
With the 5G network expectations With the development of digital transformation, the 6G communication era envisions how humans will interact with the digital virtual world after 2030 to cope with the communication and network challenges after 2030. While traditional applications (such as multimedia streaming) will still exist, the article envisions new application areas for 6G systems, such as multi-sensor extended reality (XR) applications, connected robots and autonomous systems (CRAS), and wireless brain-computer interaction (BCI) [1]. Holographic telepresence, eHealth (including in vivo networks) are other 6G use cases that require extremely high data rates, ultra-low latency and ultra-reliability [2].
6G revolutionizes wireless networks from connected things to “connected intelligence” [1], [2]. Therefore, artificial intelligence becomes an integral part of the network. Distributed heterogeneous networks require ubiquitous AI services to ensure 6G goals are achieved. Intelligent wireless communications, network closed-loop optimization, and 6G big data analysis emphasize the use of artificial intelligence in all aspects of 6G networks.
After 2030, wireless applications will require higher data rates (up to 1 Tb/s), extremely low end-to-end latency (
This section also discusses the Security issues arising from architectural changes and new technologies. Figure 1 illustrates possible attacks on different layers of the 6G architecture, outlining how this paper presents the security threat picture for 6G.
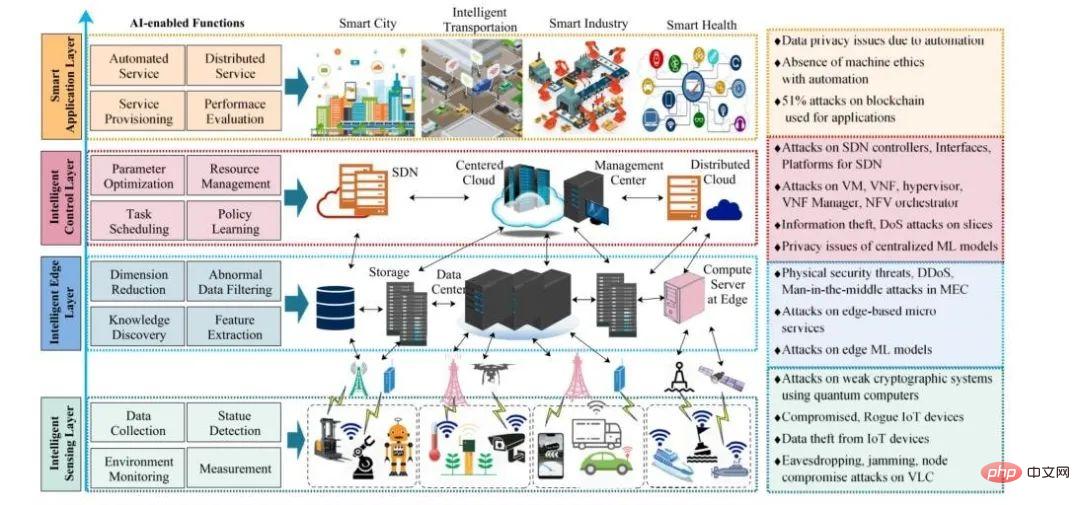
Figure 1 Intelligent 6G architecture [6] and 6G security and privacy issues
in 5G Network softwareization technologies such as software-defined networking (SDN), network functions virtualization (NFV), multi-access edge computing (MEC), and network slicing are still applicable to 6G systems; therefore, their security issues still exist in 6G. Prominent security issues related to SDN are attacks on SDN controllers, attacks on northbound and southbound interfaces, inherent vulnerabilities in the platforms used to deploy SDN controllers/applications [7]. NFV-related security issues are attacks on virtual machines (VMs), virtual network functions (VNFs), hypervisors, VNF managers, and NFV coordinators [8]. Due to the massively distributed nature of 6G systems, MEC in 6G is subject to physical security threats, distributed denial of service (DDoS), and man-in-the-middle attacks. A potential attack on network slicing is a DoS attack, where information is stolen through a compromised slice. Attacks on network softwareization technologies prevent 6G networks from achieving the promised dynamism and full automation.
6G envisions the Internet of Everything (IOE), a collection of billions of heterogeneous devices. A basic device security model that relies on SIM cards is not a realistic deployment of IOE in 6G, especially for small form factor devices such as in-body sensors. In such a large network, key distribution and management functions are inefficient. Resource-constrained IoT devices are unable to provide complex passwords to maintain strong security, making them prime targets for attackers. These devices can be compromised and potentially used to launch attacks. Hyperconnected IOEs pose privacy concerns for providing data collection for 6G applications. Exploiting resource-constrained IoT devices for data theft will impact data privacy, location privacy, and identity privacy.
Existing 5G network deployments typically serve vertical industries such as industry, healthcare, and education. 6G further extends this concept by allowing smaller networks such as in-body networks, swarms of drones, environmental sensor networks with longer battery life [4]. These local networks operate as independent networks and interoperate with wide area connections when needed. Unlike well-defined native 5G networks, many stakeholders implement native 6G networks with varying levels of embedded security. On-premises 6G networks with minimal security provide an opportunity for intruders to launch attacks. Then infiltrate into the network of trust-compromised networks.
