21
comment 0
665

Log4j vulnerability repair guide: Thoroughly understand and quickly resolve log4j vulnerabilities
Article Introduction:Log4j vulnerability repair tutorial: Comprehensive understanding and rapid resolution of log4j vulnerabilities, specific code examples are required Introduction: Recently, serious vulnerabilities in Apachelog4j have attracted widespread attention and discussion. This vulnerability allows an attacker to remotely execute arbitrary code via a maliciously constructed log4j configuration file, thereby compromising the security of the server. This article will comprehensively introduce the background, causes and repair methods of the log4j vulnerability, and provide specific code examples to help developers fix the vulnerability in a timely manner. 1. Vulnerability background Apa
2024-02-19
comment 0
848

PHP code rewriting technology used to fix vulnerabilities
Article Introduction:PHP code rewriting technology is used to repair vulnerabilities. Vulnerabilities are an inevitable problem in software development, especially in web applications. Security issues may lead to serious consequences such as user information leakage and system crash. In order to protect user privacy and maintain system stability, developers need to fix these vulnerabilities in a timely manner. A common technique for fixing vulnerabilities is PHP code rewriting. PHP code rewriting refers to modifying and optimizing existing PHP code to fix existing vulnerabilities. Below are some common ones
2023-08-08
comment 0
1055
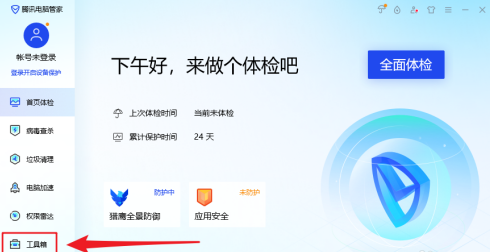
How Tencent Computer Manager fixes system vulnerabilities with one click - Tencent Computer Manager fixes system vulnerabilities with one click
Article Introduction:I believe that the users here like to use Tencent Computer Manager software just like the editor, but do you know how Tencent Computer Manager can fix system vulnerabilities with one click? Next, the editor will bring you Tencent Computer Manager’s one-click method of repairing system vulnerabilities. Method, interested users can take a look below. Open the [Tencent Computer Manager] software and click the [Toolbox] option. In the [Toolbox] interface, click the [Fix Vulnerability] option. On the [Tencent Computer Manager - Vulnerability Repair] interface, click the [One-click Repair] button. After waiting for the prompt [All vulnerabilities have been successfully repaired, the computer is more secure!], click the [Finish] button.
2024-03-04
comment 0
1392
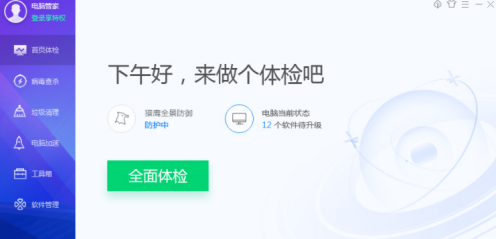
How Tencent Computer Manager fixes system vulnerabilities - Tencent Computer Manager fixes system vulnerabilities
Article Introduction:Presumably many people are using Tencent Computer Manager software on their computers, so do you know how Tencent Computer Manager fixes system vulnerabilities? Next, the editor will bring you Tencent Computer Manager's method of repairing system vulnerabilities. Interested users please hurry up Let’s take a look below. When a computer has a system vulnerability that prevents it from starting or running normally, it is a wise choice to consider using security protection software such as Tencent Computer Manager to repair it. Open Tencent Computer Manager, click "Virus Scan" and "Fix Vulnerabilities" in sequence. At this time, Tencent Computer Manager will start scanning the system for vulnerabilities.
2024-03-04
comment 0
1157

Log4j Vulnerability Remediation Guide: Make sure your system is not vulnerable to log4j vulnerabilities
Article Introduction:Log4j vulnerability repair tutorial: Protect your system from log4j vulnerabilities Summary: This article will introduce the risks and impacts of log4j vulnerabilities, as well as specific steps to repair the vulnerabilities. The article will focus on repair methods for Java backend applications and provide specific code examples. Introduction: Logging is an essential feature in the software development process. Due to its wide application, ApacheLog4j, as one of the most common Java logging frameworks, has become the focus of hacker attacks. Recently, a
2024-02-19
comment 0
1271

Do system vulnerabilities need to be fixed?
Article Introduction:System vulnerabilities must be repaired in a timely manner to protect system security, improve stability, comply with compliance requirements, save costs, and keep software up-to-date. Methods to fix vulnerabilities include: reviewing vendor security bulletins, using security management solutions, disabling unnecessary services, encrypting data, and conducting security audits.
2024-05-07
comment 0
464

How to fix system vulnerabilities in Tencent Computer Manager How to fix system vulnerabilities in Tencent Computer Manager
Article Introduction:Tencent Computer Manager is a software that can protect computers very well. It has very high security and can provide system vulnerability repairs. Some users have this software on their computers, but they don’t know how to fix it if a vulnerability occurs. Next Next, the editor will share the solution with you, hoping to help the majority of users. The operation method is as follows: 1. Double-click to open the software and click the virus scanning option in the left menu bar. 2. Then click Repair Vulnerabilities on the right. 3. Wait for the vulnerability scan to complete. 4. Finally, click the one-click repair button above.
2024-08-30
comment 0
808

