
The first Asia-Pacific Conference on Cyber Law Practice and the Fifth Cyber Law Practice Conference, as well as the Forum on Compliance Development of Artificial Intelligence and Metaverse, were held in Hangzhou on June 10th.. The focus of the meeting was to discuss the Metaverse and artificial intelligence, especially the application scenarios, compliance development, and content risks of the Metaverse.
According to the Law and Consumer Protection Desk of the Network Economic Society (LAW.100EC.CN), the guiding units for this conference include the United Front Work Department of the Xihu District Committee, the Internet Information Office of the Xihu District Committee, the Internet Federation of Xihu District, and the Market Supervision and Management of Xihu District Under the guidance of the Bureau, the organizers are Kenting Law Firm, Micro-Chain, and the Future Unicorn Project, with Zhejiang Blockchain Technology Application Association, Internet Economic Society, etc. as supporting units.

At the beginning of the conference, Ouyang Kunpo, co-founder of Kenting Law Firm and practical instructor of Zhejiang University, delivered a speech, introducing the background, main content and speakers of the conference. Ouyang Kunpo said that the Metaverse is currently used in many scenarios. This conference will not only discuss the compliance development of the Metaverse, but also involve discussions on investment, security and other contents.
The following are the key points of the conference speech brought to you by the Internet Economic Society (WWW.100EC.CN):
1. Zhu Jiwei, Executive Vice President of Zhejiang Blockchain Technology Application Association: Yuan Universe - Helping the upgrading of the physical industry

1. Artificial intelligence liberates productivity, and blockchain solves production relations. The future trend of the Metaverse is artificial intelligence and blockchain.
2. At present, the blockchain has reached a sufficient level, but the technology sector is not yet mature, and the trust relationship of the Internet needs to be solved.
3. The six major scenarios where artificial intelligence helps the real economy are medical care, automobiles, education, manufacturing, transportation, and e-commerce. These are currently the hottest industries for AI applications.
2. Ni Zhili, CEO of Hangzhou Virtual Human Technology Co., Ltd.: An operational attempt to generate NFT by combining Metaverse space with AIGC

1. The Metaverse is the third migration of the Internet. It represents the migration of the Internet from mobile Internet to space interconnection. It includes a large number of new technologies such as VR/AR, AI, cloud, blockchain, etc. The current new technologies have Gradually improving, there is an urgent need for the emergence of new integrated products.
2. The application scenarios of AI virtual humans mainly include: the integration of trendy IP and AIGC, such as product design, scene design, sales space, etc. Existing cases include the Aimu Brand Yuanverse Mini Program Mall, Pepsi Yuanverse Space , KPMG Metaverse Digital Exhibition, etc.
3. Lu Hongkang, Vice President of Hangzhou Youlian Times Technology Co., Ltd.: In the era of the metaverse, 3D digital clones of people and everything

1. The foundation of the metaverse is the 3D digital clone of people and everything.
2. The application scenarios of digital clones mainly include offline experience halls, exhibition halls, university teaching (teaching and research), cultural tourism (digital clones implanted in scenic spots), metaverse space, brand promotion, business districts, games, conferences, virtual Fittings, Metaverse movies, etc.
4. Kang Kang, co-founder of Art Meta Yuan Yishu Digital Collection Circulation Service Platform: a piece of the puzzle in the development of Yuan Universe - the circulation and application of digital collections

1. Yuanyisu starts from NTF digital copyright transactions, connects with the physical supply chain system, customizes private domain traffic, and sells it through e-commerce platforms such as Douyin and Tmall.
2. The rights of digital copyright works include reproduction rights, distribution rights, rental rights, exhibition rights, performance rights, screening rights, broadcast rights, etc.
5. Luo Dan, head of the Yuanverse Industrial Innovation Center of Wensan Digital Life Street in Hangzhou: A preliminary study on the current status of AIGC supervision and compliance risks

