
In the era of digital economy, data, as a new production factor and strategic resource, is an important driving force for scientific and technological progress, policy formulation and economic development. However, the value of data can only be maximized if privacy and security are guaranteed.
In recent years, with the promulgation and implementation of the "Cybersecurity Law", "Data Security Law" and "Personal Information Protection Law", the state, industry and local governments have successively issued a series of supporting policy documents related to data security. , improve the data element management system and ensure the security of data circulation transactions. In particular, the "Twenty Data Articles" released at the end of 2022 have further promoted the compliant and efficient circulation and use of public data, corporate data, and personal data. Data "usable but not visible" and "controllable and measurable" have become legal requirements.
In the way of promoting the implementation of the twenty concepts of data, privacy computing has received more and more attention as the key "technical solution" to balance data circulation and value release. Among the 25 emerging technologies worthy of attention listed in the 2022 Gartner Hype Cycle, 6 are related to privacy computing, which shows its value and potential.
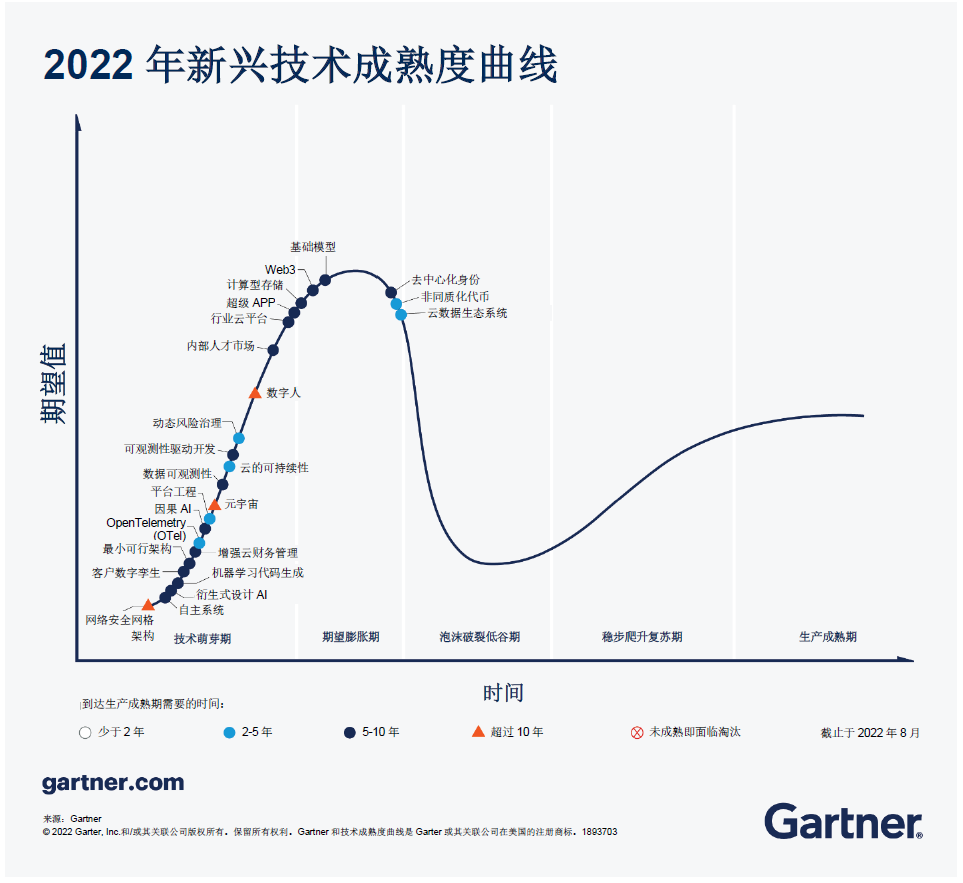
Image source: gartner.com
In January this year, the Ministry of Industry and Information Technology , the Cyberspace Administration of China, the National Development and Reform Commission and other 16 departments issued the "Guiding Opinions on Promoting the Development of the Data Security Industry", which clearly proposed to strengthen the research on key technologies such as privacy computing and data flow analysis, and strengthen the research and development of data quality assessment, privacy computing and other products.
