
# 三个配置文件: # testserver1: server_name testserver1 www.rona1do.top; root /opt/app/code1; # testserver2: server_name testserver2 www.rona1do.top; root /opt/app/code2; # testserver3: server_name testserver3 www.rona1do.top; root /opt/app/code3;
Configure the three virtual hosts with the same server_name mentioned above The host will access testserver1 first, and the priority of access is based on the server's reading order, that is, the order of file names.
=: Exact matching of ordinary characters, that is, complete matching
^~ : Indicates ordinary character matching, use prefix matching
: Indicates performing a regular match (adding is not case-sensitive)
4. The difference between Nginx’s alias and root# 先检查对应的url地址下的文件存不存在,如果不存在找/index.php,类似于重定向 location / { try_file $uri /index.php; }Copy after login
location /request_path/image/ {
root /local_path/image/;
}
# 请求:http://www.rona1do.top/request_path/image/cat.png
# 查询: /local_path/image/request_path_image/cat.pnglocation /request_path/image/ {
alias /local_path/image/;
}
# 请求:http://www.rona1do.top/request_path/image/cat.png
# 查询: /local_path/image/cat.pngGeneral solution: You can negotiate with the first-level agent and set the header information x_real_ip to record the user’s ip6. Common error codes in Nginx
set x_real_ip=$remote_addr
- 系统全局性修改、用户局部性修改、进程局部性修改
Configuration File:
/etc/security/limits.conf# root:root用户 root soft nofile 65535 # hard 强制限制、soft 超过会发送提醒(邮件等),不限制 root hard nofile 65535 # *:所有用户 * soft nofile 65535 * hard nofile 65535Copy after loginProcess locality modification
/etc/nginx/nginx.conf# 针对nginx进程进行设置 worker_rlimit_nofile 35535;Copy after login4. CPU affinity
Number of physical CPUs:
<div class="code" style="position:relative; padding:0px; margin:0px;"><pre class="brush:php;toolbar:false;"># /etc/nginx/nginx.conf
# nginx建议数量跟cpu核心数保持一致
worker_processes 2;
# 配置cpu亲和
worker_cpu_affinity 0000000000000001 0000000000000010
# 与上一行等价,自动对应(Nginx1.9版本以上)
worker_cpu_affinity auto</pre><div class="contentsignin">Copy after login</div></div>
ps -eo pid, args,psr | grep [n]ginx
5. Nginx general configuration optimization<div class="code" style="position:relative; padding:0px; margin:0px;"><pre class="brush:php;toolbar:false;"># nginx服务使用nginx用户(最好不要使用root用户)
user nginx;
# cpu亲和(最好跟核心数保持一致)
worker_processes 2;
worker_cpu_affinity auto;
