
A large number of modern enterprises adopt web applications to seamlessly connect with their customers, but due to incorrect coding, many security issues are caused. Vulnerabilities in web applications can allow hackers to gain direct access to sensitive information (such as personal data, login information, etc.).
Web applications allow visitors to submit data and retrieve data from a database over the Internet. The database is the heart of most web applications. The database maintains the data that the web application uses to deliver specific content to visitors. The web application also obtains data from the database when delivering information to customers and suppliers.
SQL injection attack is the most common web application attack technique, which attempts to bypass SQL commands. When the user input is not "sanitized", if this input is performed, it will exhibit a SQL injection vulnerability.
Checking for SQL injection vulnerabilities mainly involves two aspects, one is auditing the user's web application, and the other is the best way to perform the audit by using an automated SQL injection scanner. Here, the author lists some SQL injection scanners that are valuable to web application developers and professional security auditors.
1. SQLIer
SQLIer can find a URL with a SQL injection vulnerability on the website and generate SQL injection vulnerability based on the relevant information. , but it does not require user interaction. In this way, it can generate a UNION SELECT query, which can then brute force the database password. This program does not use quotes when exploiting the vulnerability, which means it can be adapted to a variety of websites.
SQLIer Strong password via "true/false" SQL injection vulnerability. With the help of the "true/false" SQL injection vulnerability strong password, users cannot query data from the database. They can only query a statement that can return "true" and "false" values.
According to statistics, an eight-character password (including any character in the decimal ASCII code) only takes about 1 minute to crack.
The usage syntax is as follows, sqlier [option] [URL]
The options are as follows:
-c :[主机] 清除主机的漏洞利用信息 -s :[秒]在网页请求之间等待的秒数 -u:[用户名]从数据库中强力攻击的用户名,用逗号隔开。 -w:[选项]将[选项]交由wget 此外,此程序还支持猜测字段名,有如下几种选择: --table-names [表格名称]:可进行猜测的表格名称,用逗号隔开。 --user-fields[用户字段]:可进行猜测的用户名字段名称,用逗号隔开。 --pass-fields [口令字段]:可进行猜测的口令字段名称,用逗号隔开。
Let’s talk about its basic usage:
For example, assume the following There is a SQL injection vulnerability in the URL:
example.com/sqlihole.php?id=1
We run the following command:
sqlier -s 10 example.com/sqlihole.php?id=1
to get enough information from the database to exploit its password , where the number "10" means to wait 10 seconds between each query.
If the table, username field, and password field names are guessed correctly, the exploit program will submit the username to the query and prepare to brute force attack the password from the database.
sqlier -s 10 example.com -u BCable,administrator,root,user4
However, if the built-in field/table name does not guess the correct field name, the user can execute:
sqlier -s 10 example.com --table-names [table_names] --user-fields [user_fields] --pass-fields [pass_fields]
Unless the correct table name, username field, and password are known field name, SQLIer cannot brute force attack the password from the database.
2. SQLMap:
This is an automatic "blind" SQL injection tool developed with python , which performs a dynamic database management system fingerprinting that enables complete enumeration of remote databases. The goal is to implement a fully functional database management system tool that is capable of exploiting all flaws in web application programming that can lead to SQL injection vulnerabilities.
After SQLMap detects one or more SQL injection vulnerabilities on the target system, the user can choose from multiple options to perform comprehensive back-end database management system fingerprinting and retrieve database management system sessions. Users and databases, enumerating users, password hashes, databases, running its own SQL SELECT statements, reading specific files on the file system, etc.
This software fully supports back-end database management systems such as MySQL, Oracle, PostgreSQL, and Microsoft SQL Server. In addition, it also recognizes Microsoft's Access database, as well as DB2, Informix, Sybase, Interbase, etc.
The usage method is as follows:
sqlmap.py [选项] {-u <URL> | -g <google dork> | -c <配置文件>}
其中,-u URL指明目标URL
-g google dork 将google dork结果处理为目标url3. SQLID:
This tool is a SQL injection vulnerability digger. is a command line utility that can find SQL injection vulnerabilities and common errors in websites. It can perform several operations: find SQL injection vulnerabilities in web pages, test submitted forms, and look for the possibility of SQL injection vulnerabilities. It also supports HTTP, HTTPS, Basic Authentication, and more.
Its usage is as follows:
Sqid.rb [Option]
The options are as follows:
-m,--mode MODE,它指明以某种模式进行操作,其中MODE有以下几种情况:g,google:以google搜索模式操作;u,url检查这个url;p,page,它主要检查单一的网页;c,crawl,检查站点。
Among them, the google search mode options are as follows In several cases, -q, --quary query, QUERY executes google search; -s, --start START, zero index of the first result required; -r, --results RESULTS, specify the required Number of results, default value is 20.
4. SQL Power Injector
SQL Power Injector可帮助渗透测试人员找到并利用网页上的漏洞。目前,它支持SQL Server、Oracle、MYSQL、Sybase/Adaptive Sever和DB2等数据库,但在使用inline注入时,还可借助现有的数据库管理系统来使用此软件。
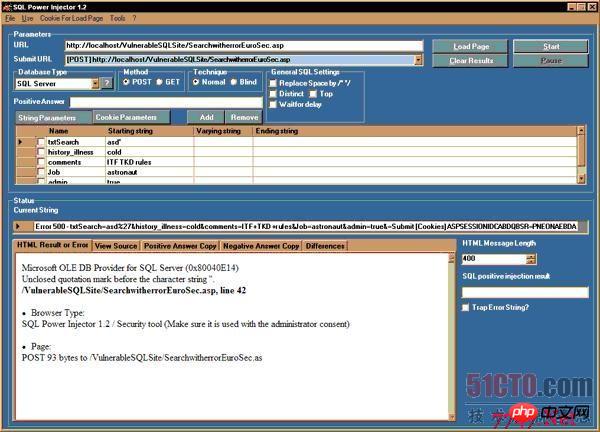
其自动化的工作模式以两种方式进行,一是比较期望的结果,二是根据时间延迟。
其工作状态如图:
五、SQLNinja:
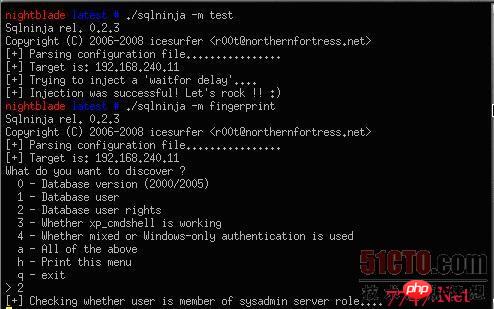
Sqlninja可以利用以SQL Server为后端数据支持的应用程序的漏洞,其主要目标是提供对有漏洞的数据库服务器的远程访问。Sqlninja的行为受到配置文件的控制,它告诉了Sqlninja攻击的目标和方式,还有一些命令行选项。比如,有如下一些命令选项:
-m<攻击模式>,其攻击模式有测试(test)、指纹识别(fingerprint)、强力攻击(bruteforce)等;
其它的命令选项,-v : 指明进行详细输出;-f:指明一个使用的配置文件。-w指明以强力攻击模式使用的单词列表。
如图是运行过程界面:
【相关推荐】
1. 特别推荐:“php程序员工具箱”V0.1版本下载
The above is the detailed content of Share five famous SQL injection vulnerability scanning tools. For more information, please follow other related articles on the PHP Chinese website!