The privacy computing industry is also accelerating its rise. According to a report from the China Academy of Information and Communications Technology, China's private computing market is expected to reach 10 billion yuan in 2025.
Privacy computing is the abbreviation of Privacy-preserving Computation, which can ensure that the data provider does not leak the original data. Analyzing, processing and using data is a broad concept that involves the cross-fusion of many disciplines and fields such as artificial intelligence and data science, covering secure multi-party computation, homomorphic encryption, differential privacy, zero-knowledge proof, federated learning, Trusted execution environment and many other technical sub-items, as well as the combination of these technical sub-items and related product solutions.
Secure Multi-Party Computation
was developed in 1982 by Academician Yao Qizhi, winner of the Turing Award Founded by asking and answering the "Millionaire Question". Secure multi-party computation can ensure that each participant only obtains correct calculation results and cannot obtain any information other than the calculation results. It is a comprehensive application of a variety of cryptographic basic tools. In addition to obfuscated circuits, secret sharing, inadvertent transmission and other cryptographic principle structures, In addition to the classic multi-party secure computing protocol, all other cryptographic algorithms used to implement multi-party secure computing (such as homomorphic encryption and zero-knowledge proof) can form a multi-party secure computing protocol. After more than 30 years of theoretical research, secure multi-party computing has become technically mature. It can be used in scenarios where common customers or interests need to be identified but other data needs to be protected, such as joint research in the medical field, or data sharing between enterprises to improve Business efficiency has exerted important application value.
Confidential Computing
The basic principle of confidential computing is to store the data or code that needs to be protected In a Trusted Execution Environment (TEE), any access to these data and codes must go through hardware-based access control to prevent unauthorized access or modification during use, thereby realizing the data processing process. Verifiable and controlled to enhance data security. Among them, a trusted execution environment is defined as an environment that can provide a certain level of protection in terms of data confidentiality, data integrity and code integrity, including cloud environments. Confidential computing can be traced back to the launch of TrustZone technology by ARM in 2002. The launch of SGX technology by Intel in 2015 marked the rapid development stage of confidential computing. Now AMD, Huawei and other manufacturers have also launched their own confidential computing technologies.
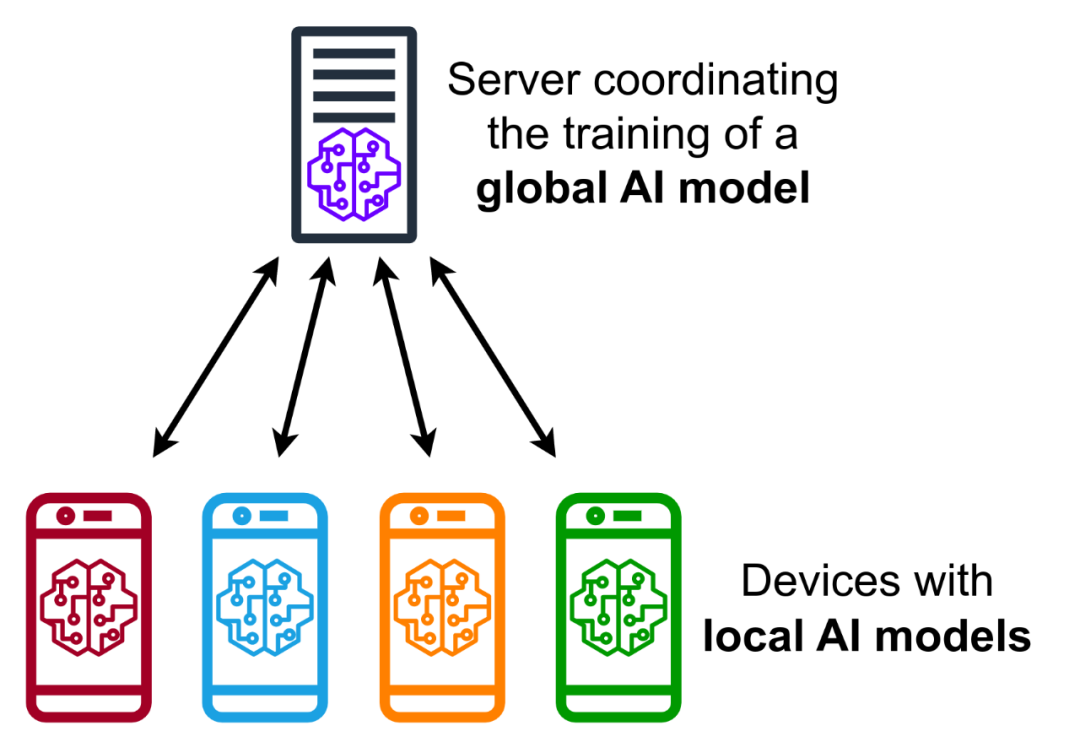
Use federated learning to jointly train machine learning models on multiple mobile terminals. Image source: Wikipedia
##Federated Learning
Federated learning was proposed by Google in 2016. Its core idea is to allow two or more participants to collaboratively complete the construction and use of models without data leaving the domain. It emphasizes that "data does not move the model "Mobile, data available but not visible" is suitable for joint computing application scenarios with many participating users, many data features and widespread distribution. According to the distribution of data participating in calculations among data parties, it can be divided into horizontal federated learning, vertical federated learning and federated transfer learning. Usually, federated learning needs to be used in conjunction with other privacy protection technologies to protect data during the calculation process.
