Found a total of 10000 related content

Research on the psychology of network hacker attacks
Article Introduction:With the rapid development and popularization of information technology, network hacker attacks have become a global problem. Cyber hacker attacks not only bring huge economic losses to businesses and individuals, but also have a huge impact on people's mental health. Therefore, studying the psychology of network hacker attacks will not only help understand the behavioral motivations and psychological states of hackers, but also help people face the problem of network hacker attacks more rationally. First of all, there are two main psychological motivations for hacker attacks: one is the love for technology and the desire to prove it through hacker attacks.
2023-06-11
comment 0
3906
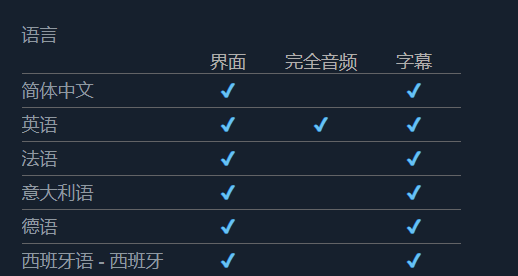
Anonymous hacker simulator settings Chinese method
Article Introduction:Regarding the Chinese setting method of the anonymous hacker simulator, the overall process is relatively simple. You can follow the following steps: Before starting to adjust, make a proper backup of game resources. Avoid game anomalies caused by misoperation. How to set up the anonymous hacker simulator in Chinese 1. Make sure that the anonymous hacker simulator has been successfully installed and started. 2. Look for the settings button or menu item on the main interface of the game and click to enter. 3. Find the "Language" option in the settings menu and click to expand the language list. 4. Select "Simplified Chinese" in the language list. After confirmation, you may need to click the OK button to save. At this time, the game interface will be converted to Chinese display. Warm reminder: Since the game settings and interface may change with updates, if the above method fails to successfully set the Chinese language, please check the latest version of the game.
2024-10-07
comment 0
615

How PHP implements network security solutions to prevent hacker attacks
Article Introduction:With the rapid development and popularization of the Internet, network security issues have increasingly become the focus of attention. PHP is a commonly used server-side programming language. How to use PHP to implement network security solutions and prevent hacker attacks has become a problem faced by many developers. This article will introduce PHP methods and solutions to achieve network security. 1. Defense against SQL injection attacks SQL injection attacks are one of the most common ways of hacker attacks. Usually, by entering specific codes in the input box, the system executes dangerous SQL statements, thereby obtaining sensitive data.
2023-06-27
comment 0
2302

What types of hackers are there? (Introduction to 10 types of hackers)
Article Introduction:A hacker is someone who is very interested in the mysterious workings of any computer operating system. Hackers are usually programmers. They gather advanced knowledge of operating systems and programming languages to discover vulnerabilities within systems and their causes. There are generally 10 types of hackers. They are: White hat hackers: White hat hackers refer to identifying network users by conducting penetration tests.
2019-04-20
comment 0
8669

Sony responds to hacker attack: under investigation
Article Introduction:According to CyberSecurityConnect, a hacker group called "Randomed.vc" claimed to have "invaded all of Sony's systems" and will sell off all data this week because "Sony refuses to negotiate" . Now, Sony responded to IGN that they have opened a formal investigation into the matter. "We are currently investigating the matter and have no further comment at this time." As of the time of this publication, Sony's consumer services are still running normally, including PSN and Sony customer service, and there have been no large-scale interruptions recently. CyberSecurityConnect said the new group, which emerged only last month, "has
2024-07-17
comment 0
985

TRM Labs research report: 70% of cryptocurrency theft proceeds come from Russian-speaking hacker groups
Article Introduction:According to new research from TRMLabs, Russia’s involvement in the illegal cryptocurrency business has increased significantly in 2023, reaching unprecedented levels of influence and profitability. Russian Hackers Dominate Cryptocurrency Crime TRMLabs research reveals a stark phenomenon, with nearly 70% of cryptocurrency proceeds from ransomware traceable to Russian-speaking groups of hackers, a proportion that highlights their prominent position in the field of cybercrime. The report further laid bare Russia’s central role in global hacking entities that have illegally stolen up to $500 million in cryptocurrency. Of particular concern are two ransomware operators, ALPHV/BlackCat and Lockbit.
2024-07-28
comment 0
633