Dense cellular deployments, mesh networks, multiple connections and device-to-device (D2D) communications will become the norm in 6G. Malicious parties are more likely to exploit distributed networks with more vulnerable devices, each with mesh connectivity, increasing the threat surface. The definition of subnetworks requires changes to the security policy. It is far from practical for a WAN to provide security for a large number of devices within each subnet. In 6G, a hierarchical security mechanism that distinguishes subnet-level communication security and subnet-to-WAN security will be a better approach. 6G networks will coexist with frameworks such as zero-touch networking and service management (ZSM) architectures to shorten service time to market, lower operational costs and reduce human error. Full automation with self-learning capabilities allows attacks to propagate in a closed loop and data privacy protection is extremely challenging because in a zero-touch network, automation and less human intervention are required.
6G relies on artificial intelligence to achieve a fully autonomous network . Therefore, attacks on AI systems, especially machine learning (ML) systems, will impact 6G. Poisoning attacks, data injection, data manipulation, logic destruction, model evasion, model inversion, model extraction, and membership inference attacks are potential security threats against ML systems. A larger set of features makes AI systems perform better. Attacks on collected data, as well as inadvertent use of private data, can lead to privacy concerns because data processing is often invisible to users. Blockchain is also a key technology to unlock the potential of 6G systems. Blockchain is suitable for decentralized resource management, spectrum sharing and service management in large-scale distributed 6G networks. A 51% attack is feasible on quantum computers to destabilize a blockchain. Since blockchain networks store data publicly, privacy protection is challenging. The current 5G standard does not address the security issues posed by quantum computing; instead, it relies on traditional cryptography such as elliptic curve cryptography (ECC). Since the 6G era marks the emergence of quantum computers, current security mechanisms based on asymmetric key encryption are vulnerable to quantum computer-based attacks. Therefore, without the design of quantum-safe cryptographic algorithms, secure 5G communications utilizing asymmetric key cryptography may no longer be suitable for post-quantum security.
Multi-connectivity mesh networks with microcells in 6G allow devices to communicate simultaneously through multiple base stations. Edge-based ML models can be used for dynamic detection of privacy-preserving routing, ranking devices, and allowing devices to transmit data through privacy-preserving routing based on ranking. Compared to cloud-based centralized learning, federated learning keeps data close to users to enhance data privacy and location privacy. 6G subnetwork-level AI allows privacy to be preserved within the subnetwork and only shared externally learned information to minimize privacy risks. Restricting data within a network is suitable for applications such as in vivo networks. With the vast number of applications in 6G and the massive collection of data to feed intelligent models, users will choose different levels of privacy on different applications. AI-based service-oriented privacy protection policy updates are potential solutions to support fully automated 6G networks.
[1] W.Saad, M.Bennis, and M.Chen, “A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems, ” IEEE Network, vol. 34, no. 3, pp. 134–142, 2019
[2] C. de Alwis, A. Kalla, Q. V. Pham , P. Kumar, K. Dev, W. J. Hwang, and M. Liyanage, “Survey on 6G Frontiers: Trends, Applications, Requirements, Technologies and Future Research,” IEEE Open Journal of the Communications Society, pp. 1–1, 2021.
[3]J. Lin, W. Yu, N. Zhang, X. Yang, H. Zhang, W. Zhao, A survey on internet of things: architecture, enabling technologies, security and privacy, and applications, IEEE Internet Things J. 4 (5) (2017) 1 125–1 142 .
[4]T. Shinzaki , I. Morikawa , Y. Yamaoka , Y. Sakemi , IoT security for utilization of big data: Mutual authentication technology and anonymization technology for positional data, Fujitsu Sci. Tech. J. 52 (4) (2016) 52–60 .
[5]M. Ylianttila, R. Kantola, A. Gurtov, L. Mucchi, I. Oppermann, Z. Yan, T. H. Nguyen, F. Liu, T. Hewa, M. Liyanage et al., “6G White Paper: Research Challenges for Trust, Security and Privacy,” arXiv preprint arXiv :2004.11665, 2020.
[6]K. B. Letaief, W. Chen, Y. Shi, J. Zhang, and Y.-J. A. Zhang, “The Roadmap to 6G: AI Empowered Wireless Networks,” IEEE Communi cations Magazine, vol. 57, no. 8, pp. 84–90, 2019.
[7]I. Ahmad, T. Kumar, M. Liyanage, J. Okwuibe, M. Ylianttila, and A . Gurtov, “Overview of 5G Security Challenges and Solutions,” IEEE Communications Standards Magazine, vol. 2, no. 1, pp. 36–43, 2018.
[8]R. Khan, P. Kumar , D. N. K. Jayakody, and M. Liyanage, “A survey on security and privacy of 5g technologies: Potential solutions, recent advancements, and future directions,” IEEE Communications Surveys & Tutorials, vol. 22, no. 1, pp.196–248 , 2019.
The above is the detailed content of AI meets 6G—opportunities and challenges. For more information, please follow other related articles on the PHP Chinese website!