Currently, privacy computing is in a stage of rapid development, with single-point technologies continuing to be optimized and multi-technologies present in practical applications. Integrated situation to meet the data security and privacy protection needs in different scenarios. According to Gartner's "2022 Privacy Technology Hype Cycle" report, privacy computing technology is expected to be commercially applied on a large scale in the next 5-10 years, and by 2025, more than 60% of large organizations will use it in data analysis, business intelligence or cloud computing. One or more privacy computing technologies.
As technological gains and business implementation scenarios gradually become more abundant, companies such as big data, artificial intelligence, blockchain, and cloud services have entered the privacy computing industry, and various players are actively promoting privacy computing. High technology penetration and the process of expanding application boundaries together constitute the landscape of China's privacy computing industry.
Among them, Internet giants such as Tencent, Ant, Alibaba, Baidu, and ByteDance have strong technical strength, huge user base and partners, and sit on massive amounts of high-value data. They are A force that cannot be ignored among those entering the privacy computing industry. These companies can not only accelerate the development of private computing technology and create new industry opportunities and development space, but are also expected to reshape the relationship between companies and users, and even affect the balance of industry power and market structure.
Tencent
Tencent independently developed a big data processing platform as early as 2009 and released high-performance computing in 2015 The framework Angel supports 1 billion dimensions of algorithm training and unstructured data processing, and is widely used in businesses such as WeChat Pay, QQ, and Tencent Video. In order to better respond to the needs of data security and privacy protection, Tencent actively explores privacy computing technology, established a dedicated R&D team in 2019, and made efforts to cultivate internal talents. In 2021, Tencent's fourth-generation big data platform "Tiangong" was released, aiming to break through data islands in a secure manner and create a safe, intelligent, and unified new data infrastructure. Among them, privacy computing is the core technology to ensure the security of data when machine learning and big data analysis are implemented in various scenarios.
The Angel PowerFL secure joint computing platform, the core product of Tiangong Platform, is the result of Tencent’s focus on the cutting-edge technology field of privacy computing. It has currently passed the China Financial Certification Center (CFCA), China Credit It has been evaluated by authoritative organizations such as Tongyuan Institute of Technology, and has been implemented in finance, advertising, medical, government affairs and other scenarios, and has achieved good application results. Another core product, Tencent Cloud Security and Privacy Computing Platform, is a distributed computing platform based on federated learning, multi-party secure computing, blockchain, TEE and other security technologies. It relies on Angel PowerFL capability support and focuses on strong security, high performance and strong stability. , easy-to-use four core capabilities and features, enabling the original cooperation data to realize joint modeling, secure intersection (PSI), hidden query, security statistical analysis and other functions without leaving the local area, helping the product application layer to fully meet industry needs and users The pain points have been actually applied in multiple scenarios such as cross-agency data cooperation, bank credit, insurance, government affairs, and online education.
