
The principle of AUTH permission management
The four simplest data tables of auth permission management are as follows
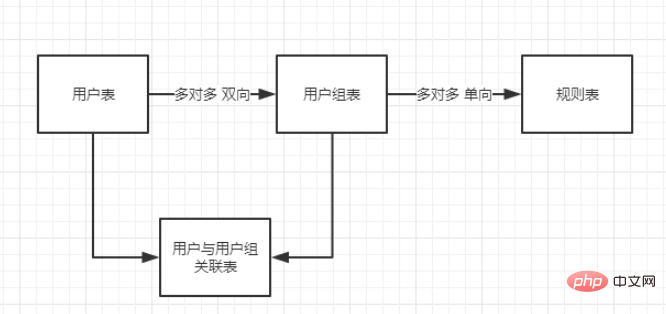
Each one A url path corresponding to the function, the rule table actually records the url path, and implements permission management through the url
Classification of permission verification timing
Pre-verification
The so-called pre-authentication means that the permissions of the internal elements of the currently accessible page are verified before they are displayed. For example: when visitors visit a web page, they cannot see a certain function menu, but administrators can see it, etc. The user experience of pre-verification is good, but the performance is poor
Post-authentication
The so-called post-authentication is simple, that is, the permissions are verified first when accessing each function. For example, click the 'Add Column' button on the page, verify it first, and then execute the add column function code after passing it. Post-verification user experience is poor, but performance is good
Permission verification code implementation location
After the user successfully logs in to the backend, all menu, navigation, and button operations in the backend will be Permission verification is required
But the backend home page, welcome page, user exit and other functions do not require permission verification, which can be customized according to specific project requirements
The difference between AUTH permission management and RBAC permission management
Similar points: both are role-based permission management
Differences: The design of the data table is different, resulting in more flexible AUTH and more delicate permission management
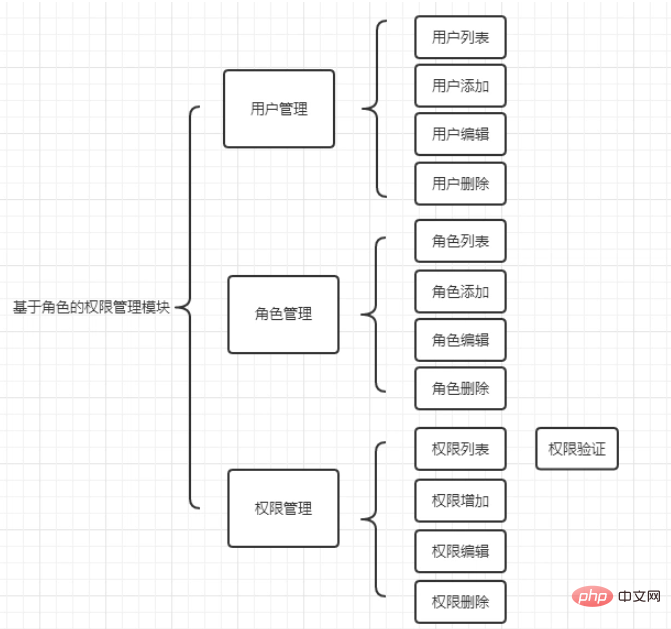
Permission module design
Recommended tutorial: "TP5"
The above is the detailed content of About AUTH permission management of THINKPHP. For more information, please follow other related articles on the PHP Chinese website!