
Shiro’s Unified Authentication and Authorization
Shiro is a simple, easy-to-use Java permissions framework under Apache. For single applications, Shiro can perfectly and quickly meet permission requirements. Therefore, Shiro will generally become the first choice of developers when working on projects.
However, if you need to make a second, third, or nth application that also requires the same authentication and authorization, you may need to extend Shiro or integrate other frameworks. It meets your needs very well.
How Shiro performs authentication and authorization
Shiro itself does not help you achieve authentication and authorization, but Shiro has well defined some concepts related to permissions, allowing you to complete specific implementations
Authentication
In Shiro, completing authentication is generally subject.login(token). Subject represents a user, and Token represents the authorization information submitted when a user requests authorization. Through AuthenticatingRealm .doGetAuthenticationInfo() obtains some information about the current Subject, such as Principals, Credentials, and verifies the submitted token. If the login is successful, save the current logged-in user
Authorization
in Shiro , Permission control is generally like @RequiresPermissions. When a user accesses a protected resource, Shiro will use AuthorizingRealm.doGetAuthorizationInfo() to obtain the user's permissions from the Principals of the currently authenticated Subject to determine whether the user can access the resource
In Shiro, the above two things are accomplished by implementing Realm. When you have a single application, it is very simple to complete the authentication and authorization of the application.
But what should you do when you have multiple applications and need to reuse the same set of users and permission information? You can reuse Realm and the user permissions are in the same db. This is possible, but The coupling is too high, and different applications must access the same data source; or the DAO related to user permissions can be stripped out and used as an RPC or Rest call, which can also be implemented; but a better way is to separate the entire authentication and authorization Come out and serve as an authentication and authorization service alone
Unified authentication and authorization based on Shiro
In order to achieve unified authentication and authorization, Shiro has CasFilter, which can integrate CAS, but CAS is another set of frameworks, which is more important , there is a separate learning cost, so here is a simpler, lightweight, easy-to-use, Shiro-based authentication and authorization service shiro-uaa
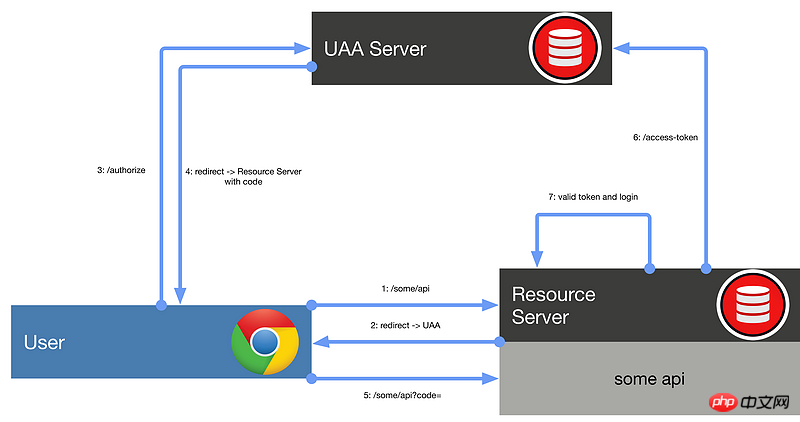
Authentication and authorization process
User requests protected resources Resource Server
Resource Server determines whether the user is logged in
If not logged in, Resource Server guides the user to UAA Server to log in
The user logs in to the UAA Server. If the login is successful, the UAA Server returns the code to the user and guides the user to the previously visited Resource Server
Resource Server uses code to obtain access-token from UAA Server. The token contains user authorization information
Resource Server verifies whether the accessToken is legal. If it is legal, saves the user information in Resource Server
As shown below:
Use
auth-server
Quote maven
Implement your own login
resource-server
Quote maven
Like shiro, use relevant annotations for permission control
Detailed explanation of Shiro authorization implementation
##Apache Shiro User Manual (1) Shiro Architecture IntroductionThe above is the detailed content of Introduction to Java Permission Framework: Shiro's Unified Authentication and Authorization. For more information, please follow other related articles on the PHP Chinese website!




