
Course Advanced 9135
Course Introduction:"JS Development Verification Form Tutorial" will introduce the front-end div+css layout in detail and achieve the effect of verification form through native js code.

Course Elementary 10626
Course Introduction:The 13th online training class of php Chinese website officially started last night (2020.9.28)~~! The first 3 days of the course are free and open to the public, welcome to study! To register, please contact QQ27220243 (Teacher Zhong) or go to: //m.sbmmt.com/k.html

Course Intermediate 3529
Course Introduction:A firewall is a system used to control access to a computer network. Firewalls can isolate risk areas from safe access areas and prevent unpredictable or unauthorized external access from invading the internal network. Learning firewalls under Linux is not only for these reasons. The most important thing is that during the learning stage, through the use of firewalls, you can better master the principles of network communication, become familiar with the operation of Linux, and master network services and network protocols. It is also important for learning Linux operation and maintenance or Cybersecurity is helpful. There are many firewalls under Linux, including iptables, firewalld, selinux, tcp_warppers, etc. This course summarizes these firewall-related technologies.

Course Intermediate 11360
Course Introduction:"Self-study IT Network Linux Load Balancing Video Tutorial" mainly implements Linux load balancing by performing script operations on web, lvs and Linux under nagin.
Ways to protect form from button submission
2023-10-10 10:47:12 0 1 684
2023-08-17 10:16:22 0 2 593
The firewall function of symfony2 security, curl simulates form submission error reporting
2017-05-16 16:44:15 0 1 558
2017-05-18 10:52:14 0 1 742
2023-09-13 22:06:46 0 1 648

Course Introduction:With the rapid development of the Internet, websites have become an important carrier for business, education, entertainment, social networking, etc. In this context, forms are needed to collect user data information. However, forms have also become an important target for cyber hackers. Common network attack methods include injection attacks, cross-site scripting attacks, HTTP request hijacking, man-in-the-middle attacks, etc. To protect against these security threats, website developers need to secure their forms by using techniques that protect against code review scripts. 1. What is a defensive code review script? protection
2023-06-24 comment 0 1365

Course Introduction:With the continuous development of network technology, forms on websites are becoming more and more common, including login forms, registration forms, comment forms, etc. However, the security of form data has also received increasing attention. When developing a form, we must consider not only the functionality of the form, but also the security of the form. This article will focus on the security implementation techniques of drop-down menus in forms, especially the protection methods of drop-down menus in PHP forms. 1. What is a drop-down menu? A drop-down menu refers to a drop-down list that appears on a web page. Users can click the drop-down list to
2023-06-24 comment 0 1096

Course Introduction:How to prevent PHP forms from being hacked? With the development of the Internet, websites have become an important platform for people to obtain information, share content and communicate. Forms on websites are often used for users to submit data, register accounts, leave messages and other functions. However, due to the existence of hackers, our form data is easily attacked and tampered with, causing serious security issues. In order to prevent PHP forms from being attacked by hackers, we will introduce some common security protection measures and related code examples below. Input validation hackers often exploit the
2023-08-18 comment 0 1166
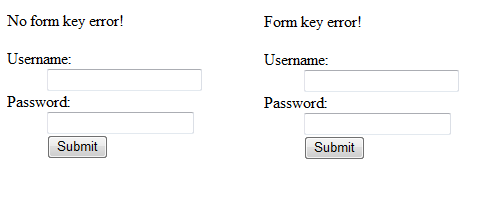
Course Introduction:Security is a hot topic. Securing your website is extremely important for any web application. In fact, 70% of my time is spent protecting applications. One of the most important things we have to protect are forms. Today we will review a way to prevent XSS (cross-site scripting) and cross-site request forgery on your forms. Why? POST data can be sent from one website to another. Why is this bad? A simple scenario...a user logged into your website visits another website during their session. The website will be able to send POST data to your website - for example, using AJAX. Because the user is logged in to your site, other sites can also send publishing data to a secure system that is only accessible if they are logged in.
2023-09-07 comment 0 1456

Course Introduction:Prevent Web Form Submission with ENTER KeyPreventing the ENTER keypress from triggering form submission is a common requirement in web...
2024-11-07 comment 0 956