'Brother Dao' Wu Hanqing leaves Alibaba to become China's top hacker representative
Article Introduction:According to news on May 25, according to reliable sources, Wu Hanqing, a well-known researcher at Alibaba, has recently left the company. According to DingTalk, his resignation date is May 19. Wu Hanqing holds a researcher position at Alibaba, with a rank of P10. According to people familiar with the matter, Wu Hanqing decided to start a business after leaving Alibaba, chose the field of AI short videos, and has completed a round of financing. Wu Hanqing, known as "Brother Dao" in the industry, is one of China's top young generation hackers and was the chief security scientist of Alibaba Cloud. Public information shows that Wu Hanqing joined Alibaba in 2005 and participated in the construction of application security systems for Alibaba, Taobao, Alipay and Alibaba Cloud. At the age of 23, he became Alibaba’s youngest senior executive
2023-05-25
comment 0
1960
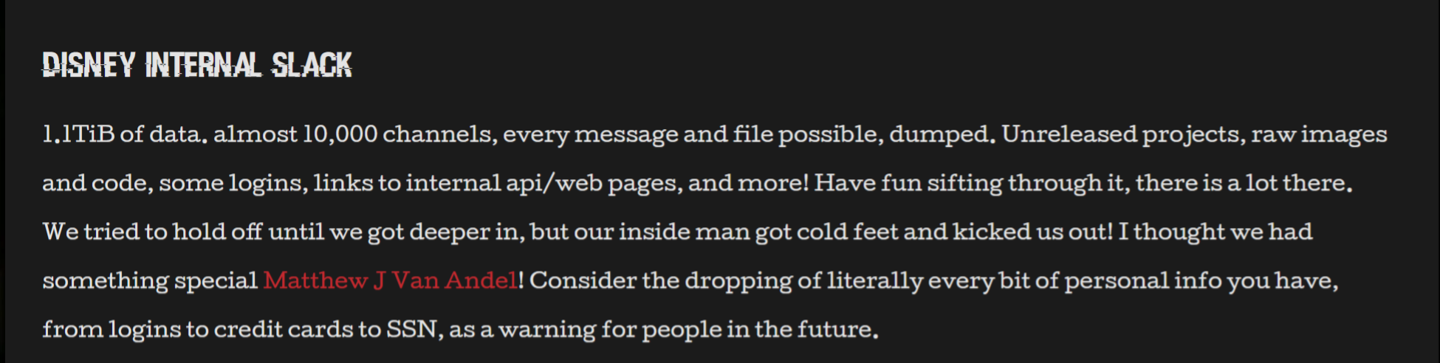
Hacker group NullBulge announces breach of Disney's internal Slack collaboration platform: 1.2TB of messages and documents leaked
Article Introduction:According to news from this site on July 14, the hacker group NullBulge announced that it had invaded Disney's internal Slack infrastructure and leaked 1.2TB (1.1TiB) of sensitive data, including internal messages and document information from nearly 10,000 channels. The hacker group posted on the BreachForums forum on July 12: 1.1TiB of data. Nearly 10,000 channels, all possible information and files were dumped. There are also unreleased projects, original images and code, some login information, internal API/web links, and more! Feel free to sift through it, there's a lot out there. ▲Screenshot of BreachForums forum, source StackDiary, leaked according to foreign media StackDiary citing anonymous sources
2024-07-17
comment 0
792

Hot news: Alibaba Cloud held an AI hacker programming competition; Jimmy Lin became the spokesperson of Xpeng G6...
Article Introduction:Text/Editor of Zinc Finance Editorial Department/Dafeng Alibaba Cloud held a global AI hacker programming competition. On June 5, Alibaba Cloud officially announced that it will hold the first AI hackathon based on Alibaba's largest AI model community "Magic" in China. Challenge. This competition is open to developers from all over the world. The winning team will receive a bonus of up to 30,000 yuan and is expected to share a venture capital fund pool of tens of millions of dollars with other teams. According to the official introduction of Alibaba Cloud, in this competition, the Moda community will provide participating teams with resources for model training inference and demo deployment display. At the same time, developers can directly call more than 30 large models with one billion parameters and more than 10 large models with tens of billions of parameters in the community, as well as corresponding development tools. Baidu launches AI-based large model
2023-06-08
comment 0
688

Who is a cyber hacker?
Article Introduction:Cyber hackers refer to individuals or organizations with advanced computer technology and programming capabilities who invade computer systems, networks or devices through illegal means to gain unauthorized access, steal sensitive information, damage systems or conduct other malicious activities. Cyber hackers are divided into different types including ethical hackers, black hat hackers, gray hat hackers, state-level hackers and non-state hackers. Detailed introduction: 1. Ethical hackers, also known as white hat hackers or security consultants, are a type of legal hackers employed by organizations to test and evaluate computer systems and networks in an authorized manner.
2023-09-07
comment 0
2542