# error的日志级别设置为warn
error_log /var/log/nginx/error.log warn;
pid /var/run/nginx.pid;
# 文件句柄对于进程间的限制(建议1w以上)
worker_rlimit_nofile 35535;
# 事件驱动器
events {
use epoll;
# 限制每一个worker_processes进程可以处理多少个连接
worker_connections 10240;
}
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
#字符集(服务端响应发送的报文字符集)
charset utf-8;
log_format main &#39;$remote_addr - $remote_user [$time_local] "$request" &#39;
&#39;$status $body_bytes_sent "$http_referer" &#39;
&#39;"$http_user_agent" "$http_x_forwarded_for"&#39;;
access_log /var/log/nginx/access.log main;
# 静态资源的处理
sendfile on;
#tcp_nopush on;
keepalive_timeout 65;
# gzip压缩(对于IE6或以下版本对于gzip压缩支持不是很好)
gzip on;
# IE6或以下不进行压缩(兼容)
gzip_disable "MSIE [1-6]\.";
gzip_http_version 1.1;
include /etc/nginx/conf.d/*.conf;
}</pre><div class="contentsignin">Copy after login</div></div>3. Nginx security
secure_link_module, improves encryption verification and effectiveness of data security, suitable for core important data
acces_module, serves the backend and some users Data provides IP prevention and control
后台密码撞库,通过猜测密码字典不断对后台系统尝试性登录,获取后台登录密码
后台登录密码复杂度
access_module,对后台提供IP防控
预警机制(一个IP在一段时间内重复不断请求等)
利用一些可以上传的接口将恶意代码植入到服务器中,再通过url去访问以执行代码
例:http://www.rona1do.top/upload...(Nginx将1.jpg作为php代码执行)
# 文件上传漏洞解决办法
location ^~ /upload {
root /opt/app/images;
if ($request_file ~* (.*)\.php){
return 403;
}
}利用未过滤/未审核用户输入的攻击方法,让应用运行本不应该运行的SQL代码
Nginx+LUA配置WAF防火墙防止SQL注入
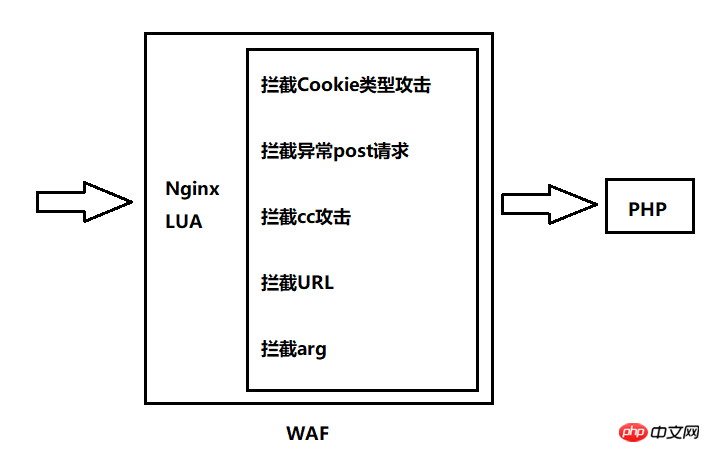
ngx_lua_waf 下载地址
使用waf步骤:
git clone https://github.com/loveshell/ngx_lua_waf.git
cd ngx_lua_waf
mv ngx_lua_waf /etc/nginx/waf
vim /etc/nginx/waf/conf.lua,修改RulePath为对应路径(/etc/nginx/waf/wafconf)
vim /etc/nginx/waf/wafconf/post,加入一行,\sor\s+,放sql注入的正则
集成waf:
# /etc/nginx/nginx.conf lua_package_path "/etc/nginx/waf/?.lua"; lua_shared_dict limit 10m; init_by_lua_file /etc/nginx/waf/init.lua; access_by_lua_file /etc/nginx/waf/waf.lua
reload Nginx
waf/conf.lua配置文件中打开防cc攻击配置项
CCDeny="on"
CCrate="100/60" #每60秒100次请求
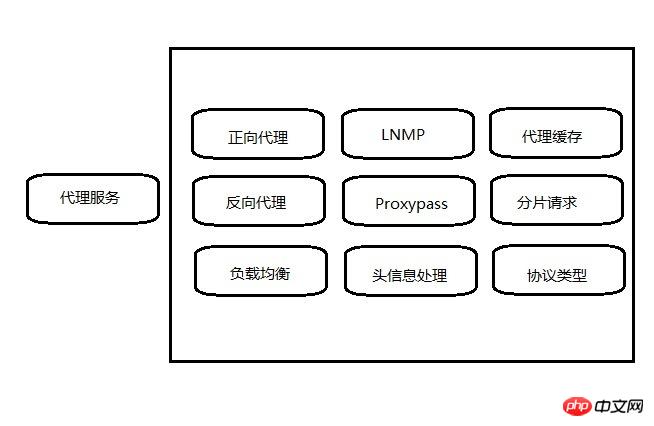
定义Nginx在服务体系中的角色
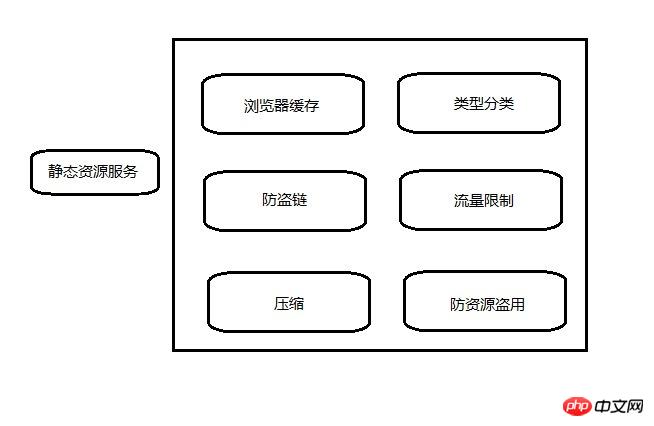
静态资源服务
代理服务
动静分离
设计评估
LVS、keepalive、syslog、Fastcgi
用户权限、日志目录存放
CPU、内存、硬盘
硬件
系统
关联服务
配置注意事项
合理配置
了解原理(HTTP、操作系统...)
关注日志
相关推荐:
The above is the detailed content of About Nginx architecture. For more information, please follow other related articles on the PHP Chinese website!




