Found a total of 10000 related content


Internet of Things 'botnet DDos attacks' are growing alarmingly, threatening global telecommunications networks
Article Introduction:Recently, as revealed in Nokia’s 2023 Threat Intelligence Report, a surge in malicious activity was first observed during the Russia-Ukraine conflict and has now spread to various regions around the world. In addition to the increase in botnet-driven DDoS attacks, the threat intelligence report also highlights that the number of Trojans targeting personal banking information on mobile devices has doubled and now accounts for 9% of all infections. A recent report from the Nokia Threat Intelligence Center reveals an alarming rise in IoT botnet DDoS attacks targeting telecommunications networks around the world. The study shows that such attacks have increased fivefold in the past year, with cybercriminals taking advantage of insecure IoT devices and profit-driven hacking collectives. This was first observed during the Russian-Ukrainian conflict
2023-06-14
comment 0
1642

DDoS attacks using IoT bots increase fivefold in one year
Article Introduction:Botnet traffic originating from unsecured IoT devices, which enforce distributed denial of service (DDoS) on IoT networks, has increased fivefold in the past year. According to the report, this increase stems from more profit-oriented hacking groups and more consumer IoT devices, and coincides with Russia's war with Ukraine last February. The number of infected IoT devices involved in botnet-driven DDoS attacks has increased from approximately 200,000 a year ago to approximately 1 million. These devices currently generate more than 40% of all DDoS traffic, and the most common malware found in telecom networks is a type of bot malware that scans for vulnerable devices, a type of malware associated with various IoT botnets. strategy, the report also issued
2023-06-10
comment 0
1069


Protect web interfaces from Botnet attacks using Linux servers.
Article Introduction:Protecting Web Interfaces from Botnet Attacks Using Linux Servers In web development and management, protecting web interfaces from Botnet (botnet) attacks is an important security task. Botnet attacks refer to hackers using a group of infected computers or devices to launch attacks and make large-scale malicious requests to web servers to overwhelm the server's resources and bandwidth, causing a denial of service (DoS) attack or a distributed denial of service (DoS). DDoS) attack. In this article we will introduce some uses
2023-09-08
comment 0
1101

Linux network security common problems and solutions
Article Introduction:Common network security problems encountered in Linux systems and their solutions. With the development and popularization of the Internet, network security issues have become more and more important. For users of Linux operating systems, it is crucial to understand common network security issues and corresponding solutions. This article will introduce several common network security issues in Linux systems and provide some solutions. Botnet Attacks A botnet is a network of large numbers of computers infected with malware that an attacker can use to send
2023-06-29
comment 0
1187

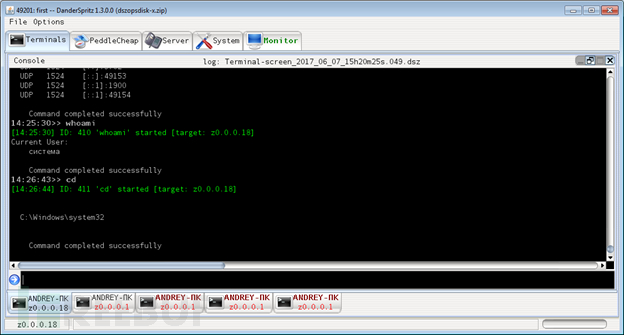
How to use NSA's new APT framework DarkPulsar
Article Introduction:Preface In March 2017, ShadowBrokers released a confidential document that shocked the world, including two frameworks: DanderSpritz and FuzzBunch. DanderSpritz is composed entirely of plugins and is used to gather intelligence, exploit vulnerabilities and manipulate taken over devices. It is written in Java and provides a graphical interface similar to the botnet management panel and a control panel similar to the Metasploit tool. It also incorporates backdoors and plugins for non-FuzzBunch controlled devices. DanderSprit Interface Overview Fuzzbunch provides a framework for different utilities to interact and work together, including various types of plug-ins.
2023-05-18
comment 0
1338
Why is artificial intelligence key to cybersecurity?
Article Introduction:To understand why artificial intelligence (AI) is an important tool in the cybersecurity toolbox today and into the future, it is important to understand how the threat landscape is evolving and what threats Internet users face every day. Evolving Threat Landscape The global threat landscape is changing. Internet consumers now face a very different threat. On the one hand, there are massive, highly automated botnets infecting consumer devices. Social engineering (or phishing) attacks, on the other hand, attempt to defraud users of their money and data. According to researchers, the scale of the botnet threat is growing: Device adoption data from some 1.7 billion connected devices in North America shows that many Internet of Things (IoT) devices are becoming increasingly popular. Among these devices, IP cameras and network attached storage (N
2023-04-08
comment 0
1080
How to install win7 operating system on computer
Article Introduction:Among computer operating systems, WIN7 system is a very classic computer operating system, so how to install win7 system? The editor below will introduce in detail how to install the win7 system on your computer. 1. First download the Xiaoyu system and reinstall the system software on your desktop computer. 2. Select the win7 system and click "Install this system". 3. Then start downloading the image of the win7 system. 4. After downloading, deploy the environment, and then click Restart Now after completion. 5. After restarting the computer, the Windows Manager page will appear. We choose the second one. 6. Return to the computer pe interface to continue the installation. 7. After completion, restart the computer. 8. Finally come to the desktop and the system installation is completed. One-click installation of win7 system
2023-07-16
comment 0
1271
php-insertion sort
Article Introduction::This article mainly introduces php-insertion sort. Students who are interested in PHP tutorials can refer to it.
2016-08-08
comment 0
1130
Graphical method to find the path of the PHP configuration file php.ini, _PHP tutorial
Article Introduction:Illustrated method to find the path of the PHP configuration file php.ini. Graphical method to find the path of the PHP configuration file php.ini. Recently, some bloggers asked in which directory php.ini exists? Or why does it not take effect after modifying php.ini? Based on the above two questions,
2016-07-13
comment 0
871

Huawei launches two new commercial AI large model storage products, supporting 12 million IOPS performance
Article Introduction:IT House reported on July 14 that Huawei recently released new commercial AI storage products "OceanStorA310 deep learning data lake storage" and "FusionCubeA3000 training/pushing hyper-converged all-in-one machine". Officials said that "these two products can train basic AI models." , industry model training, and segmented scenario model training and inference provide new momentum." ▲ Picture source Huawei IT Home compiled and summarized: OceanStorA310 deep learning data lake storage is mainly oriented to basic/industry large model data lake scenarios to achieve data regression from Massive data management in the entire AI process from collection and preprocessing to model training and inference application. Officially stated that OceanStorA310 single frame 5U supports the industry’s highest 400GB/s
2023-07-16
comment 0
1626
PHP function container ing...
Article Introduction::This article mainly introduces the PHP function container ing..., students who are interested in PHP tutorials can refer to it.
2016-08-08
comment 0
1165













