
Course9851
Course Introduction:The course content covers common PHP security vulnerabilities in web development, vulnerabilities in common PHP functions, and PHP file system security. At the same time, the security issues of server software are introduced.

Course2857
Course Introduction:Course introduction: 1. Cross-domain processing, token management, route interception; 2. Real interface debugging, API layer encapsulation; 3. Secondary encapsulation of Echarts and paging components; 4. Vue packaging optimization and answers to common problems.

Course1795
Course Introduction:Apipost is an API R&D collaboration platform that integrates API design, API debugging, API documentation, and automated testing. It supports grpc, http, websocket, socketio, and socketjs type interface debugging, and supports privatized deployment. Before formally learning ApiPost, you must understand some related concepts, development models, and professional terminology. Apipost official website: https://www.apipost.cn

Course5521
Course Introduction:(Consult WeChat: phpcn01) The comprehensive practical course aims to consolidate the learning results of the first two stages, achieve flexible application of front-end and PHP core knowledge points, complete your own projects through practical training, and provide guidance on online implementation. Comprehensive practical key practical courses include: social e-commerce system backend development, product management, payment/order management, customer management, distribution/coupon system design, the entire WeChat/Alipay payment process, Alibaba Cloud/Pagoda operation and maintenance, and project online operation. .....

Course5172
Course Introduction:(Consult WeChat: phpcn01) Starting from scratch, you can solve conventional business logic, operate MySQL with PHP to add, delete, modify, and query, display dynamic website data, master the MVC framework, master the basics of the ThinkPHP6 framework, and learn and flexibly master all knowledge involved in PHP development. point.
2023-11-16 14:36:03 0 12 290
Your platform is experiencing a problem detected by Composer. PHP 8.1
2023-11-06 18:01:25 0 1 255
Vite HMR cannot detect changes to components within subfolders
2023-11-04 09:37:46 0 1 272
2023-10-18 20:38:28 0 1 239
JavaScript regular expressions for URL detection and splitting
2023-09-21 18:00:47 0 1 274

Course Introduction:ASP scanning tool vulnerability detection: 1. Select the appropriate scanning tool; 2. Configure the scanning target in the scanning tool; 3. Configure scanning options as needed; 4. After the configuration is completed, start the scanning tool to start scanning; 5. Scanning tool A report will be generated listing the detected vulnerabilities and security issues; 6. Fix the detected vulnerabilities and security issues according to the recommendations in the report; 7. After fixing the vulnerability, re-run the scanning tool to ensure that the vulnerability has been successfully exploited repair.
2023-10-13 comment 01114

Course Introduction:网站漏洞检测至关重要,可通过以下方法进行:自动扫描器:易于使用,可识别潜在漏洞。手动渗透测试:更彻底,但成本更高。代码审查:可发现自动扫描器错过的漏洞。SIEM 系统:监控活动并识别可疑模式。Bug 赏金计划:奖励发现并报告漏洞的研究员。常见的漏洞类型包括:注入漏洞、XSS、SQL 注入、缓冲区溢出和 RFI。
2024-08-16 comment835

Course Introduction:Methods include: 1. Use specialized vulnerability scanning tools; 2. Manual testing to discover and verify vulnerabilities in ASP applications; 3. Conduct security audits to check the code and configuration files of ASP applications; 4. Use vulnerability exploitation frameworks; 5. Review the code of the ASP application.
2023-10-13 comment 0668
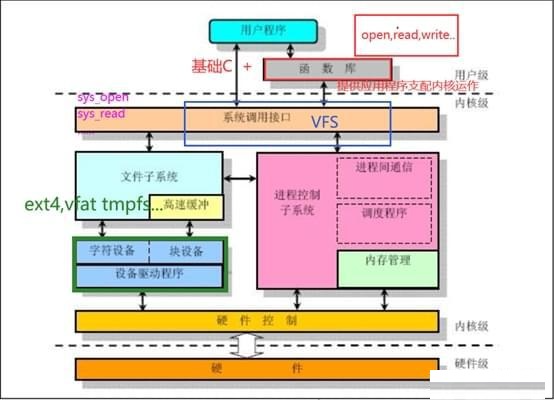
Course Introduction:The usual mode of quoting open source software is to introduce the dynamic library or jar package of open source software. Therefore, the false alarm rate of vulnerabilities will be very low during vulnerability detection, but it is different in the Linux kernel. Since the Linux kernel function modules are very rich and It is huge and will be tailored according to business needs in actual use. Therefore, how to achieve accurate vulnerability detection and reduce the false positive rate of vulnerability detection in this scenario is particularly prominent. Linux kernel structure: The Linux kernel is composed of seven parts, and each different part is composed of multiple kernel modules. The structural block diagram is as follows: Linux tailoring scenario analysis: By analyzing the Linux kernel source code, you can see that different modules are stored in different directories. The implementation code can be conf at compile time.
2024-02-13 comment 0575