
Course Elementary 9954
Course Introduction:The processing and analysis of strings is an important foundation in any programming language. The classification, parsing, storage and display of information, as well as data transmission in the network, all require the manipulation of strings. It is particularly important in web development. Most of the work of programmers is to operate strings, so string processing also reflects a programming ability of programmers.

Course Elementary 25490
Course Introduction:Object-oriented programming using php

Course Intermediate 11246
Course Introduction:"Self-study IT Network Linux Load Balancing Video Tutorial" mainly implements Linux load balancing by performing script operations on web, lvs and Linux under nagin.

Course Advanced 17582
Course Introduction:"Shangxuetang MySQL Video Tutorial" introduces you to the process from installing to using the MySQL database, and introduces the specific operations of each link in detail.
How Weex handles HTTPS network requests and how Android handles it
2017-06-17 09:16:08 0 1 917
2017-05-17 10:08:26 0 1 692
How to deal with failure to add
How to deal with failure to add
2019-06-30 17:08:43 0 1 1384
2017-04-24 09:13:51 0 3 640
python3.x - python processing javascript json
2017-05-18 11:01:28 0 2 691
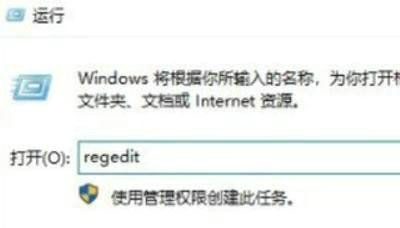
Course Introduction:When we use the security check function of Win10 system, we sometimes see some potential threats. But what should you do if you find a threat that you can’t deal with? Maybe it's because there are some files under the registry that restrict our operations. It doesn't matter, we can solve the problem by entering the WindowsDefender folder under the Registry Editor and setting it up. Next, let me give you a detailed introduction to the solution to the problem that Win10 detects threats that cannot be dealt with. What to do if Windows 10 detects threats that cannot be dealt with? Method 1. Open Run with the "win+R" shortcut key, enter "regedit", and press Enter to open it. 2. Enter the Registry Editor and click "HKEY_LOCAL_MACHINE\So" on the left
2024-09-03 comment 0 669
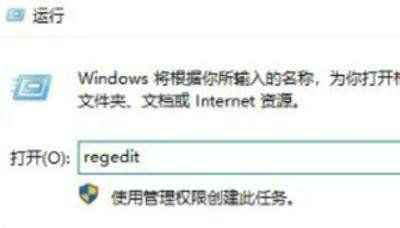
Course Introduction:When we use the security detection function in win10 system, we will find some existing threats, but what should we do if we find that the threats cannot be dealt with? It may be because there are file restrictions under the registry. Users can enter the WindowsDefender folder under the registry editor to make settings. Let this site carefully introduce to users how to deal with threats that cannot be dealt with in Windows 10. What should I do if Win10 finds that threats cannot be dealt with? Method 1. "Win+R" shortcut key to open Run, enter "regedit", and press Enter to open. 2. Enter the Registry Editor and click "HKEY_" on the left
2024-02-10 comment 0 893

Course Introduction:How to deal with and respond to security threats in Linux servers. With the development of the Internet, server security has become an important issue that enterprises and individuals must face. Linux servers, in particular, have become the main target of hacker attacks due to their open source nature and wide application. In order to protect the server from security threats, we need to take a series of measures to ensure the security of the server. This article will introduce some common Linux server security threats and corresponding treatment and response methods. First, we need to understand the common Li
2023-09-11 comment 0 1516

Course Introduction:When some users open the Security Center in Win10 system, they encounter the prompt "Your virus and threat protection is managed by your organization." What should I do if Win10 prompts that my virus and threat protection is managed by your organization? The editor below will give you a detailed introduction to the solution for Windows 10 prompting that your virus and threat protection is managed by your organization. If you are interested, take a look. Solution to Windows 10 prompting that your virus and threat protection is managed by your organization: 1. Right-click Start in the taskbar and select "Run" in the menu to open it. 2. Enter "regedit" in the window and press Enter to open. 3. After entering the new interface, change &q
2024-01-12 comment 0 2417
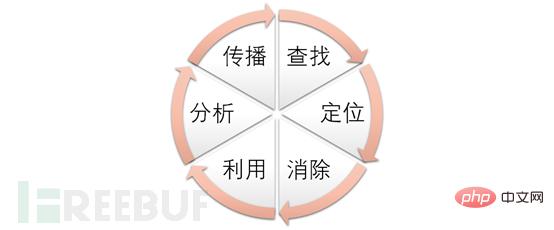
Course Introduction:About the Threat Intelligence Processing Cycle Model The term "Threat Intelligence Processing Cycle" (F3EAD) originates from the military. It is a method for organizing resources and deploying troops designed by the US Army's commanders at all levels of the main combat arms. The Network Emergency Response Center draws on this method and processes threat intelligence information in the following six stages: Threat Intelligence Processing Cycle Application of the F3EAD Threat Intelligence Processing Cycle Model Step 1: Find a date on a certain month and deploy it on the partner's public cloud server The "Onion" system alarm found a suspected Trojan horse program, so the emergency response team quickly started the emergency response process: stakeholders and others gathered the group with one click and called in. The victim system is isolated for investigation. The security system and audit logs are exported for traceability analysis. Preparation of business system architecture and code-related information to analyze intrusion breaches and victims
2023-05-14 comment 0 1784