Tencent Angel PowerFL privacy computing team is also one of the earliest teams in China to carry out research and application of privacy computing and federated learning technology. It is engaged in big data, distributed computing, distributed machine learning, distributed He has rich R&D and application experience in the fields of message middleware, multi-party secure computing, and applied cryptography. He has published nearly 10 privacy computing research papers, submitted more than 60 privacy computing technology invention patent applications, and has multiple commercial privacy computing technologies. and federated learning platform products are currently open to the outside world through Tencent Cloud. The team has won the most influential and authoritative awards in the privacy computing industry for three consecutive years, including the 2020 iDASH International Privacy Computing Competition Trusted Computing Track Champion, the 2021 iDASH Federated Learning Track Champion, and the 2022 iDASH Homomorphic Encryption Track Champion. .
Currently, Tencent Privacy Computing brings together technologies from the fields of Tencent Big Data, Tencent Security, Tencent Billing, Tencent Cloud, Tencent Advertising AI, and cryptography, privacy computing, big data and machine learning from Huazhong University of Science and Technology. expert. By combining Tencent's diverse technological capabilities and deeply integrating federated learning, secure multi-party computing, blockchain and other technologies, we help customers break data silos and activate the maximum value of data use. In the future, we will continue to integrate privacy computing and cloud AI security technology, and cooperate with other enterprises and institutions to promote the wider implementation of privacy computing.
Ant
Ant Group has been laying out privacy computing since 2016. In technology research and development, product services Many achievements have been made in aspects such as environmental protection and ecological co-construction. Ant holds the largest number of private computing patents in the industry, and has proposed new technologies such as trusted dense state computing and controlled anonymity. In terms of products and services, the open source trusted privacy computing framework SecretFlow supports almost all current mainstream privacy computing technologies and actively supports interconnection; the open source trusted execution environment privacy computing operating system Occlum is compatible with the API of the Linux environment, making it Existing applications can run in a trusted execution environment with little need for modification, significantly lowering the threshold for TEE application development. For commercial use, the Ant Privacy Computing All-in-One provides a system platform that integrates software and hardware with a full stack of trust, serving as an ideal platform for organizations. Provides one-stop security solutions for joint data computing among enterprises; Ant Chain Moss, a large-scale multi-party secure computing commercial platform, is the first in the industry to pass the multi-party secure computing product evaluation (CAICT MPC evaluation) and the first batch to pass the Gold Standard Committee MPC evaluation products, as of February 2022, it has served more than 150 industry customers. In terms of ecology, Ant also actively promotes the formulation of international and domestic industry standards and is the leading organization for many important standards.
##Alibaba
Alibaba Group is widely involved in the field of privacy computing. Its Alibaba Security, Alibaba Cloud and Damo The institute carries out relevant research. Alibaba Security’s Gemini Laboratory focuses on homomorphic encryption, secure multi-party computation and other directions. Its R&D technology has been widely used in Alibaba’s business, and some technologies have reached the leading level in the industry. Alibaba Cloud first released a trusted virtualization instance based on chip security in 2020, and released the DataTrust privacy-enhanced computing platform in 2021. Based on homomorphic encryption and a trusted execution environment, it ensures data security and privacy while supporting multi-party data collaborative analysis and Forecast, which is not affected by data scale or complexity, is the first public cloud-native encrypted computing product in China. DAMO Academy released the FederatedScope federated learning framework in 2022 and made it open source. It supports large-scale and efficient federated learning asynchronous training in rich application scenarios. It is compatible with different device operating environments such as PyTorch and Tensorflow, which greatly reduces the cost of federated learning. Development difficulty and cost in scientific research and practical applications.
