
Course Advanced 10628
Course Introduction:The course content covers common PHP security vulnerabilities in web development, vulnerabilities in common PHP functions, and PHP file system security. At the same time, the security issues of server software are introduced.

Course Intermediate 10279
Course Introduction:Composer is a tool used by PHP to manage dependency relationships. You can declare the external libraries (libraries) you depend on in your project, and Composer will install these dependent library files for you.

Course Intermediate 3469
Course Introduction:A firewall is a system used to control access to a computer network. Firewalls can isolate risk areas from safe access areas and prevent unpredictable or unauthorized external access from invading the internal network. Learning firewalls under Linux is not only for these reasons. The most important thing is that during the learning stage, through the use of firewalls, you can better master the principles of network communication, become familiar with the operation of Linux, and master network services and network protocols. It is also important for learning Linux operation and maintenance or Cybersecurity is helpful. There are many firewalls under Linux, including iptables, firewalld, selinux, tcp_warppers, etc. This course summarizes these firewall-related technologies.
2018-05-24 21:24:46 0 0 1261
What software should I install to learn HTML?
What software should I install to learn HTML?
2018-08-22 16:08:22 0 2 1592
Installation of console software prompts no response
Installation of console software prompts no response
2020-03-28 22:43:15 0 0 1315
Analyze the security of npm packages
2023-08-15 13:45:16 0 1 560
Where can I download this software?
2020-08-26 16:57:09 0 1 1485
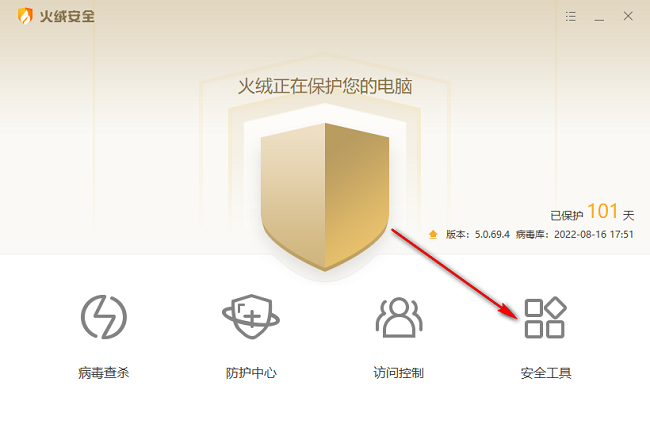
Course Introduction:Tinder Security is an anti-virus protection software with a simple interface and complete functions, which can bring users a good experience. More and more friends choose to use it. Does anyone know how to disable software activation in Tinder Security Software? The editor below will give you a detailed introduction to how to disable software activation in Tinder Security Software. If you are interested, you can take a look. Operation method: 1. Double-click to open the software and click the "Security Tools" option at the bottom of the page. 2. In the window interface that opens, click "Startup Item Management" in "System Tools". 3. Then click the "Allow Enable" option box on the right if you want to disable the startup items.
2024-08-15 comment 0 675
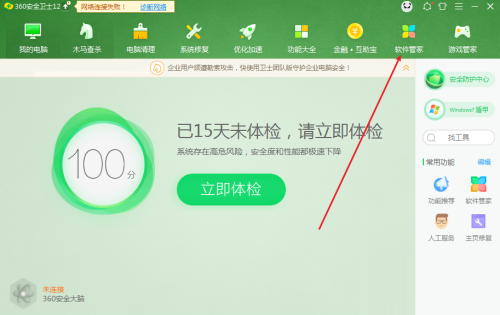
Course Introduction:Recently, some friends asked the editor how to uninstall the software of 360 Security Guard. The following will bring you the method of uninstalling the software of 360 Security Guard. Friends in need can come and learn more. 1. Open 360 Security Guard and click [Software Management] at the top, as shown in the figure below. 2. Find and click [Uninstall], as shown in the figure below. 3. Find the 360 Security Guard software and click [Uninstall] on the right, as shown in the figure below.
2024-03-04 comment 0 1361

Course Introduction:1. Most software will come with an uninstall tool, and Tinder Internet Security Software is no exception. Click the Start Menu ---[Tinder Security Lab]-----[Sysdiag]----[Uninstall]. 2. Click [Uninstall Now] when the uninstallation interface appears. 3. Uninstalled successfully. Method 2: 1. Enter the system control panel and find [Programs and Features] and click to enter. 2. Enter the uninstall and change program, find [Tinder Internet Security Software], right-click and select [Uninstall/Change]. 3. Click [Uninstall Now] when the uninstallation interface appears. 4. Uninstallation is successful. Method three: Find the root directory of the software, use 360 or other software to directly shred the files. Method four: Enter safe mode to delete the folder and delete the service in the registry.
2024-06-07 comment 0 912
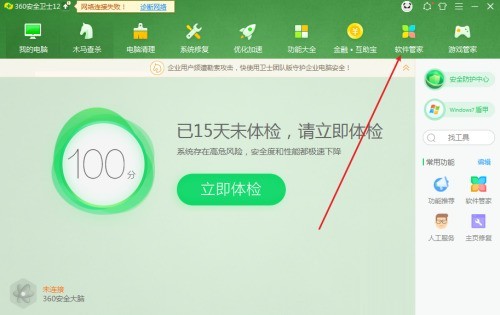
Course Introduction:1. Open 360 Security Guard and click [Software Management] at the top, as shown in the figure below. 2. Find and click [Uninstall], as shown in the figure below. 3. Find the 360 Security Guard software and click [Uninstall] on the right, as shown in the figure below.
2024-06-03 comment 0 875

Course Introduction:Is it safe to buy Bitcoin software via mobile phone? Analyze the truth! As a virtual currency, Bitcoin has become increasingly popular in recent years. As its value continues to rise, many people are beginning to consider buying Bitcoin as an investment. In order to facilitate users to conduct transactions, many applications for buying Bitcoin have been launched on mobile phones. However, many people have some concerns about the security of this type of software. After all, is it safe to buy Bitcoin software on mobile phones? Below I will answer these questions for you one by one. Security Issue 1: How to prevent software intrusion and account theft? When buying Bitcoin software, security issues are always the top concern for users. It is true that some software has certain security risks. In order to avoid account theft, users should choose the software platform reasonably and download it before downloading.
2024-02-08 comment 0 668