Phishing: Hackers Getting Smarter
Article Introduction:A whopping $41 million has been lost in October so far due to the increasing influx of phishing attacks. Most of the phishing operations within the crypto space usually involve engaging users in signing actions through their crypto wallets, to approv
2024-10-17
comment 0
371

How to hack javascript
Article Introduction:In the Internet age, Javascript can be said to be a ubiquitous programming language. Whether it is web development, mobile applications, games, etc., Javascript is used. Due to its widespread use, Javascript has also become a key target for hacker attacks. Therefore, this article will introduce how to hack Javascript to help readers better understand hacker attack techniques and preventive measures. 1. Common vulnerabilities in Javascript During the development process of Javascript, there are often many vulnerabilities. learn
2023-05-09
comment 0
670
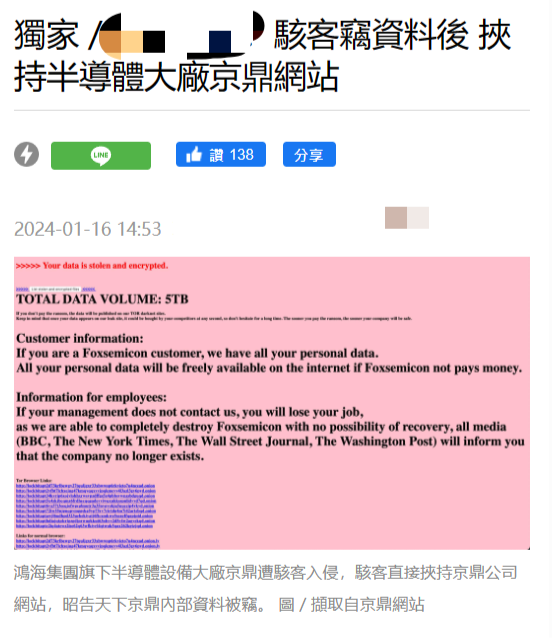
Hackers invaded Jingding, a major semiconductor equipment manufacturer owned by Hon Hai, and directly threatened to disclose data on the official website
Article Introduction:According to the news on this website on January 16, according to the Taiwanese media "Economic Daily", Jingding, a major semiconductor equipment manufacturer under the Hon Hai Group, was hacked by hackers. The hacker group even directly threatened Jingding's customers and employees on the website. If Jingding ignores it, customers will be threatened. Information will be made public and employees will lose their jobs. Incidents of hacker groups hacking into listed companies to steal information happen from time to time, but this is the first time in Taiwan that a hacker group has stolen information and directly hijacked the company's website, revealing that the company's internal information has been stolen and threatened. Jingding is a subsidiary of Hon Hai Group. It mainly engages in the research and development of key modules of semiconductor front-end process equipment and semiconductor automation equipment. According to reports, there was a lot of discussion among companies in Zhuke Park today because when they entered the website of Jingding Company, they were shocked to find that the website had been hacked by a hacker group.
2024-07-18
comment 0
368

Example analysis of MSSQL backdoor from Winnti hacker group
Article Introduction:For some time, ESET researchers have been tracking the activities of Winnti, a group that has been active since 2012 and has targeted the video game and software industry supply chains. Recently, a previously undocumented backdoor was discovered that targets Microsoft SQL (MSSQL). This backdoor bears many similarities to the PortReuse backdoor, another tool used by WinntiGroup and first documented in October 2019. This year, a new backdoor sample, skip-2.0, was detected. The author is a member of the winnti organization. This backdoor targets MSSQL Server 11 and 12 and allows attackers to use magi
2023-05-27
comment 0
1467

Linux server security tips
Article Introduction:Preventing hackers and server security are the main tasks of system management services. Here are some basic security tips for Linux servers.
2019-03-18
comment 0
3351

PHP implements secure programming: practical attack and defense against hackers
Article Introduction:With the continuous development and deepening of the Internet, various hacker attacks have occurred frequently, posing serious threats to network security. PHP is a commonly used web development language used by many businesses and developers to create websites and applications. Therefore, in PHP programming, how to implement safe programming has become very important. This article will introduce common security vulnerabilities in the PHP language and how to prevent them. At the same time, we will also share some hacker attack cases and corresponding countermeasures. SQL InjectionSQL injection is currently
2023-06-18
comment 0
1572


The latest exchange in Europe and Italy cannot be opened
Article Introduction:Reasons why the European-Italian exchange cannot be opened: server maintenance or upgrade; network problems; outdated browser or application; web firewall or anti-virus software; geographical location restrictions; hacker attack or phishing.
2024-08-05
comment 0
1032















