
Course Intermediate 11329
Course Introduction:"Self-study IT Network Linux Load Balancing Video Tutorial" mainly implements Linux load balancing by performing script operations on web, lvs and Linux under nagin.

Course Advanced 17632
Course Introduction:"Shangxuetang MySQL Video Tutorial" introduces you to the process from installing to using the MySQL database, and introduces the specific operations of each link in detail.

Course Advanced 11344
Course Introduction:"Brothers Band Front-end Example Display Video Tutorial" introduces examples of HTML5 and CSS3 technologies to everyone, so that everyone can become more proficient in using HTML5 and CSS3.
Ways to fix issue 2003 (HY000): Unable to connect to MySQL server 'db_mysql:3306' (111)
2023-09-05 11:18:47 0 1 822
Experiment with sorting after query limit
2023-09-05 14:46:42 0 1 724
CSS Grid: Create new row when child content overflows column width
2023-09-05 15:18:28 0 1 615
PHP full text search functionality using AND, OR and NOT operators
2023-09-05 15:06:32 0 1 577
Shortest way to convert all PHP types to string
2023-09-05 15:34:44 0 1 1003
Course Introduction: 求PHP网站后台管理 管理员 权限控制 系统方案小弟现在做一个网站后台,包括文章上传模块,供下载的文件上传,用户留言模块等。问题:后台管理员权限分配说明:现在系统有一个超级管理员,具有所有权限。现在想实现:超级管理员可以添加一般管理员,并且可以控制一般管理员的权限。比如控制某个一般用户只能上传文章,而不能上传图片等等,这该如何实现?求个思路,有源码实例更
2016-06-13 comment 0 1392

Course Introduction:PHP learning steps: How to use permission control management system Introduction: In modern software development, permission control is a very important part. Whether it is a website management system or a backend management system, permission control is an essential function. This article will introduce how to use the PHP programming language to implement a basic permission control management system. Step 1: Create a database table First, we need to create a database to store user and permission information. We can use MySQL or other relational databases to create tables. CREA
2023-08-26 comment 0 1038

Course Introduction:Title: Example of permission management module for Java online examination system Introduction: When developing an online examination system, the permission management module is an important component. Through permission management, we can restrict users' access to system functions and data. This article will use Java programming language to implement a simple permission management module for the online examination system and provide code examples. 1. Design ideas of the authority management module. The authority management module of the online examination system mainly includes functions such as user authentication, role management, authority allocation and authority control. Down
2023-09-24 comment 0 1231
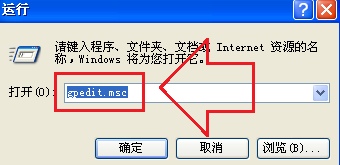
Course Introduction:Control Panel is the part of Windows that allows you to adjust some basic system settings. However, some WinXP users find that they cannot open the control panel and it shows that they do not have permission. So what can be done to solve this problem? What should I do if the WinXP system control panel cannot be opened without access rights? 1. Open the "Start" menu in XP and select the "Run" option, or use the shortcut key "Win+R" to bring up the run window, then enter "gpedit.msc" and press Enter or OK. 2. After opening the Group Policy window, expand the "User Configuration" > "Administrative Templates" > "Control Panel" option in the left menu, and double-click to open the "Control Panel" in the list on the right. 3. Then double-click the mouse to open the "Prohibit Access 'Control Panel'
2024-09-09 comment 0 900

Course Introduction:This article mainly introduces the basic principles of permission control in Linux systems. Security Model In the Linux system, all our operations are essentially processes accessing files. To access files, we need to obtain the corresponding access permissions first, and the access permissions are obtained through the security model in the Linux system. Regarding the security model in the Linux system, we need to know the following two points: The original security model on the Linux system is called DAC, whose full name is DiscretionaryAccessControl, which translates to autonomous access control. Later, a new security model was added and designed called MAC, whose full name is MandatoryAccessControl, which is translated as mandatory access control.
2023-12-31 comment 0 1295