1. The underlying logic of GhatGPT is the integration of natural language processing technologies such as GhatGPTr and GPT. It is essentially a language model based on neural networks.
2. Data compliance risk refers to the supervision at the data level, which mainly includes the "Personal Information Protection Law", "Data Security Law", "Civil Code", "Anti-Unfair Competition Law", etc., based on different behaviors carried out on data and clarify different compliance obligations and related risks.
3. Pay attention to the network content generated by AI, which needs to comply with the "Network Information Content Ecological Governance Regulations", "Network Audio and Video Information Service Management Regulations" and other entities stipulated for network information content producers and network information content service platforms. Responsibilities for online content management.
6. Xu Junjun, Vice President of Shanghai Yitu Network Technology Co., Ltd.: AIGC’s content risks and solutions
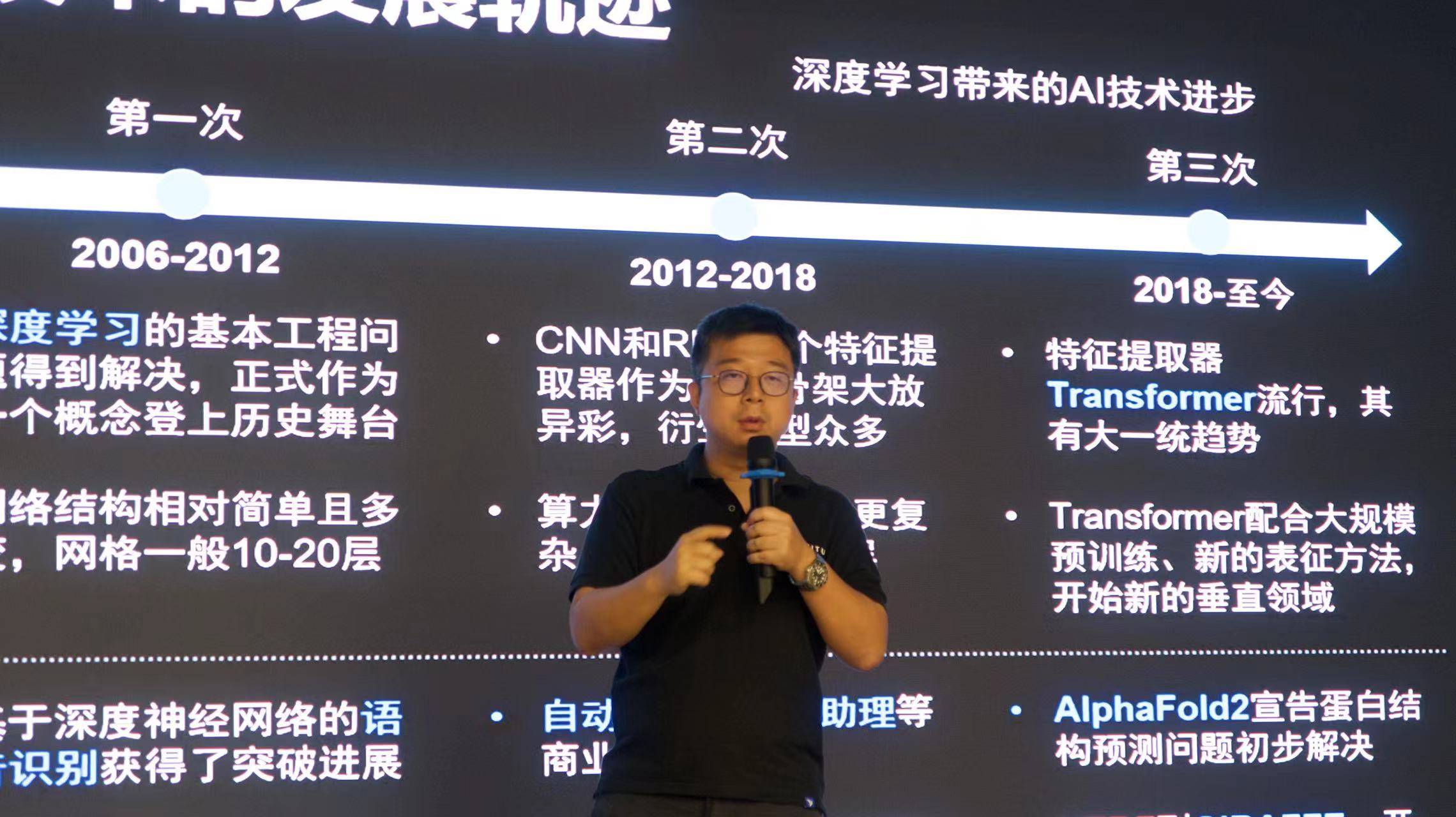
1. The development trajectory of AI technology can be mainly divided into four periods:
During the period from 1995 to 2006, various modes emerged in endlessly, and structured data was the main input mode, which required a lot of manual assistance and limited performance.
Between 2006 and 2012, the basic engineering problems of deep learning were solved, thus officially becoming a concept on the historical stage. The network structure is relatively simple and changeable, and the grid generally has 10-20 layers.
Between 2012 and 2018, two feature extractors, CNN and RNN, played an important role in the network structure and derived many models. With the support of computing power, the network is more complex, reaching 100-200 layers.
Since 2018, Transformer, as a popular feature extractor, is showing a unified trend. With large-scale pre-training and new representation methods, Transformer is entering new vertical fields.
2. The main regulatory agencies for AI include the Cyberspace Administration of China, the State Administration of Radio and Television, the Ministry of Culture and Tourism, the Cyber Security Bureau of the Ministry of Public Security, the Ministry of Industry and Information Technology, the State Administration for Market Regulation, and the Propaganda Department of the CPC Central Committee.
3. Regarding content security review, image review is more difficult. The image review process includes image clustering, face recognition, text recognition, and QR code detection. Due to the low cost of image forwarding and the diverse content scenarios, the review accuracy is not high.
7. An Tongjian, head of Qijian AI Laboratory of Anheng Information Central Research Institute: Thoughts and practice on ChatGPT and AI-driven security technology changes