Baidu
Baidu released the "Data Security Policy" in 2012 and established a Data Privacy Protection Committee in 2018. At present, privacy computing, as the underlying basic technology, is deployed on Baidu Smart Cloud, Baidu Security, Baidu Super Chain and other platforms, and combines multiple technologies to launch solutions to achieve application implementation. Baidu Smart Cloud also integrates with the blockchain platform to promote the implementation of privacy computing in various scenarios by incorporating blockchain technology into the process of cloud computing and privacy computing. Baidu Dianshi, a big data service platform under Baidu Brain, is based on mainstream privacy computing technologies such as federated learning, multi-party secure computing, and trusted execution environments to safely and efficiently implement data empowerment and help customers increase the value of their data. Baidu Dianshi Security Computing Platform (MesaTEE) is an important platform for Baidu Security to implement privacy computing for enterprises. Based on PaddleFL, the open source federated learning framework developed by Baidu Paddle, cooperation between enterprises can be carried out securely at the data level. PaddleFL provides a variety of federated learning strategies and their applications in computer vision, natural language processing, recommendation algorithms and other fields.
ByteDance
ByteDance has a relatively concentrated layout in the field of privacy computing, and its most important product is the Fedlearner federated learning platform. The project was launched in 2019. It was initially customized for a single enterprise and based on neural network vertical federated learning technology to help enterprises improve the efficiency of advertising. Through subsequent iterations, it will gradually be implemented in the fields of e-commerce, Internet finance and education. In 2020, Fedlearner is open source and supports multiple types of federated learning models. The entire system includes console, trainer, data processing, data storage and other modules. Each module is symmetrically deployed on the clusters of both parties participating in the federation, and communicates with each other through agents to achieve training. As a member of the Privacy Computing Alliance (CCC), ByteDance is also involved in promoting the development of the private computing market, influencing technology and regulatory standards, and helping to improve computing trust and security for the next generation Internet.
As data security and compliance circulation become inevitable, privacy computing is the only technical solution to realize the "usable and invisible" of data at present, which will have a great influence on the future technology industry. and key areas of the real economy will have an important impact. In addition to typical financial, medical and other scenarios, privacy computing is also being explored in more and more industries and fields.
For example, through privacy computing, electric power companies can protect the entire life cycle of power grid data, allowing the data to be safely uploaded to the cloud, or outsourced to computing service providers for calculations, realizing the power Reduce costs and increase efficiency of enterprises. Advertising platforms use privacy computing to encrypt user data and make the original data non-identifiable, thereby completing ad targeting and personalized recommendations without revealing personal information. Using technologies such as federated learning, they can achieve this without sharing original user data. Multiple parties jointly train a machine learning model, and can also complete personalized recommendations in the user terminal, ensuring the recommendation effect while maximizing user privacy protection. In the future, innovative privacy protection solutions, including trusted execution environments for mobile devices, can achieve a satisfactory user experience and protect user privacy in mobile personalized recommendation services, truly achieving a win-win situation. In the field of travel, privacy computing allows operators and service providers to use online data in an encrypted state to analyze and predict urban traffic conditions and travel needs, providing a basis for traffic dispatch and new business innovation, while protecting user privacy and data. Safety.
We have seen that fully releasing the value of data can promote revolutionary innovation. Just imagine products that are smarter than ChatGPT entering our lives, understanding our interests and habits, and providing customization Personalized services make work and life more convenient and personalized than ever before. In this process, privacy computing will serve as an indispensable part of new technology applications, allowing data to remain secure and controllable while creating value, and protecting people's reasonable expectations for privacy protection.
The above is the detailed content of Born for data, fighting for privacy: the accelerated rise of the private computing industry. For more information, please follow other related articles on the PHP Chinese website!
 What skills are needed to work in the PHP industry?
What skills are needed to work in the PHP industry?
 How to insert page numbers in ppt
How to insert page numbers in ppt
 js method to generate random numbers
js method to generate random numbers
 What should I do if the USB disk cannot be read on the computer?
What should I do if the USB disk cannot be read on the computer?
 The difference between sqlserver and mysql
The difference between sqlserver and mysql
 Usage of isalpha function
Usage of isalpha function
 Common Linux download and installation tools
Common Linux download and installation tools
 computer virus
computer virus