Identification and repair of Java framework security vulnerabilities
Article Introduction:Answer: Identify vulnerabilities through code review, security scanning tools and audit logs and fix them in updating patches, validating inputs, refactoring code and security configurations. Identify security vulnerabilities: code review, security scanning tools, audit logs Fix security vulnerabilities: patch updates, input validation, code refactoring, security configuration
2024-06-01
comment 0
1136

Preventing and repairing logic vulnerabilities in PHP websites
Article Introduction:Prevention and Repair of Logic Vulnerabilities in PHP Websites In today's Internet era, website security has become a matter of great concern to both users and website developers. However, while various types of vulnerabilities exist in websites, logic vulnerabilities are often the most overlooked. In this article, we will explore common logic vulnerabilities in PHP websites and provide some methods to prevent and fix them. Logic vulnerabilities refer to security issues caused by incorrect logic or improper design in the program. In PHP websites, common logic vulnerabilities include unauthorized
2023-08-07
comment 0
1153

Fix log4j vulnerabilities in your applications: a step-by-step guide to help you fix them quickly
Article Introduction:Log4j vulnerability repair tutorial: Quickly fix log4j vulnerabilities in your application, specific code examples are required [Introduction] In the field of network security, log4j vulnerabilities are a serious security issue that has attracted much attention recently. This vulnerability affects many Java applications that use the log4j logging library, allowing hackers to execute remote code through maliciously crafted log messages. In order to help developers quickly repair log4j vulnerabilities in their own applications, this article will provide detailed repair steps and specific code examples. [
2024-02-19
comment 0
427

Linux common vulnerability repair tutorials!
Article Introduction:Fixing common vulnerabilities in Linux systems is an important step in ensuring system security. Here is a general tutorial for fixing common vulnerabilities: Update system patches: Keeping your operating system up to date with patches is a critical step in preventing vulnerability exploitation. Use a package manager (such as yum, apt-get) to check for and install available system updates. Install the latest software versions: Update the software installed on your system to the latest versions, as new versions often fix known vulnerabilities. Make sure to install the latest packages using your package manager. Disable unnecessary services and ports: Check the services and open ports running on the system, disable unnecessary services and close unused ports. This reduces the system's exposure to potential attacks. Configure Firewall: Set up and configure a firewall to restrict network traffic and
2024-03-07
comment 0
640

PHP file upload vulnerability and its fixes
Article Introduction:PHP file upload vulnerability and its repair measures With the development of the Internet, the file upload function has become increasingly important in website development. However, the PHP file upload function is also one of the common security holes. Hackers may use this vulnerability to upload malicious files and then attack the website. This article will introduce the principles and attack methods of PHP file upload vulnerabilities, and provide some repair measures. 1. Vulnerability Principle PHP file upload vulnerabilities are usually based on the following two principles: file type verification is incomplete: the $_FILES array in PHP is used
2023-08-07
comment 0
2483

Fixes for PHP remote execution and command injection vulnerabilities
Article Introduction:Title: Fix for PHP Remote Execution and Command Injection Vulnerabilities Introduction: In web development, PHP is a widely used back-end programming language. However, due to the characteristics of PHP and incorrect code writing, it is easy to cause some security vulnerabilities, such as remote execution vulnerabilities and command injection vulnerabilities. This article explains how these two vulnerabilities work and provides code examples to fix them. 1. Principle of Remote Execution Vulnerability Remote execution vulnerability means that the attacker causes the server to perform unexpected operations by sending malicious code. When developers use unsafe functions
2023-08-14
comment 0
1393

What is the log4j vulnerability repair tutorial?
Article Introduction:Steps to repair the log4j vulnerability: 1. Confirm the scope of the vulnerability; 2. Upgrade the Log4j version; 3. Temporarily disable JNDI lookup; 4. Replace the original JndiLookup class with the code; 5. Security data collection and monitoring. Detailed introduction: 1. To confirm the scope of the vulnerability, you first need to determine the scope of the vulnerability. You can determine whether it is affected by the vulnerability by checking the Log4j version used in the application and whether external dependencies are introduced. Common affected versions include Log4j 2.0 to 2.15.0-rc1 and so on.
2024-01-23
comment 0
1214

Discussion on the necessity and details of Win7 system vulnerability repair in 2020
Article Introduction:The win7 system has unfortunately been eliminated in 2020, but many friends are still using the win7 system. So do the loopholes that appear at this time still need to be fixed? The following is a detailed introduction for you to take a look at. Is it necessary to fix the vulnerability in win72020? Answer: It is necessary to fix it. Although Microsoft has stopped updating win7, the loopholes still need to be fixed, and they can be fixed manually. Manual repair method for win7 vulnerabilities: 1. Click on My Computer and select "Control Panel". 2. Then select “windowsupdate”. 3. Select "Detect Updates" and click "OK" to complete the settings.
2024-01-06
comment 0
998

How to scan and repair security vulnerabilities in Java development projects
Article Introduction:How to Scan and Repair Security Vulnerabilities in Java Development Projects With the rapid development of the Internet, Java development has become the first choice for many companies and individuals. And the security issues that come with it are gradually becoming important. The potential risks that security vulnerabilities bring to projects cannot be ignored. Therefore, it is crucial to scan and repair security vulnerabilities in Java development projects. This article will introduce some methods and tools to help developers effectively scan and repair security vulnerabilities. Understand common security vulnerabilities before scanning and remediating security vulnerabilities.
2023-11-03
comment 0
983
















