
Course Intermediate 11273
Course Introduction:"Self-study IT Network Linux Load Balancing Video Tutorial" mainly implements Linux load balancing by performing script operations on web, lvs and Linux under nagin.

Course Advanced 17597
Course Introduction:"Shangxuetang MySQL Video Tutorial" introduces you to the process from installing to using the MySQL database, and introduces the specific operations of each link in detail.

Course Advanced 11309
Course Introduction:"Brothers Band Front-end Example Display Video Tutorial" introduces examples of HTML5 and CSS3 technologies to everyone, so that everyone can become more proficient in using HTML5 and CSS3.
HTML table repeats content on every submit click
2024-02-21 18:09:04 0 1 440
Ways to fix issue 2003 (HY000): Unable to connect to MySQL server 'db_mysql:3306' (111)
2023-09-05 11:18:47 0 1 773
Experiment with sorting after query limit
2023-09-05 14:46:42 0 1 703
CSS Grid: Create new row when child content overflows column width
2023-09-05 15:18:28 0 1 594
PHP full text search functionality using AND, OR and NOT operators
2023-09-05 15:06:32 0 1 552
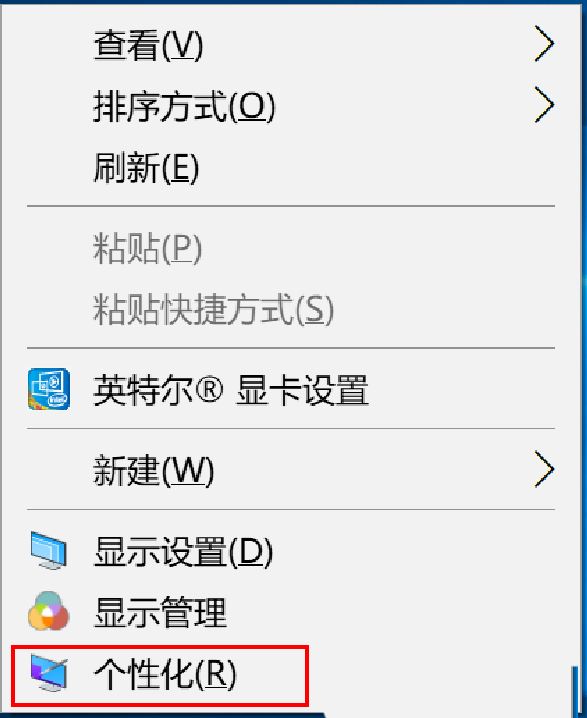
Course Introduction:How to delete the pictures in the personalized background of Windows 10? The desktop backgrounds we have used are all in the settings. Some users want to delete them, so how do they do this? Users can enter the personalized function interface to operate. Let this site carefully introduce to users how to delete pictures in the personalized background of Win10. How to delete pictures in the personalized background of Windows 10 1. Click [right-click] on a blank space on the desktop, and select [Personalize] from the menu item that opens. 2. In the Select Picture in the Background, you can view the desktop background pictures you have used. Delete the used desktop background image: Note: This operation involves modifying the registry. Modifying the registry is risky. Please back up the data in advance. 1. Press [
2024-02-14 comment 0 1504
Course Introduction:What is registry mode? it's actually really easy! The role of the registry is to provide system-level object access capabilities. We often take "global variables are bad" as an article of faith when coding. However, everything has two sides, and global data access is very attractive. Here comes the problem: Most systems are divided into several layers, and each layer only communicates with adjacent layers through pre-defined channels. Sharing layers makes the program flexible, and replacing or modifying each layer can minimize the impact on other parts of the system. But when you need to obtain information in one layer that is not adjacent to another layer, what should you do...
2016-11-12 comment 0 1655

Course Introduction:Microsoft launches new ChatGPT-powered Bing, but not everyone can use it. That's because the new Bing is still in preview and only accessible to those who join the waitlist. However, some users signed up for their Microsoft accounts weeks ago and still haven't gotten past the waitlist. Microsoft has a piece of advice for these people. According to Michael Schechter, vice president of Bing growth at Microsoft, one of the reasons you're stuck on the Bing waitlist is that your Microsoft account profile doesn't include your birthday. Schechter also said that Microsoft will not approve users' requests to try out the new Bing unless
2023-05-26 comment 0 1716
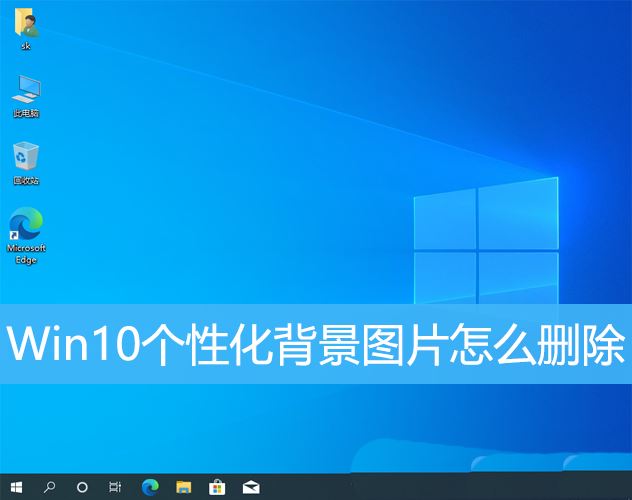
Course Introduction:Every time the desktop background used in Win10 system will be displayed in the personalized background image in the settings, some users want to delete it, but don’t know how to do it. This article is about how to delete the personalized background image in Win10 shared by this site. View used desktop background images: 1. Click [right-click] on a blank space on the desktop, and select [Personalize] in the menu item that opens; 2. In the selection image in the background, you can view the desktop backgrounds you have used. Picture; delete the used desktop background picture: Note: This operation involves modifying the registry. Modifying the registry is risky. Please back up the data in advance. 1. Press the [Win+R] key combination at the same time to open the run window and enter [regedit] ] command, and then click [OK]; 2
2023-12-21 comment 0 1757

Course Introduction:How to use PHP to implement the verification code function of the CMS system. With the development of the website and the increase in user interaction, in order to ensure the security of the website, it is often necessary to add the verification code function in operations such as user registration, login and form submission. This article will introduce how to use PHP to implement the verification code function of the CMS system to protect the website from robots and malicious attacks. 1. Generate verification code First, we need to generate a verification code image. PHP provides a GD library that can be used to generate pictures and draw text, interference lines and other effects on the pictures. The following is raw
2023-08-04 comment 0 1456