SecurityMultiTool-masterPHP Security Library is a set of advanced security layers that are easy to use, well-structured, fast and designed specifically for PHP-like web applications. This intrusion detection system does not provide any mitigation and anti-virus mechanisms, nor does it filter malicious input content. Its function is simply to identify malicious activities carried out by attackers against the site and provide timely reminders in the way that everyone needs. With a set of proven and very strict filtering rules, the detection system will give an impact rating value to any attack activity, helping users more easily understand how to respond to current hacker attacks. There are many ways to respond, including simply sending log records to the development team via an emergency email, displaying a warning message about the attacker, or even immediately terminating the user's current session.
All resources on this site are contributed by netizens or reprinted by major download sites. Please check the integrity of the software yourself! All resources on this site are for learning reference only. Please do not use them for commercial purposes. Otherwise, you will be responsible for all consequences! If there is any infringement, please contact us to delete it. Contact information: admin@php.cn
Related Article
 Nosecone: a library for setting security headers in Next.js, SvelteKit, Node.js, Bun, and Deno
Nosecone: a library for setting security headers in Next.js, SvelteKit, Node.js, Bun, and Deno
17 Dec 2024
We’re excited to announce Nosecone, an open-source library designed to make setting security headers—like Content Security Policy (CSP) and HTTP Strict Transport Security (HSTS)—straightforward for applications built with Next.js, SvelteKit, and othe
 How to use Composer to improve the security of Laravel applications: Applications of wiebenieuwenhuis/laravel-2fa library
How to use Composer to improve the security of Laravel applications: Applications of wiebenieuwenhuis/laravel-2fa library
18 Apr 2025
When developing a Laravel application, I encountered a common but difficult problem: how to improve the security of user accounts. With the increasing complexity of cyber attacks, a single password protection is no longer enough to ensure the security of users' data. I tried several methods, but the results were not satisfactory. Finally, I installed the wiebenieuwenhuis/laravel-2fa library through Composer and successfully added two-factor authentication (2FA) to my application, greatly improving security.
 How to ensure code security using Composer: Application of captainhook/secrets library
How to ensure code security using Composer: Application of captainhook/secrets library
17 Apr 2025
In team development, preventing sensitive information such as passwords from leaking to the version control system is an important issue. I once encountered this problem in a project: a team member accidentally submitted the database password to a Git repository, causing a security risk. To solve this problem, I used the captainhook/secrets library, which integrates easily through Composer, successfully detects and prevents the leakage of sensitive information.
 C# Sealed Class: When Should You Use It? (Specific scenario focus)
C# Sealed Class: When Should You Use It? (Specific scenario focus)
22 May 2025
The article discusses using C#'s sealed class in scenarios like finalizing class behavior, preventing accidental inheritance, improving performance, enhancing security, and controlling library design. It explains how sealing impacts inheritance and o
 What are the different types of classloaders in Java?
What are the different types of classloaders in Java?
04 Jul 2025
Java class loaders are divided into four categories. BootstrapClassLoader is implemented by C/C and is responsible for loading the JVM core class library such as rt.jar; ExtensionClassLoader loads the extended class library, with the default path being java.ext.dirs; ApplicationClassLoader is responsible for loading classes under the user class path, with the default path being controlled by java.class.path; Custom ClassLoader inherits the ClassLoader class and is used to implement specific loading logic, such as hot deployment, encrypted class loading, etc., and usually follows the parent delegation model to ensure security.
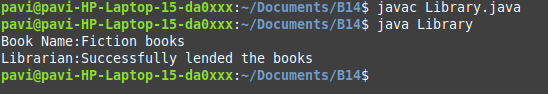 Java basic program with expansion
Java basic program with expansion
30 Dec 2024
Created a class as public class Library Created a object as Library books = new Library(); Object is memory representation of class. Most important object name should not be in capital. How to create an object in Java? {TBD} Java provides five ways


Hot Tools

A class to prevent SQL injection in PHP
A class to prevent SQL injection in PHP

PHP implements sensitive word filtering class
PHP implements sensitive word filtering class

Various interceptor classes in php
Various interceptor classes in php