In the era of the Internet of Everything, we are faced with issues related to Internet security every moment, and many hacking incidents are closely related to daily life. Secondly, network security is also related to enterprises and governments, and can easily cause huge damage to them.
2. The application of AI-driven network security technology is mainly used to improve the defense capabilities of security products, improve the depth of security platform analysis, improve the energy efficiency of security operation services, and improve the internal efficiency of security enterprises.
The emergence of ChatGPT and large-scale models will lead to changes in security technology, while also bringing challenges and business opportunities to the security industry. Among them, AI technology and the strong generation capabilities of large models may be used to generate malware, traffic, and phishing emails and automate attacks. Customers face new security challenges, and security products need to effectively improve their detection and defense capabilities. .
ChatGPT has increased the convenience of cyber crimes, expanded the scale and impact of security incidents, and required corresponding security measures.
8. Wang Xin, Legal Director of Hangzhou Qulian Technology Co., Ltd.: From encryption technology to “anonymization”

1. "Personal Information Protection Law" explains: Anonymization refers to the process in which personal information cannot be identified as a specific natural person and cannot be recovered.
2. There are three test standards for judging "deliberate intruders". One is higher than "ordinary people" and has reasonable abilities and resources; the other is lower than "professionals": hackers and illegally obtained items should not be considered. information, etc.; the third is to take into account the sensitivity of the information and the consequences of leakage; the fourth is to consider the relevant information subjects that have been mastered.
9. Shu Sibin of Kenting Law Firm: Issues related to deepfakes

1. Deep forgery is mainly used in face swapping, attribute editing, facial reshaping, and full synthesis. Because of its autonomy, convenience and authenticity, crime becomes easier, the cost and threshold are lower, and the possibility of success is higher.
2. Deep forgery may affect individual rights and interests, such as insults and slander; social order, such as forged identities and fake news; and even national security, such as political influence and international relations.
Platforms such as Meta and Douyin have formulated countermeasures. At the same time, some counterfeit products can currently be detected manually.
4. In terms of content security, we need to pay attention to the standards of content review, the implementation of content review, pay close attention to political information, news information, and the protection of minors.
The above is the detailed content of The first Asia-Pacific Cyber Law Practice Conference was held. Nine experts discussed the metaverse and the development of artificial intelligence.. For more information, please follow other related articles on the PHP Chinese website!




