
Taking the previous IDAPRO or HOOK, we can get XXTEA decrypting key. For SIGN, we can directly open the original file:
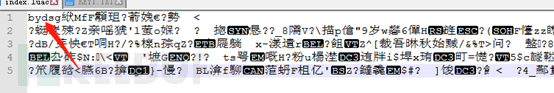
This can see the SIGN value: byds. Therefore, we can try to use the xxtea decryption tool (by getting the source code on GitHub and compiling it) to decrypt
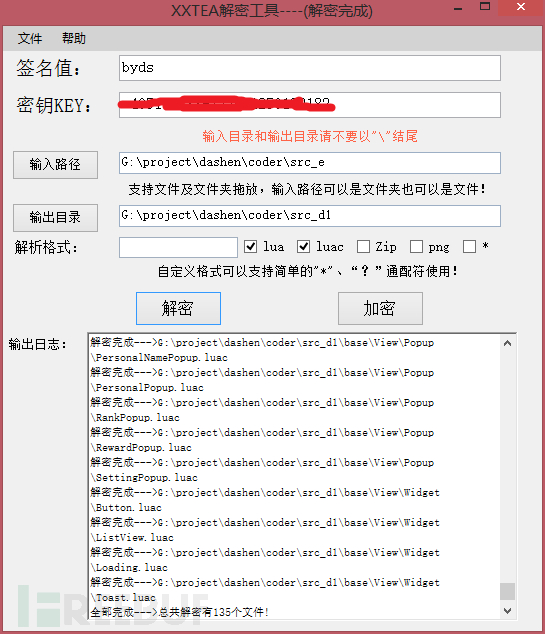
Take index.luac as an example, let’s look at index.luac decryption Changes before and after:
We see that the lua script decrypted by xxtea is still not clear text! We previously determined that the xxtea encryption was used based on the cocos2d framework source code and the master apk decoding result, and the app's Lua script also has a signature value, which also confirms that it is the xxtea encryption method, but the result we decrypted is still not plain text, which shows that we The decryption may not be complete. You have to go back to idapro to find out.
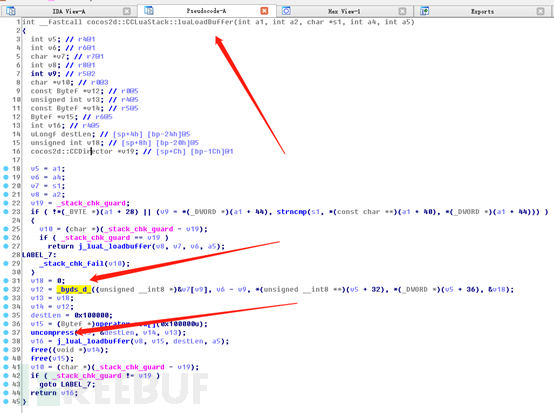
Open libgame.so with IDAPRO, search for Byds in the Export window, find the byds_d function, double -click in:
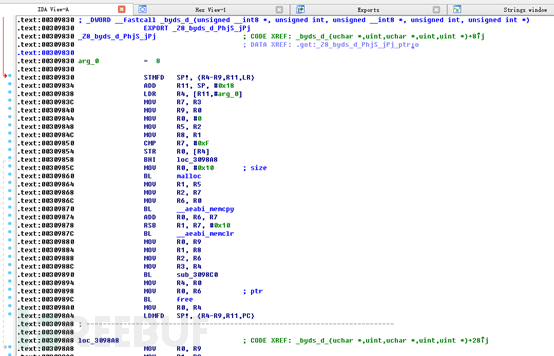
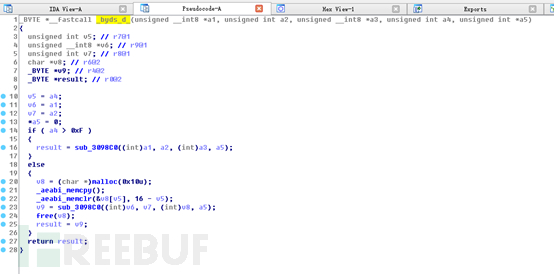
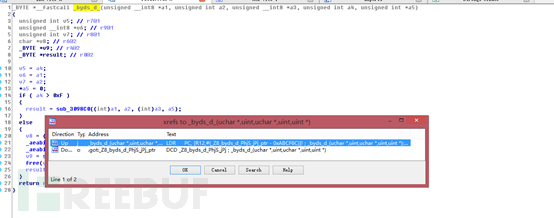
 Double-click to enter:
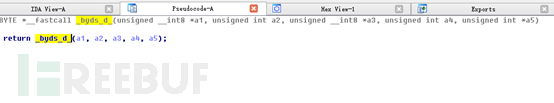
Double-click to enter:
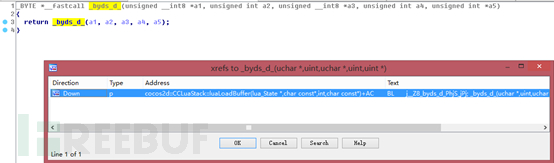 We see that the name of this function is the same as the call to xxtea_decrypt in the source code. We also included this function in the breach at the beginning. Now you can clearly see that after the script has been decrypted by byds_d, it has been decompressed again. It should be basically clear now. The lua script should be compressed and encrypted, so if you want to restore it, you should first decrypt it with xxtea and then decrypt it. compression. You can find a script to decompress zlib on GitHub, which can be used to decompress the decrypted text
We see that the name of this function is the same as the call to xxtea_decrypt in the source code. We also included this function in the breach at the beginning. Now you can clearly see that after the script has been decrypted by byds_d, it has been decompressed again. It should be basically clear now. The lua script should be compressed and encrypted, so if you want to restore it, you should first decrypt it with xxtea and then decrypt it. compression. You can find a script to decompress zlib on GitHub, which can be used to decompress the decrypted text
 Then look at index.lua:
Then look at index.lua:
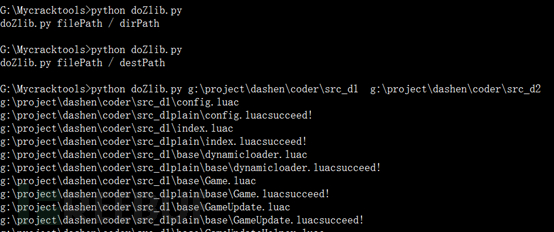 You can see that it has become clear text now.
You can see that it has become clear text now.
The above is the detailed content of How idaPro analyzes app decryption lua script. For more information, please follow other related articles on the PHP Chinese website!




